Ransomware as a Service Offered in the Deep Web: What This Means for Enterprises
 View guide: Ransomware as a Service
View guide: Ransomware as a Service
Trend Micro threat response engineer Pacag talked about how a new breed of ransomware called “Stampado,” for which a “lifetime license” was being sold in the Deep Web for US$39, a couple of weeks back. This is exactly how ransomware as a service (RaaS) works—do-it-yourself (DIY) kits are sold in forums, making it incredibly easy even for nontechnical people to mount a ransomware operation of their own.
Ransomware has continuously made headlines in recent months because of the threat’s staggering effectiveness. Users typically get infected by ransomware from browsing the Internet, opening spam, or simply using outdated software.
Once executed on a system, the ransomware starts encrypting files in the victim’s PC or server, then displays a message that demands payment (usually in Bitcoins) in exchange for a decrypt key that allows access to the encrypted files. In 2015, CryptoWall—just one ransomware strain among hundreds—raked in US$325 million from victims, possibly pure profit, given the low barrier to this criminal operation.
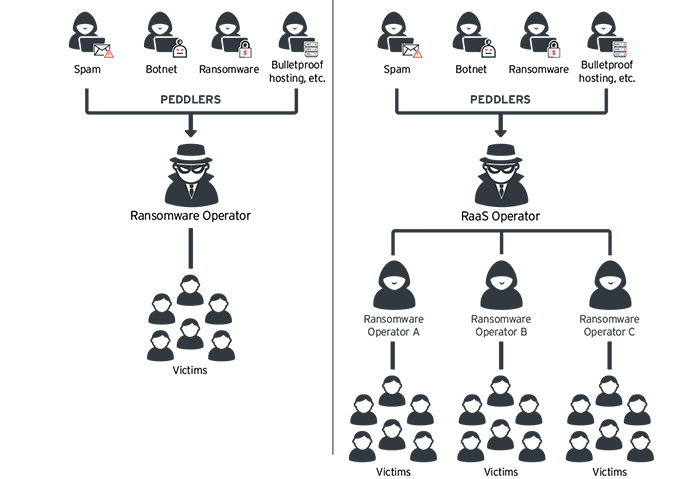 Typical ransomware operation versus RaaS
Typical ransomware operation versus RaaS
What this means for a company depends entirely on what type of data they're trying to protect. A ransomware operator hardly understands what a certain file means to the victim, but by mass-encrypting entire folders, drives, and servers, a cybercriminal can demand any amount of money from hordes of victims and still get away with profit even if only a few favorably respond.
But for an organization or business, ransomware can freeze operations or cut access to important company files. This can mean anything from lost sales, delays, or unfulfilled orders to massive productivity losses in an attempt to retrieve or recreate affected files. In either case, the company may suffer legal or regulatory penalties, brand damage, and loss of customer trust.
Ransomware has been so effective that it begs the question, “what can we do about this threat?” There is no silver bullet, unfortunately. IT administrators are expected to employ best practices against ransomware, including multilayered protection, data backup and recovery strategies, access control, timely patching, and employee education, without compromising business productivity. Security technologies must seamlessly work together to protect a network from ransomware.
View the attached guide on Ransomware as a Service to learn how it can affect businesses, as well as solutions that can be employed to protect networks against the ransomware threat.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 MQTT and M2M: Do You Know Who Owns Your Machine’s Data?
MQTT and M2M: Do You Know Who Owns Your Machine’s Data? Building Resilience: 2024 Security Predictions for the Cloud
Building Resilience: 2024 Security Predictions for the Cloud Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023
Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023 Mitigating the Threat of Sidecar Container Injection
Mitigating the Threat of Sidecar Container Injection