Indicators of compromise
Indicators of compromise (IOCs) serve as forensic evidence of potential intrusions on a host system or network. These artifacts enable information security (InfoSec) professionals and system administrators to detect intrusion attempts or other malicious activities. Security researchers use IOCs to better analyze a particular malware’s techniques and behaviors. IOCs also provides actionable threat intelligence that can be shared within the community to further improve an organization’s incident response and remediation strategies.
Some of these artifacts are found on event logs and timestamped entries in the system, as well as on its applications and services. InfoSec professionals and IT/system administrators also employ various tools that monitor IOCs to help mitigate, if not prevent, breaches or attacks.
Here are some indicators of compromise information security professionals and system administrators watch out for:
- Unusual traffic going in and out of the network
- Unknown files, applications, and processes in the system
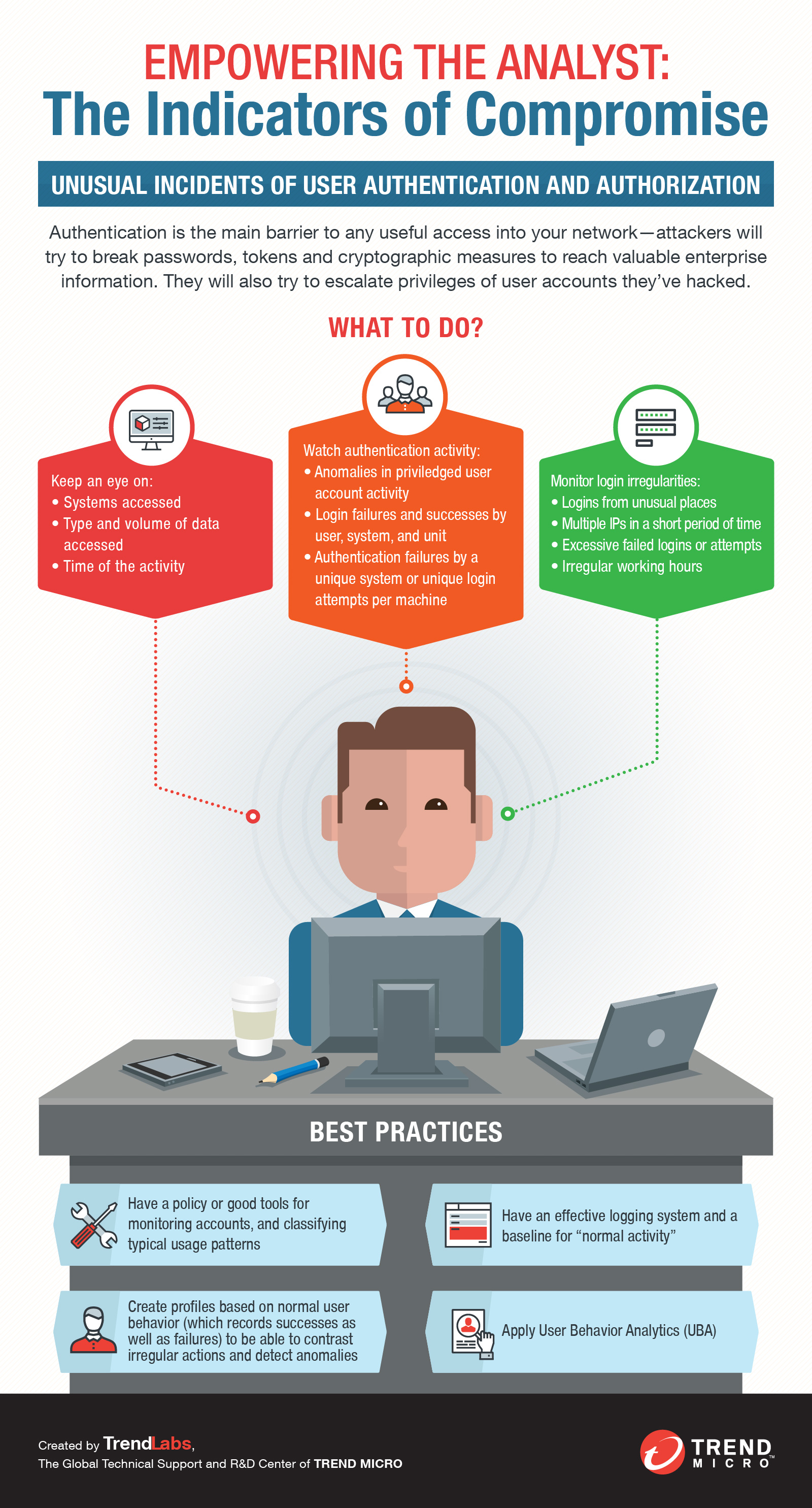
- Suspicious activity in administrator or privileged accounts
- Irregular activities such as traffic in countries an organization doesn’t do business with
- Dubious log-ins, access, and other network activities that indicate probing or brute force attacks
- Anomalous spikes of requests and read volume in company files
- Network traffic that traverses in unusually used ports
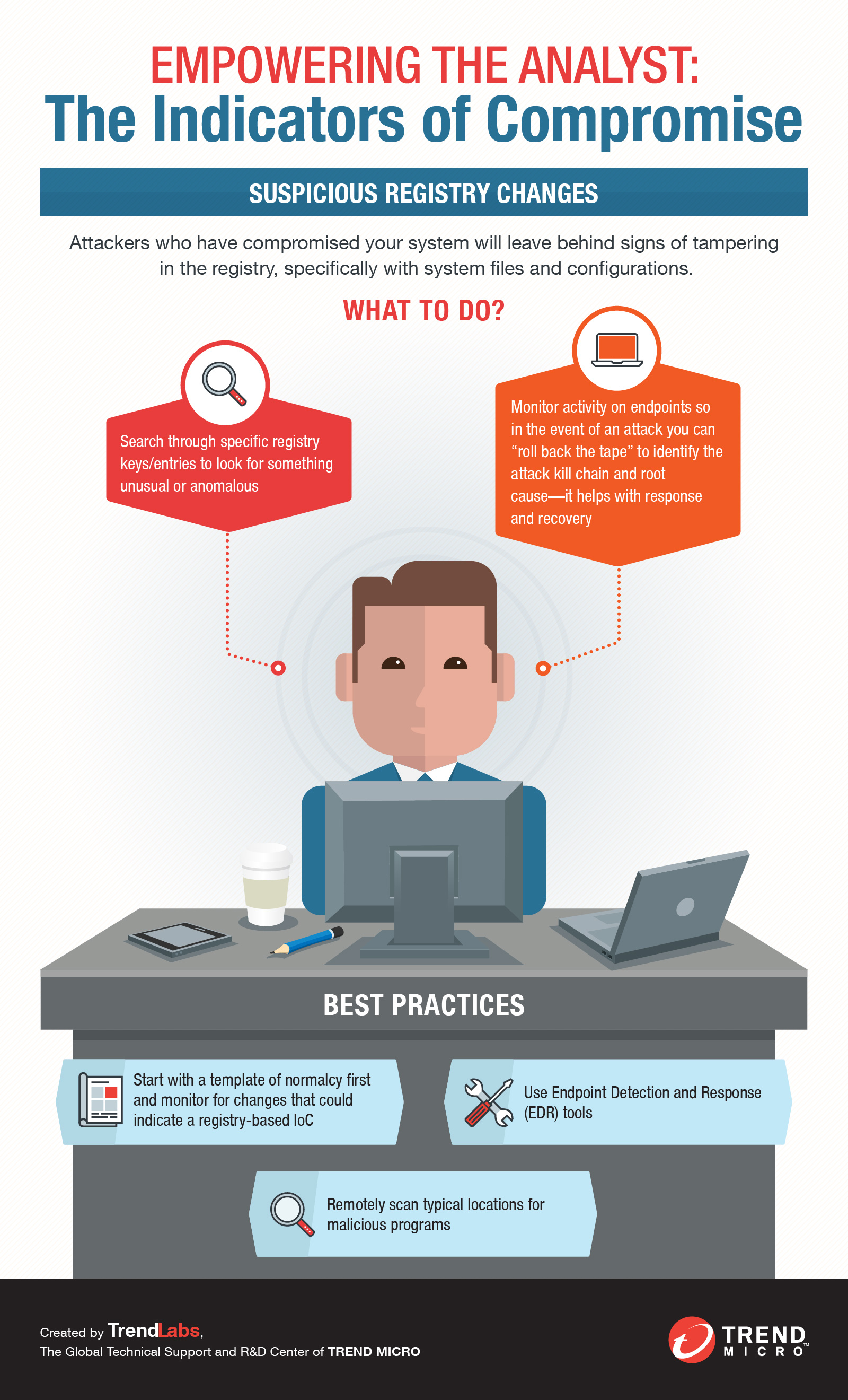
- Tampered file, Domain Name Servers (DNS) and registry configurations as well as changes in system settings, including those in mobile devices
- Large amounts of compressed files and data unexplainably found in locations where they shouldn’t be
Related terms: Targeted attacks, data breach
Related papers or primers :
https://www.trendmicro.com/vinfo/us/security/news/cyber-attacks/defending-against-data-breach-attacks
Related infographics :
https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/empowering-the-analyst-indicators-of-compromise
Graphics :