Blackhole Exploit Kit Spam Run Use Bank of America, Capital One, and Linkedin
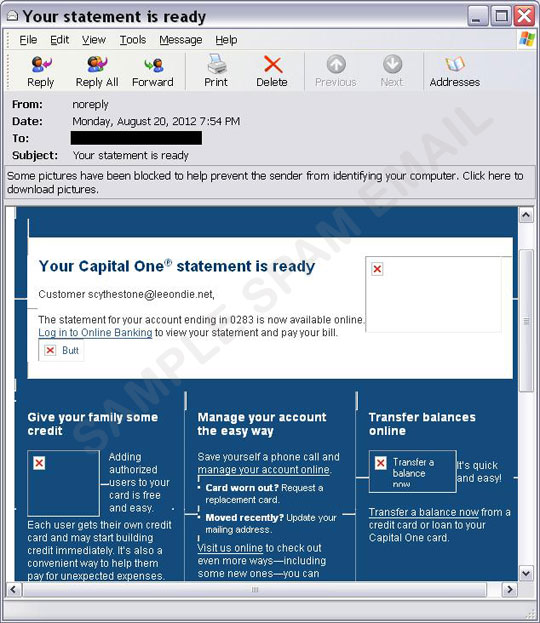
This spam run uses what looks like legitimate email notifications from Bank of America, Capital One, or LinkedIn.
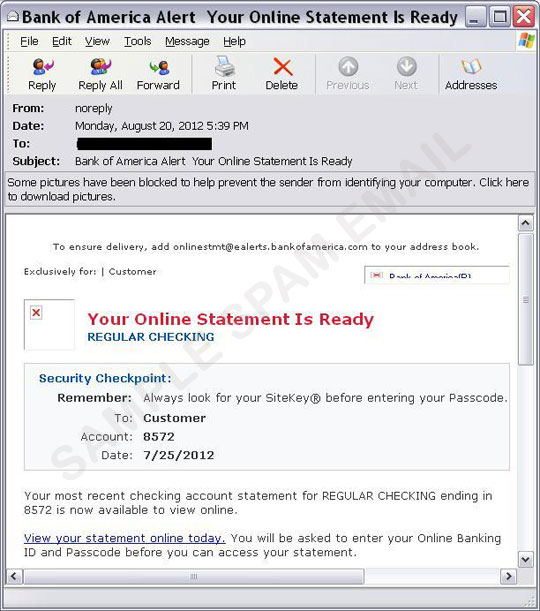
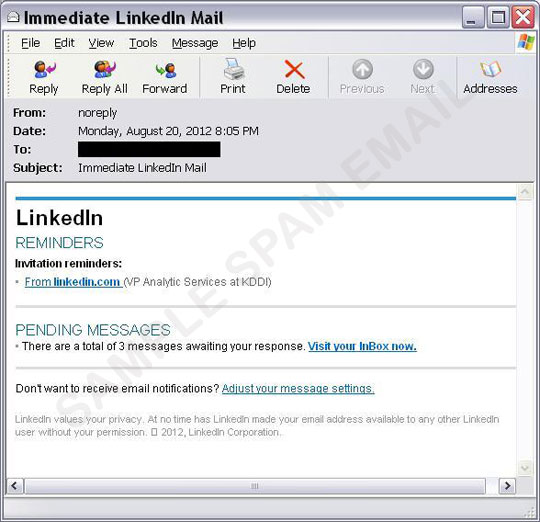
The email content aims to lure users into clicking a malicious link. Once the URL is clicked, it redirects users to a site hosting a malicious JavaScript.

While users wait for the website to load, the malicious JavaScript is already pointing them to a blackhole exploit kit server where an exploit code starts to execute. A .JAR file is executed, downloading other malicious files onto users' computers.
Users should contact their banks directly via customer hotlines provided by their banks for any account-related concerns. Users who use online banking should check their email notification settings as to when they authorize their banks to contact them via email.
Trend Micro protects users from this spam run by detecting the malicious file and spam. Smart Protection Network™ protects users from this threat by blocking the spam mail samples, as well as any related malicious URLs and malware.
- ENGINE:7.0
- PATTERN:9130