Abusing Web Services Using Automated CAPTCHA-Breaking Services and Residential Proxies
This blog entry features three case studies that show how malicious actors evade the antispam, antibot, and antiabuse measures of online web services via residential proxies and CAPTCHA-breaking services.
With contributions from Philippe Lin, Fyodor Yarochkin, Matsukawa Bakuei, and Ryan Flores
Nowadays, it is imperative for online services to determine if web traffic comes from humans or automated bots. Doing so enables operators to filter out spam, unauthorized web crawling, large numbers of fake account registrations, comments and reviews, and most of all, attacks from bot-originating web traffic. The foremost tool used to filter out bots is the Completely Automated Public Turing test to tell Computers and Humans Apart (CAPTCHA).
CAPTCHA is a type of challenge-response test, which, in theory, only humans can pass. Common CAPTCHA tests consist of squiggly numbers and letters with textured backgrounds that users would need to identify and type in a text box. Nowadays, more advanced CAPTCHA challenges involve identifying specific objects, such as traffic lights or cars, in square images.
Simple CAPTCHAs, such as those that involve numbers and letters, can sometimes be defeated by Optical Character Recognition (OCR) techniques, while more challenging CAPTCHAs, such as those with twisted characters, can be defeated by automated solvers that are boosted by machine learning (ML). These CAPTCHA-defeating tactics have given rise to the development of more advanced CAPTCHA challenges, including identifying certain objects in a grid or rotating an object to its correct position. But online service operators face a slew of different challenges when automated web traffic defeats CAPTCHAs not by using bots, but by using human CAPTCHA solvers.
The rise of CAPTCHA-breaking services
Because cybercriminals are keen on breaking CAPTCHAs accurately, several services that are primarily geared toward this market demand have been created. These CAPTCHA-solving services don’t use OCR techniques or advanced machine learning methods; instead, they break CAPTCHAs by farming out CAPTCHA-breaking tasks to actual human solvers.
The CAPTCHA-solving service follows this straightforward workflow:
1. The customer of the CAPTCHA-breaking service encounters a CAPTCHA.

2. The customer submits the CAPTCHA to the CAPTCHA-breaking service.
3. The CAPTCHA-breaking service farms out tasks to one of their human solvers.
4. The human solver works out the CAPTCHA and submits the solution to the customer.
5.. The customer receives the CAPTCHA solution.
For customers of CAPTCHA-breaking services, this workflow is accessible via simple API calls. Customers don’t have to deal with the complexities of farming out CAPTCHA-breaking tasks to human solvers themselves. They would simply call an API to submit the CAPTCHA and call another API to get the solution to the CAPTCHA.
https://captcha-solving-service.com/in.php?key=APIKEY&method=userrecaptcha&googlekey=6Le_xxxxxx__mJ
&pageurl=https://target.domain/homepage.html
OK|01234567890
OK|CAPTCHA_SOLUTION_HASHES
This makes it easy for the customers of CAPTCHA-breaking services to develop automated tools against online web services. And because actual humans are solving CAPTCHAs, the purpose of filtering out automated bot traffic through these tests are rendered ineffective.
However, online web services do not solely rely on CAPTCHAs to guard against automated bot traffic. They can employ other means, such as IP address blacklisting. Bot operators have several options to evade IP address blacklists, and using proxyware is a popular option.
Obfuscating originating IP using proxyware
Proxyware are potentially risky applications that are distributed as free software tools. However, these applications covertly turn a user's computer into a proxy node. These proxy nodes would then become a network of geographically distributed proxy nodes.
Because these proxy nodes (which are on users' computers that connect to the internet using residential broadband services) can route potentially illegal web traffic, proxyware can expose users to risks and cyberthreats.
Operators of these networks of globally distributed proxy nodes oftentimes sell their proxy service to the public as residential proxies. We have observed some threat actors purchasing these proxy services and coupling them with CAPTCHA-breaking services to evade antispam, antibot, and antiabuse measures deployed by various online web services. We highlight some notable examples, some of which were heavily targeted by CAPTCHA-breaking services as seen in Figure 1, in three case studies.
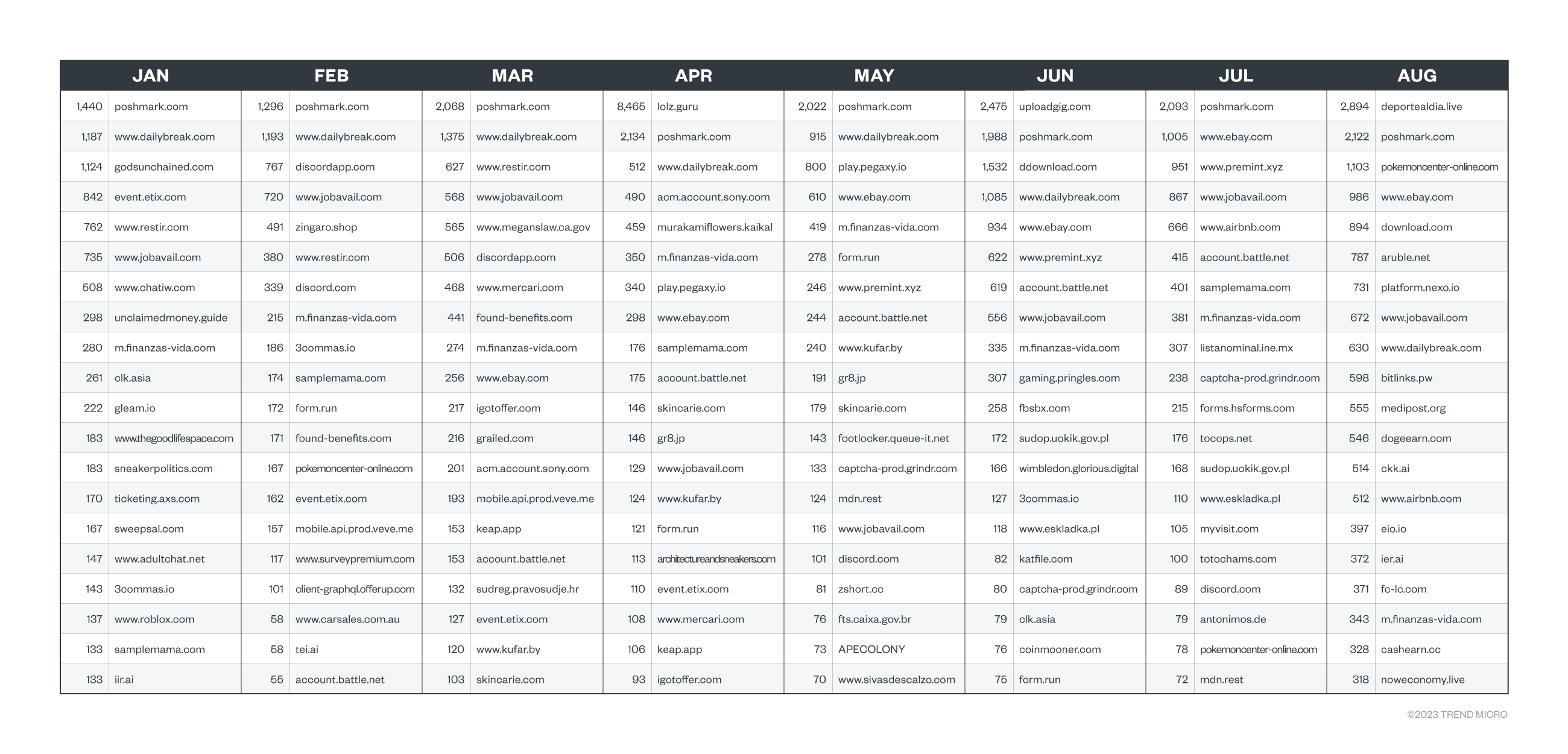
Case study 1: Poshmark
Poshmark is a popular social commerce marketplace where users can buy and sell various fashion, home, and electronics items. It integrates the use of social media to promote social interaction with users, eventually driving users to buy from the platform.
Sellers who are proficient in promoting their Poshmark stores can expect to earn good money, which can range from a few hundred dollars to more than US$1,000 per month. Poshmark sellers, also known as “Poshers,” can use a plethora of tools to promote their storefronts to prospective shoppers. These tools automate a lot of promotional tasks in Poshmark, such as sharing storefronts, sharing listings, and reciprocating shares and follows. Notably, these automated bot activities trigger Poshmark's antiabuse safeguards, which result in CAPTCHAs being presented.
One of the most notable features of these Poshmark bots is, of course, solving CAPTCHAs. These bots need to have CAPTCHA-breaking capabilities built-in, otherwise, their automated Poshmark promotional tasks would be quite limited. There are even websites that review the capabilities of the various Poshmark bots and rank them according to their feature sets.
Our observations show that there are numerous CAPTCHA-solving task requests to a known CAPTCHA-breaking service that are targeting CAPTCHAs from Poshmark's website. From the data we’ve gathered, these CAPTCHA-solving requests originated from a known Poshmark bot.
What is more interesting is that these CAPTCHA-solving requests are routed via a proxyware network. In addition to breaking CAPTCHAs via automation, Poshmark bot operators also use proxyware utilities to further obfuscate their originating IPs — an additional step to help them evade antispam measures.
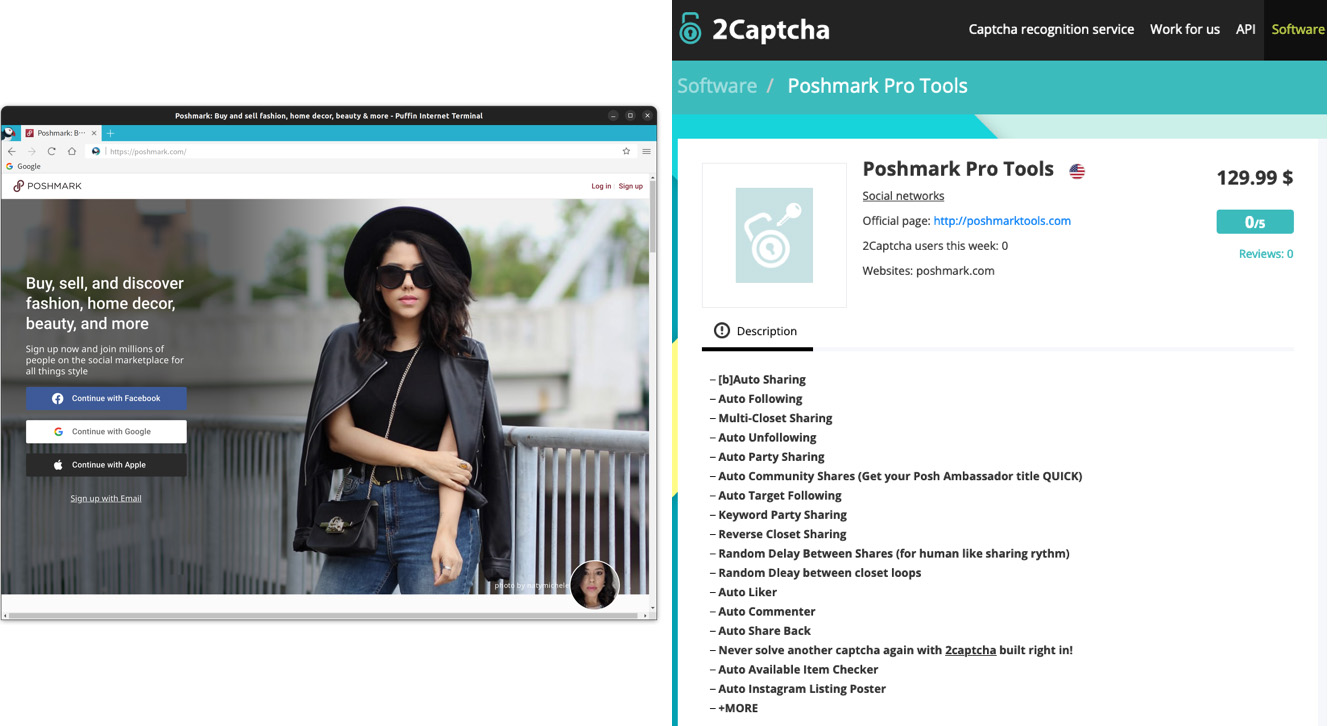
In this case, the abusers used “Poshmark Pro Tools,” an advertisement tool that Poshmark blocks. For a certain fee, this tool can be used to promote clothes, shoes, or accessories in users’ Poshmark timelines and increase the likelihood of Poshers bidding on them. To block such automated promotion tools, Poshmark uses reCAPTCHA to ensure that people, and not bots, are promoting their items. Poshmark Pro Tools uses the 2Captcha CAPTCHA-solving service to break reCAPTCHA and mask bot activity.
Case study 2: Murakami.Flowers NFT
Murakami.Flowers is a set of non-fungible tokens (NFTs) issued by a popular artist named Takashi Murakami. This NFT sale, which happened in April 2022 to preregistered users, was unique because of the popularity of the artist, and the relative rarity of the NFT collection.
To make it as fair as possible for prospective buyers to purchase Mukramami.Flowers NFTs, the organizers established the following guidelines:
1. NFT collectors must register their email address on the Murakami.Flowers website.
2. After registration, the NFT collectors will each get an email which contains a link to a website where they can register their wallets and usernames.
3. This wallet and username registration will now serve as the NFT collector's raffle entry into a lottery that aims to give all NFT collectors a fair chance to mint or buy Murakami.Flowers NFTs.
After the NFT's public mint, the NFTs will also become available to the secondary market.
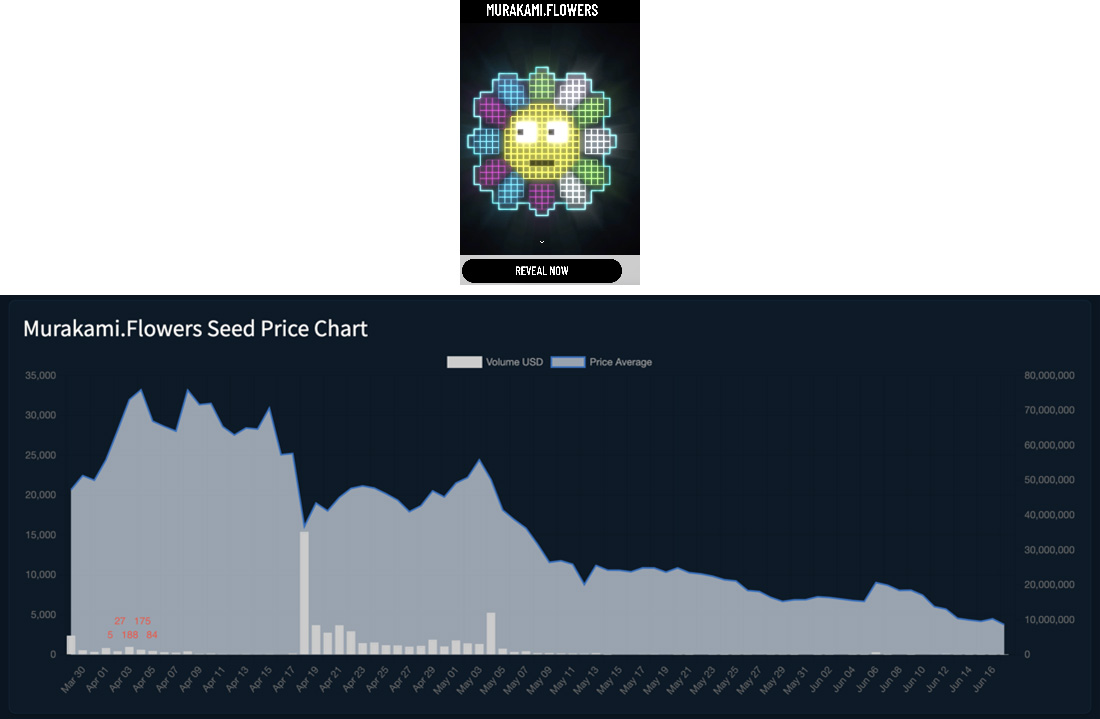
Even before the lottery began, we observed numerous CAPTCHA-breaking activities (which can be seen as red numbers on Figure 3), which primarily targeted the Murakami.Flowers email registration site. Moreover, like in Poshmark's case, these CAPTCHA-breaking activities were observed to have used the same CAPTCHA-breaking service. And like in Poshmark's case, these CAPTCHA-breaking activities were also observed to have used proxyware utilities to mask the perpetrators’ originating IP addresses.
It should be noted that we were not able to identify the abusers of Murakami.Flowers. However, we believe that the abusers wanted to register and participate in the lucky draw to become eligible to purchase the NFTs at a lower price (0.108 Ethereum). It’s possible that the abusers were looking into reselling the NFTs, which have previously sold up to 5 Ethereum, to make as much as 50 times more profit.
Case study 3: Maximizing earnings from crypto faucets
Crypto faucets are apps or websites that give small cryptocurrency rewards in exchange for completing simple tasks. These can be simple, straightforward tasks, such as reading articles, watching videos, watching ads, playing games, or completing quizzes. It should be noted, though, that these tasks can be risky at times, especially when users are asked to select links and ads, or even solve CAPTCHAs.
To maximize the amount of profit earned from crypto faucets, some actors attempt to automate the completion of crypto faucet-related tasks by using bots that are available in the market. However, crypto faucet websites typically implement antispam measures to curtail bot-like behavior, such as integrating CAPTCHA challenges on their websites. This is where CAPTCHA-breaking services come in.
We have observed CAPTCHA breaking activities that target CAPTCHAs in known crypto faucet websites. The observed CAPTCHA-breaking web traffic primarily targets login pages, where most CAPTCHA challenges typically reside. Moreover, the observed web traffic suggests the use of bots, due to the frequency and characteristics of the web traffic.
Conclusion
CAPTCHAs are common tools used to prevent spam and bot abuse, but the increasing use of CAPTCHA-breaking services has made CAPTCHAs less effective. While online web services can block abusers' originating IPs, the rise of proxyware adoption renders this method as toothless as CAPTCHAs.
It is therefore imperative for online web services to use other antiabuse tools in addition to using CAPTCHAs and blocking originating IPs. Though these tools are still working as designed, cybercriminals can easily purchase paid services that are specifically made to beat CAPTCHAs. As these services become more affordable over time, it becomes more worthwhile for malicious actors to abuse them. It is time to supplement CAPTCHAs and IP blocking with more robust security measures. We will provide detailed information about the specific security measures in an upcoming report.

