Security 101: Business Email Compromise (BEC) Schemes
![]() Over the past two years, fraudsters stole millions of dollars from businesses by compromising their official email accounts and using those accounts to initiate fraudulent wire transfers. In January 2015, the Internet Crime Complaint Center (IC3) and the FBI released a public service announcement that warns of a “sophisticated scam” targeting businesses that work with foreign suppliers. Evidently, there has been an increase of computer intrusions linked to BEC scams, involving fraudsters impersonating high level executives, sending phishing emails from seemingly legitimate sources, and requesting wire transfers to alternate, fraudulent accounts. These methods ultimately lead to successful intrusion and unfettered access to their victims’ credentials.
Over the past two years, fraudsters stole millions of dollars from businesses by compromising their official email accounts and using those accounts to initiate fraudulent wire transfers. In January 2015, the Internet Crime Complaint Center (IC3) and the FBI released a public service announcement that warns of a “sophisticated scam” targeting businesses that work with foreign suppliers. Evidently, there has been an increase of computer intrusions linked to BEC scams, involving fraudsters impersonating high level executives, sending phishing emails from seemingly legitimate sources, and requesting wire transfers to alternate, fraudulent accounts. These methods ultimately lead to successful intrusion and unfettered access to their victims’ credentials.
What is Business Email Compromise?
The FBI defines Business Email Compromise (BEC) as a sophisticated scam targeting businesses working with foreign suppliers and businesses that regularly perform wire transfer payments. Formerly known as Man-in-the-Email scams, these schemes compromise official business email accounts to conduct unauthorized fund transfers. According to the FBI, victims lost nearly $750 million dollars and affected more than 7,000 people between October 2013 and August 2015. Globally, cybercriminals scammed more than $50 million dollars from victims in non-US countries.
[Read: Billion-Dollar Scams: The Numbers Behind Business Email Compromise]
How does it work?
BEC scams often begin with an attacker compromising a business executive’s email account or any publicly listed email. This is usually done using keylogger malware or phishing methods, where attackers create a domain that’s similar to the company they’re targeting, or a spoofed email that tricks the target into providing account details. Upon monitoring the compromised email account, the fraudster will try to determine who initiates wires and who requests them. The perpetrators often perform a fair amount of research, looking for a company that has had a change in leadership in the C-suite of the finance function, companies where executives are traveling, or by leading an investor conference call. They use these as opportunities to execute the scheme.
BEC scams have three versions:
Version 1: The Bogus Invoice Scheme
This version, which has also been referred to as “The Bogus Invoice Scheme”, “The Supplier Swindle”, and “Invoice Modification Scheme”, usually involves a business that has an established relationship with a supplier. The fraudster asks to wire funds for invoice payment to an alternate, fraudulent account via spoofed email, telephone, or facsimile.
Version 2: CEO Fraud
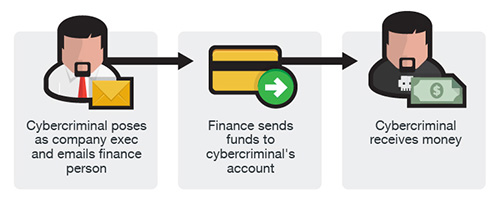
In this version, the fraudsters identify themselves as high-level executives (CFO, CEO, CTO, etc.), lawyers, or other types of legal representatives and purport to be handling confidential or time-sensitive matters and initiate a wire transfer to an account they control. In some cases, the fraudulent request for wire transfer is sent directly to the financial institution with instructions to urgently send funds to a bank. This scam is also known as “CEO Fraud”, “Business Executive Scam”, “Masquerading”, and “Financial Industry Wire Frauds”.
Version 3: Account Compromise
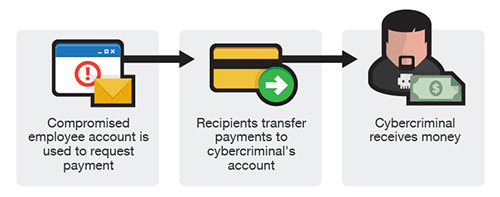
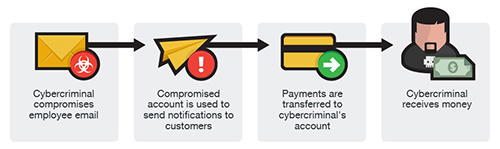
Similar to the two other versions, an email account of an employee is hacked and then used to make requests for invoice payments to fraudster-controlled bank accounts. Messages are sent to multiple vendors identified from the employee’s contact list. The business may not become aware of the scheme until their vendors follow up to check for the status of the invoice payment.
Version 4: Attorney Impersonation
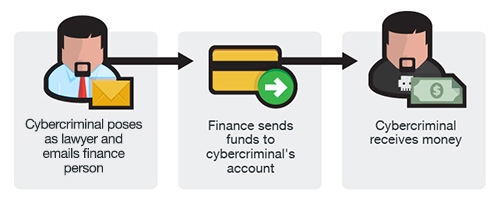
In this version, the cybercriminal contacts either the employees and/or the CEO of the company and identify themselves as lawyers or representative of law firms, claiming to be handling confidential and time-sensitive matters. This contact, typically made via phone or e-mail, pressures the contacted party into acting quickly or secretly in handling the transfer of funds. This type of BEC scheme may be timed to occur at the end of the business day or work week, when employees are getting ready to rest and thus vulnerable to panic.
Version 5: Data Theft
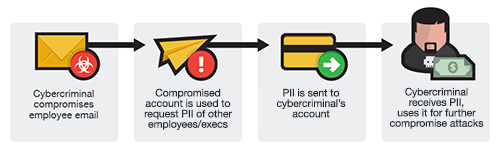
This scheme involves the email of role-specific employees (usually human resources) in the company being compromised and then used to send requests – not for fund transfers but for personally-identifiable information of other employees and executives. This can therefore serve as a jump-off point for more damaging BEC attacks against the company itself.
The scam mostly banks on social engineering, and typically doesn’t need sophisticated system penetration. Unlike phishing scams, the emails used in BEC scams are not mass-emailed to avoid being flagged as spam. In addition, in BEC scams, the victims are tricked into doing the transfers for them, usually instructing the victims to act quickly or in confidence when transferring funds.
Case Study: Predator Pain and Limitless, Hawkeye
In 2014, findings revealed that cybercriminals go beyond common attack methods to steal information. According to Trend Micro researchers, cybercriminals behind the Predator Pain and Limitless keyloggers utilized toolkits sent through emails. The emails contain a keylogger that sends back information back to the cybercriminal. Similarly, in June 2015, two Nigerian cybercriminals dubbed as “Uche” and “Okiki” used a simple keylogger called Hawkeye. The tool compromised business emails, allowing them to hijack transactions by sending alternative payment details, routing the payment straight to the cybercriminals’ pockets.
The cybercriminals behind these operations had indiscriminate targets, but they did go after specific industries where they think they will be most successful.
[Related: Olympic Vision campaign found targeting companies in the US, Middle East, and Asia]
Other targets: PII and W-2 information
As early as March 2016, a growing line of corporations and businesses have been found to have fallen for similar schemes. Companies like Seagate, Snapchat, and Sprouts Farmer’s Market were among the businesses that were victimized by email scams that use the same modus. By the end of the same month, Pivotal Software, a San Francisco-based software and services company, was breached via a phishing scheme that leaked an undisclosed number of employee tax information.
The breach was initiated by an email that appeared to be from the company’s CEO Rob Mee, requesting information on the company's staff. This resulted in the delivery of employee W-2 information that included names, addresses, 2015 income details, Social Security numbers, and Individual Taxpayer Identification numbers to an unauthorized recipient.
Not long after this incident, similar schemes were used to aim for personal information from the education sector. Following the exposure of W-2 information of 3,000 employees of Virginia-based Tidewater Community College, a similar email that posed as a request from Kentucky State University President Raymond Burse was sent to one of the school’s staff members, prompting the staff to forward a list of employees and students along with the 2015 W-2 information.
Scams that involve the theft of personal information via phishing emails have proven to be a valuable underground commodity as the stolen data could be sold in underground markets and also be used to stage future attacks. As seen in recent and previous tax fraud scams, email scams have become one of the quickest methods to trick unknowing users.
Defending against the scam
Businesses are advised to stay vigilant and educate employees on how to prevent being victimized by BEC scams and other similar attacks. It’s important to know that cybercriminals do not care about your company's size—the more victims, the better. Additionally, cybercriminals need not to be highly technical as they can find tools and services that cater to all levels of technical expertise in the cybercriminal underground. As the world relies more and more on Web services such as webmail, a single compromised account is all it could take to steal from a business. As such, here are some tips on how to stay protected and secure:
- Carefully scrutinize all emails. Be wary of irregular emails that are sent from C-suite executives, as they are used to trick employees into acting with urgency. Review emails that request transfer of funds to determine if the requests are irregular.
- Educate and train employees. While employees are a company’s biggest asset, they're also usually its weakest link when it comes to security. Commit to training employees according to the company’s best practices. Remind them that adhering to company policies is one thing, but developing good security habits is another.
- Verify any changes in vendor payment location by using a secondary sign-off by company personnel.
- Stay updated on your customers’ habits including the details, and reasons behind payments.
- Confirm requests for transfer of funds when using phone verification as part of two-factor authentication, use known familiar numbers, not the details provided in the email requests.
- If you suspect that you have been targeted by a BEC email, report the incident immediately to law enforcement or file a complaint with the IC3.
For more on protecting your organization from BEC schemes, read Battling Business Email Compromise Fraud: How Do You Start?
Trend Micro products protect medium and large enterprises from this threat. Malware in BEC-related emails are blocked by the endpoint and email security capabilities of the Trend Micro Smart Protection Suites and Network Defense solutions.
The InterScan Messaging Security Virtual Appliance with enhanced social engineering attack protection provides protection against socially-engineered emails used in BEC attacks. The Deep Discovery Analyzer found in the Trend Micro Network Defense family of solutions help detect advanced malware and other threats that come in using email.
Update: Versions 4 and 5 were added based on the FBI's updated public service announcement.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 MQTT and M2M: Do You Know Who Owns Your Machine’s Data?
MQTT and M2M: Do You Know Who Owns Your Machine’s Data? Building Resilience: 2024 Security Predictions for the Cloud
Building Resilience: 2024 Security Predictions for the Cloud Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023
Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023 Mitigating the Threat of Sidecar Container Injection
Mitigating the Threat of Sidecar Container Injection