12 Types of Social Engineering Attacks
12 Types of social engineering attacks
Social engineering attacks exploit human psychology rather than technical vulnerabilities. These manipulative tactics are designed to trick individuals into revealing confidential information or performing actions that compromise security—often without realizing it. As cybercriminals continue refining their techniques, it’s critical for individuals and organizations to understand the various forms these attacks can take.
Below are twelve of the most common types of social engineering attacks, explained with fresh perspective and practical context.
Phishing
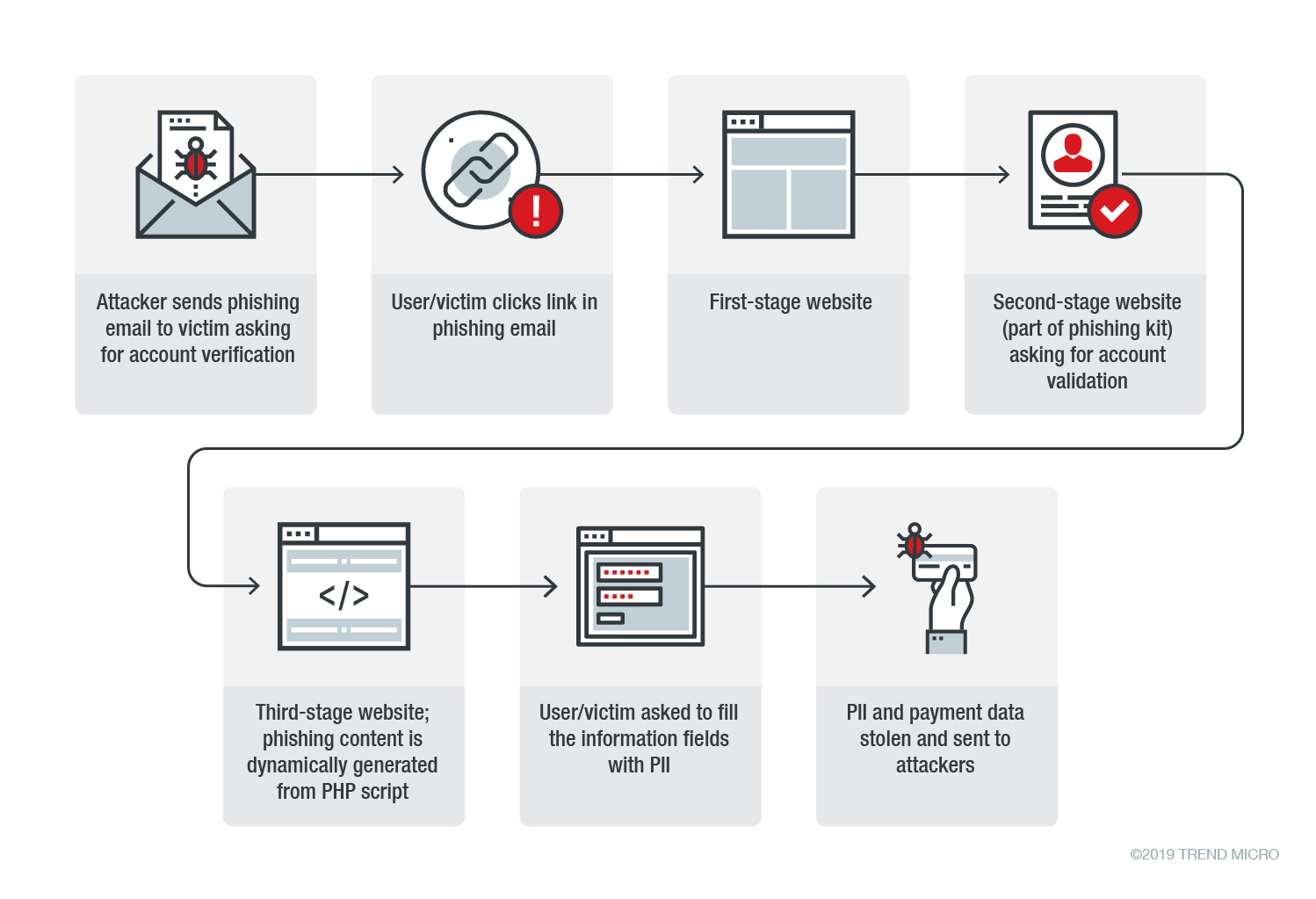
Phishing is a type of cyber-attack in which attackers impersonate trusted entities, such as banks or service providers, to send fraudulent messages, usually via email. The goal is to lure victims into clicking on harmful links or downloading malicious attachments, resulting in data theft or malware infection.
Attackers design these messages to manipulate emotions like fear or curiosity to pressure their victims to click a link or provide sensitive information. For instance, a message might warn you that your account will be suspended unless you verify personal details right away.
Spear Phishing
Spear Phishing takes the phishing concept further by tailoring messages to a specific individual or organization. Attackers conduct in-depth research to personalize the content—such as referencing colleagues’ names or current projects—making the email appear credible and relevant.
Unlike generic phishing, spear phishing is harder to detect because it mimics internal communication or trusted business correspondence. It’s often the gateway to deeper network intrusions.
Baiting
Baiting relies on enticing a target with something appealing, such as a free download or a lost USB drive labeled “Confidential.” Once interacted with, the bait delivers malware or grants the attacker access to the system.
What makes baiting particularly dangerous is that it weaponizes curiosity or greed—traits that can override security awareness in the moment.
Whaling
Whaling targets high-ranking executives or decision-makers within an organization. These attacks often disguise themselves as legitimate business communications, such as urgent legal notices or supplier invoices.
Because C-level executives often have access to sensitive financial data and systems, compromising their accounts can lead to large-scale fraud or data breaches.

Tailgating
Tailgating, also known as “piggybacking,” is a physical social engineering tactic. It occurs when an unauthorized individual gains access to a secure building by closely following someone with valid credentials.
This technique exploits social norms like politeness, such as holding the door open, making it a significant risk in organizations without strong physical security protocols.
Smishing
Smishing, or SMS phishing, involves text messages that appear to come from reputable sources, like your bank or delivery services. These messages include links or prompts that lead victims to malicious websites or prompt the download of malware.
Smishing exploits the immediacy and perceived trustworthiness of text messages, making users more likely to click without verifying.
AI-Based Scams
With the rise of generative AI, attackers are now using artificial intelligence to automate and personalize their social engineering campaigns. These scams include:
- AI-generated texts that mimic human writing to craft convincing phishing messages.
- Deepfake audio and video impersonations that replicate the voice or appearance of real people.
- Fake imagery is used to manipulate or fabricate proof for fraudulent claims.
AI allows attacks to grow in scale while still providing a personal touch, which enhances their effectiveness.
Vishing
Vishing, which is short for voice phishing, is a tactic that uses phone calls to manipulate victims into disclosing sensitive information. Scammers will often impersonate bank representatives, IT support, or even law enforcement to establish credibility and create a sense of urgency.
Unlike email phishing, vishing creates direct pressure via conversation, often catching victims off guard with persuasive dialogue or threatening language.

Scareware
Scareware bombards users with alarming messages—typically pop-up ads—that claim the system is infected. Victims are urged to install a “security fix,” which is often malware.
By creating panic, scareware overrides rational decision-making. These tactics are commonly used in fake antivirus campaigns or tech support scams.
Pretexting
Pretexting involves fabricating a scenario to gain trust and extract information. An attacker may impersonate a colleague, vendor, or authority figure, crafting a believable story to persuade the target to reveal credentials or transfer funds.
Unlike phishing, which often uses fear, pretexting relies on rapport and trust—making it especially dangerous in corporate environments.
Quishing
Quishing is a QR code-based phishing method. It replaces legitimate QR codes with malicious ones—on posters, emails, or physical locations. When scanned, the code redirects to fake websites or triggers malware downloads.
Since QR codes obscure their destination URLs, users often scan without suspicion, making this attack subtle yet potent.
Business Email Compromise (BEC)
BEC is a sophisticated scam targeting companies with international suppliers or frequent wire transfers. Attackers either spoof or hack executive email accounts to issue fake invoice or fund transfer requests.
BEC attacks are financially devastating and often bypass technical defenses by exploiting human trust and poor verification processes.
How to prevent Social Engineering Attacks?
Preventing social engineering attacks starts with awareness. These threats don’t exploit software—they exploit people. The more familiar you are with manipulation tactics, the better equipped you are to spot them.
Whether the threat comes through email, SMS, a phone call, or even a QR code, social engineers count on distraction, urgency, or misplaced trust to succeed. Organizations and individuals alike must take proactive steps to strengthen their human layer of defense.
Best Practices to Reduce Risk:
- Keep systems up to date: Regularly update your operating system, applications, and cybersecurity tools to protect against known vulnerabilities.
- Enable multifactor authentication (MFA): MFA adds an extra layer of verification, making it harder for attackers to misuse stolen credentials.
- Use a password manager: Strong, unique passwords for every account reduce the damage a compromised credential can cause.
- Be cautious with unknown emails or attachments: Don’t click on links or download files unless you can verify the source.
- Configure email filters: Set up spam filters to detect and block suspicious content before it reaches your inbox.
- Stay calm and vigilant: If you receive a message or call that creates a sense of pressure or urgency, take a moment to pause and verify the information before responding.
- Research suspicious contacts: Verify websites, emails, or phone numbers independently before taking action.
- Limit social media exposure: Avoid oversharing personal information and review your privacy settings regularly.
- Know your organization’s policies: Employees should be familiar with internal protocols for data handling, authentication, and incident response.
Trend Vision One Platform
Trend Vision One™ is a cybersecurity platform that simplifies security and helps enterprises detect and stop threats faster by consolidating multiple security capabilities, enabling greater command of the enterprise’s attack surface, and providing complete visibility into its cyber risk posture.
The cloud-based platform leverages AI and threat intelligence from 250 million sensors and 16 threat research centers around the globe to provide comprehensive risk insights, earlier threat detection, and automated risk and threat response options in a single solution.
