With contributions from Shingo Matsugaya
We take an in-depth look at ransomware activity for the fourth quarter of 2022 and highlight the three ransomware families that registered the highest numbers of attacks: LockBit, BlackCat, and Royal, the splinter group from the Conti Team One ransomware group.
Fourth-quarter data reaffirms LockBit’s position as the most active ransomware-as-a-service (RaaS) provider, which echoes the findings in our reports for the first, second, and third quarters of 2022. BlackCat, on the other hand, pulled new extortion tricks up its sleeve, including the impersonation of a victim’s website and using it to publish stolen data on the clear web. The last quarter of the year saw ransomware actors spruce up their malware arsenal and explore new schemes to infiltrate, persist, and extort.
This report is based on data from RaaS and extortion groups’ leak sites, Trend Micro’s open-source intelligence (OSINT) research, and the Trend Micro™ Smart Protection Network™, collected from Oct. 1 to Dec. 31, 2022.
Ransomware victim count in the fourth quarter declined by 5.1% versus the third quarter as the number of active RaaS groups saw flat growth
We detected and blocked a total of 2,812,825 ransomware threats across email, URL, and file layers, based on data from our telemetry in the fourth quarter of 2022. Threat detections in the fourth quarter declined significantly by 32% compared to the third quarter, which garnered a total of 4,138,110 detections.
Fourth-quarter data from ransomware groups’ leak sites (ones that published attacks on organizations that were successfully compromised but refused to pay ransom) indicates that the total number of ransomware victim organizations went down by 36 or a 5.1% decrease compared to the third quarter of 2022. Meanwhile, the needle barely moved when it comes to the total number of active RaaS and RaaS-related groups in the fourth quarter: the number went up to a total of 32 from 30 in the third quarter of 2022.
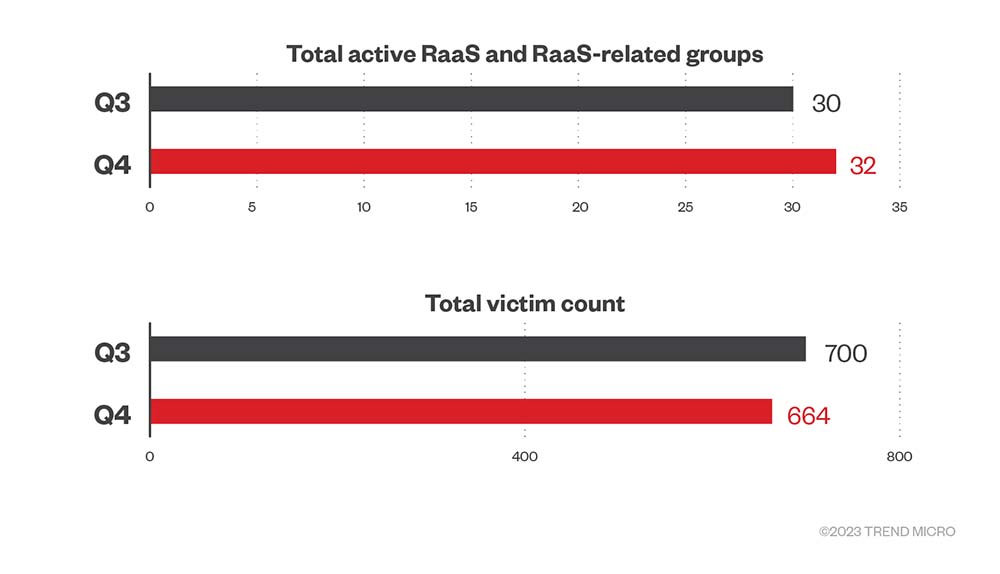
Figure 1. The numbers of active RaaS and extortion groups and victim organizations of successful ransomware attacks in the fourth quarter of 2022
Source: RaaS and extortion groups’ leak sites
Established ransomware groups lead the list of the most active ransomware groups in the fourth quarter of 2022
Data from ransomware groups’ leak sites revealed that the highest numbers of successful attacks in the three-month span were campaigns carried out by prominent ransomware groups: LockBit, BlackCat, and Royal, which is being run by former members of Conti.
LockBit firmly held the number one spot from January to December 2022. It accounted for more than a third of the total number of victim organizations in the first (35.8%), second (34.9%), and third (32.9%) quarters, but its share dropped significantly to 22.3% in the last quarter of 2022. Of the attacks in the fourth quarter, 11.7% belonged to BlackCat while 10.7% is attributed to Royal.
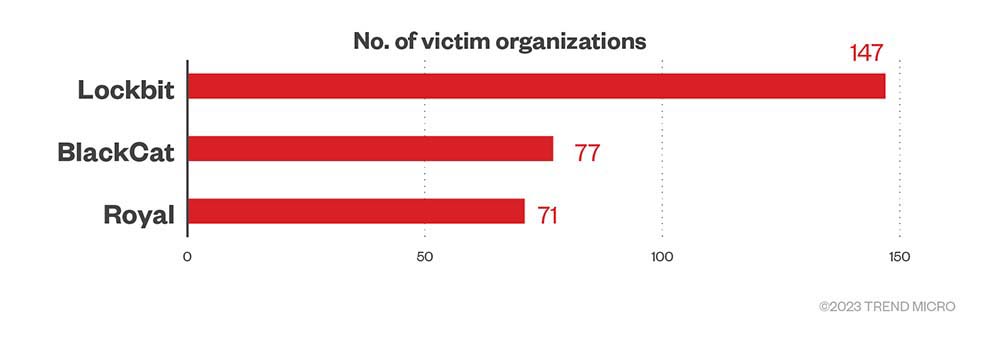
Figure 2. The most active ransomware families used in successful RaaS and extortion attacks in terms of victim organizations from Oct. 1 to Dec. 31, 2022
Source: RaaS and extortion groups’ leak sites
Information from our monitoring of ransomware attacks that attempted to compromise Trend Micro customers in the fourth quarter of 2022 showed that LockBit’s level of activity appears to approximate the 200-mark per month. This activity was unlike what was seen in the previous three quarters, wherein monthly numbers varied greatly and did not bear any discernible pattern. Meanwhile, there was no detection of BlackCat attempts in October, but November tallied 194 attempts. BlackCat numbers rose sharply in December to 457, a 135.6% increase. We did not detect any attempts by Royal on our customers during this period.
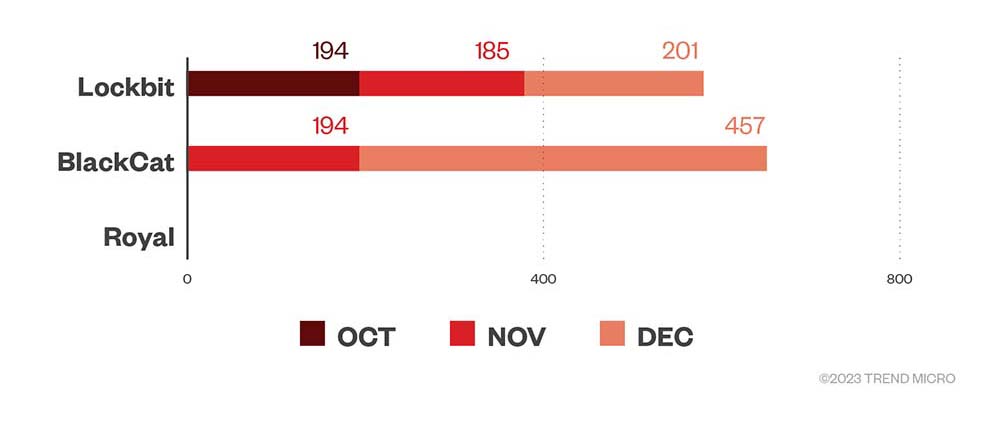
Figure 3. The numbers of ransomware file detections of LockBit, BlackCat, and Royal ransomware in machines per month in the fourth quarter of 2022
Source: Trend Micro Smart Protection Network
LockBit sustains yearlong lead and claims many high-profile attacks in the fourth quarter
Since its discovery in September 2019, LockBit has built a track record of frequently upgrading its malware capabilities and implementing affiliate expansion programs to solidify its position in the RaaS field. Aside from the deft use of double extortion in its tactics, LockBit has stayed ahead of the pack by launching unique initiatives. LockBit operators offered the Zcash cryptocurrency payment option and the ransomware bug bounty program to security researchers — the first of its kind in the for-hire business — at the same time that LockBit 3.0 was released in mid-2022.
A German multinational automotive group was among LockBit’s high-value victims in November 2022. LockBit threatened to publish the stolen data on its leak site if the organization declined to settle the ransom within the twenty-two-hour deadline, which suggests that the firm likely refused to negotiate. It should also be noted that the company also declined to confirm the breach according to reports.
The fourth quarter was indeed an interesting one for LockBit, as it provided a free decryptor to one of its victims and even issued an apology for the attack. On December 18, 2022, a hospital for children suffered a ransomware attack that disrupted its internal and corporate systems, website, and phone lines. Threat researcher Dominic Alvieri published on Twitter that LockBit issued a formal apology for the attack, provided a free decryptor, and blocked the rogue affiliate who violated the ransomware gang’s affiliate program rules.
On Dec. 26, 2022, LockBit launched an attack on the Port of Lisbon, one of the busiest hubs in Europe. Port officials disclosed to Portuguese news outlet Publico that its systems were attacked, but operations continued. The report also stated that the port administration immediately rolled out security protocols and incident response measures and worked closely with authorities to secure their systems and data.
BlackCat clones a victim’s website as a novel extortion tactic
Before it bid the year goodbye, BlackCat (aka AlphaVM, AlphaV, or ALPHV) compromised an organization in the financial services industry in late December 2022 using a new and creative extortion tactic. To tighten the proverbial noose, BlackCat operators penalized victims for their failure to meet ransom demands in two ways: first, by publishing all the exfiltrated data on the gang’s Tor site, and second, by leaking stolen files on a site that is a replica of the victim’s and using a typosquatted domain name. Since sites published on the dark web have limited visibility, sharing stolen information on the clear web exerts more pressure on the victim by making it accessible to the public.
BlackCat operators also abused a Telegram account to promote their new RaaS offering: a prepackaged Log4J Auto Exploiter. BlackCat operators assert that the tool can be used to spread the BlackCat malware laterally within a network.
A Colombian energy supplier was among BlackCat’s victims in the fourth quarter of 2022. The organization, which belongs to the critical infrastructure sector and is one of the country’s biggest public energy, water, and gas providers, had to pause operations and take down online services because of the cyberattack. BlackCat claims to have stolen a wide variety of corporate data during the assault, but the extent of the data theft is unknown.
Royal, a breakaway group from Conti, stakes its multimillion-dollar claim in the fourth quarter
We monitored multiple attacks from Royal ransomware from September to December 2022, which mostly targeted organizations in the US and Brazil. Researchers may have first spotted Royal in September 2022, but one report asserts that the gang began its operations as early as January 2022. The report also states that Royal ransomware operators have deep roots in the cybercrime business, which accounts for its swift rise to prominence in the ransomware sphere. Royal is allegedly run by former members of Conti Team One, based on the mind map shared by the late Vitali Kremez.
We examined Royal ransomware attacks and learned that the group combines the use of old and new techniques, suggesting an extensive knowledge of the ransomware scene. Their use of callback phishing to deceive victims into installing remote desktop malware lets them infiltrate victims’ machines with minimal effort. Meanwhile, the ransomware group’s intermittent encryption tactics also speed up their encryption of victims’ files.
In its early campaigns, Royal deployed BlackCat’s encryptor. It then shifted to its own called Zeon, which dropped ransom notes similar to Conti’s. Royal later rebranded and began using Royal in the ransom notes generated by its new encryptor.
On Dec. 7, 2022, the US Department of Health and Human Services (HHS) issued a warning to healthcare organizations regarding Royal ransomware threats. A report mentioned that ransom demands range from US$250,000 to over US$2 million. Royal is reportedly a private group with no affiliates. Thus, it cannot be classified as a RaaS provider.
Small and midsize businesses were favored targets in the fourth quarter
The targeting of small and midsize businesses has been a recurring theme in all of our quarterly ransomware reports for 2022, largely because these businesses have fewer IT security resources to respond to cyberattacks.
Data from LockBit’s leak site showed that more than half of its victims were small organizations (with 200 employees at most), accounting for 51.7% in the fourth quarter, which is a slight dip from a 57.8% share in the third quarter of 2022. Midsize businesses (with 201 to 1,000 employees) comprised 21.7% in the fourth quarter of the year. Meanwhile, large enterprises (with more than 1,000 employees) accounted for 15.6% in the fourth quarter, a slight decrease from the third quarter at 16.1%.
BlackCat’s successful attacks in the fourth quarter targeted small businesses, making up 38.9% of the total, followed by midsize companies comprising almost a third of the total at 28.6%. Meanwhile, large enterprises accounted for a quarter of BlackCat’s victims.
Small businesses comprised 51.9% of Royal’s victims in the fourth quarter, while midsize organizations got a 26.8% share. Large enterprises made up 11.3% for this period.
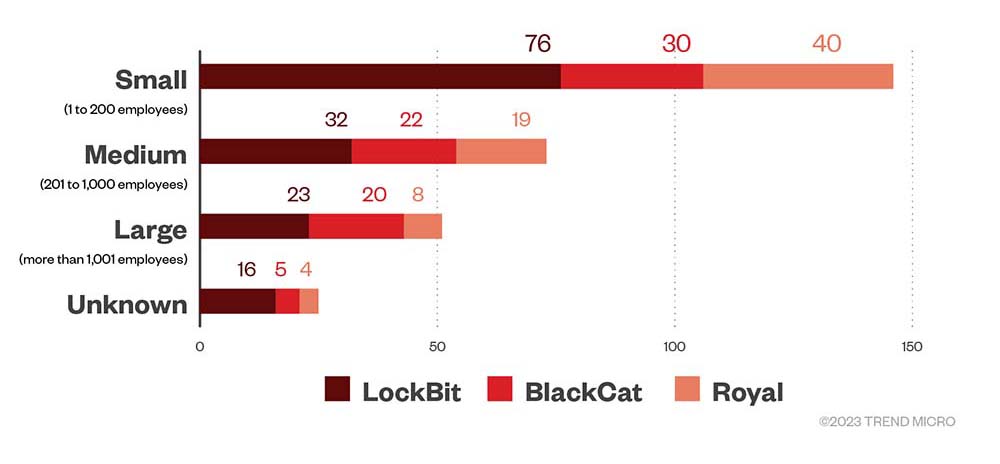
Figure 4. The distribution by organization size of LockBit, BlackCat, and Royal ransomware’s successful attacks in terms of victim organizations in the fourth quarter of 2022
Source: LockBit, BlackCat, and Royal’s leak sites and Trend Micro’s OSINT research
Fast-moving consumer goods (FMCG), government, and manufacturing industries were the most targeted in the fourth quarter
Our telemetry from October to December 2022 showed that FMCG, government, and manufacturing industries grabbed the top three ranks in terms of ransomware file detections. The rankings in November mirrored those in October, while manufacturing moved up the number one spot in December from the third rank in the two previous months.
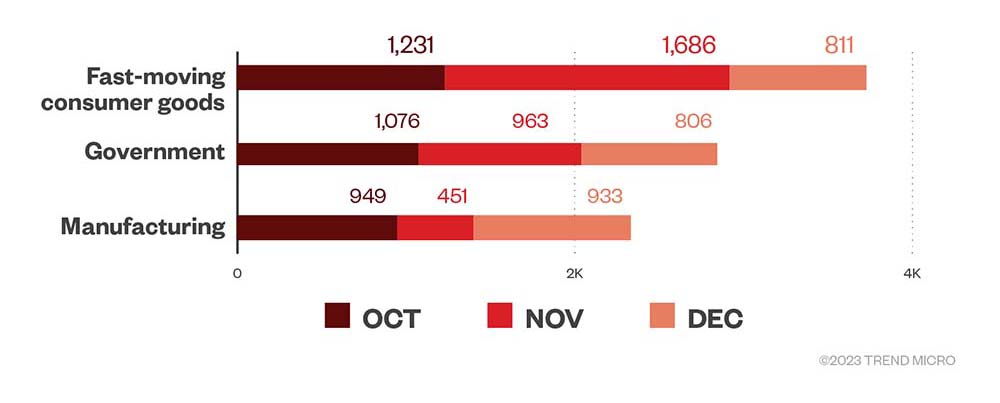
Figure 5. The top three industries in terms of ransomware file detections in machines per month in the fourth quarter of 2022
Source: Trend Micro Smart Protection Network
Organizations in IT, healthcare, and manufacturing occupied the top three spots in the fourth quarter of 2022 in terms of the number of file detections. These industries have also been consistently included in the top 10 list of favored targets by RaaS and extortion groups for the entire year.
The apparent preference for big-game targets shown by ransomware actors in 2022 will inevitably persist in the future. Organizations that belong to the list of the most affected industries possess business characteristics that cybercriminals seek, such as an expansive attack surface by virtue of the number of their offices worldwide, the significant number of workers dispersed across the globe, and the variety and scope of products and services that they provide.
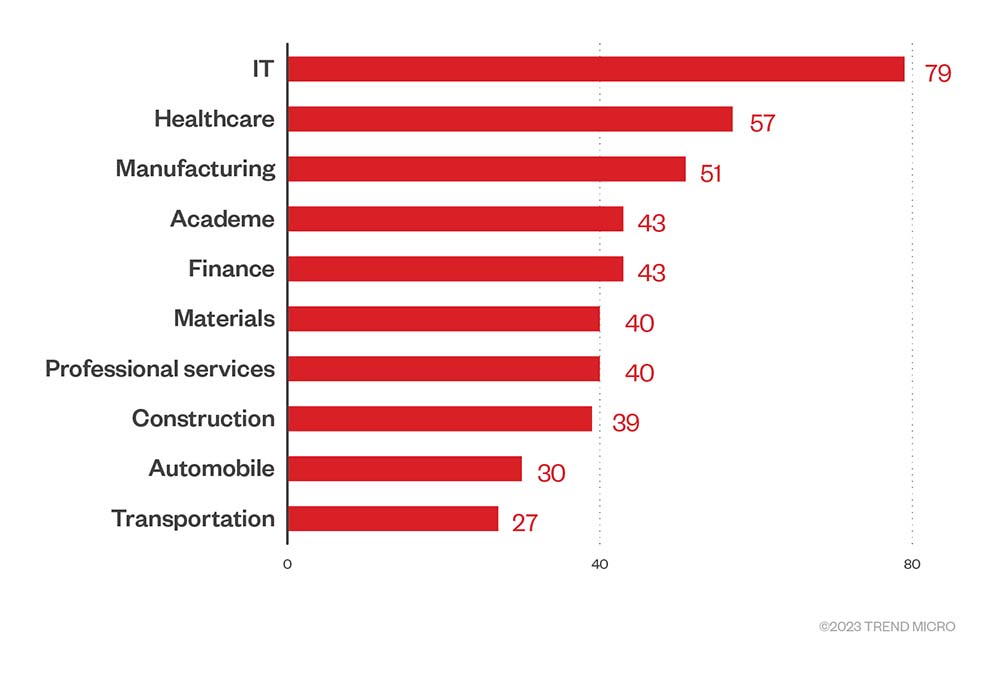
Figure 6. The top 10 industries affected by successful RaaS and extortion attacks in the fourth quarter of 2022
Source: RaaS and extortion groups’ leak sites and Trend Micro’s OSINT research
Data from the LockBit ransomware group’s leak site in the fourth quarter of 2022 shows that the finance, IT, and healthcare industries were in the top three list of LockBit’s victims. Along with manufacturing and professional services, these industries have constantly been in the top 10 list of industries affected by LockBit’s attacks throughout 2022. Notably, while LockBit severely penalized an affiliate for having violated the group’s code when a rogue member attacked a children’s hospital, we still saw healthcare organizations posted as victims on its leak site.
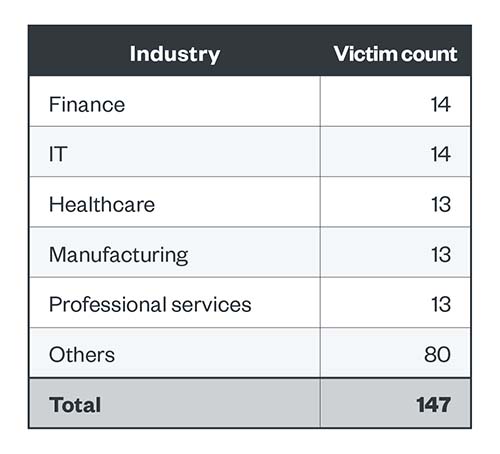
Table 1. The top five industries affected by LockBit’s successful attacks in terms of victim organizations in the fourth quarter of 2022
Source: LockBit’s leak site and Trend Micro’s OSINT research
Of BlackCat’s successful attacks, 14.3% belonged to the IT industry, followed by manufacturing at 10.4%. Like LockBit and Royal, BlackCat includes healthcare in its top 5 list of affected industries.
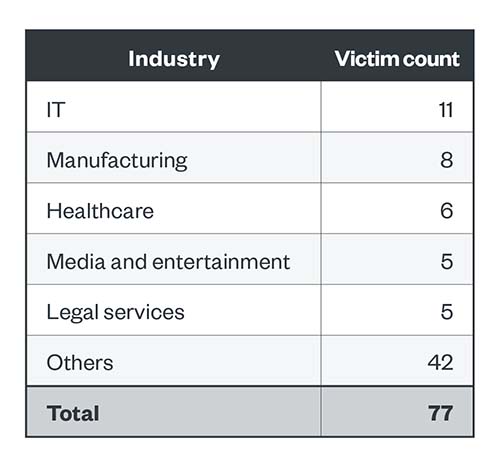
Table 2. The top five industries affected by BlackCat’s successful attacks in terms of victim organizations in the fourth quarter of 2022
Source: BlackCat’s leak site and Trend Micro’s OSINT research
Royal’s target industries for the fourth quarter of 2022 also included IT, finance, and healthcare, which were also in the top five ranks of the aggregate list shown in Figure 6. Data from its leak site showed that nine organizations belonged to the IT industry, while finance and materials got eight and six, respectively.
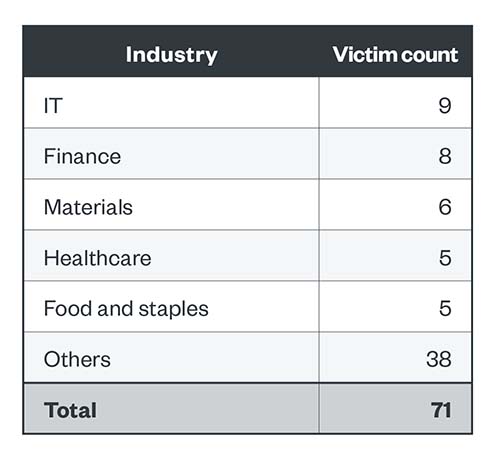
Table 3. The top five industries affected by Royal ransomware’s successful attacks in terms of victim organizations in the fourth quarter of 2022
Source: Royal ransomware’s leak site and Trend Micro’s OSINT research
Organizations in the US grab a two-thirds share of the victim count in the fourth quarter
A close look at the ransomware and extortion groups’ leak sites shows that organizations based in the US were the hardest hit by ransomware attacks from October to December 2022, accounting for 42% of the total victim count. From the first to the fourth quarter, ransomware actors have demonstrated a strong preference for targeting US-based organizations. Ransomware attacks also took their toll on a number of European countries, such as the United Kingdom and Germany, in the fourth quarter.
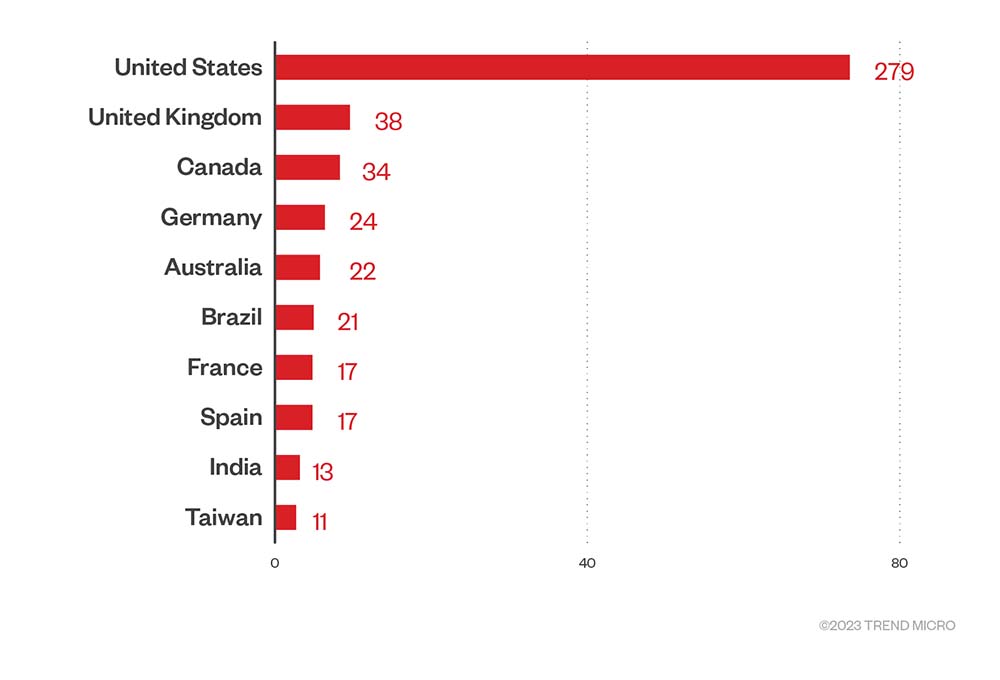
Figure 7. The top 10 countries affected by successful RaaS and extortion attacks in the fourth quarter of 2022
Source: RaaS and extortion groups’ leak sites and Trend Micro’s OSINT research
According to data from LockBit’s leak site, more than a third of its victim count in the fourth quarter belonged to organizations based in North America at 44%. Meanwhile, the number of victims in the Asia-Pacific region is at 42, which is equivalent to 28.6% of the total. In the second and third quarters of 2022, Europe-based organizations comprised about a third of the victim count. However, victim count in Europe dropped to 23.1%, as the number of victims in Asia-Pacific increased in the fourth quarter.
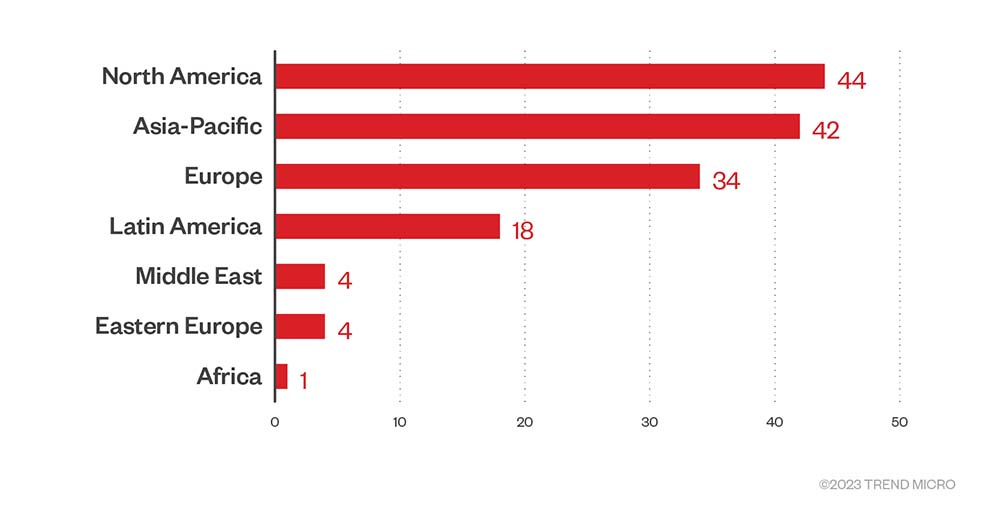
Figure 8. The top regions affected by LockBit’s successful attacks in terms of victim organizations in the fourth quarter of 2022
Source: LockBit’s leak site and Trend Micro’s OSINT research
More than half of BlackCat’s victims were in North America at 51.9% of the total number of successful attacks in the fourth quarter. Organizations in Europe ranked second, taking an 18.2% share, followed by Asia-Pacific, at 15.6%.
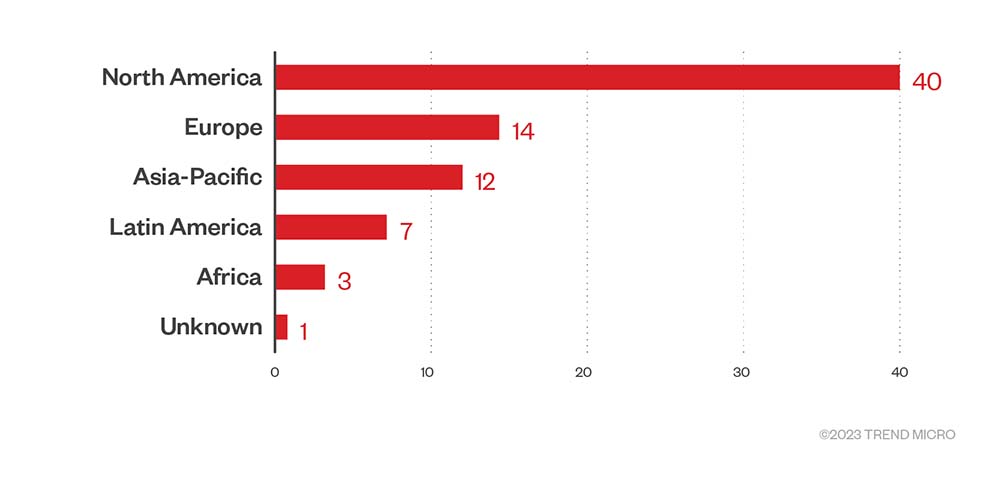
Figure 9. The top regions affected by BlackCat’s successful attacks in terms of victim organizations in the fourth quarter of 2022
Source: BlackCat’s leak site and Trend Micro’s OSINT research
Three-quarters of Royal ransomware’s victims in the fourth quarter were in North America, while those in Europe were a far second at 14.1% of the total victim count. The rest of Royal’s victims were spread across Latin America, with only two in Asia-Pacific, and one each in Africa and the Middle East.
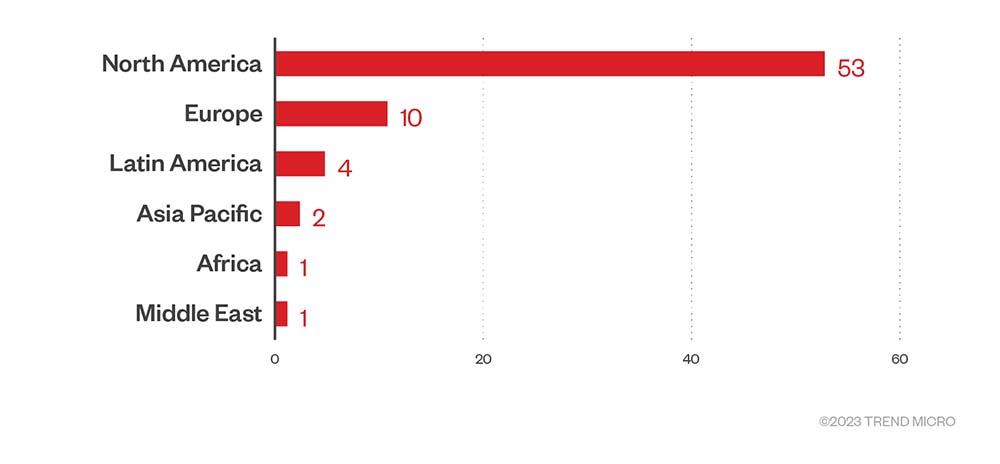
Figure 10. The top regions affected by Royal ransomware’s successful attacks in terms of victim organizations in the fourth quarter of 2022
Source: Royal’s leak site and Trend Micro’s OSINT research
Adopting a proactive mindset and implementing security best practices help mitigate the risks of ransomware attacks
The growing motivation of ransomware groups to improve their craft and seize a bigger share of a very lucrative market is a pervasive threat that organizations, regardless of size, must be cognizant of to ensure business health and longevity. Unfortunately, all indicators point to the likelihood of cyberattacks increasing as many organizations worldwide have significantly shifted their conduct of business to be in the online space. Organizations can mitigate the risk of ransomware attacks by adopting a proactive cybersecurity mindset and implementing the following security best practices:
- Enable multifactor authentication (MFA). Organizations should implement policies that require employees who access or store company data on their devices to enable MFA as an added layer of protection to prevent unauthorized access to sensitive information.
- Have a data backup. Organizations should follow the “3-2-1 rule” to safeguard their important files: Create at least three backup copies in two different file formats, with one of those copies stored off-site.
- Keep systems up to date. Organizations should update all their applications, operating systems, and other software as soon as vendors and developers release patches. Doing so minimizes the opportunities for ransomware actors to exploit vulnerabilities that enable system breaches.
- Verify emails before opening them. Malicious actors rely on tried-and-tested ways to compromise systems, such as using embedded links or executable downloads attached in emails sent to employees to install malware. Organizations should therefore train their employees to be aware of such methods to avoid them.
- Follow established security frameworks. There’s no need to reinvent the proverbial wheel. Organizations can craft cybersecurity strategies based on the security frameworks created by the Center of Internet Security (CIS) and the National Institute of Standards and Technology (NIST). The security measures and best practices outlined in these frameworks can guide members of an organization’s security team in developing their own threat mitigation plans.
Organizations can strengthen their cybersecurity infrastructure through multilayered detection and response solutions that can anticipate and respond to ransomware movements before operators can launch an attack. Trend Micro Vision One™ is equipped with extended detection and response (XDR) capabilities that gather and automatically correlate data across multiple security layers — including email, endpoints, servers, cloud workloads, and networks — to prevent ransomware attack attempts.
Organizations can also benefit from solutions with network detection and response (NDR) capabilities, which can give them broader visibility over their network traffic. Trend Micro Network One™ provides security teams with the critical network telemetry they need to form a more definitive picture of their environment, accelerate their response, and avert future attacks.
The supplementary data sheet for this report, including data from RaaS and extortion groups’ leak sites, Trend Micro’s OSINT research, and the Trend Micro Smart Protection Network, can be downloaded here.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Archive
- Phobos Emerges as a Formidable Threat in Q1 2024, LockBit Stays in the Top Spot: Ransomware in Q1 2024
- Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023
- LockBit, BlackCat, and Clop Prevail as Top RAAS Groups: Ransomware in 1H 2023
- LockBit, BlackCat, and Royal Dominate the Ransomware Scene: Ransomware in Q4 2022
- LockBit and Black Basta Are the Most Active RaaS Groups as Victim Count Rises: Ransomware in Q2 and Q3 2022

 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks Today’s Cloud and Container Misconfigurations Are Tomorrow’s Critical Vulnerabilities
Today’s Cloud and Container Misconfigurations Are Tomorrow’s Critical Vulnerabilities Ransomware Spotlight: INC
Ransomware Spotlight: INC The Realities of Quantum Machine Learning
The Realities of Quantum Machine Learning