Modern ransomware operators were quite active in the third quarter of 2021, specifically the distributors of the REvil (aka Sodinokibi) ransomware family. In early July, it was reported that malicious actors exploited zero-day vulnerabilities in the IT management platform Kaseya’s VSA software to push a malicious script onto vulnerable customers. Typically used by Kaseya to provide updates to customers, VSA was weaponized by the malicious actors to load the REvil ransomware. This ransomware is known for employing double extortion tactics to further motivate targets into paying their ransom.
We have also been tracking the LockBit ransomware group, which resurfaced with LockBit 2.0 in July and August. This version supposedly has one of the fastest and most efficient encryption methods active today. It also tries to recruit more affiliates by promising “millions of dollars” to company insiders who can provide the group with credentials and access.
The following data shows the landscape of ransomware families, both legacy and more modern threats, in the third quarter of 2021, during which we detected and blocked a total of 3,462,489 ransomware threats across our email, file, and URL layers. Our tracking and investigation covered the families themselves and the types of industries and enterprises that were targeted.
Top five ransomware detections by segment
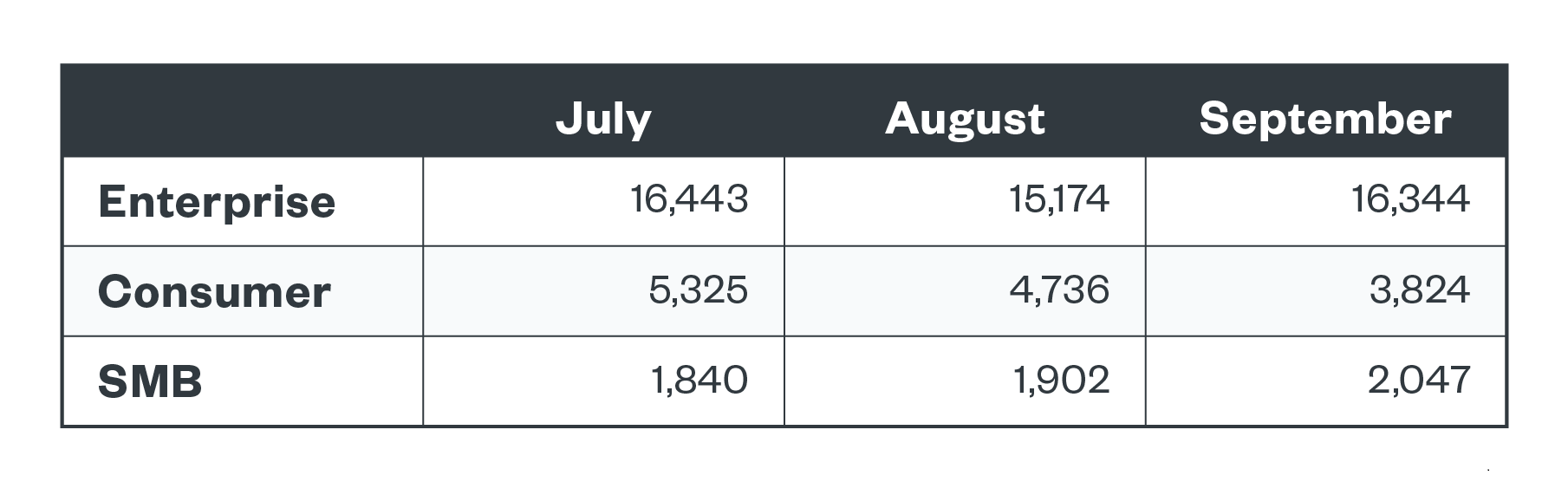
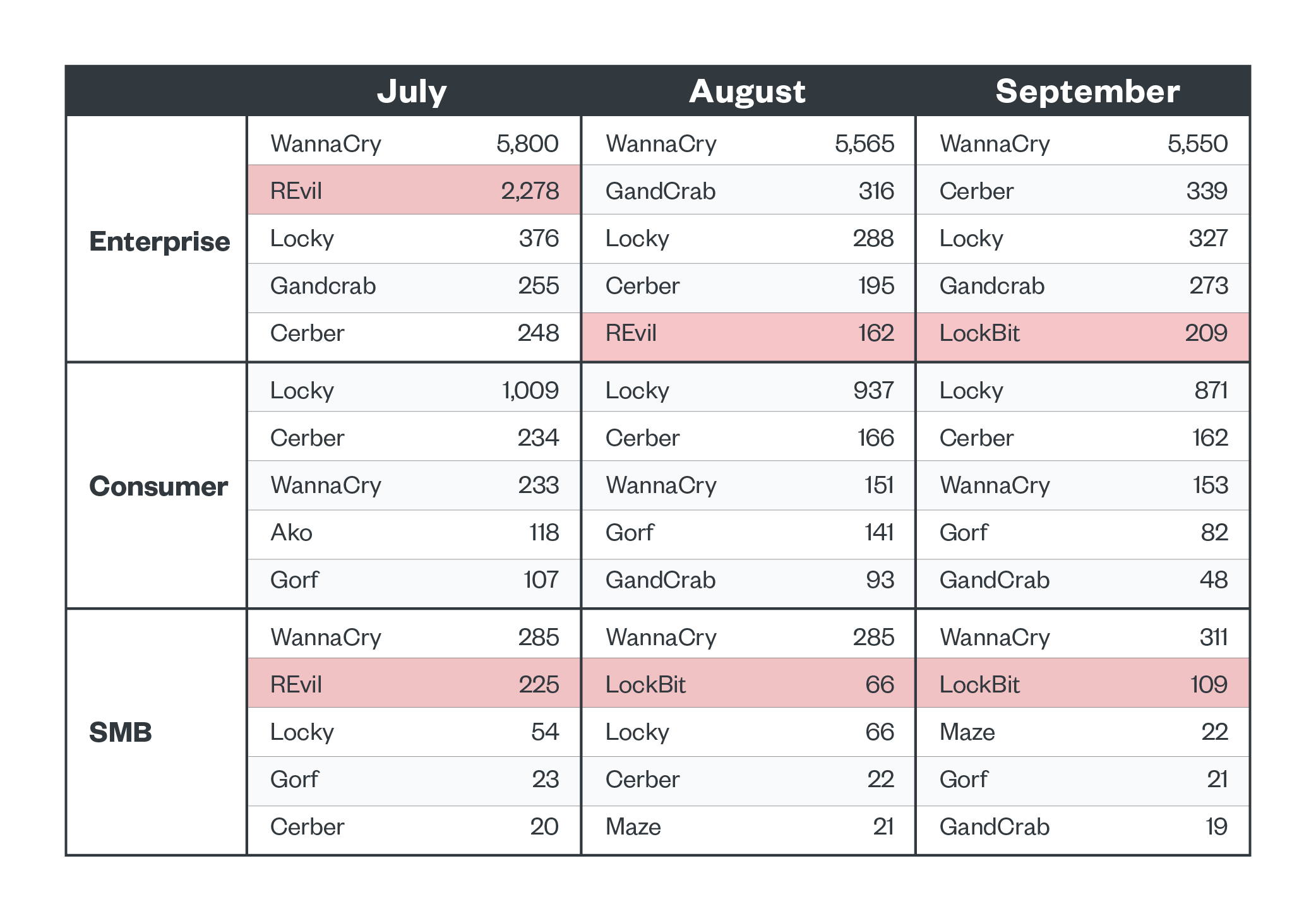
REvil detections peaked in July and LockBit appeared in August and September. Their targets were enterprises and small and medium-sized businesses (SMBs). Legacy ransomware families WannaCry and Locky were also active across all segments. WannaCry was the top detected family in the enterprise segment across all three months, and Locky was the top detected family in the consumer segment. The early July spike in REvil detections in enterprise organizations coincided with the reports about the Kaseya compromise.
Figure 1. Ransomware file detections across business segments in the third quarter of 2021
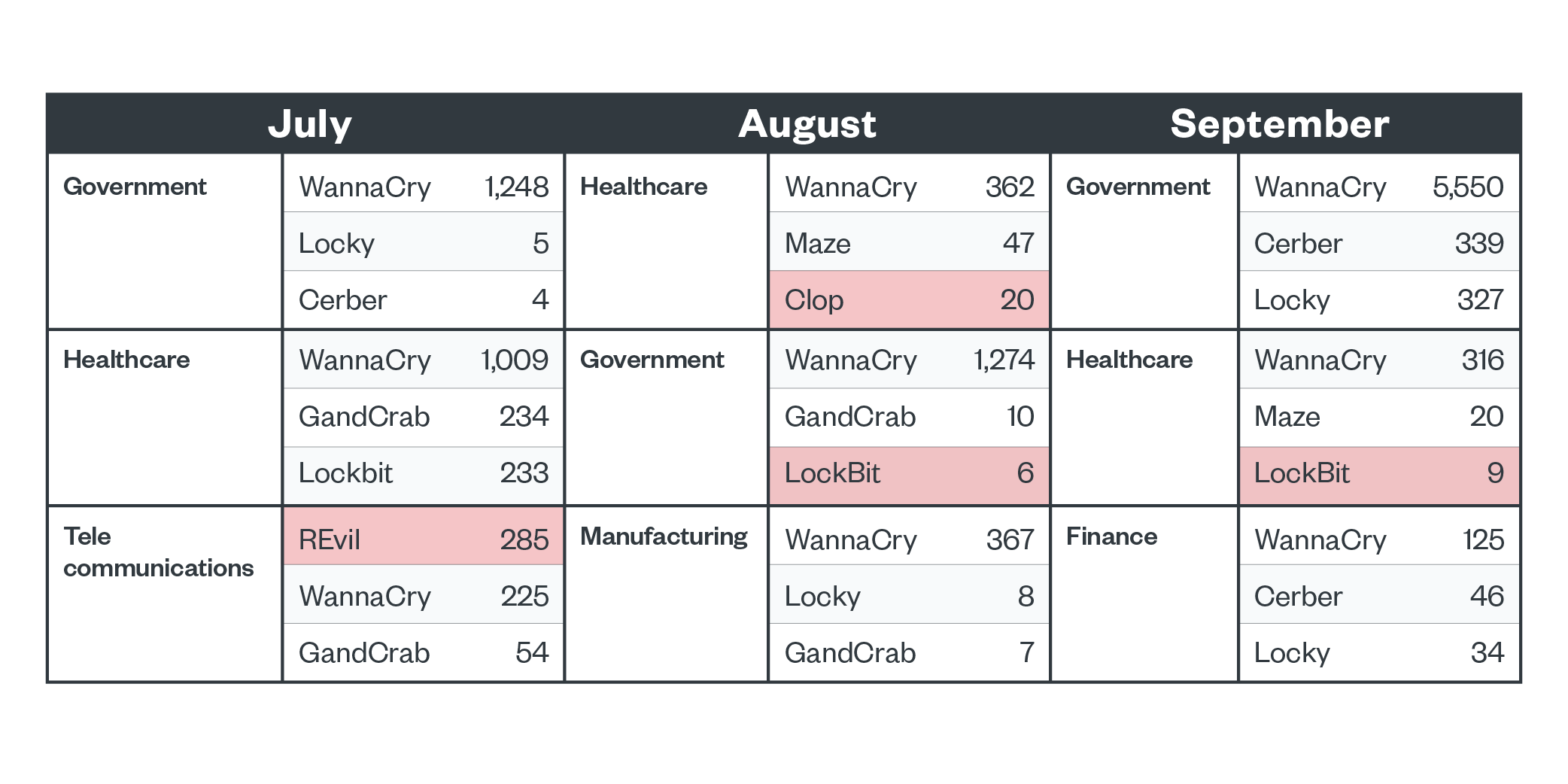
Figure 2. The top five ransomware families detected per business segment in the third quarter of 2021 (REvil and LockBit highlighted to show activity in connection with news reports)
Top 10 ransomware families
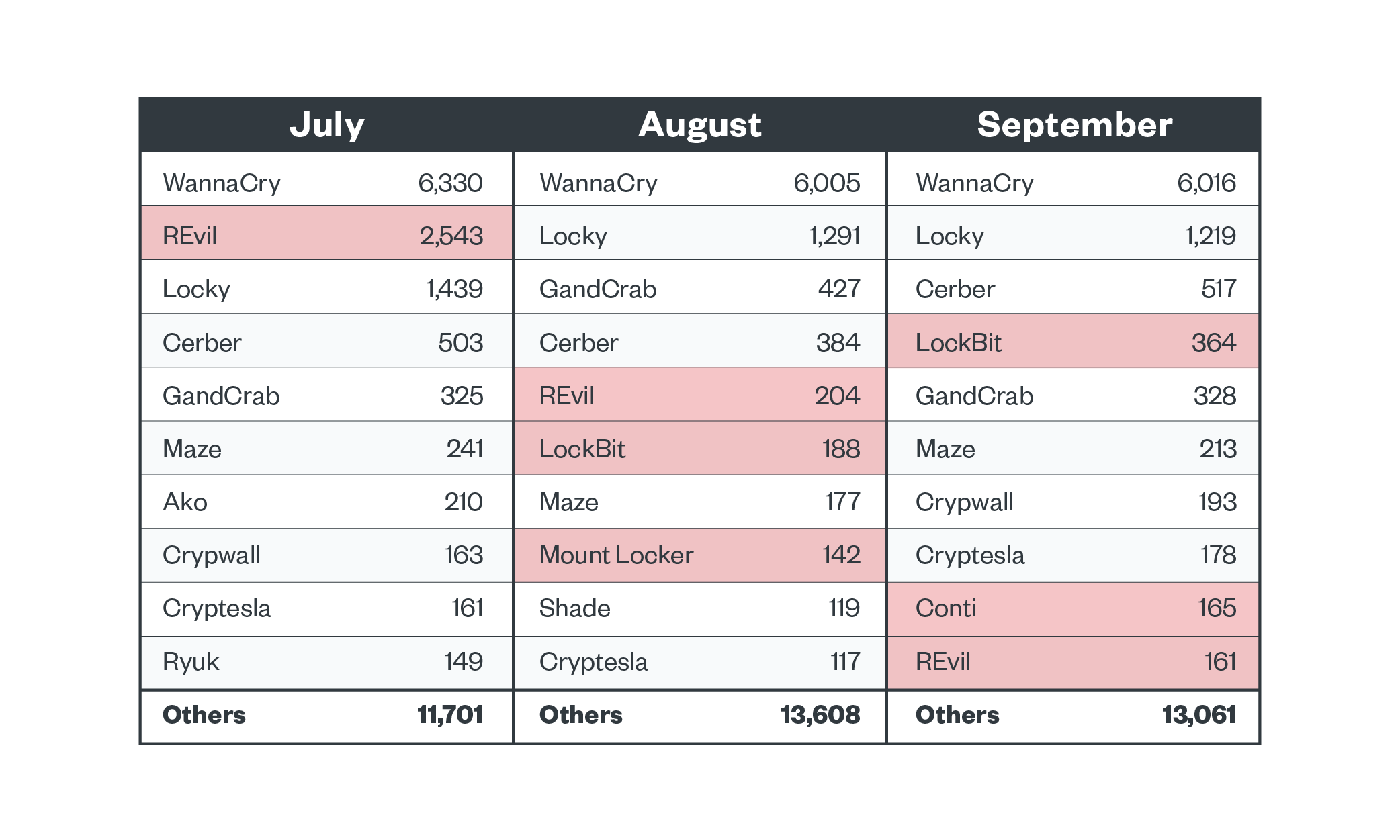
The legacy ransomware families WannaCry, Locky, Cerber and GandCrab were consistently detected throughout the third quarter of 2021. Meanwhile, more modern ransomware families such as REvil and LockBit were more volatile. Operators of modern ransomware families usually choose their targets carefully and deploy their payloads more discriminately, and thus the activity of these families is more erratic.
Conti was also notably active during this period. In September, the Cybersecurity and Infrastructure Security Agency (CISA) and the FBI reported that they had observed more than 400 attacks that used Conti against US and international organizations. Mount Locker operations were also detected during this time, and in later months new business models connected to this family were found.
Figure 3. The top ransomware families active in the third quarter of 2021 (notable families highlighted)
Top three industries with ransomware detections
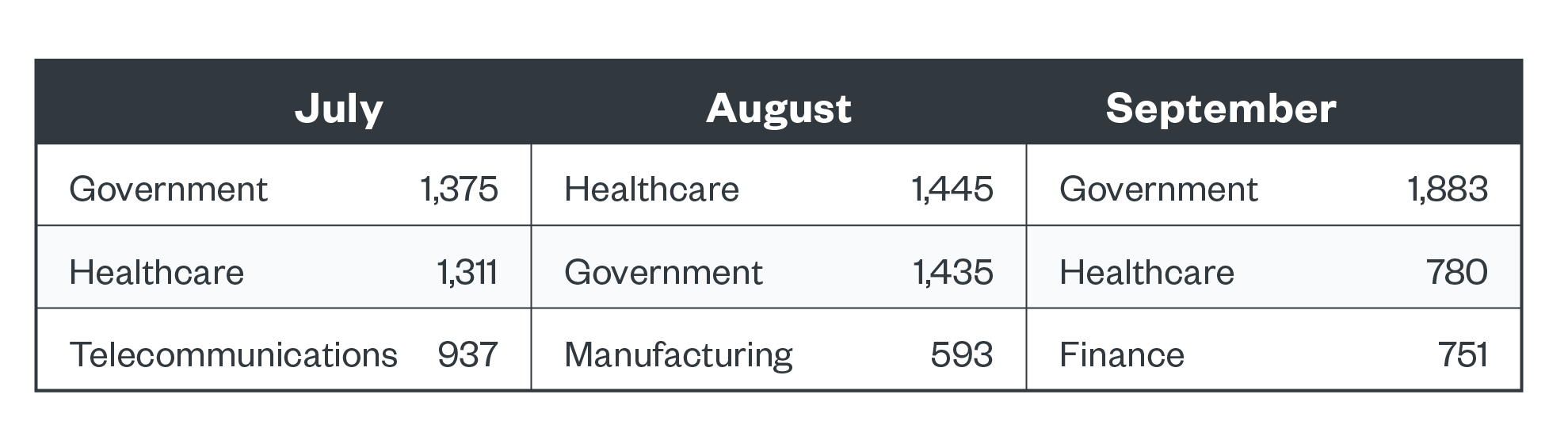
The government and healthcare industries were consistently the top two ranked in terms of ransomware detections. The telecommunications, manufacturing, and financial industries were also heavily targeted in this three-month span. There was a spike in REvil activity, and we saw the increase in activity happening specifically in the telecommunications industry. Meanwhile, LockBit was detected in government and healthcare organizations, and we also saw Clop detections within the healthcare industry. Clop is a modern ransomware family that has varied and progressively devastating extortion techniques.
Figure 4. The top three industries in terms of ransomware file detections in the third quarter of 2021
Figure 5. The top three ransomware families affecting the top-ranking industries in the third quarter of 2021 (notable families highlighted)
Top five countries with ransomware detections
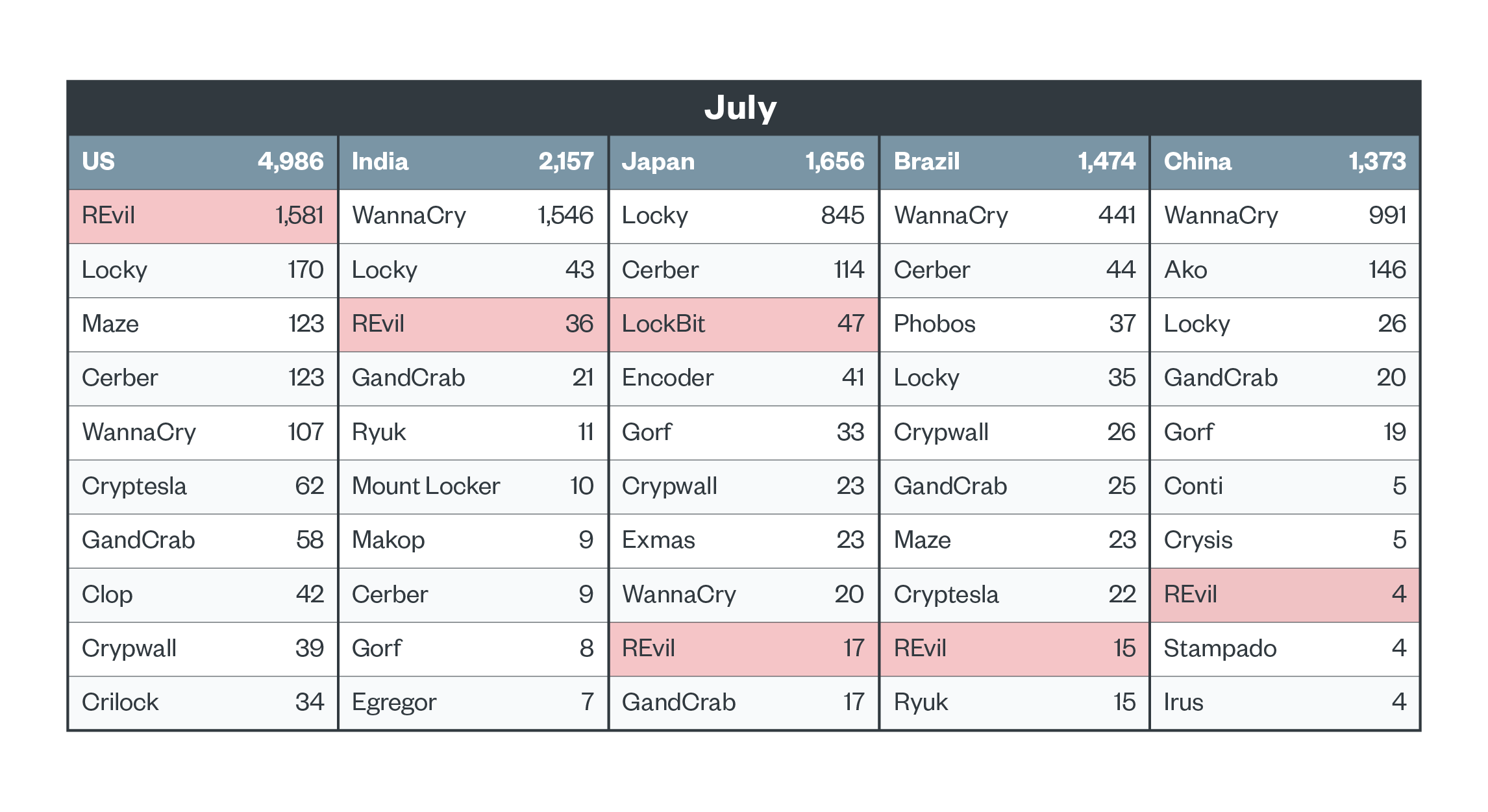
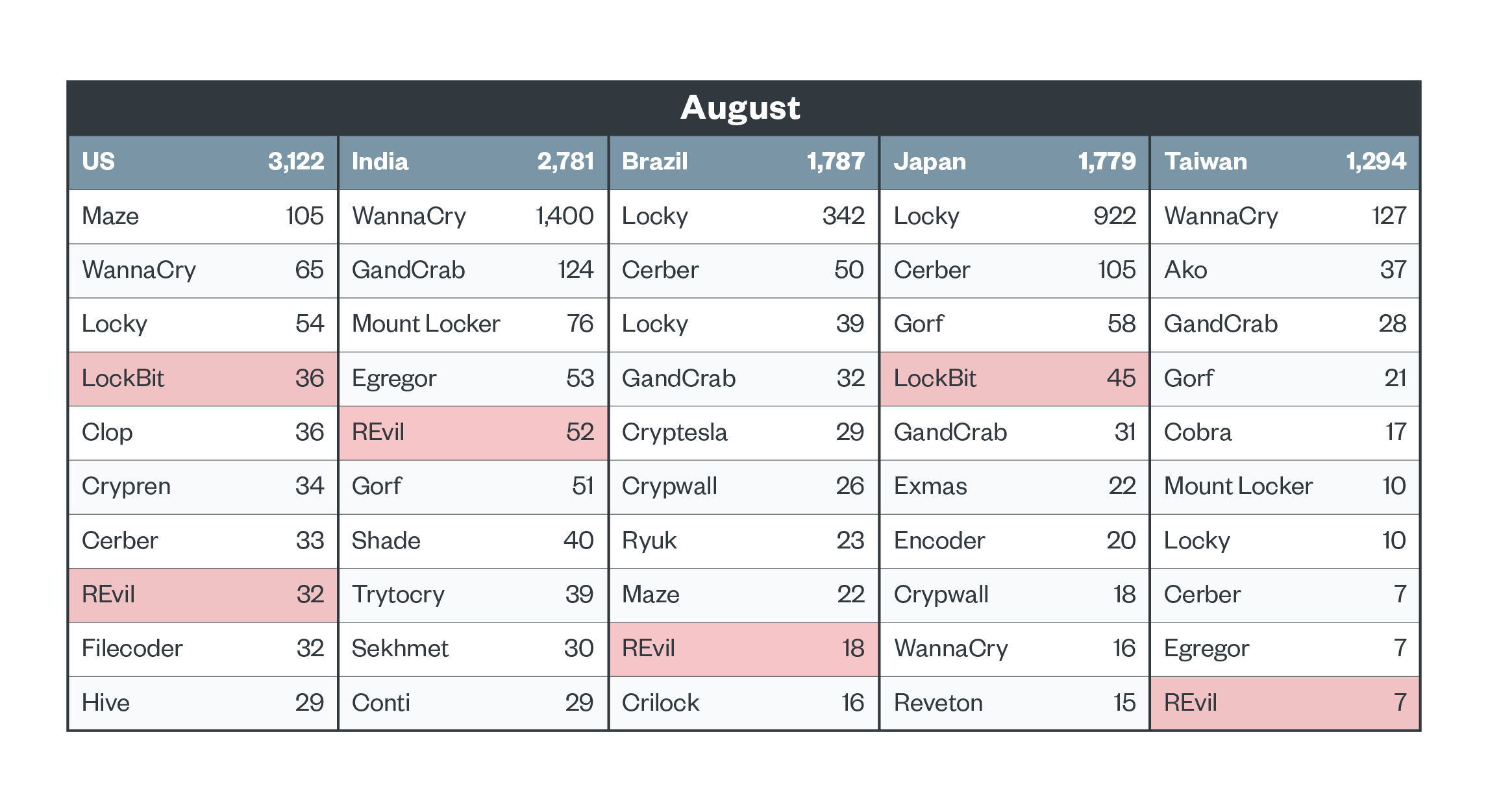
As previously mentioned, modern ransomware activity is more volatile because of focused targeting. This is seen in the case of REvil, which peaked in July in the US and virtually disappeared by September. REvil activity also declined in other countries, although low numbers were steadily observed in Brazil and Japan. Meanwhile, LockBit appeared in Japan in July, and gained traction. It was seen hitting more targets around the world in September.
Figure 6. The top five countries in terms of ransomware file detections and the top 10 ransomware families detected in each in July 2021 (notable families highlighted)
Figure 7. Top five countries in terms of ransomware file detections and the top 10 ransomware families detected in each in August 2021 (notable families highlighted)
Figure 8. Top five countries in terms of ransomware file detections and the top 10 ransomware families detected in each in September 2021 (notable families highlighted)
How to deter ransomware and minimize its impact
Ransomware is a persistent danger to enterprises, especially considering that the tools and techniques used by operators of this threat continue to evolve. Organizations can mitigate the risks of modern ransomware by investing in cross-layered detection and response solutions that can anticipate and respond to ransomware activities, techniques, and movements before operators can launch an attack. One such solution is the cybersecurity platform Trend Micro Vision One™️ with Managed XDR, which helps detect and block ransomware components to stop threat actors before they exfiltrate sensitive data.
Further protecting enterprises, network detection and response (NDR) enables organizations to monitor network traffic and respond to malicious activity and suspicious behavior at the network layer and beyond. In addition to preventing zero-day attacks, Trend Micro Network One delivers critical network telemetry to Trend Micro Vision One, enabling security operations teams to get a clearer picture of their environment, accelerating response, and preventing future attacks.
Download our ransomware detection data for the third quarter of 2021 here.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Archive
- Phobos Emerges as a Formidable Threat in Q1 2024, LockBit Stays in the Top Spot: Ransomware in Q1 2024
- Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023
- LockBit, BlackCat, and Clop Prevail as Top RAAS Groups: Ransomware in 1H 2023
- LockBit, BlackCat, and Royal Dominate the Ransomware Scene: Ransomware in Q4 2022
- LockBit and Black Basta Are the Most Active RaaS Groups as Victim Count Rises: Ransomware in Q2 and Q3 2022


 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks Today’s Cloud and Container Misconfigurations Are Tomorrow’s Critical Vulnerabilities
Today’s Cloud and Container Misconfigurations Are Tomorrow’s Critical Vulnerabilities Ransomware Spotlight: INC
Ransomware Spotlight: INC The Realities of Quantum Machine Learning
The Realities of Quantum Machine Learning