by Julie Cabuhat, Jay Yaneza, Gilbert Sison and Ryan Maglaque (Trend Micro Research)
Data from Trend Micro’s managed detection and response shows how the cybersecurity policies of organizations are reflected by the threats they most often face. For example, greater reliance on physical devices and local network shares for data transfer will no doubt lead to greater incidences of mass-spreading malware. Understanding the internal factors that cause organizations to be more prone to certain threats than to others is an important step toward better cybersecurity.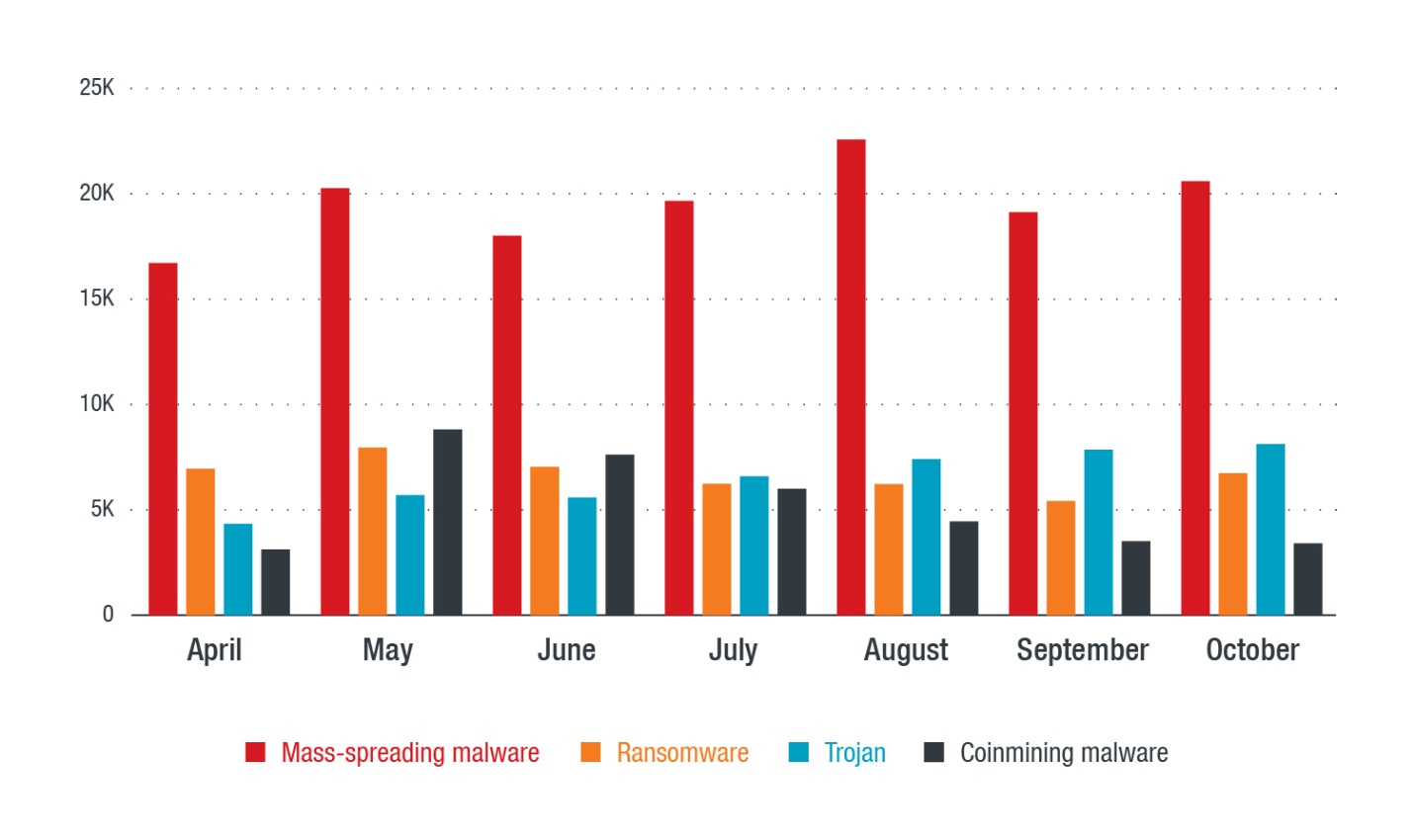 Figure 1. Comparison of threats on a per-month basis from April to September
Figure 1. Comparison of threats on a per-month basis from April to September
To illustrate how the most prevalent threats to organizations reflect internal policies, we looked at data from the Trend Micro™ Smart Protection Network™ infrastructure of South East Asia over a six-month period.
We can see that from the second to third quarters of 2018, older threats were at the forefront, with mass-spreading malware being the most prevalent threat. There is a notion that mass-spreading malware is old and outdated, which is why the volume of detections may come across as a surprise. Organizations looking at the global landscape may think that it is sufficient to put measures in place for threats that are taking center stage globally, such as “fileless” and cryptocurrency-mining malware. In this case, deploying solutions for these newer threats would be a mismatch.
Instead, cybersecurity investments should be tailored to the organization. As the data shows, threat actors do not necessarily abandon old methods at all times; they choose attacks depending on the weak points of an organization.
In the next sections, we look at more examples of behaviors that keep organizations vulnerable, and recommend policies to address them.
Unsecure data transfer mechanisms spread malware
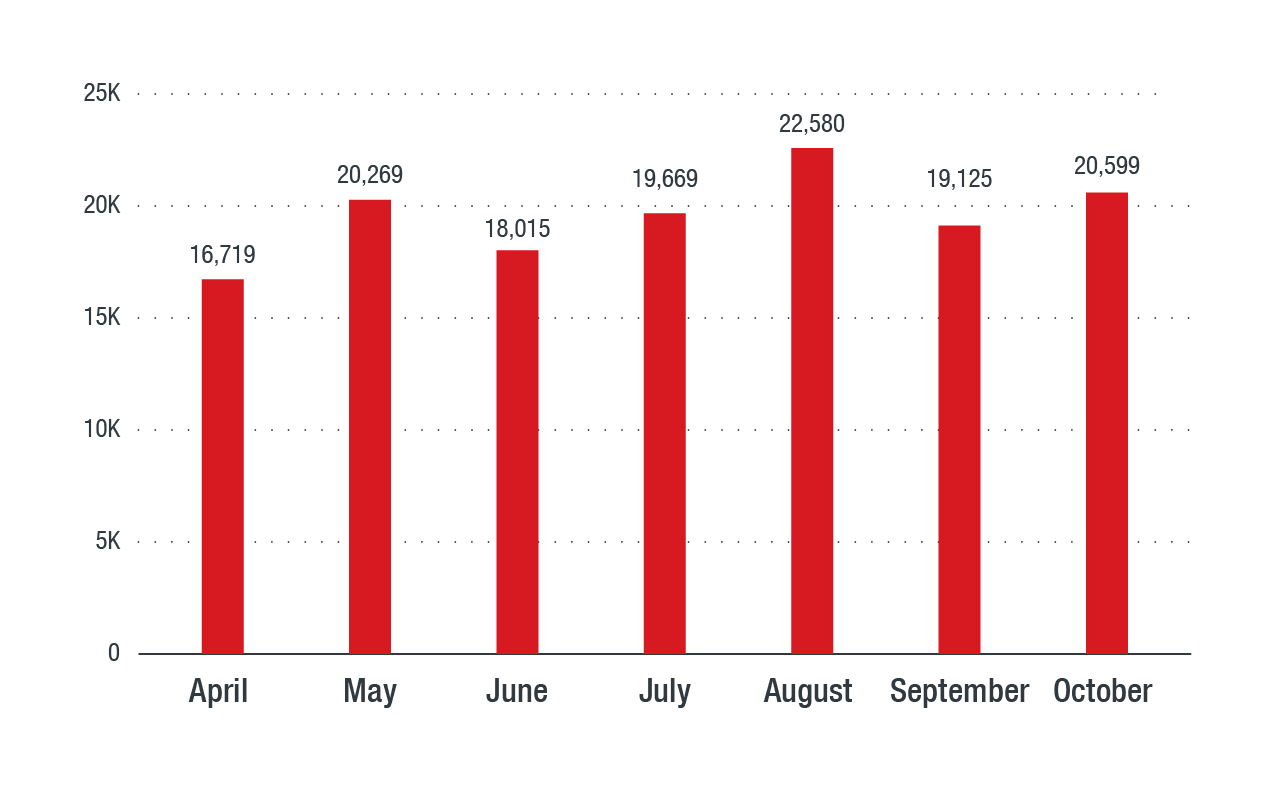 Figure 2. Mass-spreading malware detections on a per-month basis
Figure 2. Mass-spreading malware detections on a per-month basis
Given the challenges some countries in the region face when it comes to adopting cloud services, many companies, especially small and medium enterprises (SMEs), still rely on physical devices such USB flash drives and external hard drives, and on local network shares for transferring data within the organization. This kind of setup is a breeding ground for mass-spreading malware. It’s small wonder, then, that the count for mass-spreading malware was nearly equal to the combined total of the other three categories (ransomware, trojan, coinmining malware).
The mix is not limited to older malware either. While the oldest (Sality) was first seen over a decade ago, the most recent (Wmine) was first seen in 2017, using the same Server Message Block (SMB) vulnerability used by WannaCry.
Gamarue (aka Androm, Andromeda, or Bundpil), a binary that needs other components to function properly, was consistently the top mass-spreading malware, perhaps owing to its combination of worm and backdoor behaviors.
Recommendations
There are clear steps to reduce the number of mass–spreading malware, particularly through its main arrival vector. However, these are heavily dependent on IT administrators doing their part in protecting the network, including implementing best practices designed to tighten security in the organization, such as:
- Making sure that BYOD (bring your own device) policies are actually enforced.
- Identifying networks and users that will result in having privilege restrictions in place, thereby limiting the number of people that can add or modify files in shared network folders.
- Limiting access to shared networked drives only to those who actually need it.
- Blocking unnecessary ports on specific machines.
- Disabling the autorun functionality on all Windows machines to prevent malware that abuses this feature from affecting the system.
Irregular patching and updating habits lead to re-infections
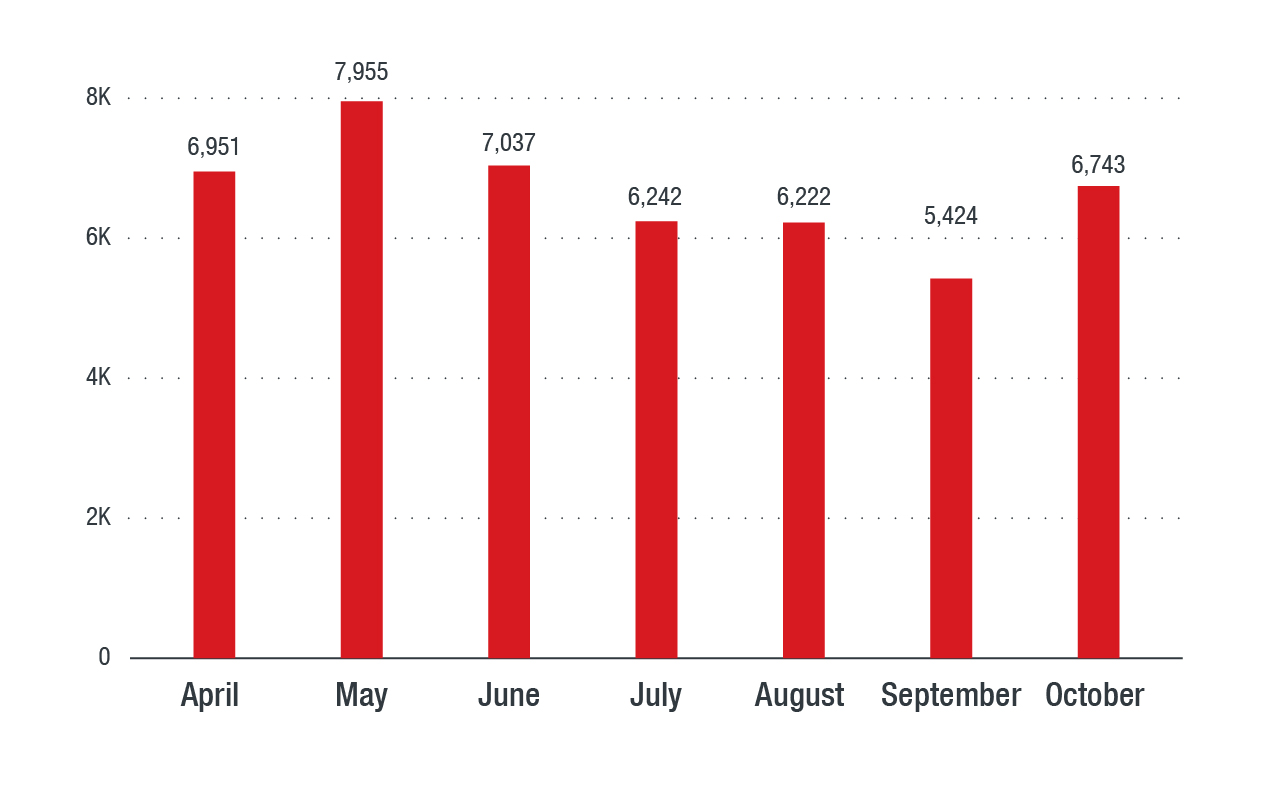 Figure 3. Ransomware detections on a per-month basis
Figure 3. Ransomware detections on a per-month basis
It’s been over a year since WannaCry (WCRY) first hit the globe,but numbers for Southeast Asia show that it is still going strong in the region. It is both the top malware family and the only ransomware family among the top malware families in Southeast Asia. Given the spread of WannaCry via older and unpatched operating systems, it’s possible that ransomware persistence is a direct reflection of poor patching habits.
Recommendations
WannaCry can be prevented from infecting a system if all systems in the network are consistently patched and updated, whereas leaving them unpatched can lead to continued re-infection.
Unregulated downloads distribute trojans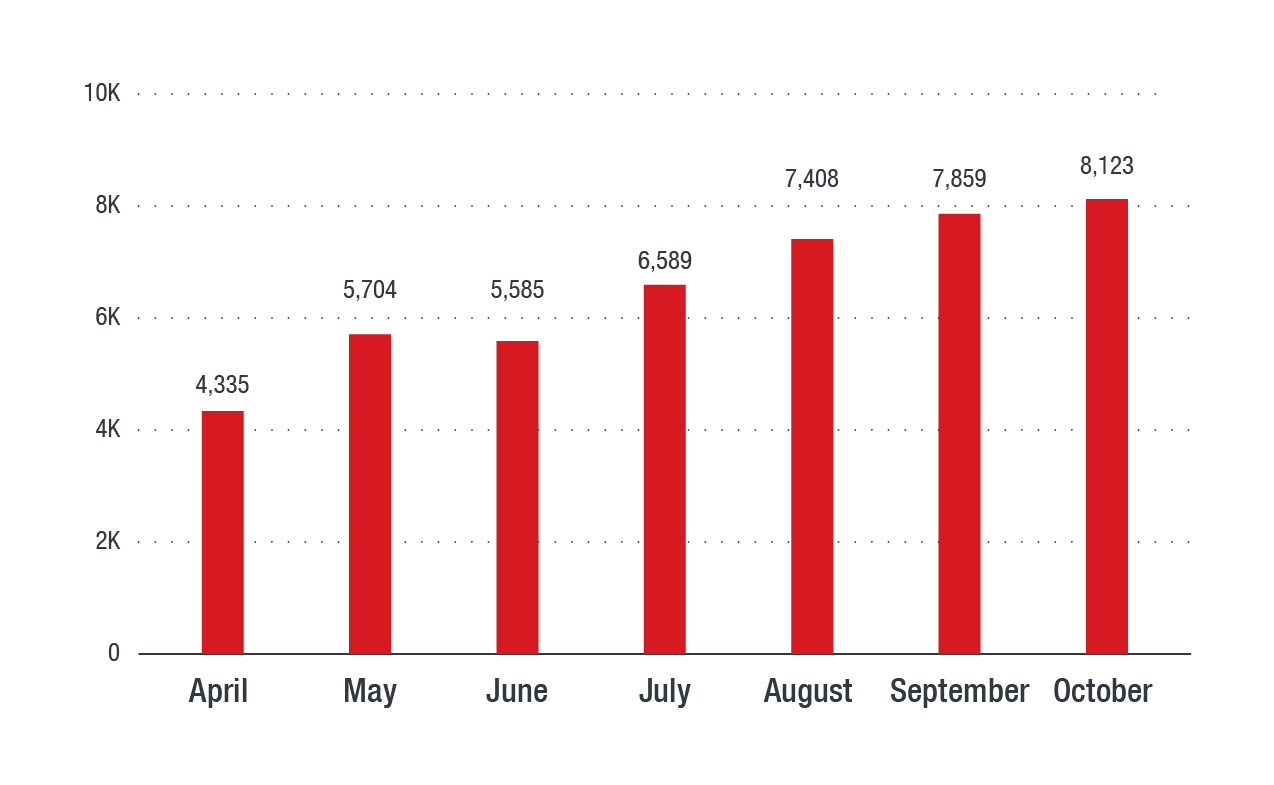
Figure 4. Comparison of trojans on a per-month basis
Lack of education on social engineering techniques and the absence of (or noncompliance with) download safety policies are seen as factors that contribute to the prevalence of trojans. By their very nature, trojans are typically among the top malware around the world. Trojans are distributed through a number of arrival vectors, most popularly through direct web downloads, contributing to their ubiquity. They can also spread through other means such as via embedded scripts and macros. Cybercriminals often use social engineering, disguising their attacks by presenting them as legitimate documents in PDF and Microsoft Word document formats, to spread trojans. For Southeast Asia, the most prevalent malware families in this segment are binaries.
Note that in this scenario, trojans are defined as lacking self-propagation abilities. This means that the presence of trojans in the wild is heavily dependent on whether they are in distribution. Whether a malware family is in distribution or not is based on threat actor activity. This might explain the sudden absence of specific malware families, such as the absence of the trojan Agents in May and June. While other regions had seen an upsurge in detections of Emotet and Powload, Southeast Asia was still dominated by Starter and Equated. These two Trojans are subsets of large families that have been active for more than a decade and feature a large array of capabilities, from information theft to denial of service (DoS). Their high detection rates mean that they are still very effective despite their age.
Unless threat actors switch to distributing other malware families, we can expect to see both Equated and Starter again next quarter.
Recommendations
An organization’s security does not stop with the security team — it extends to regular employees who often end up being unwitting gateways for threats. Companies should ensure that their end users implement best security practices, including having awareness of the various social engineering techniques used by threat actors, avoiding shady websites, and refraining from clicking on suspicious links and downloading files of dubious legitimacy.
Known vulnerabilities and users targeted to deliver cryptocurrency-mining malware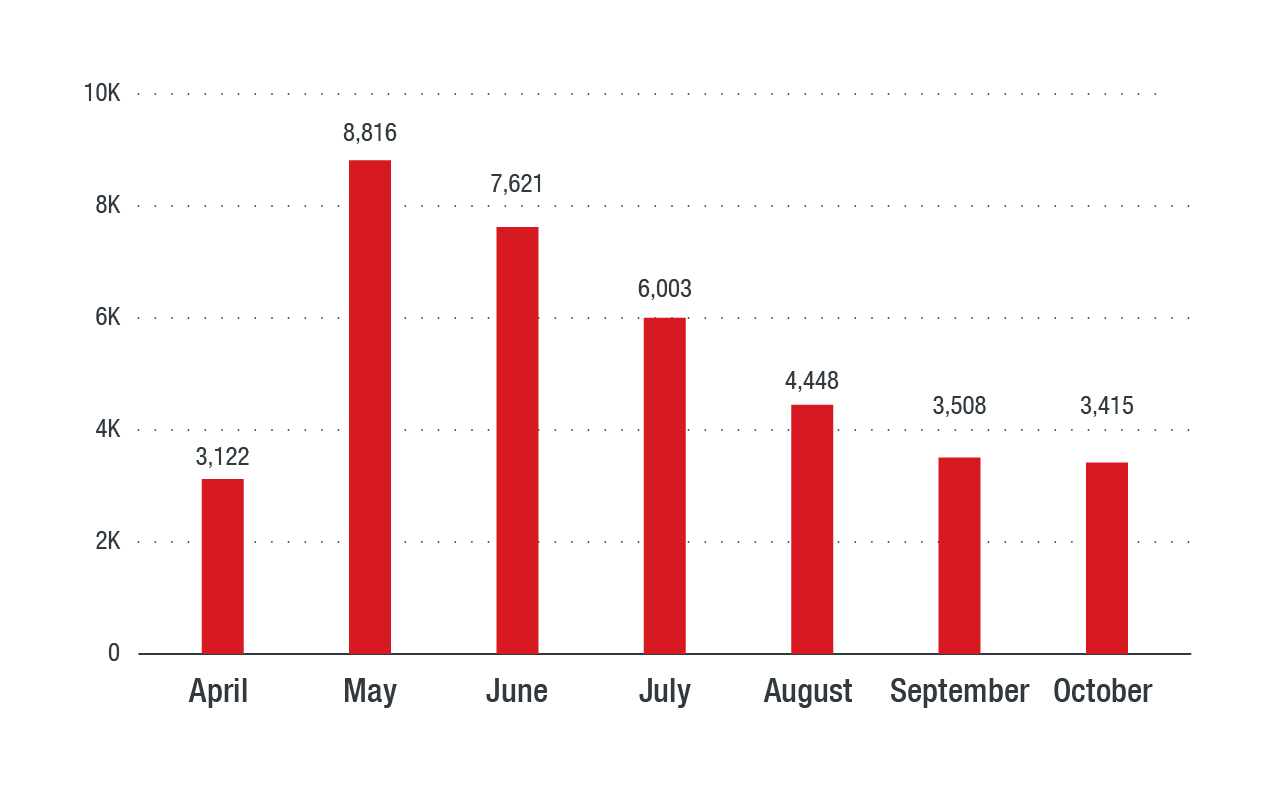
Figure 5. Cryptocurrency-mining malware detections on a per-month basis
Web-based coin-miners or cryptojackers, which were first seen in the latter half of 2017, are capable of using a computer’s resources for the unauthorized mining of cyrptocurrency through a script running on an open web browser. Perhaps the most notable example of this type of threat is Coinhive, which is usually embedded in a website, allowing it to mine the resources of user devices without their awareness. COINHIVE has been found embedded in over 300 websites as of May 2018.
In Southeast Asia, cryptocurrency-mining malware is surprisingly on the decline. The downward detection counts could mean a number of things:
- The cryptocurrency hype is starting to slow down. Compared to the record-high price of bitcoin nearing US$20,000 in the last quarter of 2017, prices have gone significantly down.
- Threat actors are possibly shifting to other ways of making profit. Cryptocurrency-mining malware in Southeast Asia might not be as lucrative as in other regions.
- People are now consciously avoiding cryptocurrency-mining malware, due to increased awareness of how the malware operates.
- Threat actors have possibly shifted to other variants of cryptocurrency-mining malware that have yet to make the list.
Cryptocurrency miners per se are not considered malware. They become malware when they mine cryptocurrency using the resources of a device without the owner’s authorization or knowledge. As malware, they make infected computers do all the heavy lifting for cryptocurrency generation without the users themselves seeing any sort of profit.
While the numbers are declining, take note that cryptocurrency-mining malware is still among the top threats in the region, and should still be taken seriously.
Recommendations
Cryptocurrency-mining malware is delivered via a wide variety of infection vectors, including social engineering and vulnerability exploits. As with the other threats, both organizations and individual users can help prevent cryptocurrency-mining malware from affecting their devices via the following practices:
- Regularly updating the firmware of devices to avoid attacks that exploit known vulnerabilities.
- Changing devices’ default credentials and using strong passwords to deter unauthorized access.
- Being wary of known attack vectors, such as socially engineered links, attachments, and files from different websites, third-party applications, and emails. Even some legitimate websites might have embedded cryptocurrency miners working in the background, so it would be a good idea to do research on whether a specific website carries a miner.
Considering managed detection and response (MDR)
The threats highlighted here show that organizations need to understand what makes them vulnerable and to adjust their policies accordingly. Managed security services such as managed detection and response (MDR) can help provide data and insights to make sure that resulting policies truly address the cybersecurity needs of an organization.
While larger organizations possess the bandwidth to establish their own teams for this purpose, smaller companies might easily be overwhelmed by the sheer effort required. In addition, many organizations face alert fatigue — having to sift through a large volume of alerts just to determine which ones are actually malicious. This makes digging for more insights into threats more challenging. At worst, some alerts can be ignored, leading to bigger problems later.
MDR offers organizations access to skilled security professionals who can provide faster alert prioritization, root cause analysis, detailed research, and a remediation plan that gives organizations the ability to quickly respond to attacks. One of the important features of MDR is its ability to correlate threats so as to paint a larger picture of their impact and origin beyond what can easily be observed. This is especially important when it comes to targeted attacks, or any concerted cybercrime effort that shows consistent patterns.
Backed by 30 years of experience in threat research, Trend Micro’s managed detection and response service provides access to experts who are proficient with live response and are familiar with products that can provide meaning to security incidents that happen to organizations and their industries. Our experts have the necessary tools and technologies to analyze threats and assist organizations in maintaining a good security posture.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization
- Agentic Edge AI: Development Tools and Workflows

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One