ANDROIDOS_FAKEBROWS.A
Trojan-SMS.AndroidIS.FakeInst.h (Kaspersky), Android/TrojanMS.FakeInst.B trojan (Nod32)
Premium Service Abuser
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This malware uses social engineering methods to lure users into performing certain actions that may, directly or indirectly, cause malicious routines to be performed. Specifically, it disguises as a mobile web browser Opera Mini. Once the user agreed with the services of the fake browser, it sends text messages to premium numbers.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
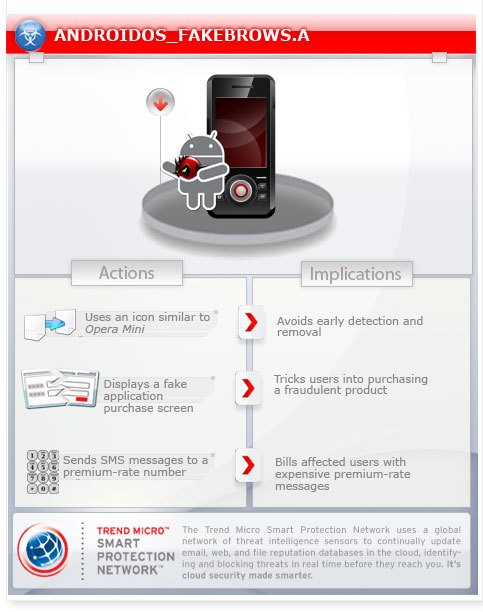
This Trojan may be unknowingly downloaded by a user while visiting malicious websites. It may be manually installed by a user.
It bears the file icons of certain applications to avoid easy detection and consequent removal.
TECHNICAL DETAILS
Arrival Details
This Trojan may be unknowingly downloaded by a user while visiting malicious websites.
It may be manually installed by a user.
Installation
This Trojan bears the file icons of the following applications:
- Opera Mini
NOTES:
This application disguises itself as the mobile web browser, Opera Mini.
Upon execution, it displays the following message:
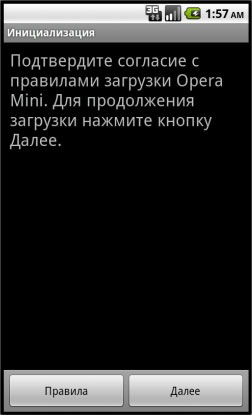
The text translates as:
- Title: Initialization
- Body: Confirm agreement with the rules of loading Opera Mini. To continue downloading, click Next.
- Button Правила: Rules
- Button Далее: Next
When the user clicks the button Правила (Rules), the following interface is displayed:

The text in the rules describe the prices of using the services of the fake browser. Payment is made by sending text messages to premium numbers in Kazakhstan, Russia, Ukraine, Latvia, Lithuania, or Estonia.
The buttons translate to (from left to right) Back and Next. Clicking the left button (Back) will bring the user back to the first screen.
When the user clicks the button Далее (Next) in either the first or second interface, it sends the text {prefix} 1oZpW none android {suffix} to a number via SMS. {prefix}, {suffix} and the number can be any of the following:
| {prefix} | {suffix} | Number |
| 7539 | . | 69991 |
| 7539 | . | 4545 |
| 79fgh | . | 7061 |
| 79fgh | . | 1060 |
| 79fgh | . | 4909 |
| 7539 | . | 55886 |
| 7539 | . | 4157 |
| 7539 | . | 4156 |
| 7539 | . | 4153 |
| 7539 | . | 5339 |
| 7539 | . | 2322 |
| 4722 | . | 2855 |
| 4722 | . | 9151 |
| 4722 | . | 7151 |
| 7539 | . | 1874 |
| 7539 | . | 1873 |
| 7539 | . | 1872 |
| 7539 | . | 81185 |
| 7539 | . | 81015 |
| 7830 | . | 9683 |
| 7830 | . | 9685 |
| 7539 | . | 19998866 |
| 7539 | . | 69067 |
| 7539 | . | 1945 |
| 40416 | . | 3302 |
| 40416 | . | 3303 |
| 40416 | . | 9818 |
| 40416 | . | 3302 |
| 40416 | . | 3303 |
| ce277 | . | 8161 |
| ce277 | . | 4449 |
| ce277 | . | 4446 |
| 7539 | . | 930399999 |
| 7539 | . | 17013 |
| 7539 | . | 17012 |
| 7539 | . | 17011 |
| 7539 | . | 1098 |
| 7539 | . | 57575 |
| 7539 | . | 90645045 |
| 7539 | . | 7910 |
| 7539 | . | 9090150 |
| 7539 | . | 9090199 |
| 7539 | . | 5040 |
| 40416 | . | 3339 |
| 40416 | . | 3336 |
| 7539 | . | 1645 |
| 7539 | . | 1635 |
| 7539 | . | 1391 |
| 7539 | . | 72170 |
| 7539 | . | 80888 |
| 7539 | . | 7796 |
| ce277 | . | 4107 |
| ce277 | . | 4106 |
After sending SMS messages, it displays the following:
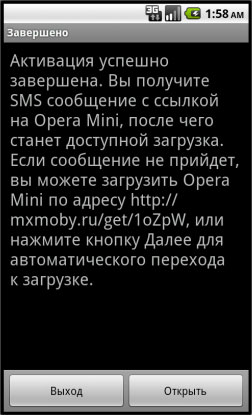
- Title: Completion
- Body: Activation was successful. You will receive an SMS message with the link to Opera Mini, which will be available after rebooting. If the message does not arrive, you can download Opera Mini at http://{BLOCKED}y.ru/get/1oZpW, or click Next to automatically reboot.
- Button Выход: Exit
- Button Открыть: Open
SOLUTION
Step 1
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android smartphones and tablets from malicious and Trojanized applications. The App Scanner is free and detects malicious and Trojanized apps as they are downloaded, while SmartSurfing blocks malicious websites using your device's Android browser.
Download and install the Trend Micro Mobile Security App via Google Play.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.


