Check for Amazon Inspector Findings and resolve them step by step to ensure that your systems are configured securely. Amazon Inspector is an AWS service that helps improve the security and compliance of your AWS resources. Amazon Inspector Findings are potential security issues found during the service evaluation of the selected resources (also known as Amazon Inspector assessment targets).
This rule can help you with the following compliance standards:
- APRA
- MAS
For further details on compliance standards supported by Conformity, see here.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
With Amazon Inspector Findings you can evaluate your operating system environments and applications deployed on AWS for potential security issues and common vulnerabilities in an automated way.
Note 1: As of April 2017, the Amazon Inspector assessment targets can consist only of EC2 instances that run on certain Linux-based and Windows-based operating systems.
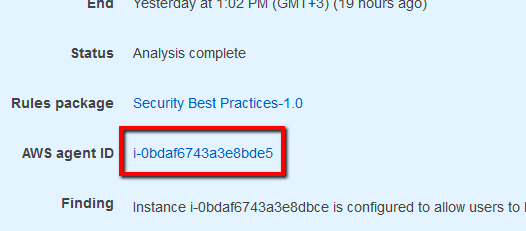
Note 2: As example, this conformity rule will demonstrate how to analyze and solve a finding (security vulnerability) generated automatically by Amazon Inspector after evaluating a group of EC2 instances (Amazon Inspector assessment target).
Note 3: This rule only generates checks based on the findings of the latest assessment run associated with an assessment template
Audit
To check for Amazon Inspector Findings within your AWS account, perform the following:
Remediation / Resolution
To solve any Amazon Inspector Findings discovered for your EC2 resources provisioned within your AWS account, perform the following:
Note: As example, this rule will provide step by step instructions on how to configure your EC2 instances running on a Linux-based OS distribution to prevent root account logins over SSH.References
- AWS Documentation
- Amazon Inspector
- Amazon Inspector FAQs
- Amazon Inspector Findings
- Amazon Inspector Assessment Targets
- Amazon Inspector Service Limits
- AWS Agents
- Working with AWS Agents on Linux-based Operating Systems
- Working with AWS Agents on Windows-based Operating Systems
- Security Best Practices
- Connecting to Your Linux Instance from Windows Using PuTTY
- AWS Command Line Interface (CLI) Documentation
- inspector
- list-findings
- describe-findings
- ec2
- describe-instances