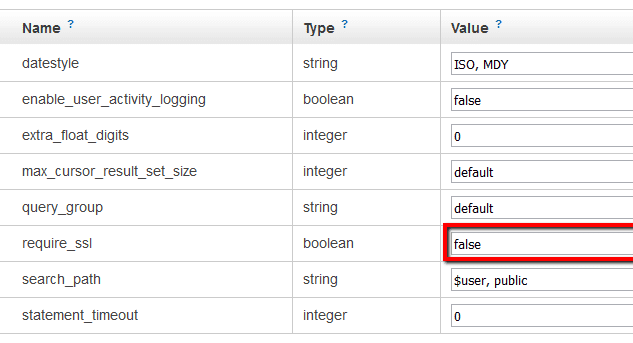
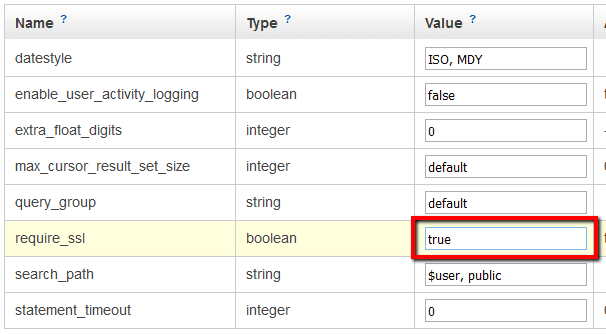
Ensure that all the parameter groups associated with your Amazon Redshift clusters have the require_ssl parameter enabled in order to keep your data secure in transit by encrypting the connection between the clients (applications) and your warehouse clusters.
This rule can help you with the following compliance standards:
- PCI
- HIPAA
- APRA
- MAS
- NIST4
For further details on compliance standards supported by Conformity, see here.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
When Redshift clusters are not configured to require Secure Sockets Layer (SSL) connections, the communication between the clients and these clusters is vulnerable to eavesdropping and man-in-the-middle (MITM) attacks. Cloud Conformity strongly recommends enabling SSL for your clusters front-end connection when dealing with sensitive or private data.
Note: For this rule, Cloud Conformity assumes that your Amazon Redshift clusters are not associated with the default parameter group created automatically by AWS, as the default parameter group cannot be modified to update the require_ssl parameter value.
Audit
To determine if your Amazon Redshift non-default parameter groups have the require_ssl parameter enabled, perform the following:
Remediation / Resolution
To enable require_ssl parameter within your Amazon Redshift non-default parameter groups in order to use SSL for the client-cluster connection, perform the following:
References
- AWS Documentation
- Amazon Redshift FAQs
- Amazon Redshift Clusters
- Managing Clusters Using the Console
- Manage Clusters Using the Amazon Redshift CLI and API
- Configure Security Options for Connections
- Managing Parameter Groups Using the Console
- AWS Command Line Interface (CLI) Documentation
- redshift
- describe-clusters
- modify-cluster-parameter-group
- reboot-cluster