How MITRE ATT&CK Assists in Threat Investigation
Categorizing the behavior of threats in a clear and easily understandable manner has always been a challenge for cybersecurity researchers. To understand the specifics of an attack, professionals normally need to analyze indicators, search for findings from other security researchers, and read reports, articles, and papers describing similar threats.
Analysis and investigation can be daunting and resource intensive for cybersecurity professionals, especially if a threat shows a high sophistication level and several components. This is further complicated by the fact that a threat actor can modify these components — hashes, command-and-control (C&C) servers, IP addresses — making threats not only more efficient but also more difficult to detect and analyze. However, attacks and campaigns typically display certain patterns depending on the attacker’s motivations and targets — patterns that have allowed the attribution of attacks to specific threat actor groups. The challenge is how to cross-check findings against data from various sources.
In 2013, The MITRE Corporation, a federally funded not-for-profit company that counts cybersecurity among its key focus areas, came up with MITRE ATT&CK™ (short for adversarial tactics, techniques, and common knowledge), a curated knowledge base that tracks adversary behavior and tactics. ATT&CK has seen widespread adoption over the past year as organizations try to keep up with the volume of cyberthreats and collate and make sense of threat data.
Seeing the bigger picture with ATT&CK
Akin to the parlance of TTPs (tactics, techniques, procedures), the main elements of ATT&CK are tactics and techniques. Within the ATT&CK framework, they are defined as follows:
- Tactics refer to the objective behind an attack, which in turn dictates what technique the attacker will use. For example, a threat actor may identify persistence as one of its tactics for a specific campaign.
- Techniques represent the “how” of an attack. It defines how a threat actor achieves their tactic. In the example above, abusing Windows Task Scheduler is one of the techniques that can achieve persistence.
The relationship between tactics and techniques are visualized in the ATT&CK Matrix, a set of matrices composed of Pre-ATT&CK, enterprise, and mobile. As its name implies the Pre-ATT&CK matrix shows the behavior of a threat actor before an attack actually occurs. Conversely, the enterprise and mobile matrices provide information on threats that affect each platform.
An advantage of using the ATT&CK Matrix is that it allows for the swift identification of the TTPs used in an attack via a standardized format. It’s essentially a common language and resource for security researchers and IT personnel not just for specific threat details — it also enables correlation to see the bigger picture of an attack. It draws from real-world examples, with references to actual attacks per technique, making it easier for researchers to find analysis on similar threats.
Viewing a MyKings botnet infection through the ATT&CK Matrix
An actual incident involving the MyKings botnet illustrates how ATT&CK can be used in threat investigation.
Last August, Trend Micro researchers detailed the case of a company that was infected with the MyKings botnet. What made this incident particularly interesting was that the botnet had been in the company’s system for approximately two years. This particular MyKings variant contained plenty of moving parts and components, including the following:
- A bootloader rootkit used to implement bootkit persistence, disable antivirus scanners, perform Asynchronous Procedure Call (APC) injection, and download the configurations and payload from the C&C server.
- Fileless persistence mechanisms that include the use of the registry, Windows Management Instrumentation (WMI), as well the scheduled task function of Microsoft Windows.
- A cryptocurrency miner, one of many possible payloads depending on the configuration.
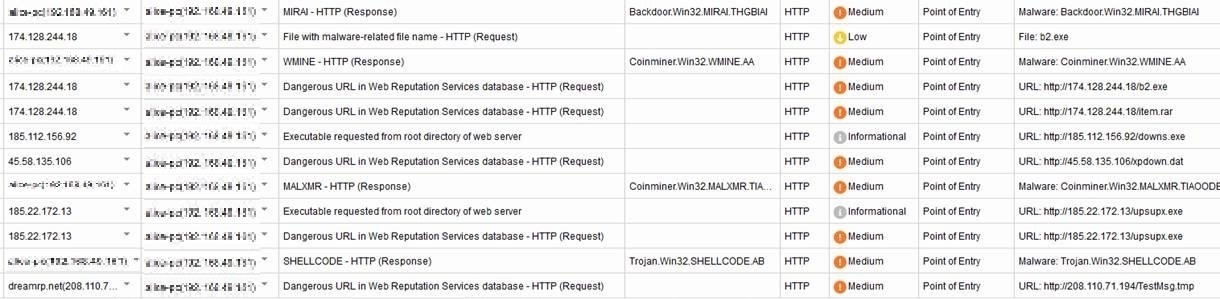
The figure below shows the Trend Micro™ Deep Discovery™ Inspector detections for a backdoor, a trojan, and a cryptocurrency miner. A person without intimate knowledge of the threat might have concluded that these detections were unrelated since they are different kinds of malware. Further complicating matters is the fact that this MyKings variant had constantly changing components and multiple payloads that depended on what the C&C server sent. When these factors were combined with the length of time the threat had stayed in the system, it became fairly difficult to provide an accurate infection chain for the attack.
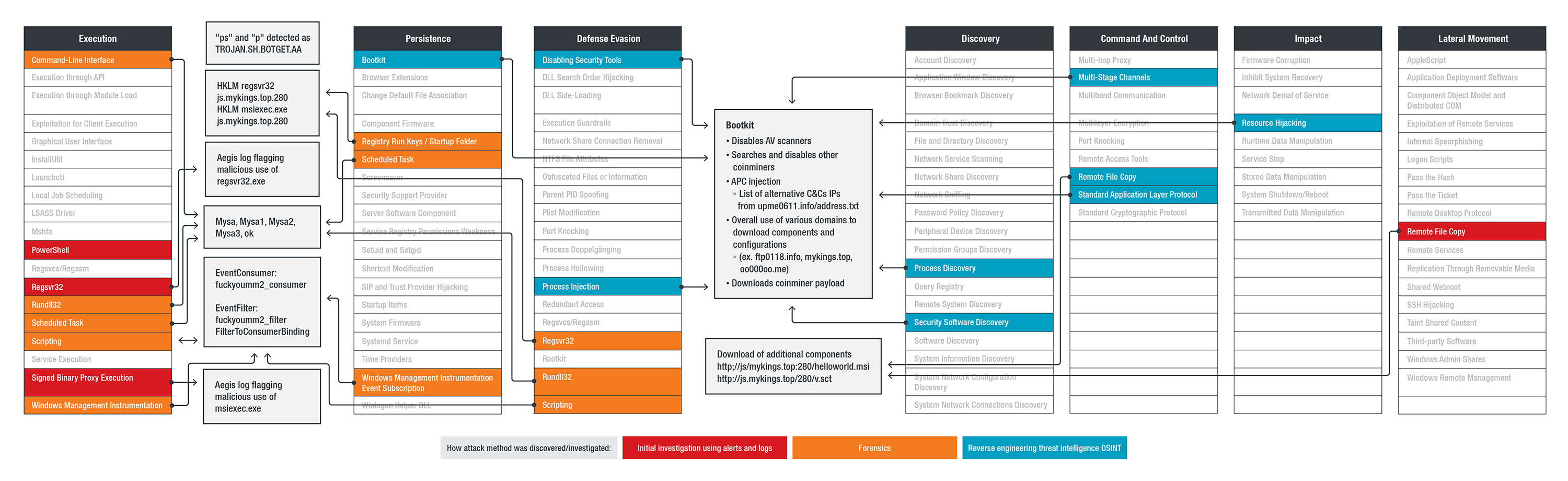
In the case of the MyKings incident, the components can be plotted on the enterprise ATT&CK matrix as follows:
The chart shown above is a modified version of the standard ATT&CK matrix, adding a color-coded scheme indicating which MyKings components were flagged by the behavior monitoring feature (Aegis) of the Trend Micro product and the Trend Micro MDR team and at what stages they were discovered and analyzed. It also shows which components have multiple functions for the malware. Knowing these enabled defenders to zoom in on points of compromise and stop further risks.
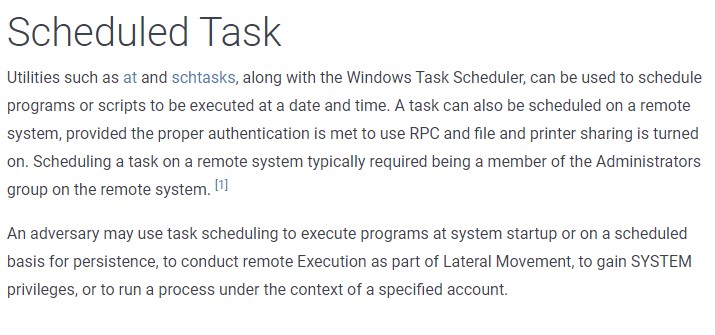
Looking at the diagram, one can see that the different functions of MyKings neatly correspond to a technique — even several ones, such as in the case of the bootkit. Knowing the malware was able to stay undetected for two years, the techniques under Persistence are worth looking into. The MyKings variant has a set of fileless persistence mechanisms. In the matrix, each persistence mechanism points directly to its counterpart. Even without labels, understanding what each component does becomes intuitive. For example, the component “Mysa” (in gray box) analyzed during Forensics was used for the “Scheduled Task” technique (T1053). The dedicated page for the technique in the ATT&CK knowledge base gives the following description:
© 2019 The MITRE Corporation. This work is reproduced and distributed with the permission of The MITRE Corporation.
From the description (and procedure examples), analysts and defenders looking at the matrix will already have an idea of how this technique is used — a mechanism for persistence, defense evasion, and execution. In this particular case of MyKings, the attack used the technique for persistence as well as execution.
Piecing the puzzle together
One of the challenges when it comes to traditional threat intelligence is that it is often a time-consuming endeavor that requires sifting through reports, articles, news stories, and even social media posts to find and analyze indicators as well as determine which information is useful for a current investigation or worth adding to an internal knowledge base. Given enough time, a dedicated security researcher would probably be able to piece together the details of the story. But in cybersecurity, time is always of the essence. Threat investigation needs to be as quick as possible to properly categorize a threat and identify where the security gaps are and how they can be addressed.
This is where ATT&CK can help threat investigation: It allows security researchers to narrow down their search to specific tactics and techniques, cutting down on the time needed to map out the details of an attack. For example, a security researcher analyzing an incident can start by looking into the technique used by a malware variant to gain initial access into the system (found under the tactic “Initial Access”). From there, security researchers can go down the line, comparing the malware variant’s tactics and techniques with the ones listed in the ATT&CK framework to see where they match up. The eventual goal, with the help of ATT&CK, is not only to tell the story of the why, how, and what of an attack but also to help pinpoint security weaknesses within the system that a security team can work on strengthening.
One of the key takeaways from the MyKings incident is that digital forensics and incident response aren’t always clear-cut and the pieces don’t always fit cleanly into the puzzle — at first. A tool like ATT&CK can help shed light on the missing parts to create a more complete picture of an attack. However, this does not mean that ATT&CK by itself is enough — it’s just another tool in a good security researcher’s toolbox.
The best security teams will know how to make use of all of these tools to make threat investigation and analysis more effective. The Trend Micro™ Managed XDR service allows organizations to benefit from a combination of expert knowledge of frameworks like ATT&CK with security analytics that integrate detection and response features across networks, endpoints, emails, servers, and cloud workloads to gain an understanding of how attacks are initiated, how far they spread in the network, and what remediation steps need to be taken.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
The Road to Agentic AI: Navigating Architecture, Threats, and Solutions