ANDROIDOS_GHOTELS.A
Information Stealer, Premium Service Abuser, Malicious Downloader
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This is the Trend Micro detection for an Android malware that disguises itself as a legitimate application. This malicious APK file is a repackaged version of a legimate program used in China to search for hotels.
Based on its code, this malware may intercept, send, and block SMS. It sends the text message "1234567" to a certain number. Since it sends messages to the said number without the users' consent, the unknowing users may be charged of an undesired service.
This Trojan may be unknowingly downloaded by a user while visiting malicious websites. It may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This Trojan may be unknowingly downloaded by a user while visiting malicious websites.
It may be manually installed by a user.
Other Details
This Trojan does the following:
- This is the Trend Micro detection for an Android malware that disguises itself as a legitimate application. This malicious APK file is a repackaged version of a legimate program used in China to search for hotels.
- The file AndroidManifest.xml contained in the APK file has also been modified to change the permission and the startup setting:
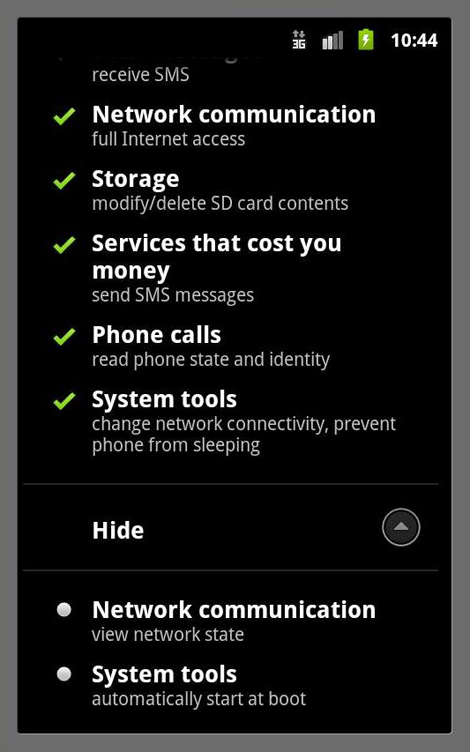
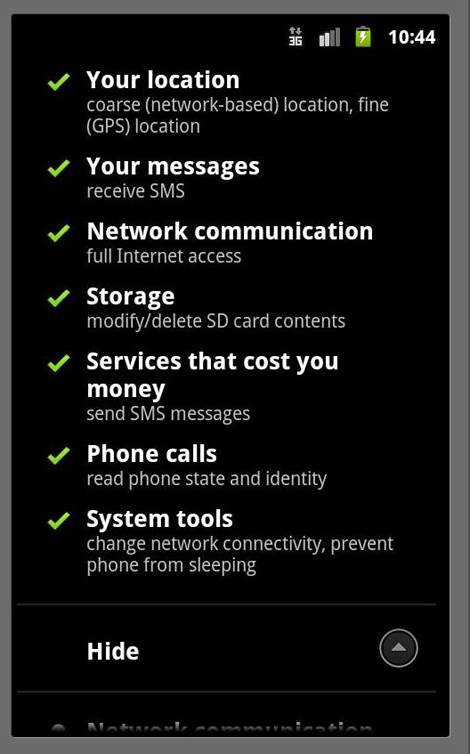
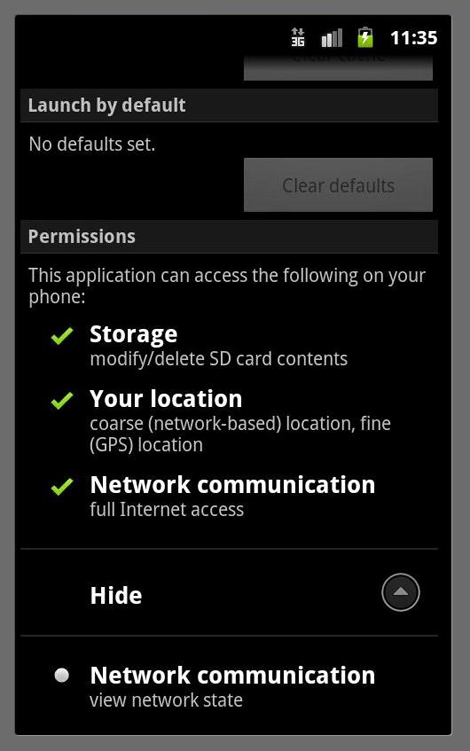
- This version contains a malicious DEX file which based on its code has the following capabilities:
- Logs its activities and saves it in the file, log.txt.
- Collects and logs the following information to the file, upload.xml:
- imei
- version
- sms center
- phone number
- malware installation details - Connects to http://www.{BLOCKED}g.com:81/Coop/request3.php to send the gathered file via HTTP POST.
- Saves the reply from the server in the file, serverInfo.xml, which may contain additional commands. However, no reply has been received as of this writing.
- Downloads a file from http://{BLOCKED}.{BLOCKED}.165.53/adapted/choose.jsp?dest=all&chooseUrl=QQQwlQQQrmw1sQQQpp66.jsp and save it to the file, vedio_file.3gp.
- All files this malware uses are saved in the directory, /data/data/com.hotel/files/.hide/
- Based on its code, this malware may intercept, send, and block SMS. It sends the text message "1234567" to the number "BLOCKED6". Since it sends messages to the said number without the users' consent, the unknowing users may be charged of an undesired service.
SOLUTION
Step 1
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android smartphones and tablets from malicious and Trojanized applications. The App Scanner is free and detects malicious and Trojanized apps as they are downloaded, while SmartSurfing blocks malicious websites using your device's Android browser.
Download and install the Trend Micro Mobile Security App via Google Play.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.


