In this post, we introduce the latest research conducted jointly by Trend Micro and Politecnico di Milano (POLIMI) in the Industry 4.0 Lab. (For more information about POLIMI and the Industry 4.0 Lab, see our previous blog post.) The title of this joint research is "Attacks on Smart Manufacturing Systems: A Forward-looking Security Analysis." In this research, by using a smart manufacturing system installed at the Industry 4.0 Lab, which is sophisticated enough to produce actual products, we sought to answer one primary question: Under which threat conditions and attacker's capabilities are certain attacks possible, and what are the consequences?

<Photo 1> Federico Maggi, Senior Threat Researcher with Trend Micro, leading this research project, together with Marco Balduzzi, also Senior Researcher with Trend Micro, and Marcello Pogliani, Davide Quarta, and Stefano Zanero from Politecnico di Milano.
Hindering the potential negative impact of associated risks
Every factory has two ultimate aims: "increasing productivity" and "reducing the defect rate." Smart manufacturing refers to the use of technology and IT-OT integration to increase productivity and reduce the defect rate - or even better, to measure and control them. More technically, it is an effort to achieve a high level of automation of production processes and managements through software-defined control, network connection, and data analysis. With the progress of digitalization, factories around the world are starting to become smarter.
However, the potential security risks associated with this new technology may delay its widespread adoption. As ENISA points out in their paper, Industry 4.0 operators, which are at various stages of Industry 4.0 adoption, often do not have appropriate governance structures in place for secure implementation of new technologies and secure maintenance of the existing ones." In some realities, cybersecurity is not given enough priority as a corporate strategy, often because of the unclear return on investment. As a result, cybersecurity is prioritized only when a security breach directly leads to financial losses - even if, in most cases, it is already too late.
Building a REAL smart manufacturing system
To see is to believe. That's why Trend Micro and POLIMI have conducted investments in building physical environments to develop proof-of-concept experiments. The best way to determine whether your company needs cybersecurity is to see what happens when a realistic smart manufacturing environment suffers a cyberattack. The following is an overview of the system used for the demonstration experiment.
This smart manufacturing plant'ss main job is to produce and assemble toy mobile phones. This system is made of stations, each of which is comprised of at least three parts:
- a physical machine, such as a loader, driller, press, camera, or industrial robot;

- an HMI that lets the operator monitor and control the progress;

- a PLC, which serves as the interface between the machine, the HMI, and the rest of the network.

Further, the overall production process is coordinated by a manufacturing execution system (MES), which is essentially a logic and control layer on top of a database. Figure 1 below shows the overall architecture of the system.
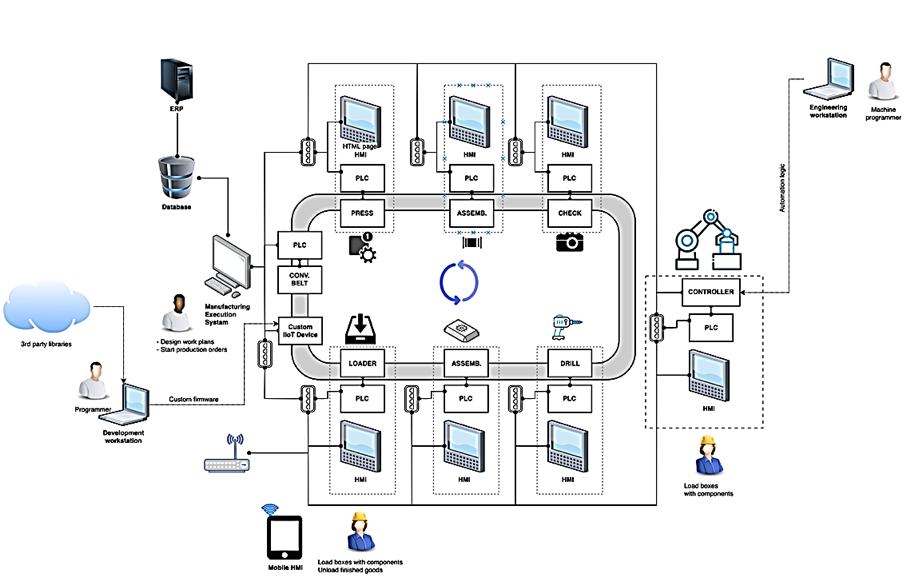
<Figure 1> Overall architecture of the smart manufacturing system used in our research.
Cyberattacks can impact the products
In this research, Trend Micro and POLIMI targeted five smart manufacturing components. All are common components that play important roles in factory environments. The five targets are:
- The MES, which is highly critical for a smart manufacturing system because it is the gateway between high-level manufacturing scheduling (e.g., ERP) and the actual manufacturing floor where goods are actually produced.
- Programmable manufacturing machines, which execute their manufacturing tasks according to a task program, such as industrial robots.
- Mobile HMIs, which are becoming more common because of their flexibility and ease due to being able to beof installed on tablets or smartphones.
- Industrial programming software, which is as extensive asany other complex software, and similarly attackable; and
- Custom industrial IoT devices, which are often used for both prototyping and production.
This research shows that attacks against - or through - these devices can negatively impact both the production process and the product itself. For example, by manipulating the MES database we injected product defects (Photo 2). This is like a butterfly effect in the factory: a tiny digital change can cause disruptive physical outcomes.

<Photo 2> The driller unexpectedly drills on the left side because the attack changed the value of the parameter associated with the operation.
Examining the root cause of this simple proof-of-concept example reveals larger concerns: factory networks have traditionally been isolated from other networks, with components like databases, MES, PLCs, HMIs, and so forth blindly trusting each other. Through practical proof-of-concept examples such as this one, our research will help you identify where and how you should implement security measures in your smart factories.
On May 11, Trend Micro will release the complete white paper, which includes more detailed information about threat conditions, attackers' capabilities, and the consequences of each of the five attacks that we tested.

