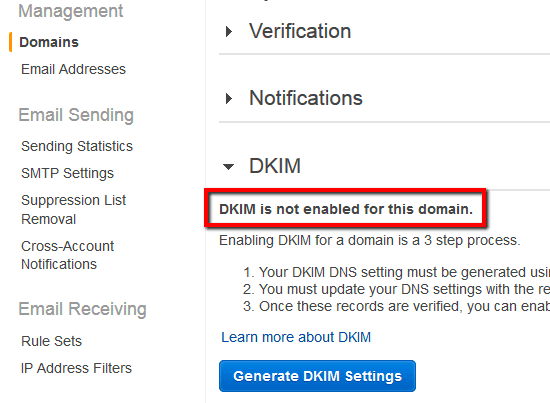
Ensure DomainKeys Identified Mail (DKIM) feature is enabled within your AWS SES settings to protect both email senders and receivers against phishing attacks by using DKIM-signature headers to make sure that each message sent is authentic.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
By enabling DKIM signing for your AWS SES outgoing email messages you will demonstrate that these messages are legitimate and have not been modified in transit by spammers.
Audit
To determine if your AWS Simple Email Service (SES) identities (domains and email addresses) are configured to use DKIM signatures, perform the following:
Remediation / Resolution
To enable DKIM signing for your existing AWS Simple Email Service (SES) registered identities (domains and email addresses), perform the following:
References
- AWS Documentation
- Amazon SES FAQs
- Authenticating Email with DKIM in Amazon SES
- Easy DKIM in Amazon SES
- AWS Command Line Interface (CLI) Documentation
- ses
- list-identities
- get-identity-dkim-attributes
- set-identity-dkim-enabled
- get-identity-dkim-attributes