Vulnerability scanning is the practice of detecting, identifying, and assessing cybersecurity vulnerabilities within an organisation’s IT infrastructure.
Vulnerability scanning is an essential component of threat detection and response that involves continuously scanning IT infrastructure for vulnerabilities that can be exploited. The entire IT environment is included in these scans, from computer networks and applications to endpoint devices like laptops, desktops, servers, and even smartphones.
Vulnerability scanning allows organisations to find and address any flaws, risks, or weaknesses in their cybersecurity that could allow bad actors to gain access to their systems, disrupt their operations, or steal their sensitive information. Vulnerabilities can include:
- Unprotected ports in servers, workstations, laptops, and other devices
- Coding errors that could permit unauthorised access
- Missing software patches and updates
- Weak passwords or misconfigured access permissions that could expose sensitive data to theft or ransom
Common misconceptions about vulnerability scanning
Vulnerability scanning is key to any successful threat management strategy. But in spite of its effectiveness, several common misconceptions have prevented vulnerability scanning from being adopted more widely.
One is that vulnerability scans need to be performed only once in a while. With thousands of new cyber threats being introduced every day, vulnerability scanning is much more effective if it’s carried out on a continuous basis.
Another misconception is that only large organisations need to scan for vulnerabilities. In fact, small- and medium-sized businesses are just as vulnerable to attack, and many of them don’t have the resources in place to recover or deal with the consequences. Vulnerability scanning can help organisations of any size defend against cyber threats and protect themselves, their clients, and their business.
Vulnerability scanning vs. penetration testing
While vulnerability scanning and penetration testing are both essential parts of an organisation’s cybersecurity strategy, there are several key differences between them.
Vulnerability scanning is an automated process that proactively identifies existing security flaws before they can be exploited. Penetration testing, on the other hand, is a manual exercise that simulates a real-world cyberattack to test an organisation’s security controls.
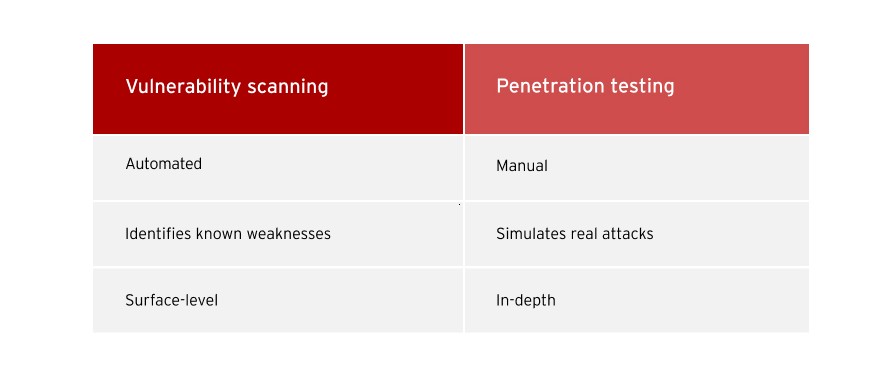
While vulnerability scanning and penetration testing are both essential parts of an organisation’s cybersecurity strategy, there are several key differences between them.
Vulnerability scanning is an automated process that proactively identifies existing security flaws before they can be exploited. Penetration testing, on the other hand, is a manual exercise that simulates a real-world cyberattack to test an organisation’s security controls.
Why is vulnerability scanning important?
As cyber threats become more sophisticated, businesses need to be able to make sure their cybersecurity defences are as robust, comprehensive, and up-to-date as possible. Vulnerability scanning can identify and inform security teams of any vulnerabilities that exist in an organisation’s IT infrastructure or cybersecurity measures, and offer recommendations for how best to mitigate them.
Vulnerability scanning can also help organisations reduce the substantial financial and reputational costs associated with security breaches and maintain their cybersecurity compliance with regulatory bodies including Payment Card Industry Data Security Standard (PCI DSS), National Institute of Standards and Technology (NIST), and Health Insurance Portability and Accountability Act (HIPAA). Plus, vulnerability scanning tools allow organisations to continually monitor the effectiveness of their cybersecurity to keep pace with any new or emerging threats, risks, or flaws.
How does vulnerability scanning work?
Vulnerability scans draw on threat intelligence databases that contain detailed information about every known threat that could compromise an organisation’s network, systems, or data. Then they employ a variety of software tools and technologies to scan for any signs of vulnerabilities to those threats using the following five-step process:
Step One: Configuration
The scanner gathers all available information about an organisation’s IT network, from IP addresses and operating systems to inventories of every device that’s connected to the network. This makes sure the scanner is configured properly to scan the system.
Step Two: Scanning
The scanner analyses the network or system to find and identify every potential flaw, weakness, or vulnerability.
Step Three: Analysis
The results of the scan are analysed to assess the risks and severity of each vulnerability.
Step Four: Reporting
The scanner sends a report to the security team detailing what it found and suggesting ways to deal with each vulnerability.
Step Five: Mitigation
The security team then uses that information to remediate any flaws in the network. This can include updating software, installing patches, or reconfiguring entire systems.
By interpreting the results of the scan, organisations can prioritise the order they address the flaws to deal with the most urgent vulnerabilities first. Once the process is complete, the scanner goes back to the first step and starts the scanning process all over again.
Types of vulnerability scans
While all vulnerability scans work in much the same way, there are three main types of scans that organisations can use to assess their cybersecurity: network scans, web application scans, and host-based vulnerability scans.
- Network vulnerability scans. These scan for flaws in an organisation’s IT network, including servers, firewalls, routers, computers, and other network-connected devices.
- Web application vulnerability scans. These detect weaknesses in web applications, including vulnerabilities to SQL code injection or cross-site scripting (XSS) attacks.
- Host-based vulnerability scans. These identify vulnerabilities in an organisation’s on-site workstations, laptops, and servers.
How do I create a vulnerability scanning policy?
A vulnerability scanning policy provides a clear set of guidelines, instructions, and standards that spell out exactly when, how, and how frequently a network should be scanned for vulnerabilities.
An effective policy should define the scope and objectives for the scan, set out a precise schedule for how frequently the scans will be performed, and outline the role of each member of the cybersecurity team in conducting the scan and responding to the results.
To provide maximum protection, vulnerability scanning should also be integrated seamlessly into any existing cybersecurity policies, tools, and strategies. This enables an organisation to maximise both the speed and accuracy of its threat detection and response (TDR) solution.
Where can I get help with vulnerability scanning?
Trend Vision One™ Cyber Risk Exposure Management (CREM) empowers organisations to shift from reactive to proactive cybersecurity by continuously scanning their networks to uncover, assess ,and mitigate vulnerabilities in real time. By discovering potential flaws before the bad actors do, CREM lets you find, prioritise, and fix weaknesses in your environment so you can build true cyber risk resilience into your entire network.