Introduction
Containers have transformed the way we develop, deploy, and manage software. By packaging applications along with their dependencies, containers make it easy to run apps consistently anywhere—from your laptop all the way up to massive cloud deployments. They offer unmatched speed, flexibility, and portability, enabling rapid scaling and updates.
Organizations running hundreds of self-hosted Kubernetes clusters and thousands of nodes rely on a complex ecosystem—including CI/CD pipelines, container registries, and deployment tools—that expands the attack surface. Each stage in the container lifecycle, from source code to deployment, presents opportunities for attackers to inject malicious payloads or compromise images.
Exploits like those involving exposed Docker APIs can lead to lateral movement within clusters and unauthorized deployment of cryptojacking workloads. Without strict controls and continuous monitoring, even indirect access points like Helm charts or internal registries can be used to compromise production environments.
While containers offer significant operational efficiency and are widely adopted—often supported by trusted open-source communities and industry-leading technology companies—even reputable sources can unintentionally distribute container images containing vulnerabilities, exposed secrets, or malicious code. Techniques such as Image Signature Verification allow you to verify the authenticity and integrity of container images, ensuring only secure, reliable containers are deployed. This practice effectively reduces risks and the surface of attack and enhances confidence in both your applications and infrastructure.
Understanding Image Signature Verification
Image signature verification is a critical process that ensures the integrity and authenticity of container images across the software supply chain. By validating image signatures, organizations can verify that images originate from trusted sources and have not been altered.
Implementing image signing at build time and verification at runtime establishes a strong chain of trust—ensuring only authorized, unmodified images are deployed. Each image is signed with a private key and later verified using a corresponding public key, preventing attackers from injecting malicious or unauthorized content into production environments.
Unsigned or tampered images would be flagged and blocked before deployment, significantly reducing the risk of compromise and reinforcing security from development to runtime.
When to Verify?
Within the Kubernetes control plane via admission webhooks:
- Purpose: Blocks deployment of unverified images at cluster entry
- Outcome: Enforces policy before workloads are created
Leveraging our Trend Vision One™ Container Security solution
Our container image signature verification capability within Container Security is designed to enhance software supply chain security. This is achieved by ensuring only trusted images are deployed into your container environments. It offers a flexible and robust, policy-based approach that integrates seamlessly into existing container security workflows.
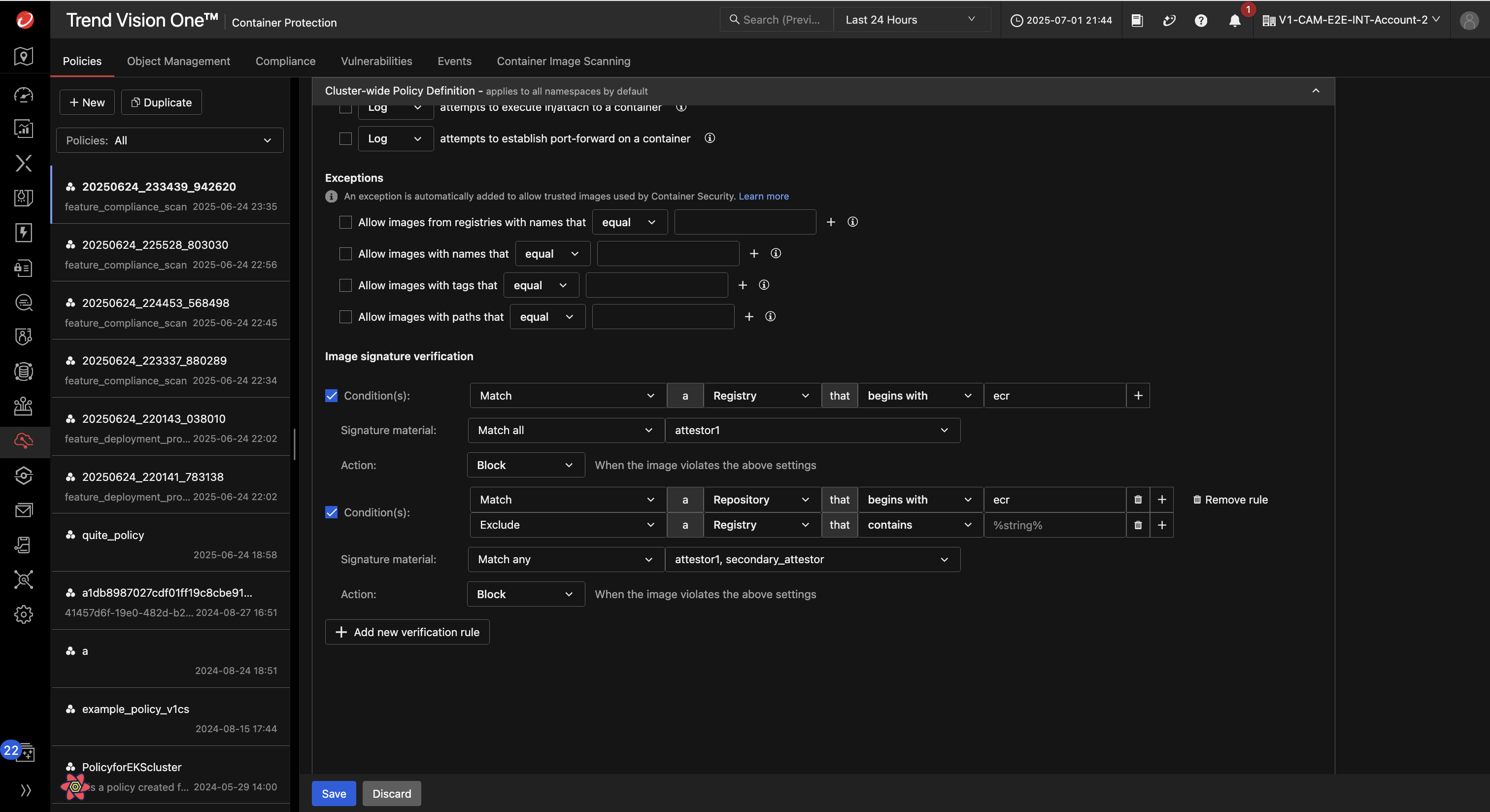
Ensure policy-driven verification at deployment
Integrated into the admission control phase, container image signature verification allows you to enforce signature verification as part of your container security policies. You can configure image validation rules during deployment to ensure compliance before workloads are admitted into the cluster.
Gain granular control and flexibility
Define verification methods, manage signature attestors such as key pairs, and set match and/or exclusion rules based on image sources, names, or labels. This flexibility allows tailored policies for different environments, use cases, or risk profiles.
Enable support for multi-key verification
Enable multiple signature validations per image to satisfy the needs of development, security, and operations (DevSecOps) teams. Each team can independently sign off on an image, ensuring accountability and reducing deployment risk.
Implement an enforcement-first approach
Enforce policy rules to block unauthorized or unsigned images from being deployed, preventing supply chain threats and reducing the attack surface of your production environment. Non-compliant images are rejected before reaching runtime.
Harness flexible policy management
Configuration is available through a web console UI for ease of use or policy-as-code (YAML/JSON) for DevSecOps pipelines. This enables both interactive management and CI/CD integration.
Visibility & Auditability
Gain full visibility into verification events with logs, metrics, and alerts to support compliance audits and incident investigation.
Container image signature verification brings together security, usability, and operational efficiency, helping organizations adopt a zero-trust approach to container deployments and build trust in their software supply chain.
Customer Benefits
Strengthen supply chain security
Prevent the deployment of tampered or untrusted container images, reducing the risk of software supply chain attacks and ensuring that only verified code runs in production
Improve policy flexibility across teams
With support for multiple signatures per image and customizable rules, organizations can tailor policies to meet the unique needs of DevSecOps teams—enhancing collaboration without sacrificing security.
Accelerate incident response and compliance readiness
Built-in logging and audit trails improve visibility and accountability, helping customers quickly trace security incidents and simplify compliance with standards like NIST, ISO 27001, PCI DSS, and HIPAA.
Integrate seamlessly into CI/CD pipelines
Whether managed via web UI or policy-as-code, the solution supports automated enforcement in DevOps workflows, enabling secure deployments without slowing down innovation.
Reduce risk to production environments
Enforced blocking of unauthorized images ensures that misconfigurations or attacks—such as cryptojacking and lateral movement via unverified images—are stopped before they impact critical systems
Conclusion
Image signing and runtime verification are essential safeguards in securing the software supply chain and reducing the risk of container compromise. At Trend Micro, we developed a custom image verification solution that verifies signatures at the container lifecycle—an approach we detail here, including how we sign and encode image payloads for deployment integrity.
Implementing image signature verification strengthens container security by ensuring only trusted, untampered images are deployed. By adopting tools and building a robust end-to-end verification process, organizations can significantly improve their security posture and maintain trust across containerized environments.

