ANDROIDOS_ADRD.B
Information Stealer
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This Android OS Trojan uses social engineering methods to lure users into performing certain actions that may, directly or indirectly, cause malicious routines to be performed. Specifically, it conceals itself as a legitimate wallpaper.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
Based on its behavior, the purpose of this Trojan is click fraud which in turn may lead to increased and expensive data charges.
This Trojan may be unknowingly downloaded by a user while visiting malicious websites. It may be manually installed by a user.
TECHNICAL DETAILS
276,333 bytes
Other
Yes
13 Jun 2011
Arrival Details
This Trojan may be unknowingly downloaded by a user while visiting malicious websites.
It may be manually installed by a user.
Other Details
This Trojan does the following:
- Conceals itself as a legitimate wallpaper application.
- Gathers the following information from affected device:
- IMEI
- IMSI
- Access Point Name (cmnet, 3gwap, 3gnet, uniwap, uninet)
- Local Date
- Sends the said information to the following website: http://adrd.{BLOCKED}an.ne/pic.aspx?im={encrypted data}
- Waits for certain reply from the servers. Based on its code, the reply may contain strings to be used to execute a search using http://wap.baidu.com.
- Downloads an updated component from the following site:
- http://adrd.{BLOCKED}n.net/index.aspx?im=
- Re-executes itself during any of the following instances:
- When the device receives a phone call
- During phone start-up
- Whenever a new network connection is started
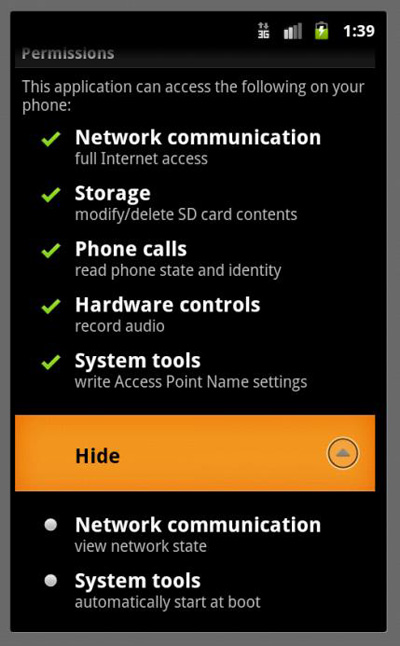
- Modifies the applications' permission to the following:
NOTES:
Based on its behavior, the purpose of this Trojan is click fraud which in turn may lead to increased and expensive data charges.
SOLUTION
8.900
1.105.00
13 Jun 2011
Step 1
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android smartphones and tablets from malicious and Trojanized applications. The App Scanner is free and detects malicious and Trojanized apps as they are downloaded, while SmartSurfing blocks malicious websites using your device's Android browser.
Download and install the Trend Micro Mobile Security App via Google Play.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.