The IIoT Attack Surface: Threats and Security Solutions
 View Infographic: The IIoT Attack Surface
View Infographic: The IIoT Attack Surface
Industrial facilities have been increasingly reliant on the industrial internet of things (IIoT), adopting devices that make for more productive and efficient systems. Today, many manufacturing factories, energy plants, and even agricultural sites have hundreds of IIoT devices that help manage and streamline their operations. But these facilities now also have to defend against new threats that take advantage of weaknesses and other attack vectors that come with the adoption of new technology.
In industrial environments, operational technology (OT) and information technology (IT) are more connected than ever. This convergence provides industries with optimized automation and better visibility, among other benefits. However, it is also the main characteristic that makes IIoT-integrated facilities more susceptible to cyberattacks. OT is concerned with the physical aspect of industrial production, including systems for checking if a certain tank is overflowing, or for ensuring that a valve opens when it should. These were normally closed systems, but now they are increasingly being brought online. Along with traditional enterprise and office functions, a key concern of IT is the flow — and sometimes collection and analysis — of data that comes from within and outside of the industrial facility. Traditional IT has many gateways — a large and vulnerable surface that is exposed to constantly evolving threats.
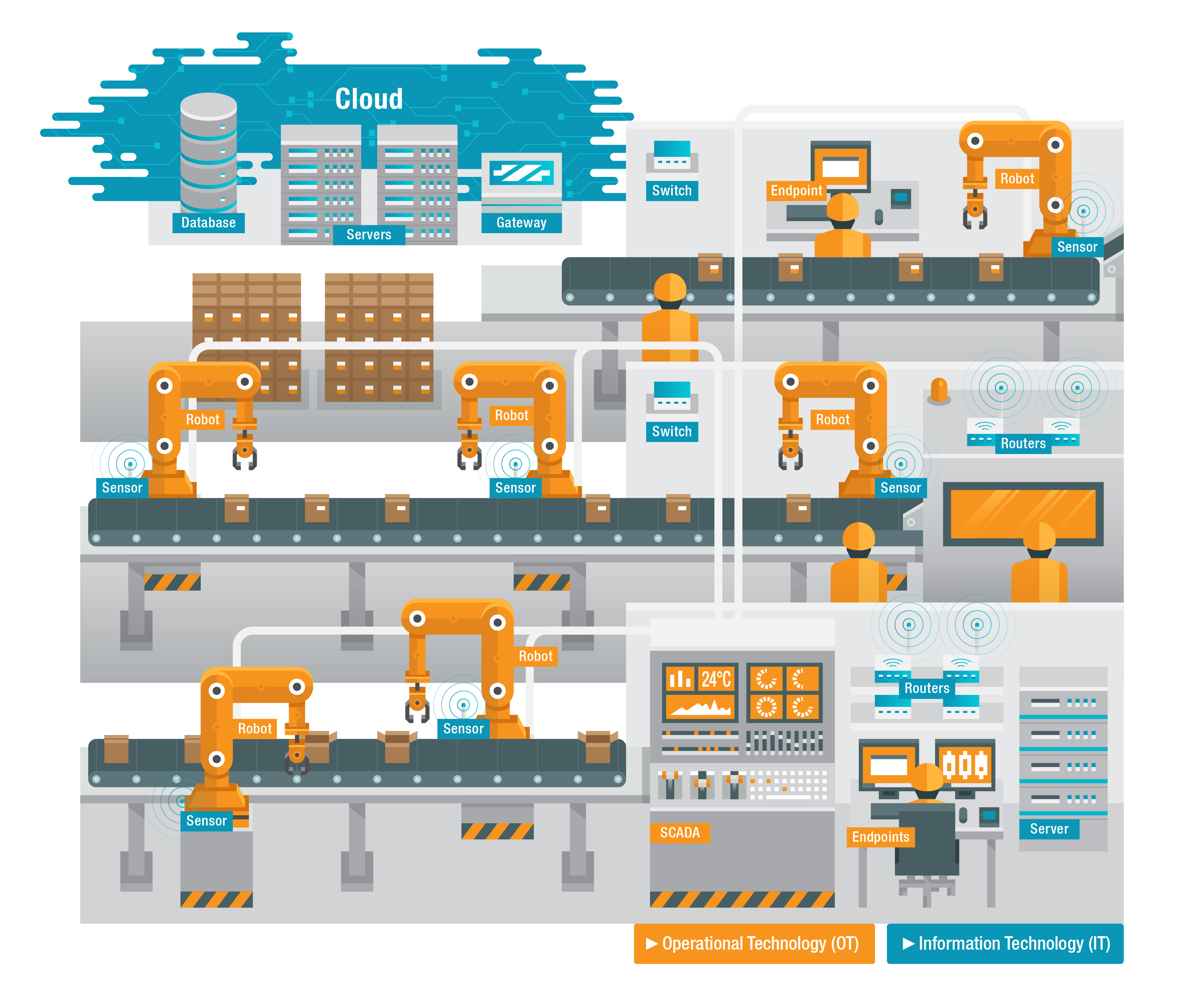
Figure 1. OT and IT in a factory setting
The convergence of IT and OT means that devices are being pushed outside what they were designed for, which can result in a weak or exposed industrial facility. Also, more connected endpoints mean more potential gateways for cybercriminals to gain access to networks and infrastructure systems. And since these networks are connected to machines and entire production lines, cyberattacks can be manifested in all-too-real, physical incidents.
What makes the IIoT difficult to secure?
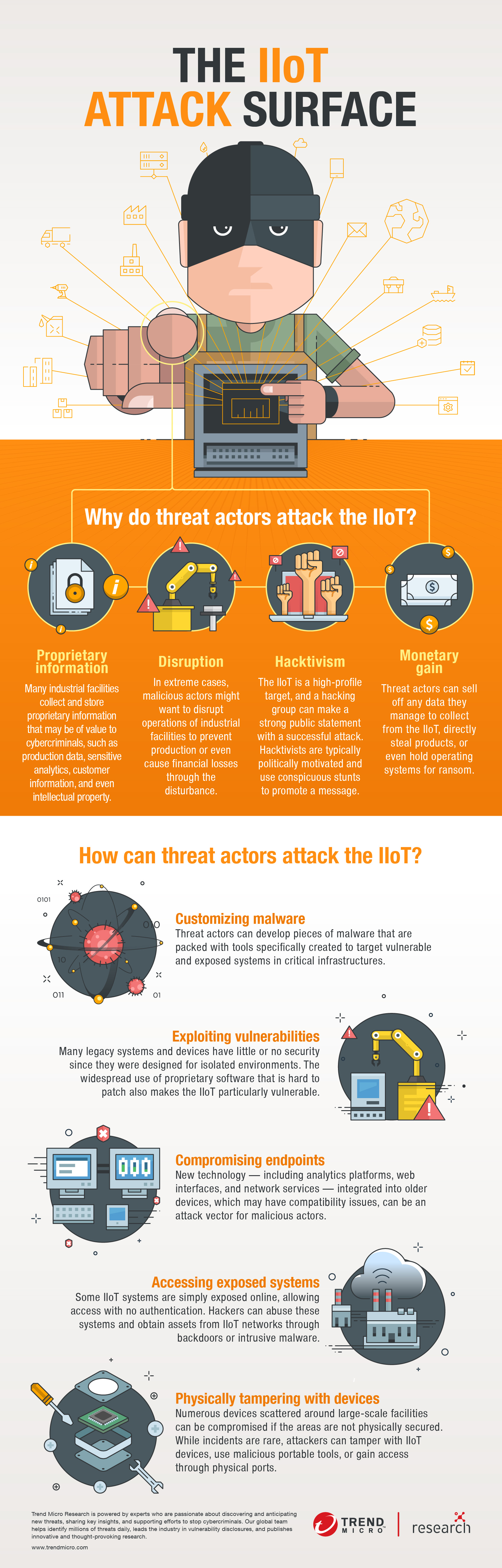
The IIoT is a viable, and increasingly popular, target for hacking groups because of several key characteristics:
- Haphazard modernization. Many machines used in industrial facilities operate with outdated hardware components and old software with known vulnerabilities. But as demand for operational analytics grows, many legacy components are being upgraded with IIoT devices and exposed to online threats without proper cybersecurity solutions. Enterprises are in a difficult position since patching is not an option for some machines, and upgrade cycles can take years and severely affect operations.
- Unique production networks. Each industrial facility has unique hardware and software configurations entirely dependent on industry requirements and specific operational demands. And often with proprietary software, maintenance and upgrading need to be overseen by the vendor.
- Vulnerable communication protocols. Controllers, actuators, sensors, and many other devices are used to manage and perform the physical processes of an industrial facility. Communication protocols such as Modbus and Profinet supervise, control, and connect these different mechanisms. But they were not designed with security in mind; they lack the ability to authenticate users, detect faults, or find abnormal behavior.
- Continued rise in deployment of devices. Facilities are increasing their adoption of IIoT devices and systems, thereby further widening the attack surface for threat actors.
What are the attack surface areas of the IIoT?
According to a March 2019 report conducted by Ponemon Institute, 90% of organizations dependent upon OT (such as those in the manufacturing, pharmaceutical, and transportation industries) experienced at least one major cyberattack in the past two years. This is certainly a problematic statistic for industrial facilities. Perhaps one cause of the problem is that, as the report states, only 20% of the surveyed professionals believed that they had sufficient visibility into their organizations’ attack surface.
The IIoT may be spread across large facilities and different locations, with numerous machines exchanging data through cloud platforms and various applications. The complexity of the system — and the fact that it is usually unique to each facility — makes it hard to map the complete attack surface of an IIoT environment. But a comprehensive view of this matter is vital to creating an effective security strategy.
Here is an overview of critical IIoT attack surface areas that organizations should properly address:
- Endpoints and legacy devices. The number of sensors, analytics platforms, and other devices and services being connected to older machines continues to grow. Each of these — be it an added piece of firmware, a physical or web interface, or a network service — is a possible entry point for attackers. Threat actors can take advantage of misconfigured settings as well as outdated components. For financially motivated actors, poorly configured OT devices are appealing entry points into IT networks — which goes against the standard expectation that attackers will hit vulnerable IT networks and pivot into OT.
- Vulnerable systems. An increasing number of industrial control systems (ICSs) are being connected to the internet as a result of the increasing interconnectivity of OT and IT networks. However, many ICSs — such as supervisory control and data acquisition (SCADA) systems, programmable logic controllers (PLCs), and the human-machine interfaces (HMIs) used with them — are simply not equipped with cybersecurity solutions that can protect them from attacks.
- Proprietary software. Industrial facilities are run with a range of proprietary software from multiple vendors. This software is often hard to update and patch since vendors maintain control over them. This leaves the IIoT particularly vulnerable since cybercriminals continue to use exploits — even those that use patched vulnerabilities — for their attacks.
- Communication protocols. Machine-to-machine (M2M) communication protocols are used in industrial facilities for the flexible exchange of data. But unsecure configurations or problematic protocols can put both data and endpoints at risk. Information can become accessible for attackers to collect, and vulnerable endpoints can become open targets for denial of service (DoS) and other types of attacks.
How can the IIoT be secured?
According to the same report from Ponemon Institute, 50% of organizations experienced an attack on critical infrastructure in the past two years that resulted in downtime to their plants or equipment. Downtime in an industrial setting can mean, say, substantial financial losses or inconveniences and even dangerous ramifications for customers. Downtime is but one consequence of attacks on IIoT environments.
It is essential, therefore, that the IIoT be secured. Knowing how to secure the internet of things (IoT) is a good place to start. Here are a few more guidelines for organizations to follow so as to secure the IIoT attack surface:
- Sustain software maintenance. One of the most significant problems with legacy software is lack of maintenance. Patching and upgrading are becoming more common in industrial control operations, but they need to be managed carefully. For one thing, stopping a device or halting systems for a patch may disrupt the whole production line. Also, patching IIoT systems often requires specialized technicians from vendors to carry out the updates properly.
- Assess risk for all devices. More IIoT devices connected to a large shared network, sometimes across multiple locations, make it harder to identify risks. All devices, down to the smallest sensor, need to be assessed and understood so that rogue assets can be quickly identified in case of a suspected breach or compromise. IT and OT communications should also be assessed and protected, with restrictions in place for devices in the IT network that connect with those in the OT network.
- Monitor access to systems and endpoints. Authentication and authorization are essential to ensuring data security. Appropriate protections should be applied to assets, from devices and other pieces of equipment to applications and systems. Biometrics, tokens, and other authentication methods need to be applied to strengthen security and prevent any unauthorized access to hardware and software.
- Secure the network and communication channels. Valuable data is exchanged over the network that connects devices and systems used in an industrial facility. Remote access controls and external communication should therefore be protected with strong firewalls, encryption, and intrusion detection. With the right cybersecurity solutions for networks, gateways, and endpoints, security threats such as data theft, vulnerability exploitation, and malware infection can be prevented.
With additional insights from Robert McArdle
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
The Road to Agentic AI: Navigating Architecture, Threats, and Solutions