Ensure that encryption at rest is enabled for your Amazon Glue Data Catalogs in order to meet regulatory requirements and prevent unauthorized users from getting access to sensitive data. With this feature enabled, you can encrypt AWS Glue Data Catalog objects such as databases, tables, partitions, connections and user-defined functions and also encrypt connection passwords that you provide when you create data connections. Amazon Glue is a fully managed ETL (Extract, Transform and Load) service that makes it simple and cost-effective to prepare and load your data for analytics. Glue consists of a central metadata repository known as the AWS Glue Data Catalog, an ETL engine that generates Python/Scala code and a scheduler that handles dependency resolution, job monitoring and retries.
This rule can help you with the following compliance standards:
- HIPAA
- GDPR
- APRA
- MAS
- NIST4
For further details on compliance standards supported by Conformity, see here.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
When your Amazon Glue metadata repository (i.e. AWS Glue Data Catalog) is working with sensitive or private data, it is strongly recommended to implement encryption in order to protect this data from unapproved access and fulfill any compliance requirements defined within your organization for data-at-rest encryption.
Audit
To determine if your AWS Glue Data Catalogs are using encryption at rest, perform the following actions:
Remediation / Resolution
To enable encryption at rest for Amazon Glue Data Catalog objects and connection passwords, perform the following actions:
References
- AWS Documentation
- AWS Glue
- AWS Glue FAQs
- What Is AWS Glue?
- Encryption and Secure Access for AWS Glue
- Encrypting Your Data Catalog
- Setting Up Encryption in AWS Glue
- AWS Command Line Interface (CLI) Documentation
- glue
- get-data-catalog-encryption-settings
- put-data-catalog-encryption-settings

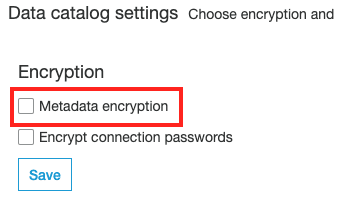 , data-at-rest encryption is not enabled for your Amazon Glue Data Catalog available within the selected AWS region.
, data-at-rest encryption is not enabled for your Amazon Glue Data Catalog available within the selected AWS region.