Safe communication, seamless collaboration
Understand, communicate, and mitigate risk
Gain real-time visibility into employee risk levels to proactively prevent user-targeted threats, prioritize and mitigate risk, identify vulnerabilities, monitor user behavior, and automate responses with AI-powered email security.
Gain flexible deployment and simplify compliance
Whether your email infrastructure is Microsoft 365®, Microsoft® Exchange Online, or Google Workspace™, deploy email security while meeting data privacy and security requirements across email and collaboration environments.
Streamline security operations and eliminate blind spots
Remove silos by centralizing visibility and management to streamline analysis, detection, risk prioritization and mitigation for effective security operations.
Run AI-powered protection
Fully integrated, robust defense against phishing and Business Email Compromise (BEC) to reduce remediation time bolstered by automated monitoring and response capabilities.
Identify anomalies in email
Safeguard sensitive data and financial assets with AI-driven techniques like writing style analysis, anomaly detection, and boosted trees, preventing irregularities and protecting personnel from email compromise and payment hijacking schemes.
Track malicious behaviors
Keep your inboxes secure with AI-powered email protection that detects suspicious language, analyzes sender behavior, and clusters similar messages. Enhanced with advanced language models and algorithms like SVM, Text CNN, and LLM, it accurately distinguishes legitimate emails from spam, executes macros, and blocks social engineering attacks and malicious downloads.

Detect phishing intentions
AI-driven analysis detects threats and assigns email scores. Using linear ranking models like token-based N-gram TFIDF, it captures and analyzes content and text messages. A boosting ensemble technique enhances classification accuracy, while an auto-rule set detects up to 150K phishing URLs daily.
Scan fraudulent websites
Deliver real-time alerts to your IT team when employees engage with fake websites. Powered by computer vision and Visual AI, the system scans web content, forms, and images. Advanced webpage analysis detects, prioritizes, and scores high-risk elements to identify phishing and BEC threats.
Why Email and Collaboration Security
Protect email and collaboration apps across the ever-changing attack surface
Enhance all cloud services
- Protect against complex threats from email beyond those detected by cloud email services’ security.
- Powered by AI and sandbox malware analysis, Email and Collaboration Security uncovers zero-day threats, BEC attacks, and advanced phishing techniques that built-in security can miss.
- Cover every angle with protection for both cloud-hosted and on-premises email solutions.

Collaborate with confidence
- Scan files in real-time for threats and enforce data loss prevention across collaboration platforms.
- Access 200+ customizable compliance templates for Microsoft OneDrive® for Business, SharePoint® Online, Teams®, Dropbox®, Box®, and Google Drive™.
- Detect and prevent infiltration through cloud file-sharing and messaging tools, regardless of user location.
Break the attack chain
- Improve visibility and management of any email service with Email and Collaboration Security.
- Detect threats from additional attack vectors, including endpoint, network, cloud, or third-party intelligence.
- Investigate suspicious events that can be missed and respond quickly from one platform.
- Proactively silence threats and disrupt attacks with Cyber Risk Exposure Management (CREM) by continuous analysis of risky users, behavior, and events.
Market-leading performance

Gartner Peer Insights - Trend Micro reviews in Email Security Platform
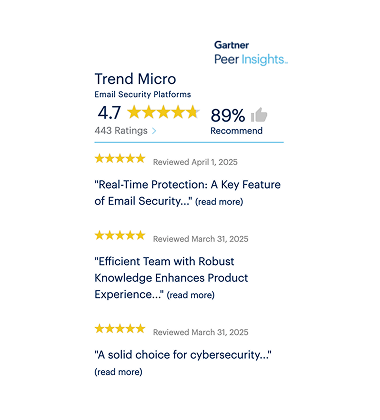

Email and Collaboration Security is rated #1 by SE LABS® and won the AAA Email Security Service award.

What customers say
Enhance email and collaboration security
Cyber Risk Exposure Management (CREM)
Dramatically reduce your risk exposure with continuous attack surface discovery, real-time risk assessments and prioritization, and automated mitigation.
Security Operations
Gain greater visibility, break down silos, and achieve faster, more precise detection.
Security Awareness Training
Minimize human risk and empower employees to become your first line of defense against evolving cyberattacks.
Trend Email Solutions
Choose from a broad range of leading email and collaboration security capabilities
Trend Micro™ Deep Discovery™ Email Inspector
Provides the most advanced threat protection against targeted attacks.
Trend Micro™ ScanMail™ Suite for Microsoft Exchange (SMEX)
The industry’s most comprehensive mail server security protects internal and external email against phishing, ransomware, and targeted attacks.
Trend ScanMail™ for Domino (SMD)
Leading malware and spam protection secures internal and external email as a native Domino server application to stop phishing, ransomware, and targeted attacks.
Trend Micro™ PortalProtect™ for Microsoft SharePoint
Provides malware, content filtering, and data loss prevention securing your collaborations with employees, partners, and customers.
Trend Micro IM Security™ for Microsoft Skype for Business Servers
Protects instant messaging from malware, web threats, content violations, and data loss.
Try the Trend Vision One platform today


