Operation Secure: Trend Micro's Threat Intelligence Fuels INTERPOL's Infostealer Infrastructure Takedown
In this blog, we discuss how Trend Micro played a pivotal role in Operation Secure, a multi-national law enforcement effort that dismantled the infrastructure behind widespread infostealer malware campaigns across Asia and the Pacific.
Key takeaways:
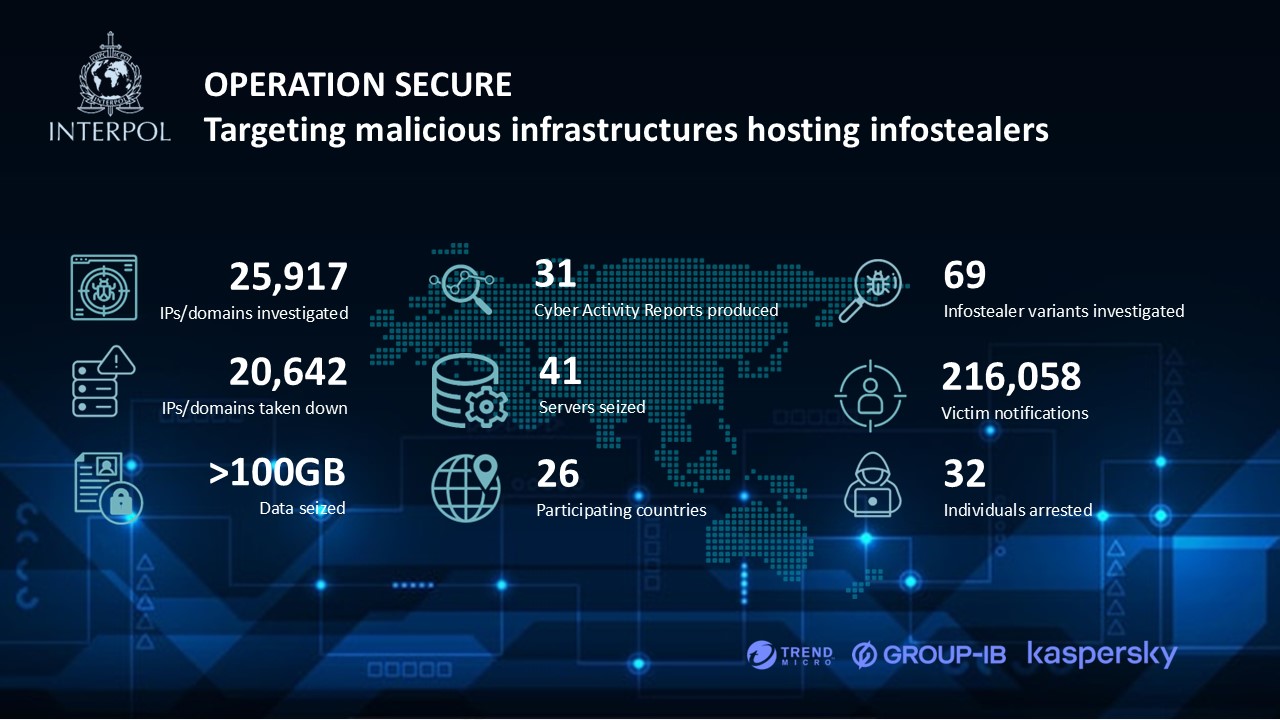
- Trend Micro was a key private sector partner in Operation Secure, a multi-country initiative that disrupted infostealer malware campaigns and enabled law enforcement agencies to take down over 20,000 malicious IPs and domains and arrest of involved cybercriminals.
- The collaborative effort saw the seizure of 41 criminal servers and more than 100 GB of critical cybercrime data and proactively notified over 216,000 victims to facilitate swift protective actions.
- Trend Micro leveraged its advanced global threat telemetry and provided actionable intelligence and malware analysis, contributing to a 79% removal rate of suspicious IP addresses and strengthening cyber defense efforts in the Asia-Pacific region.
- Our investigations also revealed Vidar, Lumma Stealer, and Rhadamanthys as some of the most prominent infostealer families detected in this operation. We provide an overview and related reading to these infostealers in the blog.
Trend Micro was part of the recently concluded Operation Secure that successfully disrupted the infrastructure behind widespread infostealer malware campaigns throughout Asia and the Pacific.
The multi-country initiative brought together law enforcement agencies and experts from 26 countries and took down over 20,000 malicious IP addresses and domains, seized 41 criminal servers and more than 100 GB of data, and arrested 32 individuals linked to cybercrime. Operation Secure was conducted from January to April 2025 and together with law enforcement, where over 216,000 victims were notified to enable rapid protective countermeasures.
We provided crucial intelligence and malware analysis as one of the operation’s three private sector partners, leveraging our extensive global threat telemetry to produce detailed and actionable data that enabled law enforcement to identify malicious servers and pinpoint criminal infrastructure. The successful operation recorded a remarkable 79% removal rate of identified suspicious IP addresses.
Hong Kong law enforcement analyzed over 1,700 intelligence leads and identified 117 command-and-control (C&C) servers across 89 hosting providers identified as being used for phishing and fraud activities.
Meanwhile, Vietnamese authorities arrested 18 suspects and seized devices and SIM cards linked to account fraud schemes. Police force in Sri Lanka and Nauru also conducted house raids, arresting 14 individuals and identifying 40 victims.
These actions illustrate how server identification drives both tactical disruption and strategic arrests in multinational cybercrime operations.
Targeting rising infostealer activities
With INTERPOL at the helm, our experts specifically identified malicious servers utilized for deployment and C&C communications by infostealers and other malware campaigns. These servers are core infrastructures that serve as the backbone of cybercriminal operations and identifying them is critical for law enforcement takedowns. These servers control infected devices, exfiltrate and store stolen data, and deliver additional malware payloads. By mapping and seizing these servers, law enforcement agencies were able to disrupt operations at scale, gather forensic evidence, and trace threat actors.
The identification of these servers also facilitated real-time victim alerts, and the operation improved threat intelligence for long-term cybercriminal activity disruption and strengthened global coordination.
Our investigations into these malicious servers also uncovered which infostealer families were most active as either deployed from or communicating with the compromised servers. The next sections give an overview of the infostealer families found to be prominent in this operation. We also provide links for more information and further reading.
Vidar
Vidar is a prevalent Malware-as-a-Service (MaaS) that has been active since 2018. Vidar is capable of exfiltrating sensitive data like browser credentials, cookies, and cryptocurrency wallets. It commonly spreads through malvertising, phishing, and cracked software, and can also act as a loader for other malware, including ransomware. Trend™ Research,h in an investigation, revealed its distribution via social media. We have also previously observed samples that suggest that the cybercriminals behind this infostealer have tried to shift and use their tactics and techniques to deliver ransomware.
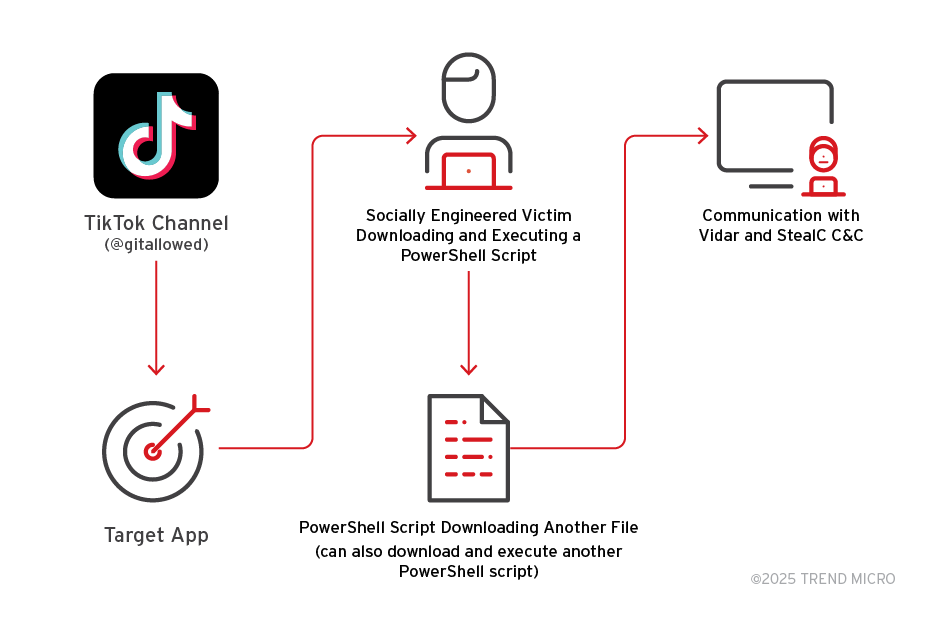
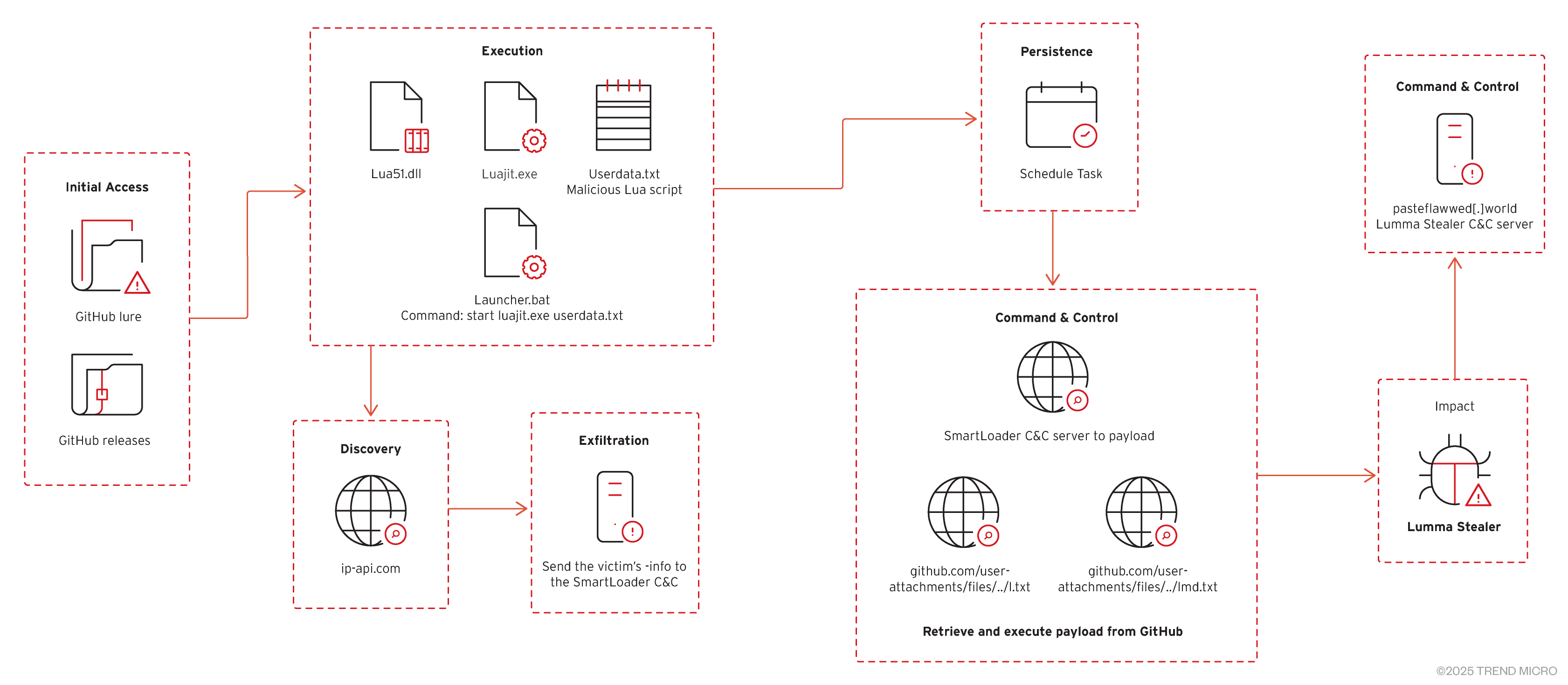
Lumma Stealer (LummaC2)
This rapidly growing infostealer-as-a-service gained notoriety in late 2022 and became one of the most active families in 2025. Lumma Stealer specializes in stealing browser credentials, crypto wallets, and autofill data. This infostealer often leverages public platforms like GitHub and content delivery networks for stealthy payload delivery, but has also been observed to abuse Discord’s content delivery network (CDN) for hosting and delivery. It was the target of a major takedown operation by Europol in May 2025, which was conducted in partnership with other industry experts.
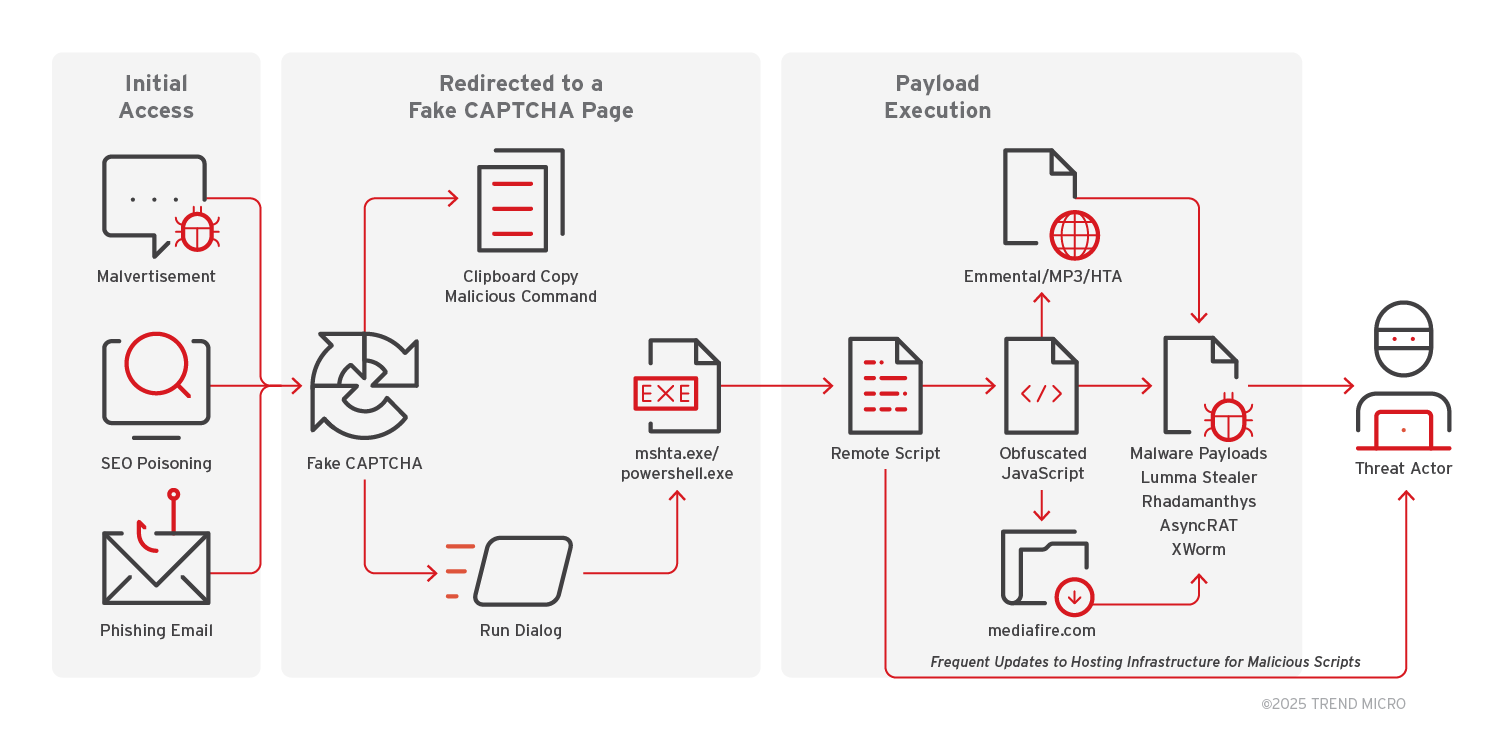
Rhadamanthys
First observed in late 2022, Rhadamanthys is a sophisticated infostealer distributed through phishing, fake installers, and pirated software. It collects credentials, cookies, and detailed system information, communicating over encrypted channels to exfiltrate stolen data. Its reliability and customization options make it a favorite among threat actors.
Continuing the Global Fight Against Cybercrime
Trend’s participation in Operation Secure underscores our steadfast commitment to public-private collaboration in the fight against global cybercrime.
We have previously partnered with INTERPOL in its Operation Synergia that took down over 1,300 C&C servers which led to 30 house searches and the identification of 70 suspects facilitating phishing, banking malware, and ransomware activity.
Trend also contributed to INTERPOL’s operation to help Brazilian and Spanish law enforcement agencies analyze Grandoreiro malware samples as part of their national cybercrime investigations that resulted in the arrest of five administrators behind a Grandoreiro operation.
Trend also partnered with INTERPOL in Operation Red Card by providing intelligence that helped lead to the arrest of 306 suspects and the seizure of 1,842 devices involved in banking, investment, and messaging app scams.
As cybercriminals continuously evolve their tactics, proactive intelligence sharing and cross-border coordination remain essential for effective defence. Our partnership with INTERPOL endures as Trend persists in its commitment to securing our increasingly connected world.

