Ransomware Recap: Oct. 24- Nov. 4, 2016
 Locky, one of the most prominent ransomware families to have surfaced of late, continues to make its presence felt with updated propagation methods and infection routines. At the beginning of September, a modified version of Locky (detected by Trend Micro as RANSOM_HPLOCKY.SM51) was discovered to have adopted new routines with a variant that shows hardcoded RSA keys that allow the malware to run without the need for C&C server communication. On the other hand, by the tail-end of the same month, researchers discover a variant of Locky (with samples detected by Trend Micro as RANSOM_LOCKY.AE and RANSOM_LOCKY.AC) that appended .odin to affected files, an extension name that is new to the ransomware variant.
Locky, one of the most prominent ransomware families to have surfaced of late, continues to make its presence felt with updated propagation methods and infection routines. At the beginning of September, a modified version of Locky (detected by Trend Micro as RANSOM_HPLOCKY.SM51) was discovered to have adopted new routines with a variant that shows hardcoded RSA keys that allow the malware to run without the need for C&C server communication. On the other hand, by the tail-end of the same month, researchers discover a variant of Locky (with samples detected by Trend Micro as RANSOM_LOCKY.AE and RANSOM_LOCKY.AC) that appended .odin to affected files, an extension name that is new to the ransomware variant.
Interestingly, it appears that new variants of Locky are being released at a faster pace, with new variants adopting the use of new extension names more frequently than before. By the end of October, researchers have seen a new variant that appends the extension name .shit to its locked files. Samples analyzed by Trend Micro researchers (detected as RANSOM_LOCKY.DLDSAPY and RANSOM_LOCKY.DLDSAPZ) exhibit similar behaviors as seen in previously-detected variants. It arrives via spam and, when executed, will download a DLL file before carrying out its encryption routines. Another sample (detected by Trend Micro as RANSOM_LOCKY.R011H0DJP16) with a similar routine downloads an executable file. Upon encryption of target files, it renames locked files with random characters before adding the extension name.
Not long after this discovery, a new variant of Locky was observed using another extension name: .thor. This particular variant (with samples detected by Trend Micro as RANSOM_LOCKY.DLDTAPZ and RANSOM_LOCKY.THOR) is known to be distributed by spam, while other samples were seen being pushed by Sundown exploit kit. As with previous variants, it enables the download of an encrypted DLL attachment that will then be executed on the target’s machine before the encryption gets fully carried out.
During the same week, researchers discovered another ransomware variant that may look like the notorious Locky, but turned out to be a “cheap knockoff”. Named Hucky (detected by Trend Micro as RANSOM_LOCKY.DLDSAQI), or Hungarian Locky by researchers, this ransomware shares some similarities with Locky, but is simply an imitation of the original.
While most versions of Locky retrieve its public RSA key by communicating with a C&C server, Hucky has its key hardcoded in it. Once executed, this variant displays a Word document that distracts the target while its encryption routine runs in the background. Researchers also noted that Hucky only goes after half of the file types commonly encrypted by Locky. It then appends the extension, .locky and forces the infected machine to restart after the file encryption is done—a routine that has never been seen in past Locky variants.
The ransom note, targeted at Hungarian-speaking users, bears resemblance to Locky, but shows signs of it being a less sophisticated version. It contains instructions to email its operator on a provided Mail2Tor address, instead of an automated Tor website commonly used by previously-seen Locky variants.
Here are some notable ransomware stories observed in the past two weeks:
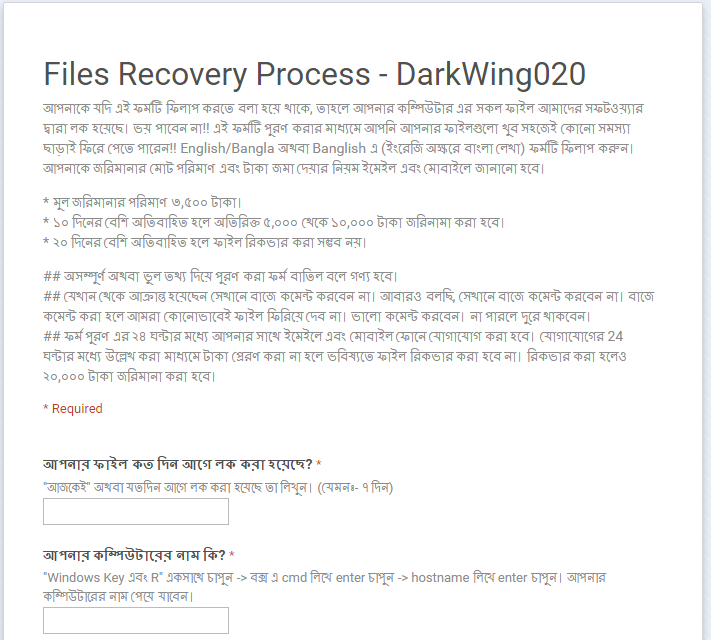
Written in Bengali, the official state language of Bangladesh, the ransom note demands a payment of 3,500 rupees (equivalent to over US$50), with instructions sent via email and SMS. This then increases to 5,000 to 10,000 rupees (around $74 to $140) if not settled within a 10-day period. Interestingly, the ransom note identifies the developer behind this particular variant—a hacker using the moniker, DarkWing020.
ANGRY DUCK

Angry Duck ransomware (detected by Trend Micro as RANSOM_ANGRYDUCK.A) was discovered around the last week of October, encrypting files using AES-512 cryptography. After encryption, files are appended with the extension .adk. Following successful infection, this ransomware changes the victim’s desktop wallpaper with a ransom note containing an image of an angry duck, and a ransom demand of 10 bitcoins. The ransom amounts to almost US$ 7,300—a rather hefty sum of money compared to more common ransom prices seen of late.
EncrypTile
EncrypTile (detected by Trend Micro as RANSOM_ENCRYPTILE.A) emerged by the tail-end of October, exhibiting behavior common to earlier variants. This particular family encrypts files using AES and RSA cryptography and appends the string EncrypTile to the file name of the encrypted files. For instance, a file named “image.jpg” when encrypted by this ransomware becomes “image.jpgEncrypTile”.
It demands a ransom of 0.05 bitcoins (around US$36) in exchange for the decrypt key. A pop-up window containing a countdown timer, bitcoin address, a list of locked files, and a video on how to decrypt files , is also displayed. If the ransom is not paid within the prescribed period, the files will be permanently deleted. Victims are also allowed to send one file that can be decrypted for free to an email address that uses a .ph (Philippines) country domain extension, which is believed to be the first ransomware of its kind using this. This is commonly done to convince users that paying for the decrypt key works.
LOCK93 and ISHTAR
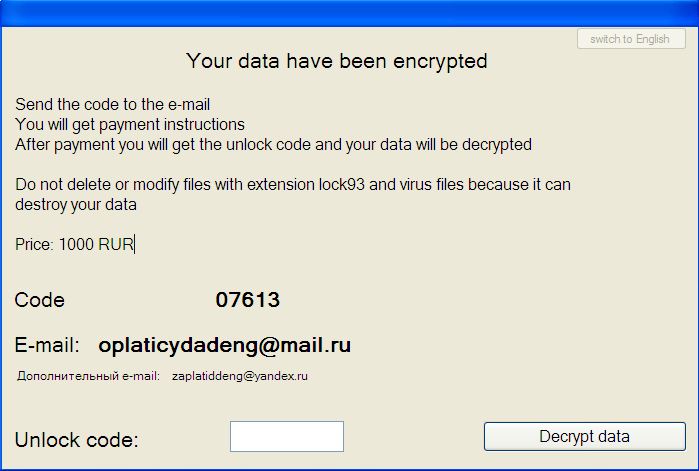
Lock93 (detected by Trend Micro as RANSOM_LOCK93.A) also surfaced late in October, adding the extension .lock93 to its infected files. Upon successful encryption, it displays a ransom note written in Russian. Translated, the note instructs the user to send a code to a provided email address. An indicated ransom of 1000 RUR ($15) is also demanded from the victim.
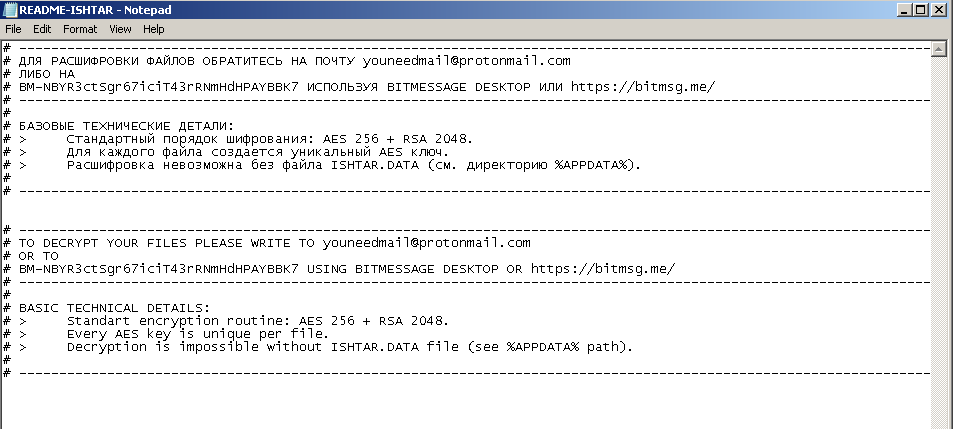
The following week, another ransomware variant was reportedly seen predominantly targeting a Russian-speaking victim base. ISHTAR (detected by Trend Micro as RANSOM_ISHTAR.F116K3) creates a ransom note in a text file written in Russian and English. Interestingly, unlike other ransomware variants seen of late, this ransomware prepends the string ISHTAR- to each encrypted file’s file name. This means that a locked file named “sample.doc” becomes “ISHTAR-sample.doc” after encryption.
FAKELOCK.I and FAKELOCK.J
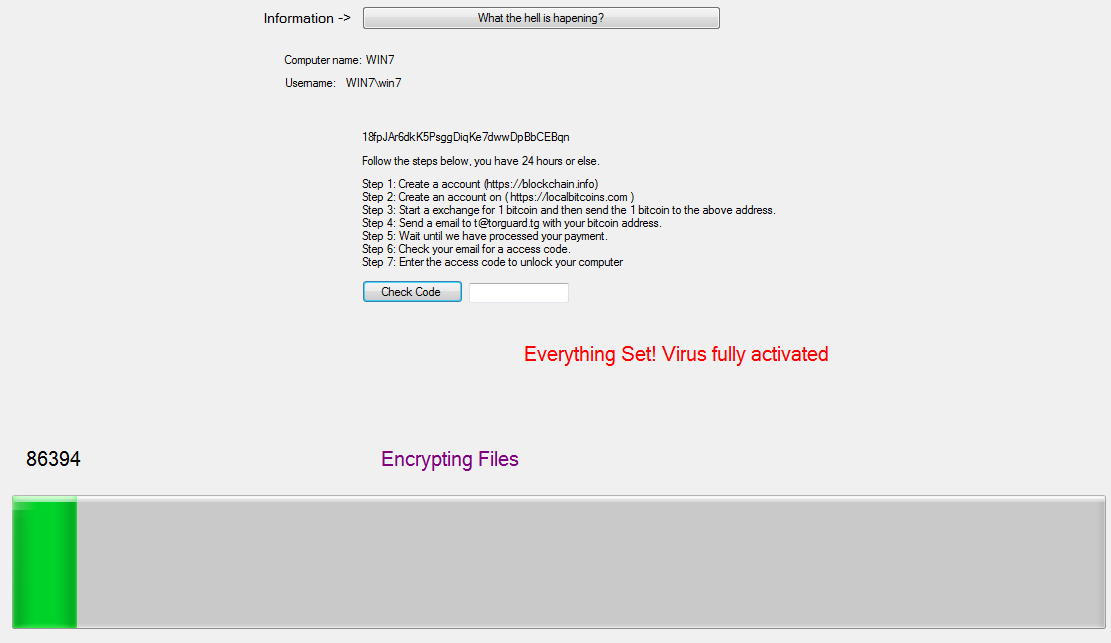
Two lockscreen ransomware were detected over the past two weeks. One variant (detected by Trend Micro as RANSOM_FAKELOCK.I) does not encrypt files found in the target systems. Instead, it disables the Command Prompt, Task Manager, and Registry Editor to prevent the victim from terminating the lockscreen. It tricks the user into believing that the encryption is ongoing by showing a loading bar that progresses and tells the user of the actions that are supposedly happening in the background.
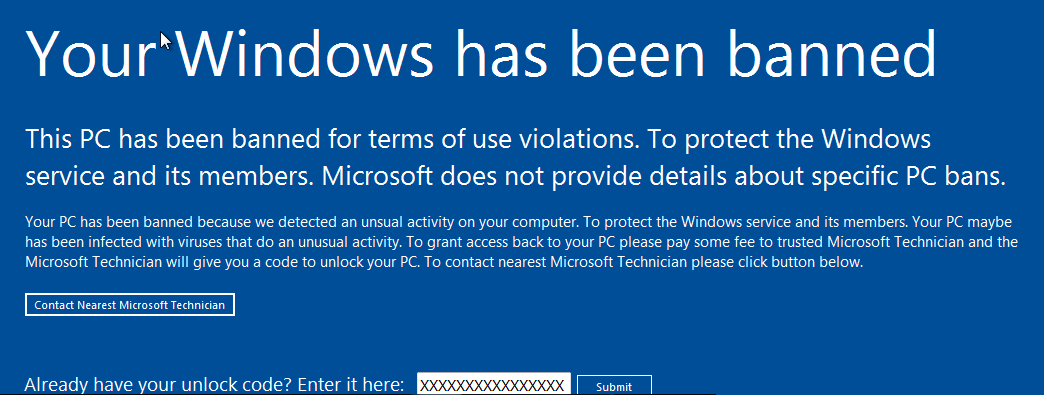
Another variant (detected by Trend Micro as RANSOM_FAKELOCK.J) locks the target machine and displays a fake notification saying that the victim’s machine has been banned, for “unusual activity”. It asks the user to send an undisclosed fee to a “trusted Microsoft Technician,” and advises the user to contact the technician for payment instructions. The code to unlock the screen will then be supplied by the said technician once the payment has been made.
ESMERALDA and KANGAROO
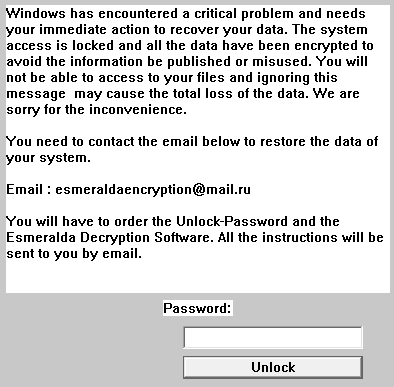
Esmeralda (detected by Trend Micro as RANSOM_ESMERALDA.A), a new variant of Apocalypse, was also sighted making its rounds over the last week of October. After the encryption routine, it appends the extension name .encrypted and displays a ransom note saying that the victim’s machine has “encountered a critical problem.” An email address is provided to establish communication between the victim and the developer.
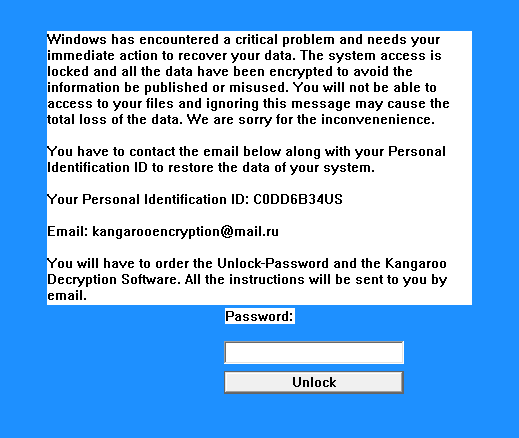
Not long after Esmeralda, another Apocalypse variant called Kangaroo (with samples detected by Trend Micro as RANSOM_APOCALYPSE.F116K4 and RANSOM_APOCALYPSE.E) was spotted last week. This particular variant uses the same trick as Esmeralda, feigning a “critical problem” in its would-be victim’s Windows. Following encryption, the extension .crypted_file is added to the locked file. While the ransom price is not disclosed in the note, it provides an email address that allows victims to communicate with the developers regarding payment instructions.
JACKPOT
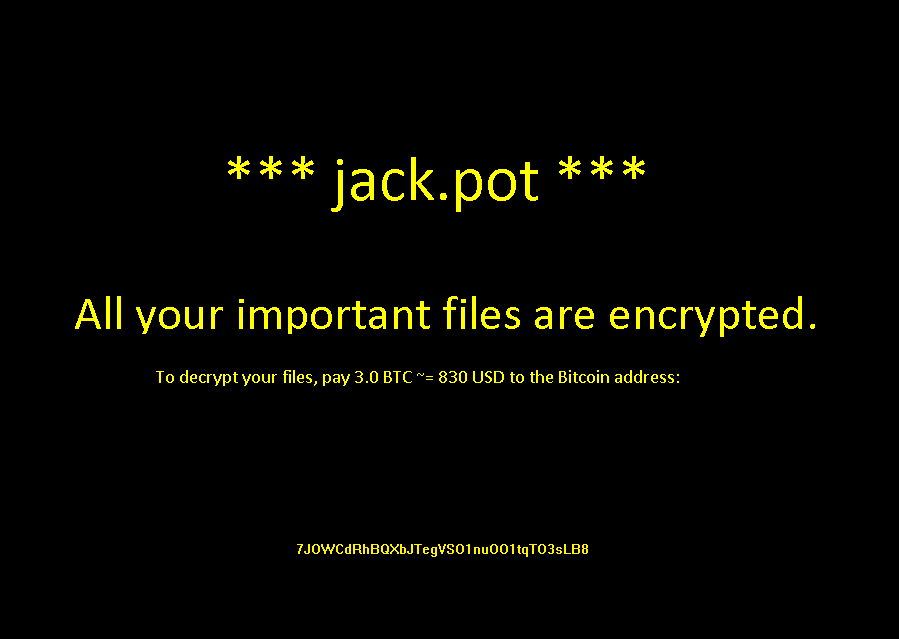
By the end of last week, a ransomware variant named Jackpot (detected by Trend Micro as RANSOM_JACKPOT.A) has surfaced. Following its encryption routine, it appends locked files with the extension .coin. The ransom note will also be displayed, asking a steep ransom payment of 3 bitcoins, which amounts to more than US$2,000. However, it was reported that the payment address provided belongs to a LiteCoin address instead of the Bitcoin address required for payment. Upon verification, Trend Micro researchers found that the address provided is, in fact, a LiteCoin address. This change, according to reports, shows that this is a "low-quality" ransomware.
ZEROCRYPT
Another ransomware variant that demands an uncommonly steep ransom emerged recently. ZeroCrypt (detected by Trend Micro as RANSOM_ZEROCRYPT.A) encrypts files with RSA-1024 algorithm and appends a .zn2016 extension to the file name of its locked files. Following encryption, a text file is created and left on the victim's desktop, serving as its ransom note.
The ransom note makes it one of the most expensive seen of late. It asks a ransom payment of 10 bitcoins—amounting to more than $7,300—for a single computer, while a decryption program for infections on multiple machines is priced at 100 bitcoins, or a hefty sum of over $73,000.
A multi-layered approach to defending against ransomware is key to keep all entry points in a system or a network safe from being infected. A solid backup strategy is also the most reliable way to mitigate damage from an infection.
Ransomware solutions:
Trend Micro offers different solutions to protect enterprises, small businesses, and home users to help minimize the risk of getting infected by ransomware:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
The Road to Agentic AI: Navigating Architecture, Threats, and Solutions