A Security Guide to IoT-Cloud Convergence
 The internet of things (IoT) has risen as one solution to the demands that have emerged because of the worldwide pandemic. The IoT, with its key characteristic of minimizing human interaction in performing a myriad of functions, seems a perfect fit in a world of remote setups and social distancing. But it is thanks to cloud computing that enterprises can smoothly make large-scale deployments of the IoT.
The internet of things (IoT) has risen as one solution to the demands that have emerged because of the worldwide pandemic. The IoT, with its key characteristic of minimizing human interaction in performing a myriad of functions, seems a perfect fit in a world of remote setups and social distancing. But it is thanks to cloud computing that enterprises can smoothly make large-scale deployments of the IoT.
The integration of the IoT and cloud computing — as prominently manifested in the profusion of cloud services that power the IoT, collectively known as the IoT cloud — poses a new frontier for how industries are run. It is thus important not to overlook their respective security risks and the implications of these risks when the two technologies converge.
The role of cloud computing in the IoT
With regard to the security of IoT-cloud convergence, it would be best to understand how the IoT and cloud computing work together. The IoT by itself works on a diverse selection of devices that fit into the requirements of different industries or settings. Cloud computing, on the other hand, involves storing and accessing data, applications, or services over the internet — that is, in the cloud — instead of in physical servers or mainframes.
The cloud helps IoT environments by all but removing their defining limitations, such as their processing and storage capacities. The IoT, meanwhile, connects the cloud to physical or real-world devices. Figure 1 shows an example of a cloud-based IoT infrastructure.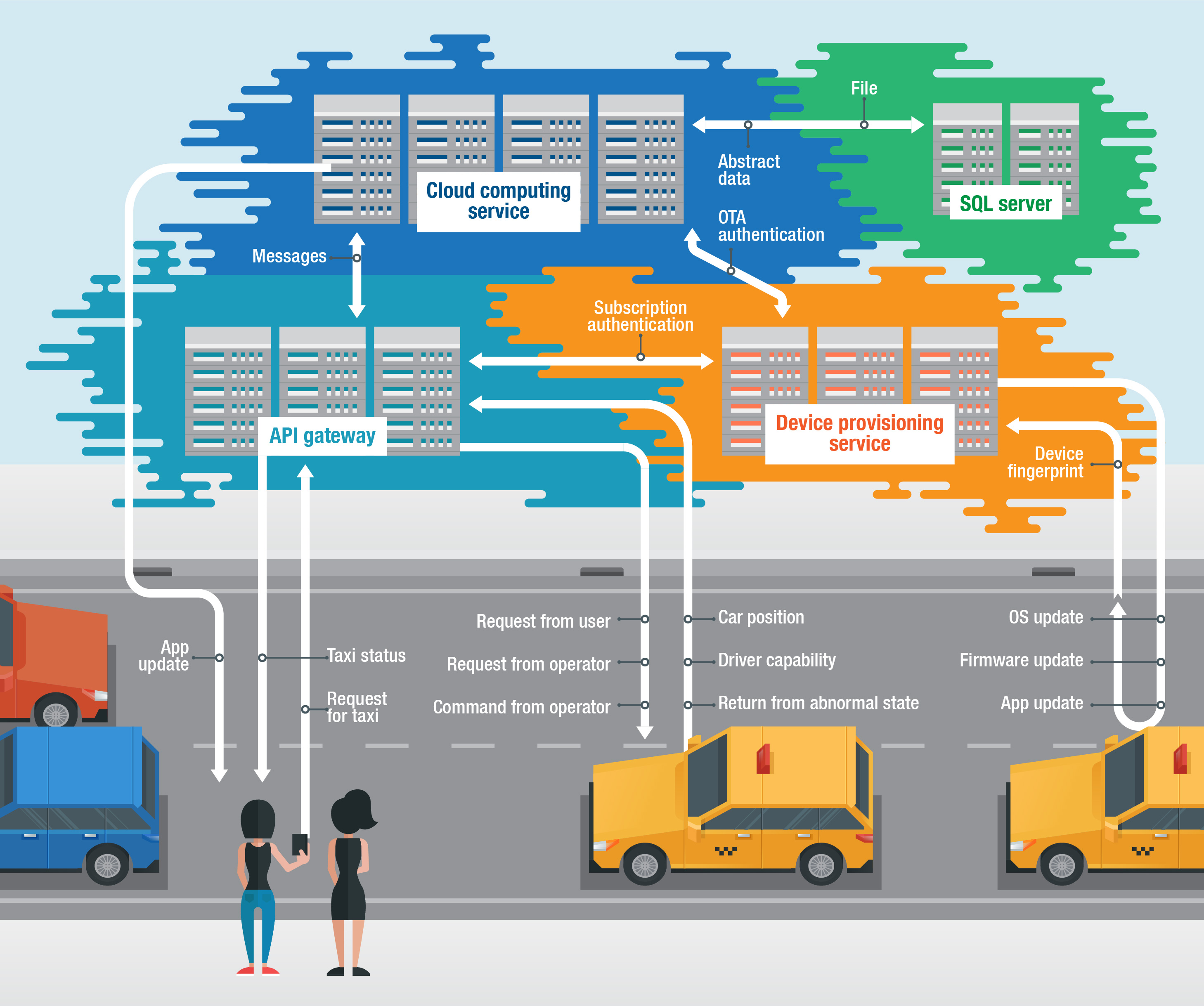
Figure 1. An example of a cloud-based IoT infrastructure
The following are some of the other advantages of IoT-cloud convergence:
- Remote operation and interoperability: IoT devices do not typically have the resources for interoperability. Integration with the cloud, which is by nature interoperable, allows support engineers and device administrators to perform remote tasks (such as gathering data on their assets, conducting maintenance, and setting configurations) on IoT devices deployed in the field, which is a crucial requirement in present times.
- Unlimited data storage: The IoT handles troves of unstructured data coming from multiple sensors. The cloud is known for its near limitless storage capacity. When the two are combined, it opens up more space for aggregation and analysis of data.
- Unlimited processing capabilities: IoT devices and apps have limited processing capabilities, often just enough to perform their specific functions. Processing of a lot of data is done on a separate node. Integration with the cloud opens up its unlimited virtual processing capabilities, including the use of artificial intelligence (AI) and machine learning (ML) for data-driven decision-making and improvements.
- Added security measures: The cloud offers features that address some of the security gaps in the IoT. Examples of these features include enhancement of authentication mechanisms and device identity verification.
Security challenges
While it is true that the cloud offers solutions that can address some of the security gaps of the IoT, the integration of the two does not instantly solve the threats both technologies face. In some ways, IoT-cloud convergence elevates the urgency of these security risks as IoT-related weaknesses could cause more complicated problems in the cloud ecosystem, and vice versa.
The following are some of the challenges enterprises might face in creating secure IoT-cloud environments:
- Risk arising from centralizing the entry into critical infrastructure. The integration of the IoT and the cloud significantly reduces the attack surface by restricting all incoming and outgoing traffic to pass through the API gateway in the cloud. A high-end firewall is necessary to protect this flow of data through this gateway, but this highlights an old security concern, which is whether the firewall is sufficient defense. While a single entry minimizes the attack surface, it directs attention to a single target for potential attackers. If a malicious actor finds the right opportunity, this entry could somehow become their very “tunnel” into the infrastructure.
- Unsecure communication and data flow between the edge and the cloud: If the endpoints or the cloud has inadequate security features, such as authentication and encryption, this could put access controls and the integrity of the data sent between these two points at risk.
- Privacy and authorization issues: Enterprises need to consider how IoT devices and sensors gather sensitive data, which in a cloud-based ecosystem would be transmitted to a space that is interoperable and serves other users and clients in the case of the public cloud. Enterprises need to discuss the location of their data with their respective cloud service providers especially in areas with strict capitalization.
- Poor implementation of the IoT: An IoT ecosystem where security measures (such as changing default passwords, applying network segmentation, and physically securing devices) are not adequately implemented is likely to carry its weaknesses over even with the integration with the cloud. For example, to access the cloud, IoT components need one key to pass the API gateway. In IoT implementations, endpoint devices should not store this key in plain text and the shared access signature (SAS), which allows limited access to the cloud, without a timeout.
- Cloud misconfiguration and other vulnerabilities: One of the most common problems faced in cloud computing is misconfiguration. Misconfigurations give malicious actors openings to conduct attacks such as data exfiltration. These and similar security flaws in the cloud could lead to serious consequences for the IoT ecosystem it is a part of.
Figure 2 illustrates the impact of these challenges if left unaccounted for, mapped to the top 10 web application security risks according to the Open Web Application Security Project (OWASP).
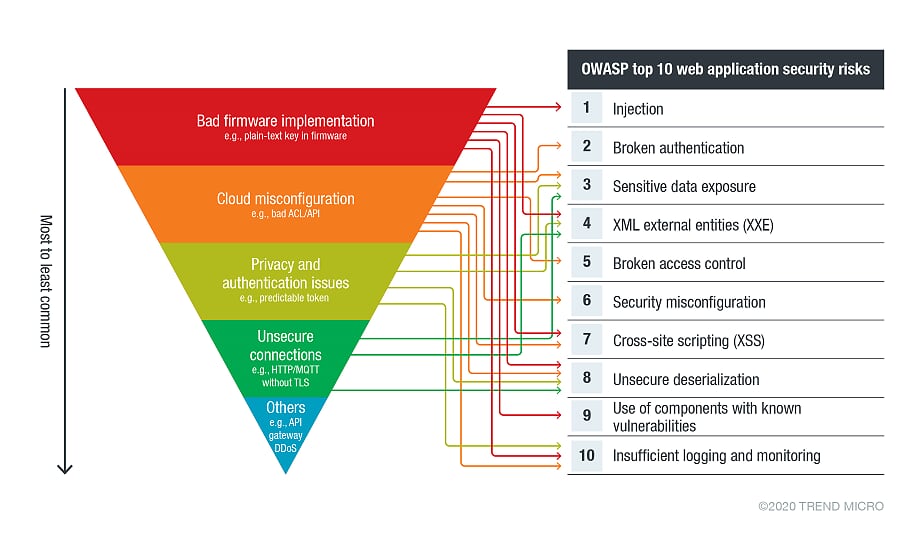
Many of these issues are discussed in a publication by the European Network and Information Security Agency (ENISA). Our discussion on cloud-based IoT solutions also details the advantages and disadvantages of IoT-cloud ecosystems and highlights other attack vectors.
Secure IoT-cloud convergence
Based on the security challenges discussed, ensuring secure IoT-cloud implementation already minimizes the risks that could arise from the integration of the two technologies. Enterprises can also apply additional technologies and take steps to make sure that their entire ecosystem is secure, from the cloud to the IoT endpoints.
The following are a few other pointers that enterprises can follow to ensure the security of their IoT-cloud integration:
- Monitor and secure the flow of data early into the process. The flow of data from IoT endpoints to the cloud needs to be secured from the outset. Enterprises need to implement monitoring and filtering tools at the edge so that data is monitored early into processing. This gives ample opportunity to detect suspicious activity, determine anomalies, and ensure all connected devices are identified.
- Use cloud-based solutions to bring security closer to the edge. Enterprises need to secure their edge devices from both physical threats and cyberattacks. Given the limitations of edge computing, cloud-based solutions can be used to deliver added security and processing capabilities. Fog computing, an infrastructure located between the edge and the cloud, is one recommendation that brings some cloud resources closer to the edge.
- Perform vulnerability checks regularly. Errors can be detected using regular vulnerability testing. Enterprises can opt to conduct vulnerability testing to the entire ecosystem or only to a specific component, as long as it is done with regularity.
- Ensure continuous updates and patches. Updates and patches are key to preventing the exploitation of IoT vulnerabilities. Fortunately, enterprises can take advantage of the cloud to efficiently and securely distribute software updates.
- Use secure passwords for both IoT devices and linked cloud services. Weak passwords continue to contribute to cases of successful data breaches. As passwords remain the main method of authentication, enterprises should have stringent password policies. After all, neither IoT devices nor cloud services are immune to intrusions afforded by weak, guessable credentials.
- Define a clear, effective, and detailed access control plan. Enterprises need to create a complete access control plan that encompasses the entire environment, from the cloud to edge devices. All users, groups, or roles need to be identified for detailed authentication and authorization policies that are applied throughout the IoT-cloud ecosystem. The principle of least privilege, which suggests that users be allowed only the minimum access right or permission they need to conduct their tasks, should also be applied.
- Employ code or application security best practices. Code or applications play an integral role in IoT-cloud ecosystems, providing organizations a means of simplified control and remote usability. Organizations should therefore attend to this facet of their ecosystems by employing best practices such as conducting static and dynamic application analysis.
- Adopt the shared responsibility model. Enterprises should not assume that data stored in the cloud is already protected from risks. They should be mindful of the shared responsibility model used by their cloud service providers. This clarifies which operational areas enterprises are responsible for securing, such as the configuration of cloud services. Enterprises can also employ cloud-specific security solutions to protect their cloud-native systems.
Enterprises can refer to the V-Model, which is a well-known guide for software development, especially with regard to the last two pointers. The model has been used to describe software development in publications on securing industrial automation (ISO/IEC 62443) and the automotive industry (ISO 21434 and ISO 26262), which shows its applicability to the IoT.
The main takeaway from these pointers is to ensure that all the layers in the IoT-cloud ecosystem are accounted for, with security and monitoring measures present from end to end. Our IoT and cloud resource pages provide further information on current threats and how to secure systems against them.
Current and future applications
Present times have shown the capabilities of IoT and cloud technologies. Grappling with the rapid changes caused by the Covid-19 pandemic, enterprises have had to innovate and lean on available technologies to continue their operations despite restrictions on their workforce. The IoT, with help from the cloud, has emerged as one of the technologies well suited for the job.
Businesses have accelerated their adoption of the IoT in an effort to maintain their operations and comply with health protocols. Many enterprises may lean on the cloud to make the most of their IoT environments. Security measures need to keep up with these changes lest enterprises risk threats that would endanger both their IoT and cloud ecosystems.
Reviewing and fortifying security measures for IoT and cloud ecosystems not only is in line with current trends, but also prepares enterprises for future innovations granted by these two technologies. The convergence of the IoT and the cloud redefines the IoT’s scalability for future expansions and gives the cloud an avenue for creating new services and boosting capabilities.
With additional insights from Shin Li.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Unmasking Task Scams to Prevent Financial Fallout From Fraud
- Beware of MCP Hardcoded Credentials: A Perfect Target for Threat Actors
- Lessons in Resilience from the Race to Patch SharePoint Vulnerabilities
- LLM as a Judge: Evaluating Accuracy in LLM Security Scans
- The Silent Leap: OpenAI’s New ChatGPT Agent Capabilities and Security Risks
 Trend Micro State of AI Security Report 1H 2025
Trend Micro State of AI Security Report 1H 2025 AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
The Road to Agentic AI: Navigating Architecture, Threats, and Solutions