
Immediate response
When your organization is breached, every second is vital. Our Incident Response team and tools immediately begin monitoring, identifying, and containing.

Expert advice
While threat experts analyze the attack, our incident response professionals act fast to provide your team with a customized response plan. Eradicate the threat and bolster your defenses with their expert insight to prevent future attacks.

Advanced threat intelligence
Using Trend’s industry-leading security technologies and deep threat analysis, we provide a full view of each incident, from determining the point of entry to providing a complete infection timeline, with forensic analysis and recommendations to evolve your security strategy.
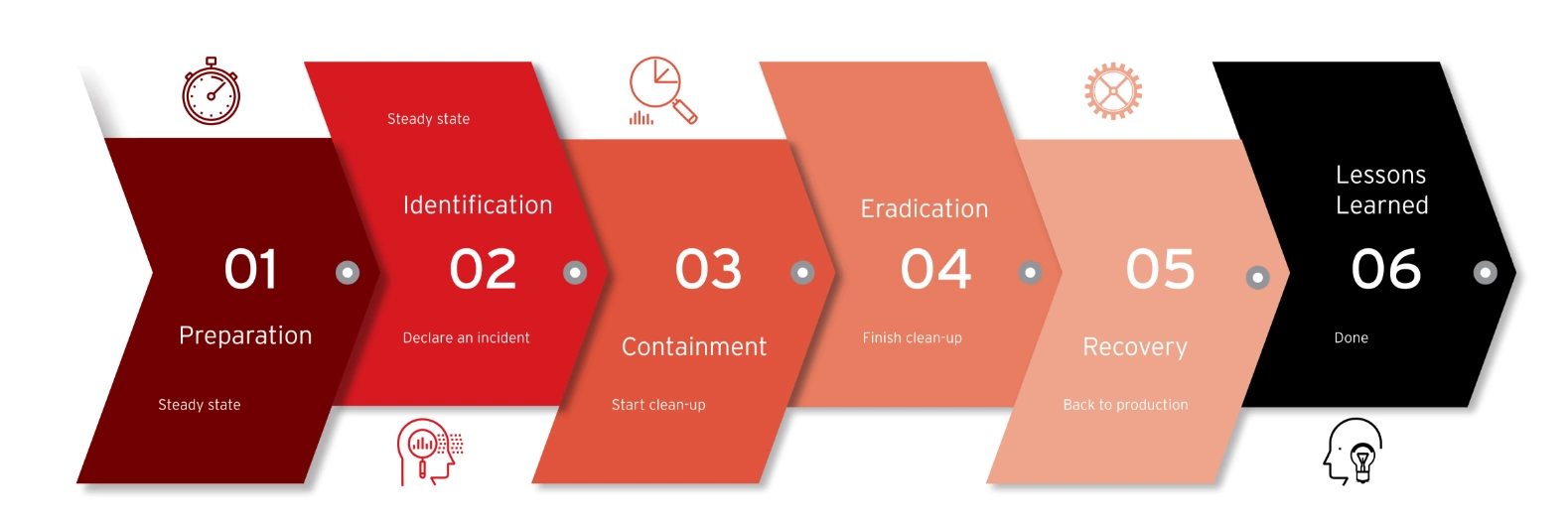
Supporting you step by step
We structure our Incident Response engagements along the SANS incident response model, an industry standard proven to be fast and decisive. Our team will assist you throughout the process to:
- STOP the ongoing attack in its tracks
- START rebuilding your production environment by localizing unaffected assets and backups
- HARDEN your network, servers, and endpoint defenses to protect against future attacks
Why managed security operations makes business sense
According to ESG, organizations with Trend Vision One™ achieved
- 2.43 million average cost savings from improvement in customer churn
- 1.3 million average cost savings from alleviated risk exposure
- 65% reduction of dwell time

Why Trend Micro™ Incident Response
Complement your team with advanced threat intelligence
Rapid, thorough analysis
Maintaining an in-house IR team with the skills, training, and time to manage breaches can seem impossible. The expanding digital attack surface, evolving threats, and the complexity of cloud environments only add to the challenge.
Trend’s Incident Response team correlates alerts from multiple sources to rapidly identify a breach’s point of origin. Threat researchers enhance automated root cause analysis (RCA) and package their findings along with a remediation plan for step-by-step guided response.
In-depth investigation
Simply sealing the point of entry won’t stop a breach. Securing your network requires mapping vulnerabilities, identifying exfiltrated data, and determining how far the original threat managed to spread throughout your network.
Our team can help by:
- Sweeping for indicators of compromise (IoCs) to map the extent of the attack
- Determine threat profile for effective response
- Monitoring your environment during the recovery process
Effective, guided response
The Incident Response team provides full documentation of every incident in the Targeted Attack Handling Report, a comprehensive guide that demonstrates how to improve your cybersecurity posture and meet compliance obligations.
Each report includes:
- The breach’s point of entry
- An infection timeline
- Observed Tactics, Techniques and Procedures (TTP) following the MITRE ATT&CK matrix
- Forensic analysis with a full list of IoCs
- Recommendations to prevent future attacks

See what our customers have to say on Gartner Peer Insights
JOIN 500K+ GLOBAL CUSTOMERS
Respond to breaches with fast and effective support

