Dark Motives Online: An Analysis of Overlapping Technologies Used by Cybercriminals and Terrorist Organizations

Cybercriminal activities have always involved the abuse of legitimate online tools and services. Examples of these activities come in many forms and can be found everywhere—from using vulnerabilities in software, websites, and web applications as attack vectors, hosting malicious components in cloud services, to leveraging clickbait posts and links on social networking sites to lure hapless users into falling for their schemes. No matter what technology or service rolls out in the future, there will always be room for abuse.
During the course of our research on cybercrime, we found that one particular group appears to share the same level of proficiency as cybercriminals in abusing legitimate services: terrorist groups who can be considered as cybercriminals in their own right, as their online activities also run afoul of the law. The two groups have different motives though, as cybercriminals are motivated by financial gain, while terrorists aim to spread propaganda instead of malware.
This research is about how cybercriminals and terrorists overlap in their abuse of technology and online platforms to benefit their cause. We will focus on their methodologies, the services they abuse, and the tools they’ve homebrewed to streamline said abuse so that their followers can facilitate their activities much more easily.
Aiming for Anonymity
Due to the obviously illegal nature of their goals, cybercriminals and terrorists share the need to remain untraceable and anonymous online. Both groups are known to abuse tools and services that have been developed to help those who have a legitimate reason to hide their identities (such as journalists, whistleblowers, and activists). Some examples of these tools include anonymizing programs such as TOR, and certain encryption tools found in the Deep Web.
Another example of a web service we saw being abused by terrorists is the DDoS 1 mitigation service, Cloudflare. A legitimate service designed to provide a working mirror for websites that are either experiencing heavy traffic or being subjected to denial of service attacks, Cloudflare is abused to hide the real hosted IP address of the website. We’ve seen this used time and again by cybercriminals looking to distract or delay authorities from being able to track the location of their hosted servers. We found that terrorists have also begun to adopt Cloudflare to give propaganda websites another level of anonymity.
Besides this, we’ve also spotted terrorists adopting and distributing ‘anonymizing’ guides. Originally meant for activists and journalists, these guides are being distributed to their followers, evidently to teach new or uninitiated members ways to avoid being spied on. Some of these guides even mention the National Security Agency and how to avoid surveillance:
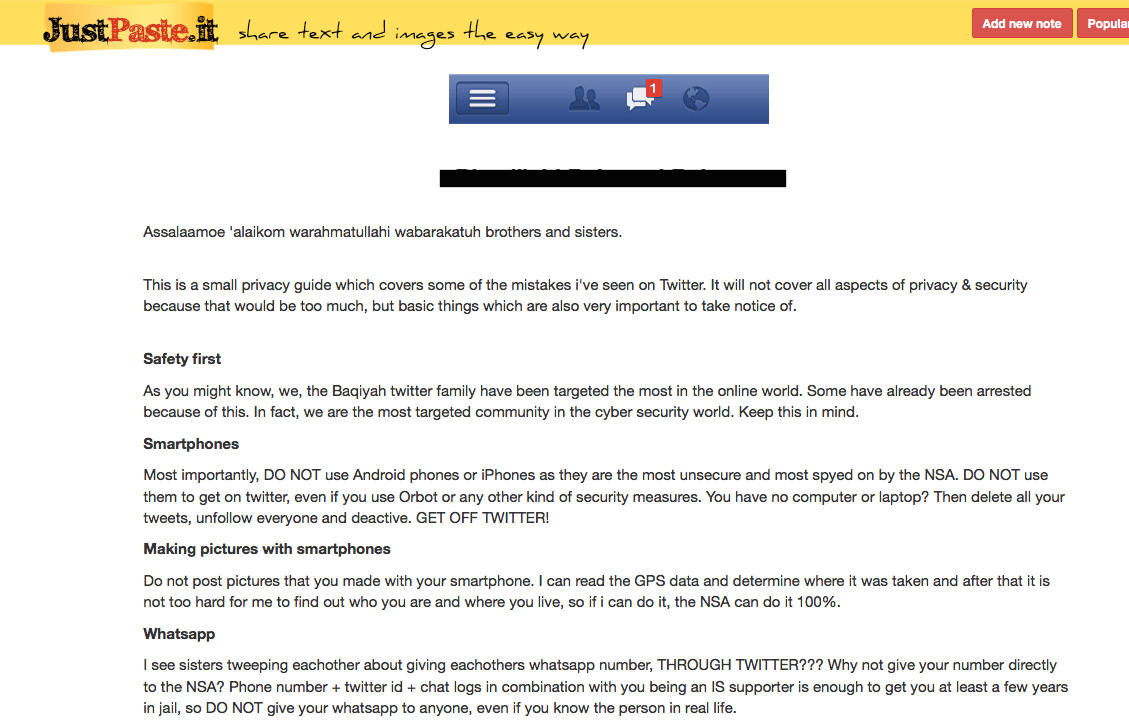
It even goes as far as scolding the reader to deactivate their social media accounts to maintain anonymity. The difference in strategies terrorist groups and common cybercriminals apply to remain anonymous is another example of the contrast between the two parties and their distinct goals. One assumption we can make here is that the consequences of being caught are different for the two groups: cybercriminals only need to worry about jail time, while terrorists would have to contend with counter-terrorism efforts, which may ultimately lead to lengthy prison sentences or death.
Communication Methods
Terrorists and cybercriminals share common communication methods. Here are some of the methods that cybercriminals from all over the world use, based on the Trend Micro research, The Many Faces of Cybercrime:
- Secure e-mail services: Japanese cybercriminals in particular use services such as “SAFe-mail” to contact and barter with each other through secure, undetectable email.
- Deep web/underground forums: Nearly all the regional cybercriminal underground communities we observed involved the use of underground forum—not only to advertise their wares and services, but also to discuss new techniques, share information, and banter. These forums are usually accessible only through TOR, with some requiring certain checks to enter.
- Social media (Twitter, Facebook): Brazilian cybercriminals used social media to stay in contact with each other but also to brag about their earnings from their activities.
We see terrorists utilize these same methods, but for different purposes—their use of the methods above focuses more on communication, coordination and propaganda-sharing (especially with social media) as opposed to price-haggling/cybercrime-related abuse. Secure email services are heavily used by terrorists, with services such as SIGAINT, Ruggedinbox, and Mail2Tor being highly recommended among their ilk.
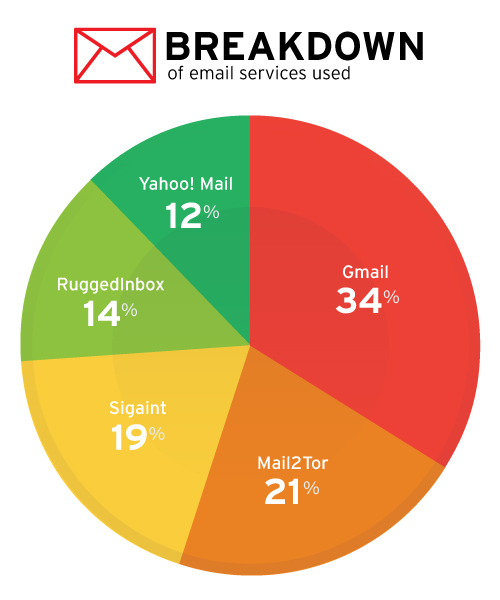
Instant messaging is also another method of communication that cybercriminals and terrorists have in common, but used more for communication and coordination rather than for information theft or to spread malicious links. We studied 2,301 accounts that openly support terrorist groups and found that instant messaging service Telegram is the most favored among terrorists, with 34% listing their contact information as a Telegram address. Wickr, Surespot, Signal, and Threema accounted for the rest, along with Whatsapp and other messaging apps. WhatsApp previously saw much more use than the 15% we saw of it today—the reduced use may have stemmed from recent terrorist arrests made through their use of the messaging app.
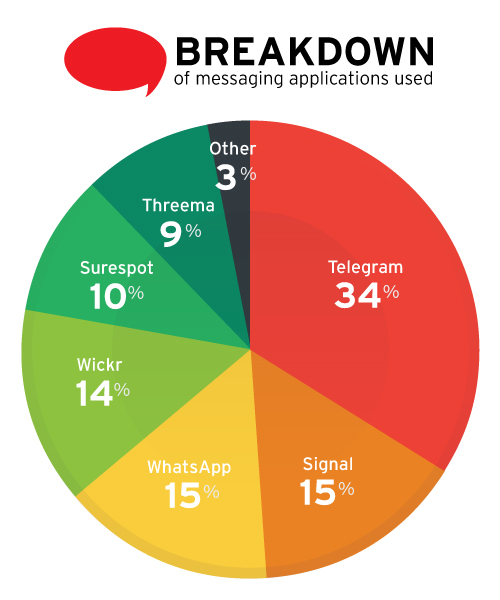
Cybercriminals and terrorists also share the use of file hosting and sharing services. These services are mostly used by terrorists to send and spread propaganda and large digital media. Examples of such services used in this fashion include top4top.net, Sendspace, and SecureDrop. Something we must note here is an ongoing trend of terrorist groups preferring file-hosting services based in regions such as the Middle East—presumably another response to the perceived threat of government surveillance plaguing communications platforms in western countries such as the US.
Finally, we end this section with a note on a communications platform that is unique to terrorist operations—mobile phones. This bears mentioning due to the fact that, unlike cybercriminals whose activities are usually confined to cyberspace, terrorist groups mostly operate in the real world and use digital means to communicate. But instead of this particular means of communication gaining traction, many underground terrorist forums recommend staying off smartphones because of their lack of security. The two most popular mobile platforms (iOS and Android) are considered undesirable in the forums.
Propaganda Dissemination
One of the clearest differences between cybercriminals and terrorists is their desire to spread propaganda. While cybercriminals’ main goals are to commit cybercrime and stay hidden while they do it, terrorists aim to have their content go viral. While cybercriminals’ main goals are to commit cybercrime (the unlawful electronic theft of funds) and stay hidden while they do it, terrorists aim to have their content go viral, to be seen and consumed not only by their followers but also by a wider public audience. At the same time, terrorist groups also try their best not to be banned or censored from the channels they use to spread their propaganda, or to have their real-life identities traced and detected while doing it.
How do they broadcast their propaganda?
- Websites. Terrorist groups use websites on both the open and dark web to host propaganda and related material such as news articles, publications, documents and other media such as videos and images.
- Social media. Terrorists and their supporters use Twitter and Facebook not only to spread propaganda but also to communicate with each other and potential converts. Notably, Twitter started cracking down on accounts that openly support and spread terrorist propaganda by banning those accounts outright. This has forced the banned account holders to start from scratch.
- Media: Videos, photos and promotional material that depict the terrorist groups in a positive light, packaged and produced in professional quality so as to grab the attention of as many viewers as possible. These may also come in the form of advertisements that highlight the group’s victories. They may even be used to ‘sell’ hostages.
- Physical storage media. Terrorist groups have also been found distributing propaganda and other information through the distribution of seeded SIM cards and USB drives as an off-the-grid option. This allows them to continue spreading their ideology without fearing detection or surveillance.
Customized Terrorist Tools
From establishing the similarities and differences in the technologies and communication methods that cybercriminals and terrorists have, we now move onto the technologies that are specific to the latter group. We have uncovered certain applications that have been homebrewed by terrorist groups to aid members who aren't as technically proficient into preserving their anonymities and securing their lines of communication. These are the six most popular and commonly-used ones, based on our observations online.
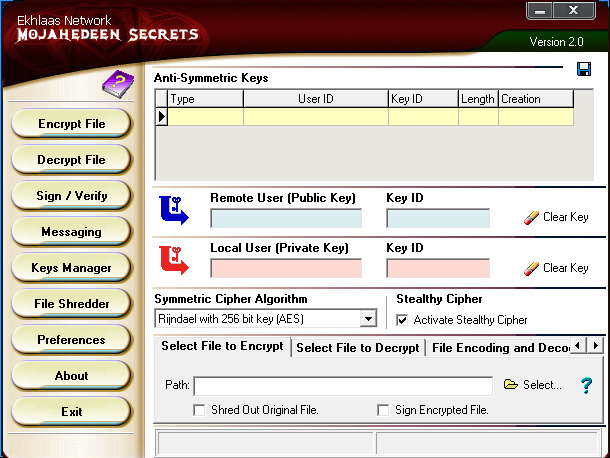
- Mojahedeen Secrets: Released in 2007 as an alternative to PGP 2, Mojahedeen Secrets is considered to be the first “professionally” developed encryption application for email. This application encrypts email and file transfers using RSA public/private encryption systems. In addition to allowing users to create private keys to use when sending emails, the application also supports messaging and a file shredder feature to delete files safely.
- Tashfeer al-Jawwal: Considered one of the first encryption applications for mobile, this app was developed by the Global Islamic Media Front (GIMF) and released in 2013. The application itself acts as a mobile encryption program.
- Asrar al-Dardashah: Released in 2013, this plugin was developed for the instant messaging application Pidgin.Easily installed, this plugin adds encryption to the instant messaging functions, securing instant messaging with the press of a single button.
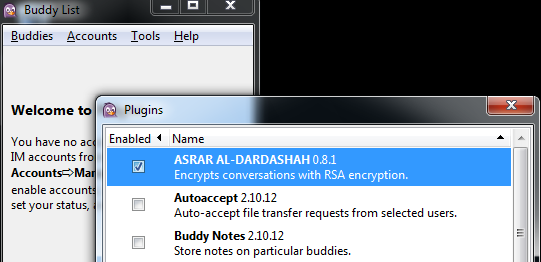
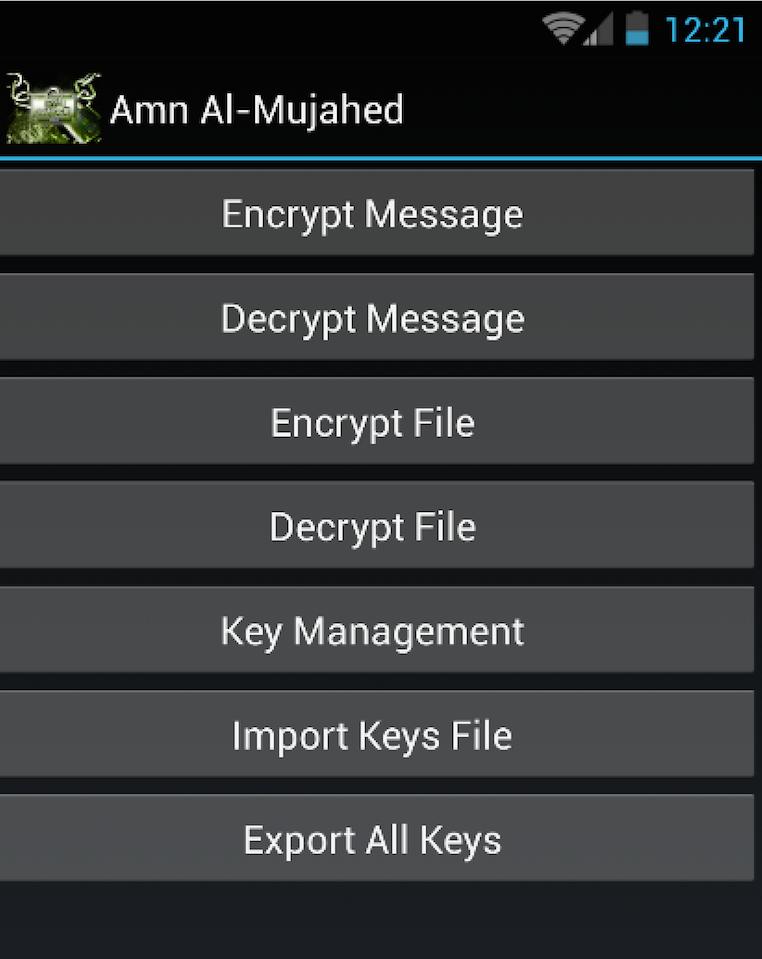
- Amn al-Mujahed: an encryption software program developed by Al-Fajr Technical Committee (ATC). Released in 2013, this software currently in version 1.1 and is still actively being developed. It encrypts messages for use with multiple messaging platforms, such as email, SMS, and instant-messaging.
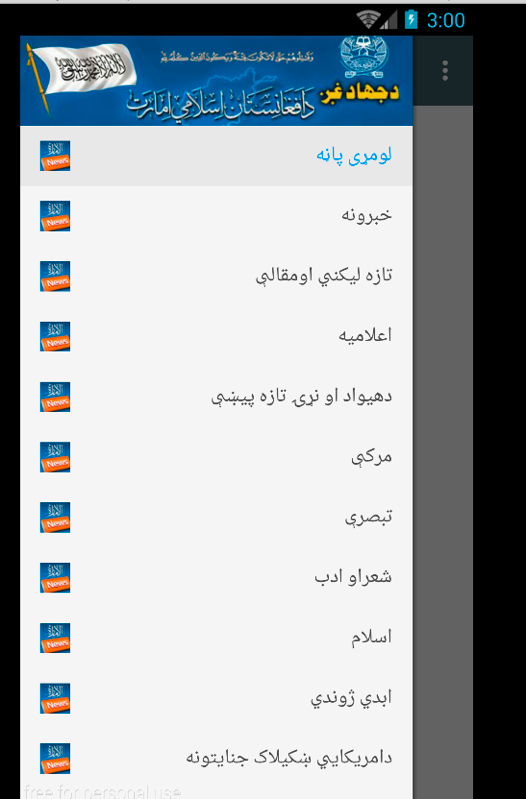
- Alemarah: This new Android application serves as a news distributor for terrorist-related actions. It lists news feeds, websites, and calendars that contain information related to ongoing operations.
- Amaq v 1.1: Amaq is an Android application known to be used by terrorist organizations to disseminate information. The widely-distributed app has gone through multiple versions. Its latest version, Amaq 2.1 uses a configuration file that allows the app’s distributor to easily change the URL where the app is hosted should any of their websites get taken down—a technique also used by cybercriminals in managing their malware URL.
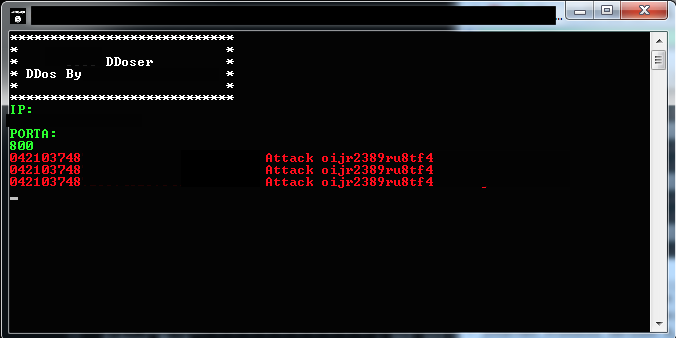
- DDOS Tool: During the course of our investigation of tools utilized by terrorist organizations, we also came across one that claims to be a DDOS tool created by an individual who appears to be a sympathizer of a certain terrorist organization. It was initially thought to be a fake application that was unlikely to cause anything. However, tests confirmed that it was capable of performing limited denial of service attacks through the common SYN flood technique. While this application is not particularly advanced, it shows that there is active exploration into disruptive technology.
Conclusion
In being able to gain a level of visibility on the online activities of both terrorists and cybercriminals, we see a lot of differences and similarities in their techniques and methods. While both groups are particularly keen on keeping their anonymity online, the way they disseminate information related to their agenda is quite different. We see that cybercriminals are more inclined to engage with limited contacts, and put weight on individuals’ online reputation. Terrorist organizations, on the other hand, focus their efforts on getting their propaganda out to a wider audience, in the hopes of finding potential sympathizers.
Motivations aside, there are a lot of overlaps regarding the online presence of terrorist organizations and cybercriminals. They both communicate through the same channels and use the same technologies, making the task of tracking terrorists as challenging as it is to track cybercriminals, if not more. Knowing the channels and technologies they use, however, is a critical first step towards getting a better understanding of how these groups function, which can ultimately help provide ways to stop their activities.
Research Notes:
On the definition of terrorist
For the purpose of this research, a minimum number of seven nation states must call the specific group “terrorists” or “terrorist organizations” for us to use the data in this paper. Seven countries designating a particular organization as a “terrorist organization” allowed us to focus on truly international groups that weren't just labeled as such because of regional political views or prejudices. Seven countries agreeing upon the labeling of a specific group involve a truly global consensus, setting aside political differences and ideals.
On terrorist supporters
The individuals and organizations studied as part of this research include those who are actively supporting terrorist organizations and/or are providing material support to these organizations. These include:
- An individual or group who readily and outwardly identifies themselves as a member of terrorist organizations defined by at least seven nation states.
- An individual or group who readily and widely distributes newsletters, publications, or video material in direct support of terrorist organizations.
On technical details and sample information
We obfuscated any mention of a terrorist or terrorist organization in this research, so as to focus on the core message—the technology they use. The technologies defined in this research are current methods and applications found to be currently in use by identified terrorists and terrorist organizations. We will not cover new technology or technology that has yet to be used by the organizations.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks Today’s Cloud and Container Misconfigurations Are Tomorrow’s Critical Vulnerabilities
Today’s Cloud and Container Misconfigurations Are Tomorrow’s Critical Vulnerabilities Ransomware Spotlight: INC
Ransomware Spotlight: INC The Realities of Quantum Machine Learning
The Realities of Quantum Machine Learning