Network Security
Will Cloud-Native Network Security Oust Firewalls?
Security threats have already begun to outpace cloud firewalls. It’s a fact. But organizations exploring new cloud-native solution find themselves more prepared to stay resilient. Find out how cloud-native network security’s features and benefits are making this possible.
Digital transformation is worth the pain.
Aside from expediency and security improvements, digital transformation has brought cutting-edge tools and new approaches to developing, deploying, and managing applications on the cloud.
One product of this digital evolution that’s been gaining popularity is cloud-native. This approach empowers organisations to build, deploy, and run applications with the full capabilities of cloud computing, including unlimited on-demand power and availability.
Cloud-native applications adopt a microservices architecture composed of several small integrated services that can be independently operated. This has led to cloud application security regularly being an essential concern to organisations and cybersecurity experts looking to minimise or completely insulate their products from security breaches and cyberattacks.
In addition, Cloud-native network security ensures that applications running in cloud-native environments are protected from adverse security events. It offers modern protection features and services like compliance management, network security, advanced threat detection, security key management, and encryption functionalities.
What exactly is a cloud firewall?
Having been around as long as networks, a firewall is a software tool that allows you to verify and control your application’s network traffic. A cloud firewall is just like its traditional on-premises replicate but hosted on the cloud and remotely available. Cloud firewalls effectively protect applications against generic malicious network traffic and attacks.
Because cloud firewalls have empowered organisations to manage their network nodes and enforce security protocols and corporate policies, they’ve become a major player in cloud computing security.
Cloud-native network security
The world is gradually transitioning away from traditional virtualizations to the cloud. Although there are countless advantages to digital transformation, the sophistication and frequency of security breaches and attacks on cloud infrastructures present one important question… how can we stay ahead of threat actors looking to compromise cloud-native networks and applications? According to a report from IDC more organisations using cloud infrastructures experiencing ar experiencing security-related failures.
Cloud services providers are responsible for several security requirements, such as infrastructure and computing resource protection. Still, security must be handled separately for native applications running on the cloud environment. Cloud-native network security is gradually gaining adoption in cloud application security because it can accommodate the many facets of cloud security. This includes application, file storage, workflow, and container security.
Cloud-native security providers now offer cutting-edge protection tools—like the Trend Micro Cloud One™ cloud security platform—which meets the high standards required of today’s advanced cloud security landscape.
Implications of cloud-native network security
There are typically numerous questions as to what the new security situation will look like when migrating to the cloud.
It’s important to know that many cloud-native users opt out of cloud firewalls in favour of more cost-effective security tools offered by providers like Amazon Web Services (AWS).
When these tools are combined with the increasingly popular Trend Micro Cloud One™ – Network Security, they boast significant capabilities and protections that far outweigh the usefulness of a cloud firewall. These may include central discovery, visibility and reporting across cloud environments, robust authentication through extra layers of credentials, and multiple approaches to threat detection.
Since cloud-native applications are extremely dynamic, cybersecurity teams often find it challenging to establish a firewall around a cloud-native application that meets the security requirements of applications running on the cloud.
Cloud-native applications typically have a microservice and distributed architecture model with many moving parts rather than the traditional monolithic application model. This creates difficulties for traditional firewalls with limited scopes.
It’s beneficial to examine the features and capabilities of Cloud One - Network Security and cloud-native network security in general.
Network Security capabilities
Over time, you should see that surrounding your cloud-native application with a cloud firewall by itself is ineffective, considering the advancement of cloud security vulnerabilities, attacks, and breaches. These often include advanced persistent threats and cloud hypervisor attacks which can bypass some cloud firewall rules.
Network Security offers modern, advanced protection tools that are significantly more effective against cloud-native security threats that would ordinarily bypass a cloud firewall.
Leveraging advanced threat intelligence and protocol analysis, anomaly detection, indicators of compromise (IoC) blocking, and classic signature-based methods, Network Security detects and protects against entire classes and techniques of attacks in addition to specific attacks.
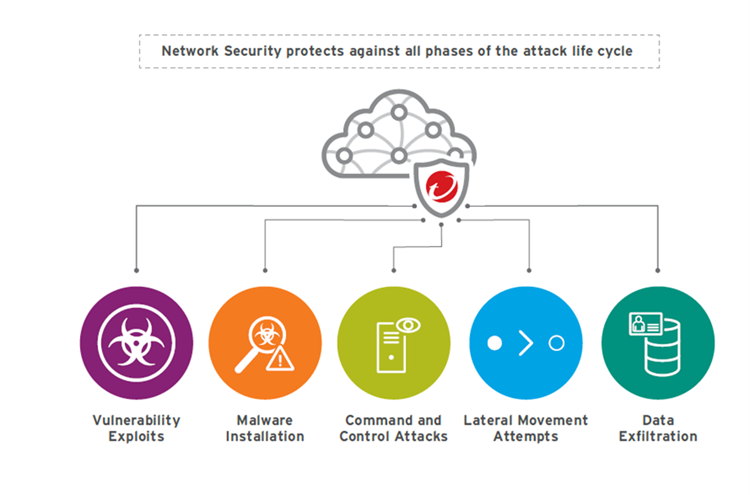
Advanced application and workflow security
Trend Micro Cloud One – Network Security applies IPS/IPDS (intrusion prevention system/ intrusion prevention detection system) with state-of-the-art machine learning algorithms and a virtual patching approach to bring a secure workflow to your organisation. This approach allows aggregated logs and information from every component of your application to be efficiently monitored and vetted.
Cloud-native applications need advanced tools and approaches that traditional cloud firewalls with limited scopes don’t typically offer. The inclusion of Network Security ensures application, workflow, and operations security.
Efficient API integration across platforms
Network Security has numerous security APIs (such as the Trend Micro Cloud One™ API key for authentication and the Trend Micro Cloud One™ – Workload Security API). This enables you to integrate effortlessly into your application’s DevOps processes without affecting your codebase or infrastructure. While integration is sometimes overlooked in security tools, many third-party APIs in fact require extra packages and logic to adapt.
In addition its easy incorporation via the AWS Security Hub integration channel, enabling Trend Micro Cloud One to send security events, logs, and assessments to AWS, Network Security is efficient across multiple environments—physical, virtual, cloud, and containers.
Robust and integrated security arsenal
Traditional firewalls hosted on the cloud suffer from limited tools and approaches. Alongside other cloud-native network security platforms, Network Security offers a wide range of integrated defensive tools and protocols. Security deployment automation, intelligent threat aggregation, and reporting to application security health checks all contribute to its robust cloud-native application security.
Optimize the entire administrative process by bringing a unified approach to system visibility, management, and role-based control.
Cost-effective software-as-a-service model
Individual third-party services like DDoS protections and bot mitigation are often billed at a fixed price, causing organisations to pay during downtime. Network Security gives you flexible offerings (including hourly pricing), so you only pay for the time and resources your application consumes.
System scaling, administrating, and deploying
Scaling security infrastructures and system requirements to accommodate your rapidly changing users is a challenge—especially when dealing with cloud-native applications. Network Security intelligently monitors your application for changing security requirements, automatically scaling your application’s security resilience against network traffic.
You’re also enabled to reduce the complexity of administrating and deploying your cloud-native application. This eliminates the need for multiple-point solutions and ensures secure deployment, storage, and user privacy. Furthermore, Network Security guarantees secure communications and the reliable operation of your cloud-native application.
Trend Micro offers two simple deployment options for Network Security:
Virtual Appliance: Trend Micro is responsible for inspecting network traffic while customers deploy, scale resources, provide staffing and software maintenance, along with the associated cost of running the service.
Hosted Infrastructure: Trend Micro is responsible for the deployment, scaling of resources, software maintenance, and inspecting the network traffic.
Are cloud firewalls still relevant?
The influence of cloud firewalls may be fading, but they are still being utilised by organisations employing cloud-based application security.
While these tools have helped control the traffic across a network and maintain the efficiency and integrity of that network, cloud-native network security goes further. You’re provided with extra layers of credentials and advanced tools to insulate an application from attacks and security breaches.
Cloud-native network security is highly effective in several use cases, including the identifying and accessing of management policy engines. In addition, flow logs are aggregation and network traffic is monitored. Teams are also provided with cloud logging for control planes and data encryption and security key management
In addition to enabling platform flexibility for integration and migration, and simple deploying and scaling security architecture, cloud-native network uses machine learning algorithms for automated threat recognition. In case of application crashes, your team can pull from a data backup.
Revolutionizing the cloud computing world
Attacks unleashed on cloud applications and infrastructures are becoming more sophisticated, and only cutting-edge tools and approaches can ensure the resilience and integrity of cloud-native applications. Without this security, businesses and organisations must rely on cloud firewalls and multiple individual security services for their applications.
There’s one important way to simplify your digital transformation journey, and it starts with joining the cloud-native revolution.
Explore Trend Micro solutions to learn more about cloud-native network security and Cloud One - Network Security.


