ANDROIDOS_TROJMMARKETPLAY.B
Premium Service Abuser
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
Via app stores, Downloaded from the Internet
This malware employs a new method to abuse premium service. It logs in to a third party app store and downloads paid apps and media in the background without the user's consent or knowledge. This results in unwanted charges being billed to the user's account.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
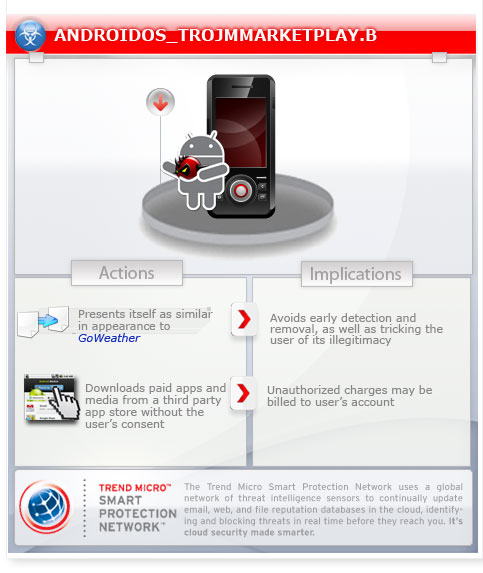
This malware may be downloaded by users from third party app stores.
It pretends to be a weather forecast tool, GoWeather. The said application is modified and repacked by the remote user to add malicious code.
This malware is a “beta build” as the test information and even the malicious user's information is seen in the code.
It does the following routines:
- Set the device APN to CMWAP
- Browse M-Market website and download paid apps and media
- Intercept the confirm verification SMS sent by M-Market which includes a verification code.
- Extract the verification code from the verification SMS and auto reply to M-Market
As such, downloaded apps and media are billed to the user’s account.
This Trojan may be manually installed by a user.
TECHNICAL DETAILS
4,600,000 bytes
APK
Yes
12 Jul 2012
Arrival Details
This Trojan may be downloaded from the following remote site(s):
- nDuoa/GFan/AppChina/LIQU/ANFONE/Soft.3g.cn/TalkPhone/{BLOCKED}9.com/AZ4SD
It may be manually installed by a user.
NOTES:
This malware may be downloaded by users from third party app stores.
It pretends to be a weather forecast tool, GoWeather. The said application is modified and repacked by the remote user to add malicious code.
This malware is a “beta build” as the test information and even the remote user's information is seen in the code.
Once installed, it changes the access point name (APN).
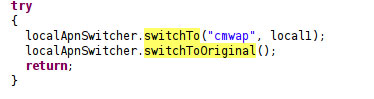
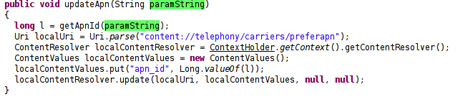
As such, the M-Market can be login automatically after setting the APN to CMWAP. Users who login for the first time to M-Market are prompted with a charge pop-out window. The malware then clicks the said window to close it.
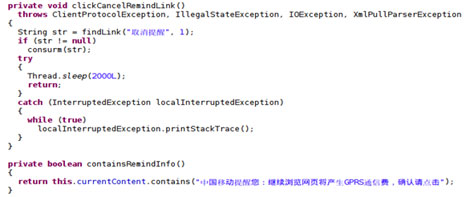
After which, it opens a page on M-Market to find and download paid applications and media.

This malware also intercepts the verification SMS and replies with the verification code.
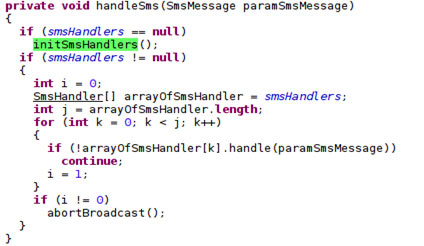
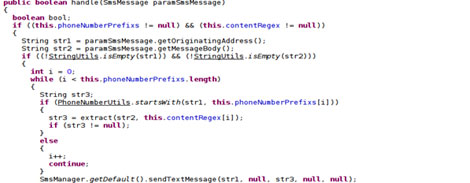
If there is a CAPTCHA image, the malware downloads the said image and sends it to a remote server to decode
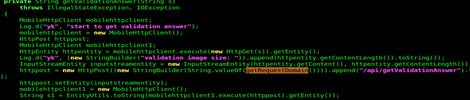
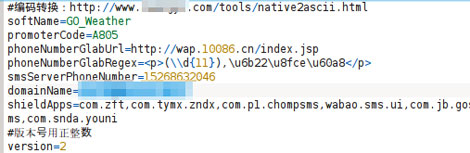
The decode server’s domain name is in a config file called yk-static.config.

There are other configurations in the file, including a phone number which is used to send to an init SMS. The domain name filed is used to store the decode server’s domain.
SOLUTION
9.200
1.275.00
13 Jul 2012
Step 1
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android smartphones and tablets from malicious and Trojanized applications. The App Scanner is free and detects malicious and Trojanized apps as they are downloaded, while SmartSurfing blocks malicious websites using your device's Android browser.
Download and install the Trend Micro Mobile Security App via Google Play.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.

