RANSOM_SHOR7CUT.A
Ransom:PHP/SchRansom.A (Microsoft)
Windows


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
Downloaded from the Internet
This ransomware purportedly targets web servers. Once it finds its target, it encrypts files in the web server. It has the option to encrypt or decrypt files.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.

This Trojan may be hosted on a website and run when a user accesses the said website.
TECHNICAL DETAILS
6,062 bytes
Script
No
20 Oct 2016
Encrypts files, Displays message/message boxes
Arrival Details
This Trojan may be hosted on a website and run when a user accesses the said website.
Other Details
This Trojan does the following:
- Encrypts files within the web server directory entered by a malicious user.
- It has the option to encrypt or decrypt the files
- When save mode is triggered, the current running script is deleted
- It exclude the files with the following strings in their filenames:
- .png
- .svg
- .woff
- .jpg
- .htaccess
- lol.php
NOTES:
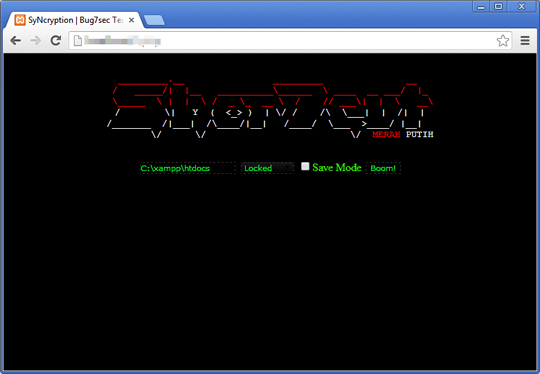
This ransomware displays the following user interface when accessed:
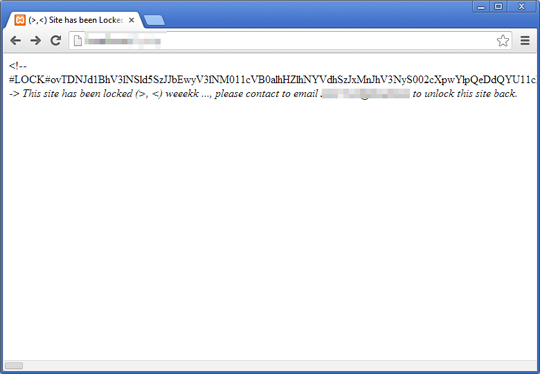
It displays the following when encrypted files are accessed:
SOLUTION
9.800
12.848.04
20 Oct 2016
12.849.00
21 Oct 2016
Scan your computer with your Trend Micro product to delete files detected as RANSOM_SHOR7CUT.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.

