Ransomware
New LockBit 5.0 Targets Windows, Linux, ESXi
Trend™ Research analyzed source binaries from the latest activity from notorious LockBit ransomware with their 5.0 version that exhibits advanced obfuscation, anti-analysis techniques, and seamless cross-platform capabilities for Windows, Linux, and ESXi systems.
Key takeaways:
- The LockBit 5.0 Windows variant uses heavy obfuscation and packing by loading its payload through DLL reflection while implementing anti-analysis technique. The Linux variant has similar functionality with command-line options for targeting specific directories and file types. The ESXi variant specifically targets VMware virtualization infrastructure, designed to encrypt virtual machines.
- The new variants use randomized 16-character file extensions, has Russian language system avoidance, and event log clearing post-encryption.
- LockBit 5.0 also has a dedicated ESXi that targets VMware's ESXi virtualization infrastructure.
- The existence of Windows, Linux, and ESXi variants confirms LockBit's continued cross-platform strategy, enabling simultaneous attacks across entire enterprise networks including virtualized environments. Heavy obfuscation and technical improvements across all variants make LockBit 5.0 significantly more dangerous than its predecessors.
- Trend Vision One™ detects and blocks the specific IoCs mentioned in this blog, and offers customers access to hunting queries, threat insights, and intelligence reports related to LockBit 5.0.
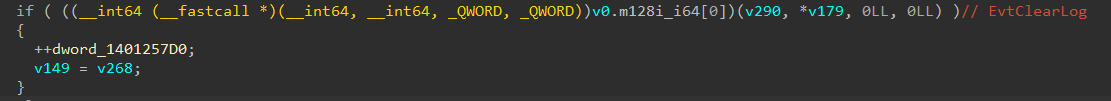
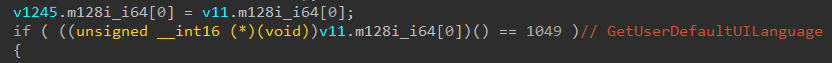
Trend™ Research has identified and analyzed the source binaries of a new LockBit version in the wild, which is the latest from the group’s activities following the February 2024 law enforcement operation (Operation Cronos) that disrupted their infrastructure. In early September, the LockBit ransomware group reportedly resurfaced for their sixth anniversary, announcing the release of "LockBit 5.0". Trend Research discovered a binary available in the wild and began analysis that initially discovered a Windows variant and confirmed the existence of Linux and ESXi variants of LockBit 5.0.
This latest news continues the group's established cross-platform strategy seen since LockBit 2.0 in 2021.
Trend Research analysis found that the Windows binary uses heavy obfuscation and packing: it loads its payload through DLL reflection while implementing anti-analysis techniques like ETW patching and terminating security services. Meanwhile, the newly discovered Linux variant maintains similar functionality with command-line options for targeting specific directories and file types. The ESXi variant specifically targets VMware virtualization environments, designed to encrypt entire virtual machine infrastructures in a single attack.
Our investigation also reveals that these newer versions share key behaviors: randomized 16-character file extensions, Russian language system avoidance through geolocation checks, and event log clearing post-encryption. The 5.0 version also shares code characteristics with LockBit 4.0, including identical hashing algorithms and API resolution methods, confirming this is an evolution of the original codebase rather than an imitation.
LockBit 5.0 Windows analysis
The Windows version of Lockbit 5.0 uses the -h parameter to display help information; the new version features a better user interface with clean formatting, which has not been seen in previous versions. It describes various options and settings for executing the ransomware, including basic options like specifying directories to encrypt or bypass, operation modes such as invisible mode and verbose mode, notes settings, encryption settings, filtering options, and examples of usage. The detailed commands and parameters illustrate the flexibility and customization available to the attacker.
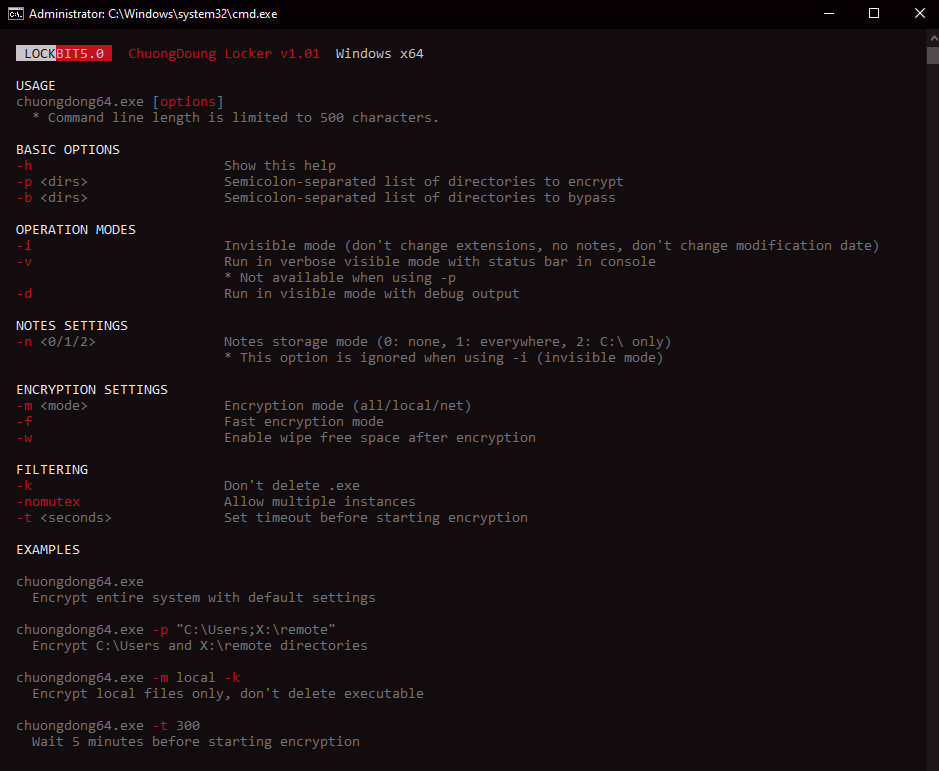
Table 1 shows the command line arguments observed in Trend Research threat hunting analysis and their respective descriptions.
| Option | Description |
| Basic Options | |
| -h | Show help |
| -d <dirs> | Semicolon-separated list of directories to encrypt |
| -b <dirs> | Semicolon-separated list of directoriees to bypass |
| Operation Modes | |
| -i | Invisible mode (don't change extensions, no notes, don't change modiciationdate) |
| -p | Run in verbose visible mode with status bar inc onsole (not available when using -i) |
| -v | Run in visible mode with debug output |
| Notes Settings | |
| -n <0/1/2> | Notes storage mode: |
| 0: None | |
| 1: Everywhere | |
| 2: C:\ only | |
| Ignored when using -i (invisible mode) | |
| Encryption Settings | |
| -m <mode> -w | Encryption mode: |
| all: Encrupt all files | |
| local: Encrypt local files | |
| net: Encrypt network files | |
| Enable wipe free space after encryption | |
| Filtering | |
| -k | Don'r delete .exe files |
| -nomutex | Allow multiple instances |
| Timeout | |
| -t <seconds> | Set timeout before starting encryption |
Table 1. A summary of the command line arguments in our analysis of the LockBit 5.0 Windows version.
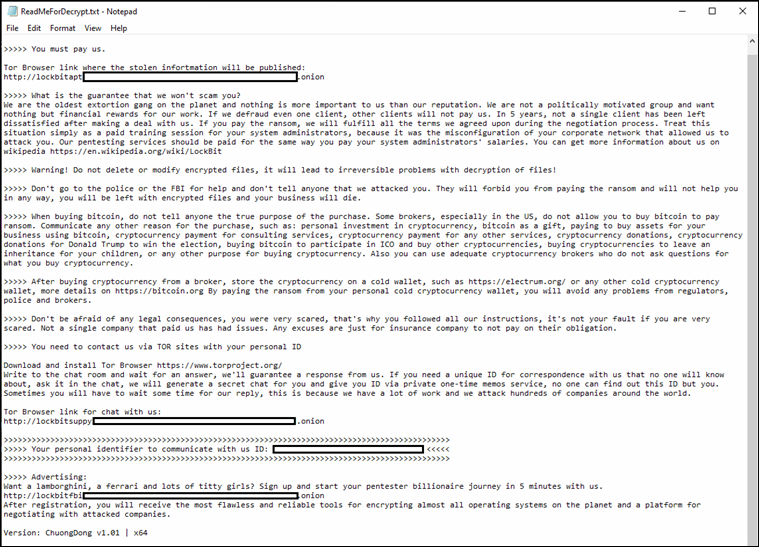
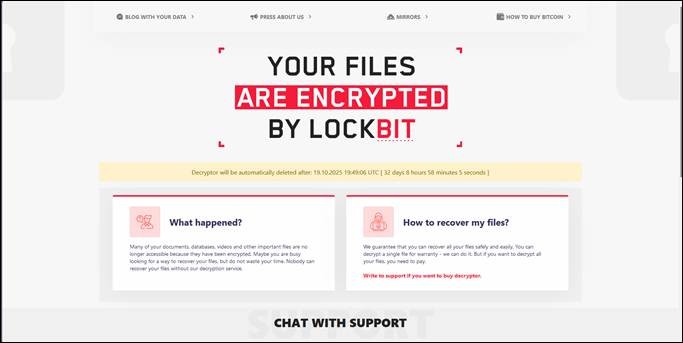
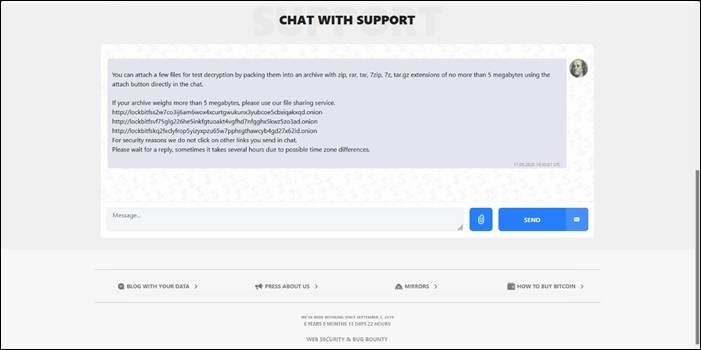
Upon execution, the ransomware generates its signature ransom note and directs victims to a dedicated leak site. The infrastructure maintains LockBit's established victim interaction model, featuring a streamlined "Chat with Support" section for ransom negotiations.
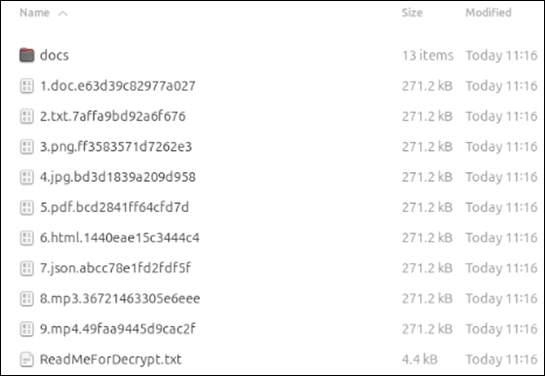
The encryption process appends randomized 16-character extensions to files, complicating recovery efforts. Unlike some ransomware variants that use common infection markers, LockBit 5.0 omits traditional markers at file endings. However, our analysis revealed consistent patterns including the original file size embedded in the encrypted file footer.
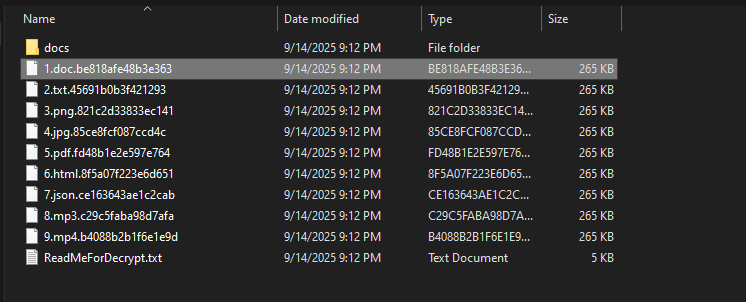
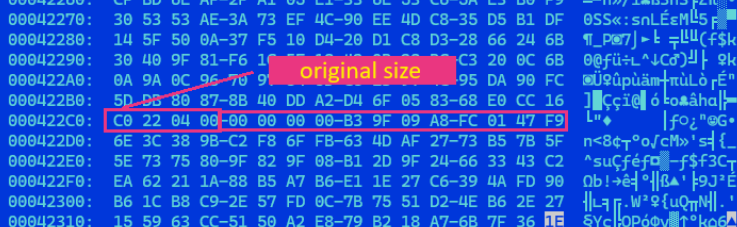
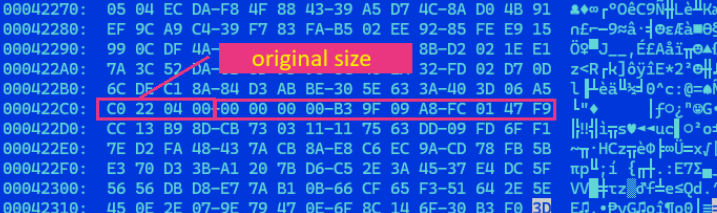
The sample Trend Research analyzed employs heavy obfuscation through packing. During debugging, we discovered it functions as a binary loader, decrypting a PE binary in memory and loading it via DLL reflection methods. This sophisticated loading mechanism significantly complicates static analysis.
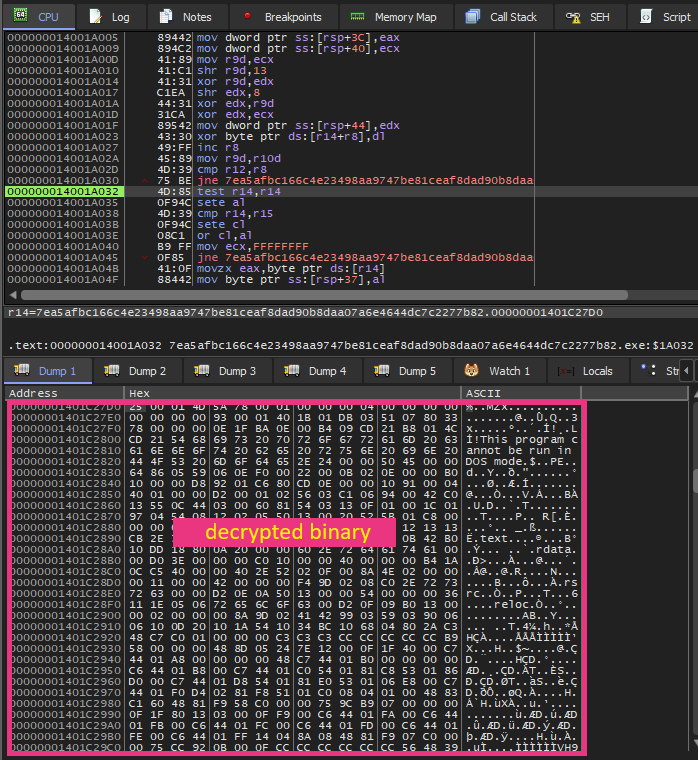
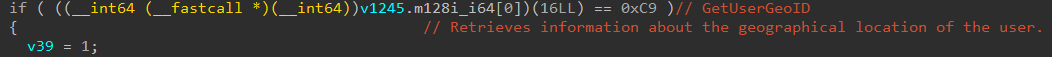
Aside from that, the malware implements multiple anti-forensics techniques. It patches the EtwEventWrite API by overwriting it with a 0xC3 (return) instruction, disabling Windows Event Tracing capabilities. Additionally, it terminates security-related services by comparing hashed service names against a hardcoded list of 63 values, then clears all event logs using the EvtClearLog API after encryption completion.
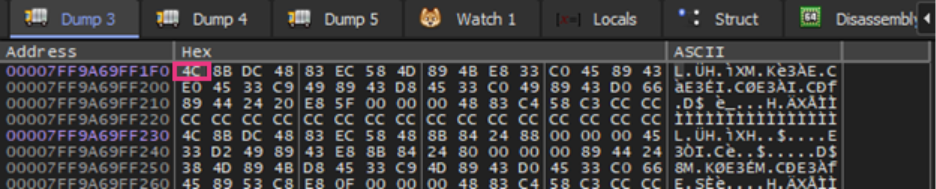
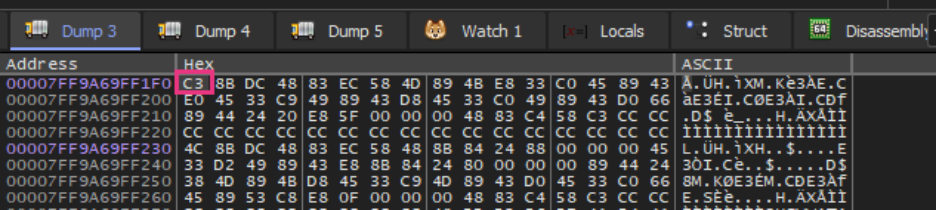
It compares all the services if they run the system by hashing the service name and comparing it with the hardcoded list. Service names that match are then terminated.
FEF56F15, BEC3470B, 9757464D, 88CE6B8E, 826AC445, 83143F70, 8685D050, 493AEE1F, 35BE2F4E, 23FA53E4, FEF56F16, 10D06066, 1370CEA3, E11A285C, DBECA3C2, BEC3470C, C347B317, CA6C4394, 732AA0BF, 60B29D13, 493AEE20, 5E5F1954, 5EF504FC, A49FA5E2, 9757464E, 9A768D62, A1816235, 41278146, 35BE2F4F, 369D7114, 3B6794E3, E7AA4056, E11A285D, E5C9CC93, E66A2C63, 7B39B584, 732AA0C0, 739BF272, 7ABD1404, 88CE6B8F, 9439954E, 9655130F, 23FA53E5, 26336765, 2C1F8E5F, DBECA3C3, DCF04E8C, DEED0E56, 60B29D14, 62C32884, 6337AD82, A49FA5E3, A8F16BAB, BD071334, 41278147, 4292EDD8, 47F1286A, E7AA4057, E7BF305D, F82A288D, 7B39B585, 7F480CF7, 7DD43601
Consistent with previous versions, LockBit 5.0 includes geopolitical safeguards, terminating execution when detecting Russian language settings or Russian geolocation. This is a common practice among Eastern European ransomware groups.
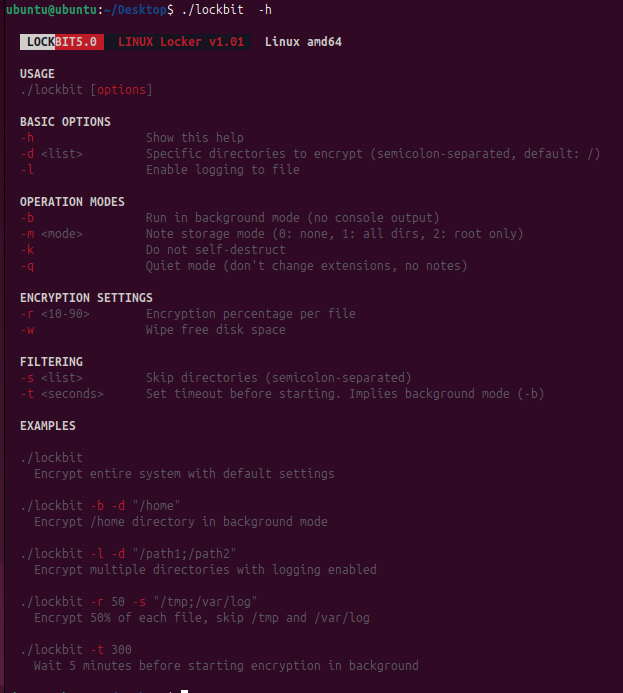
LockBit 5.0 Linux analysis
The 5.0 Linux variant has similar features with its Windows counterpart, demonstrating LockBit's commitment to cross-platform capabilities. The command-line interface mirrors the Windows version's formatting and functionality, providing attackers with the same operational flexibility across both platforms.
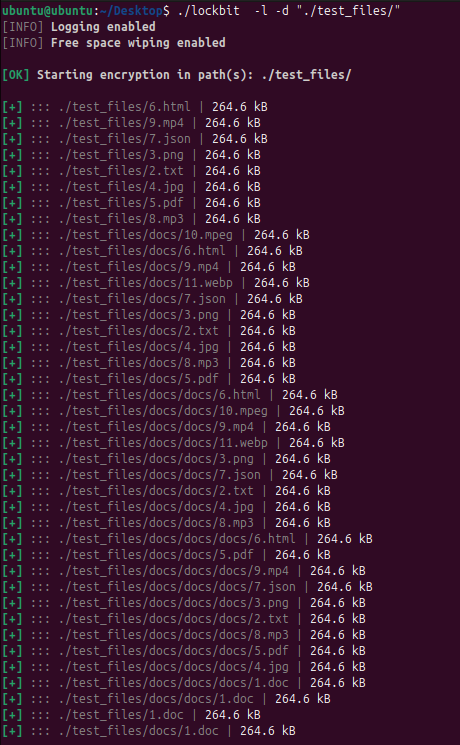
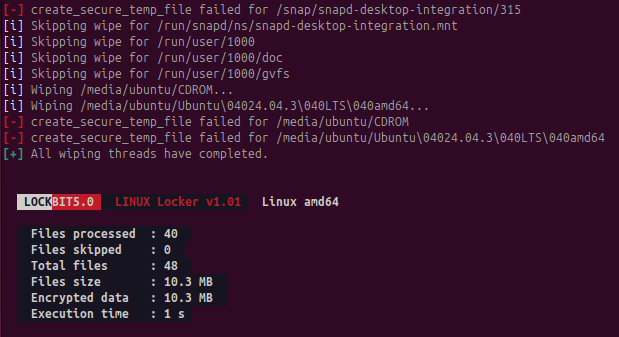
During execution, the Linux variant provides detailed logging of its activities, displaying files targeted for encryption and folders designated for exclusion. This transparency in operation logs suggests the variant can be used in testing environments or by affiliates requiring detailed execution feedback.
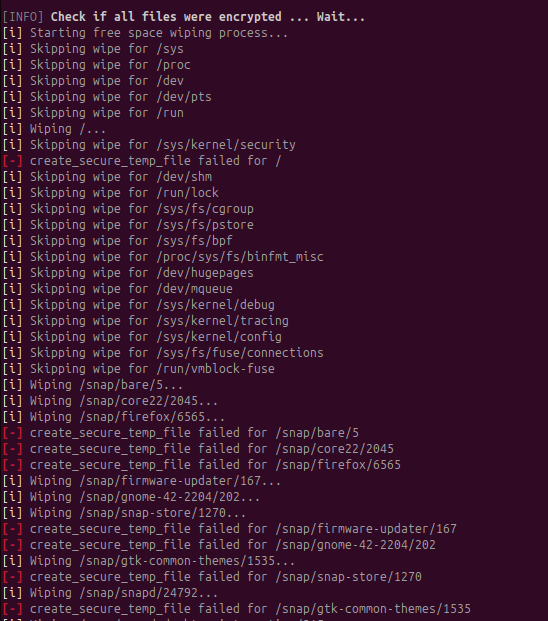
Upon completion, the ransomware generates a comprehensive summary showing the total number of files encrypted and their cumulative size. Like the Windows version, it applies randomized extensions to encrypted files, maintaining consistency in post-encryption file handling across platforms.
LockBit 5.0 ESXi analysis
Further investigation revealed a dedicated ESXi variant of LockBit 5.0, specifically targeting VMware virtualization infrastructure. This variant represents a critical escalation in LockBit's capabilities, as ESXi servers typically host multiple virtual machines, allowing attackers to encrypt entire virtualized environments with a single payload execution.
The ESXi variant maintains the same command-line interface structure as its Windows and Linux counterparts, ensuring operational consistency for attackers across all platforms. The help menu reveals ESXi-specific parameters optimized for virtual machine encryption, including options to target specific directories and VM configuration files.
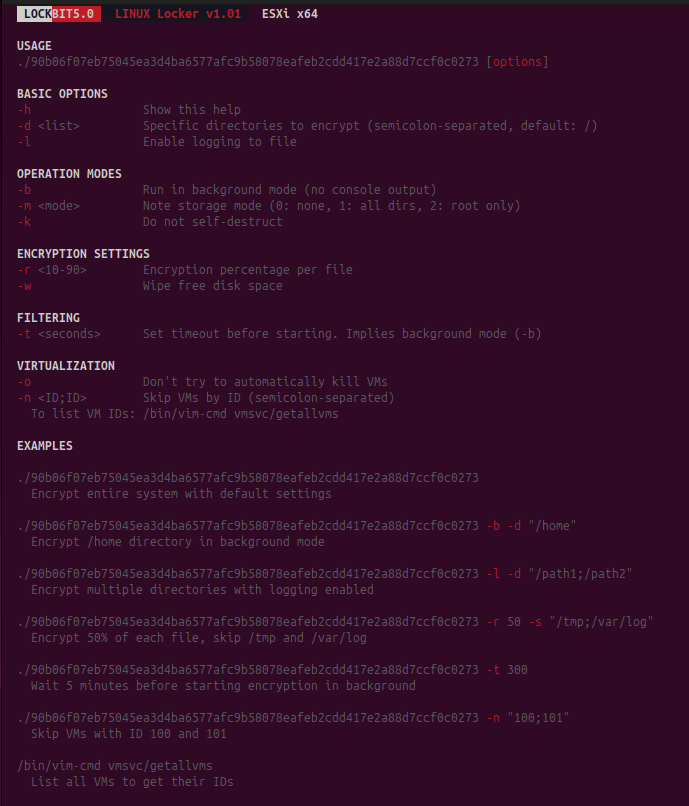
This ESXi variant demonstrates LockBit's strategic focus on maximizing impact through virtualization infrastructure, where a single compromised ESXi host can result in dozens or hundreds of encrypted virtual machines, significantly amplifying the attack's business disruption potential.
LockBit 4.0 versus LockBit 5.0
A comparative analysis between LockBit 4.0 and 5.0 reveals significant code reuse and evolutionary development rather than a complete rewrite. Both versions share identical hashing algorithms for string operations, a critical component for API resolution, and service identification. The code structure for dynamic API resolution remains remarkably similar between versions, suggesting the developers built upon the existing LockBit 4.0 codebase. The screenshots on the left in figures 20 and 21 are from chuong dong blog.
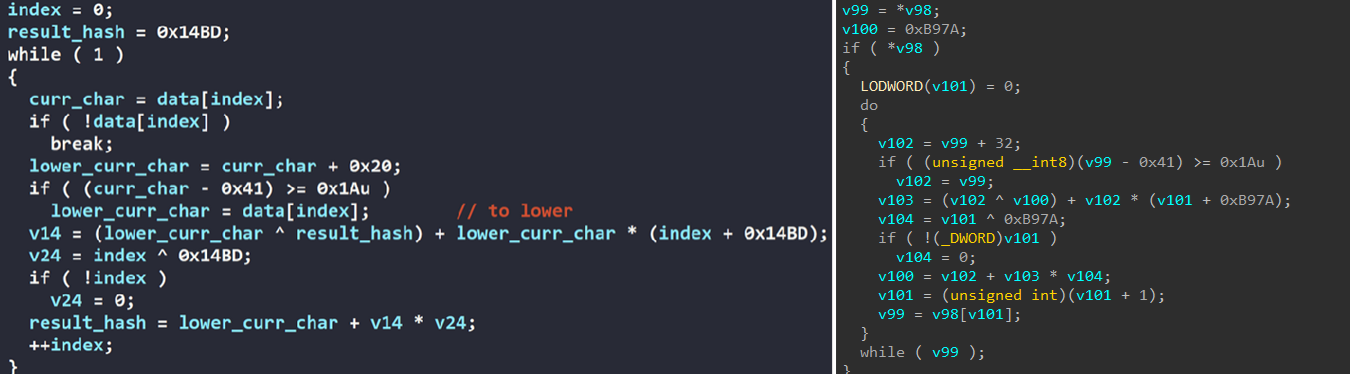
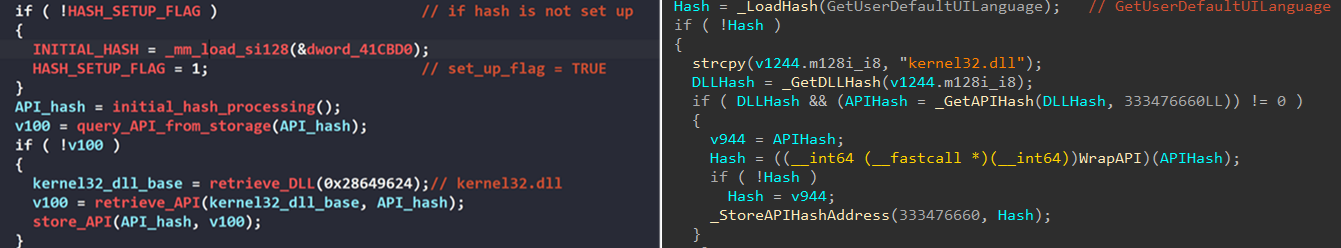
Trend Research believes that these similarities are a clear indication that LockBit 5.0 represents a continuation of the LockBit ransomware family and is not an imitation or rebrand by different threat actors. The preservation of core functionalities while adding new evasion techniques demonstrates the group's strategy of incremental improvement to their ransomware platform.
Conclusion
The existence of Windows, Linux, and ESXi variants confirms LockBit's continued cross-platform strategy. This enables simultaneous attacks across entire enterprise networks, from workstations to critical servers hosting databases and virtualization platforms, with the ESXi variant designed to cripple entire virtual infrastructures. Heavy obfuscation across these new variants significantly delays detection signature development, while technical improvements including removed infection markers, faster encryption, and enhanced evasion make LockBit 5.0 significantly more dangerous than its predecessors.
LockBit is among the most notorious ransomware-as-a-service (RaaS) groups that consistently stayed ahead of its competitors with an aggressive evolution of its techniques and tactics. Despite Operation Cronos, the criminals behind the group exhibit resilience with all three variants of version 5.0 now confirmed. Organizations must ensure comprehensive cross-platform defenses are in place, with particular attention to protecting virtualization infrastructure. LockBit 5.0's Windows, Linux, and ESXi variants reinforce that no operating system or platform can be considered safe from modern ransomware campaigns.
Mitigating risk from LockBit 5.0
Organizations are highly encouraged to evaluate and enhance their security posture by proactively conducting threat hunting activities tailored to group-specific tools, tactics, and procedures. It is essential to reinforce both endpoint and network protections, as well as early detection of defense evasion techniques aimed at compromising security solutions.
Proactive security with Trend Vision One™
Trend Vision One️™ is the only AI-powered enterprise cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection. This holistic approach helps enterprises predict and prevent threats, accelerating proactive security outcomes across their respective digital estate. With Trend Vision One, you’re enabled to eliminate security blind spots, focus on what matters most, and elevate security into a strategic partner for innovation.
Trend Vision One™ Threat Intelligence
To stay ahead of evolving threats, Trend customers can access Trend Vision One™ Threat Insights, which provides the latest insights from Trend Research on emerging threats and threat actors.
Trend Vision One Threat Insights
Emerging Threats: LockBit Strikes Again: Updates in Version 5.0
Trend Vision One Intelligence Reports (IOC Sweeping)
LockBit Strikes Again: Updates in Version 5.0
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
LockBit File Renaming with 16-Character Extension
eventSubId: 106 AND objectFilePath: /\.[a-f0-9]{16}$/ AND NOT srcFilePath: /.+\.[a-f0-9]{16}$/
LockBit 5 Ransom Note — ReadMeForDecrypt.txt
eventSubId: 101 AND objectFilePath: ReadMeForDecrypt.txt
More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement enabled.
Indicators of Compromise
Indicators of compromise can be found here.

