Online banks use cryptographic protocols to secure the exchange of information on the Web, and hackers do not hesitate to adapt to this technology too. A new case of fake SSL (Secure Sockets Layer) certificates appeared again, following phishing threats we've seen last April and May (see our blog posts about fake digital certificates, rock phishing, and a similar attack on Merrill Lynch). This time, the website of Open Banks Enterprises was faked by malware authors using Rock Phish Kit. The spoofed website, shown in the following screenshot, displays multiple banks that are included in the open bank community:
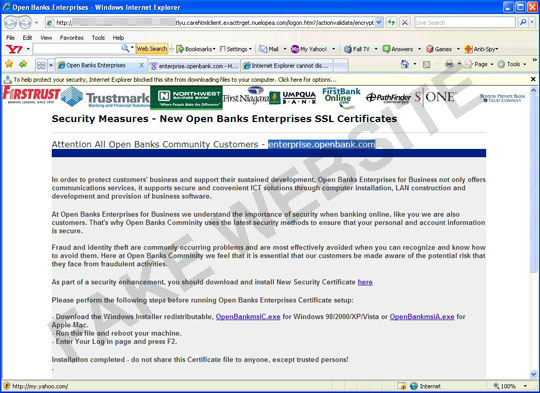
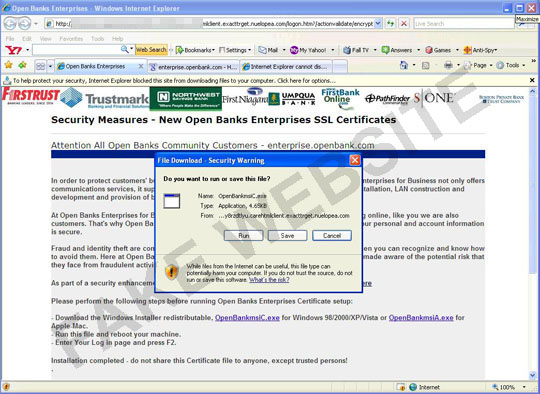
Like similar phishing or malware cases, this spoofed site asks customers to download a new security certificate. The site even displays options for Windows users and Mac users, but users are led to .EXE files, which perform malicious routines on systems, compromising their security instead of securing online transactions like security certificates are supposed to do.
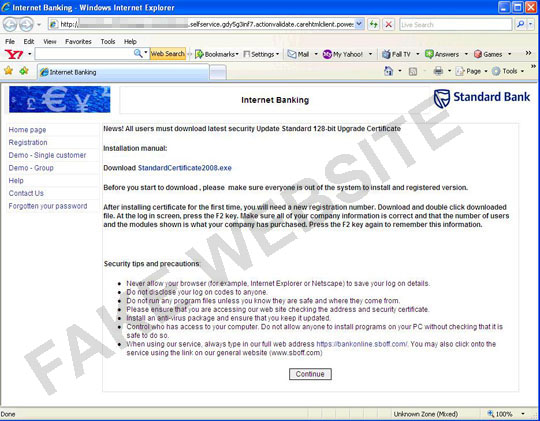
Yet another certificate attack also surfaced this day, this time involving Standard Bank. The spoofed page (also with a Rock Phish URL) asked users to download a 128-bit upgrade certificate. The .EXE file being downloaded is also malicious.
Trend Micro detects the two downloaded files as TROJ_SMALL.MJZ and TROJ_AGENT.ARNU, respectively. TROJ_SMALL.MJZ downloads a spyware detected as TSPY_PAPRAS.AR. TROJ_AGENT.ARNU meanwhile downloads Possible_Crypt, a malware that displays behavior similar to those that change DNS directories. The malicious domains are now blocked by the Trend Micro Smart Protection Network. The technology also detects the malicious executables at the desktop level and provides solutions for their removal.

