Masque, FakeID, and Other Notable Mobile Threats of 2H 2014
Users are going more and more into mobile, but threats have come along to crash the trip. As the year 2014 comes to a close, cybercriminals latch on to personal data inside mobile devices by attacking popular platforms, finding device flaws, improving the quality of fake apps, and direct-selling in the underground market.
Mobile threats are rapidly becoming more complex. Malware creators are banking on the average user's lack of awareness when it comes to properly setting mobile devices and downloading apps from known safe, legitimate sources. Moreover, they also rely on most users’ blatant disregard for recommended platform security to gain more features or get free apps, which are common reasons why many jailbreak or root their mobile devices.
In the first half of 2014, we became witness to how the number of mobile malware and high risk apps reached two million unique samples and counting, just six months after reaching the one million mark. We also saw mobile malware evolving into more sophisticated strains, as is the case with the coin miner ANDROIDOS_KAGECOIN and mobile-jumping ransomware ANDROIDOS_LOCKER.A.
This report details how the rest of the year panned out in terms of notable mobile threats and trends during the second half of 2014.
Malware and High Risk Apps Now at 4.37 Million
The number of mobile malware has more than doubled in the second half of 2014, just six months after hitting the two million milestone. There are now a total of 4.37 million malicious and high risk apps out there. This represents a rough 68% increase from 2.6 million by the end of the first half of the year.
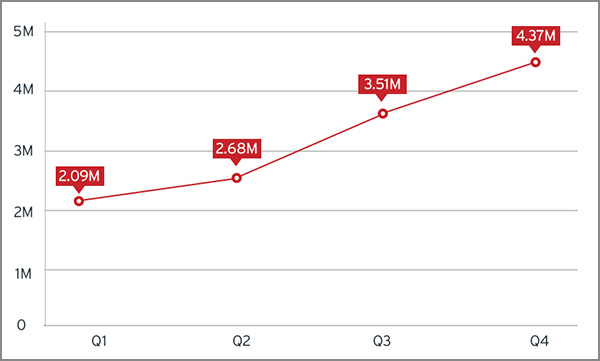
Growth of malicious and high-risk apps in 2014
Picking out the blatantly malicious apps, malware apps, from the millions we detected, we found that most of them are variants of the following top mobile malware families:
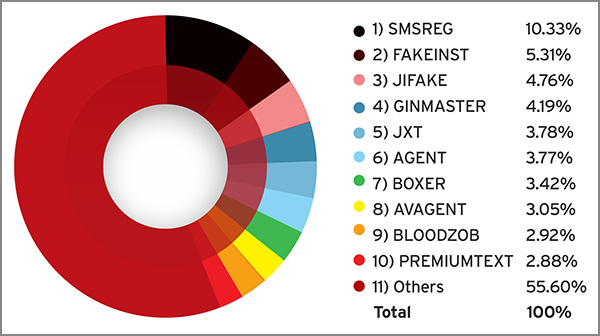
Top mobile malware families as of 2014
Categorizing how these apps affect mobile devices, we also found that roughly 69% of the threats on mobile come from adware. Adware apps are mobile apps that serve ads in a way that distracts users from maximizing their devices. Premium service abusers (PSAs) followed, making up roughly 24% of the malicious and high risk apps. PSAs are known for incurring premium costs for mobile users without their consent.
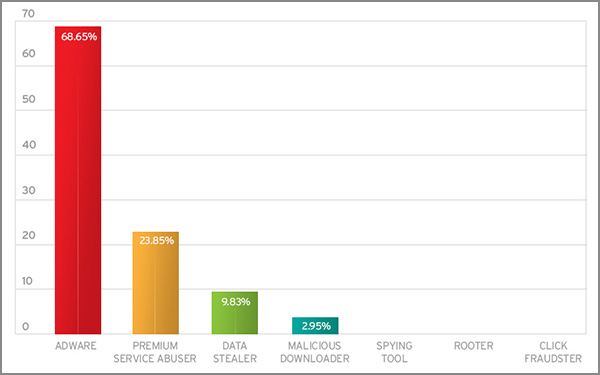
Top mobile threat type distribution in 2014
Moreover, the following adware families conquered the list in the second half of 2014:
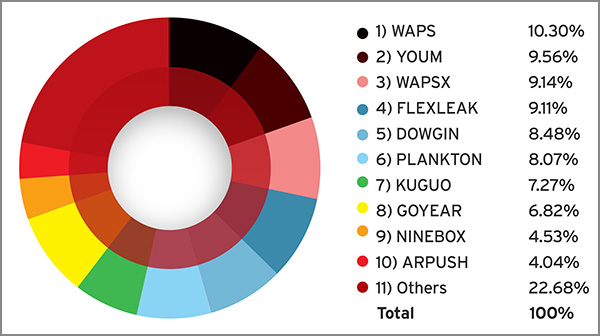
Top mobile adware families as of 2014
Impactful Device and App Flaws, Setbacks to Mobile Safety
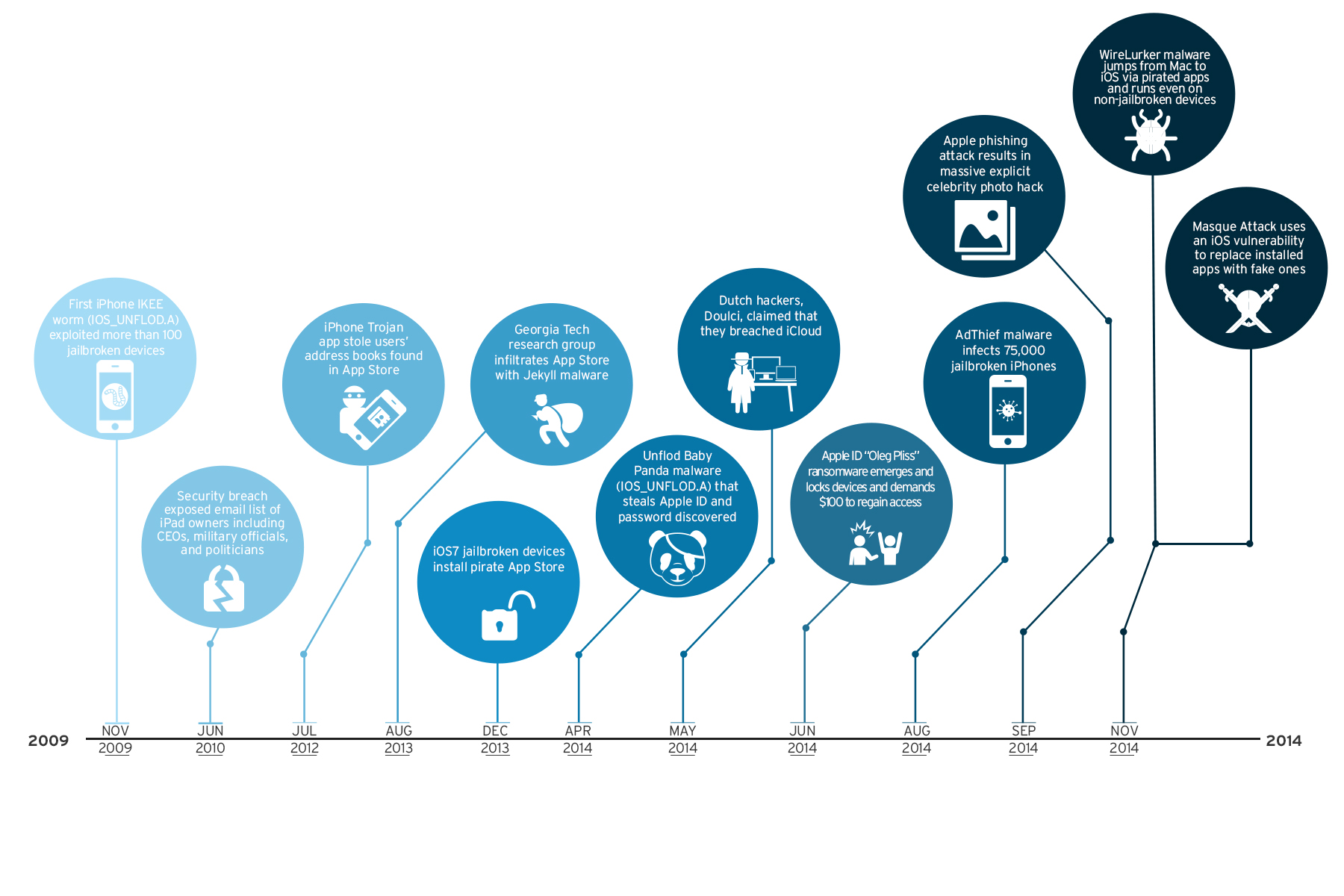
The year ends with strong reminders from mobile threats that poor mobile habits coupled with device vulnerabilities form an insecure landscape. This covers a variety of platforms, with Android and iOS being the most popular ones. As a result, users of both platforms are similarly popular attack targets. A variety of malware and high risk apps continue to attack Android users. Also despite the walled garden approach of Apple to protect the iOS environment, we still saw increasingly more dangerous threats that successfully penetrated the holes left by jailbreaking.
Timeline of iOS threats, 2009 to 2014
In November, two high-profile mobile threats attacked the iOS environment. The combined Mac and iOS Wirelurker malware, detected as OSX_WIRELURK.A, was able to jump from Trojanized apps installed in Mac computers to USB-connected iOS devices. Wirelurker was successful in installing itself even on non-jailbroken devices using a stolen certificate. Even as the malware did no particular harm to the devices, we believe this attack technique will aid cybercriminals in designing more destructive iOS malware apps.
In the same month, news of the Masque malware then blew up, threatening both jailbroken and non-jailbroken iOS device users with cybercriminals that could access the unencrypted data used by their legitimate apps. Attacks from both Masque and Wirelurker put apps created and used via enterprise provisioning in the spotlight as a viable way for cybercriminals to access personal information.
[Read:Before Masque and WireLurker: iOS Threats That Cracked the Walled Garden]
Meanwhile, a recent vulnerability in the Android platform that affects how cross-signed certificates are handled was discovered. This flaw is present in Android features that use JarFile and KeyStore—two commonly used classes in the Android framework.
Apart from this, mobile users were subjected to a dizzying flurry of other mobile vulnerabilities in the latter half of the year. News of the Android FakeID vulnerability, which allows malicious apps to impersonate legitimate ones, caught fire as it affects all Android devices running on platforms starting from Android 2.1 (“Éclair”) to 4.4 (“KitKat”).
We also heard of how attackers were able to bypass the Same Origin Policy in Android’s built-in browser, potentially allowing malicious apps to access data and cookies that were used in legitimate sites.Just recently, cybercriminals were found leading Facebook users to a malicious site that exploits this flaw.
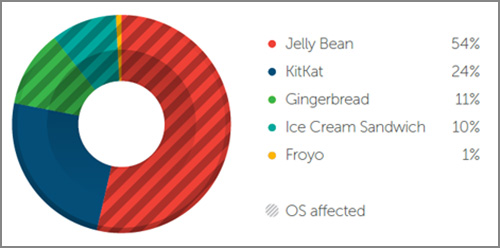
Android Operating Systems Affected by FakeID and Android Browser Vulnerabilities
Moreover, vulnerabilities in popular apps introduced additional attack vectors for mobile threats. Several in-app payment SDK flaws in apps like Spotify, Evernote, Alipay, and others allowed phishing attacks to be used against users. As we have noted in the threat roundup for 3Q 2014, it may take longer time to patch flaws in apps ran by relatively small businesses.
Conclusion
From what we have seen, we expect that mobile malware creators will follow the mobile money trail. This coming 2015, cybercriminals will likely take advantage of a number of mobile payment options that have rolled out for mobile shoppers.We predict that new mobile payment methods will introduce new threats in the form of device or app vulnerabilities, social engineering scams, and/or taking advantage of users’ unsafe mobile shopping habits.
Given all these, mobile users are called out to develop safe mobile habits. This includes the use of strong passwords or secure password managers, the installation of a security app to scan for mobile malware or adware, a more discerning eye for mobile promos or links that could lead to data theft, regular patching of mobile device flaws, and a personal effort to regularly check and prepare for the latest in mobile threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One