Ensure there is a CloudWatch alarm created in your AWS account that is triggered each time a configuration change is made at the CloudTrail service level. The alarm must fire when an API call is made to create, update or delete an AWS CloudTrail trail or when the logging process defined by a trail is stopped or started.
This rule can help you with the following compliance standards:
- CISAWSF
- PCI
- GDPR
- APRA
- MAS
- NIST4
For further details on compliance standards supported by Conformity, see here.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
Using CloudWatch alarms to detect AWS CloudTrail config changes can help you to maintain the integrity of the service configuration and prevent AWS users from covering their tracks after performing unauthorized actions within your AWS account.
Note 1: For this rule Cloud Conformity assumes that the CloudTrail service is already enabled to stream event log data to CloudWatch in your AWS account, otherwise see this rule to enable AWS Cloudtrail – CloudWatch integration.
Note 2: You can specify a custom name for the alarm using the rule configuration settings available on Cloud Conformity dashboard. Otherwise, the default name used for this rule will be “CloudTrail Changes”.
Audit
To determine if you have any CloudWatch alarms that are currently monitoring AWS CloudTrail configuration changes, perform the following:
Remediation / Resolution
Step 1: Create a Simple Notification Service (SNS) topic and the necessary subscriptions to send notifications whenever the CloudWatch alarm is triggered.
Step 2: Create AWS CloudWatch metric filter and the required alarm that will send SNS notifications whenever an AWS CloudTrail configuration change is being made.

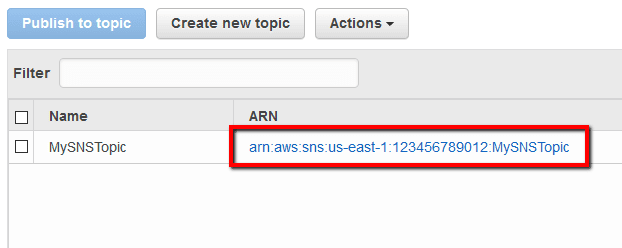
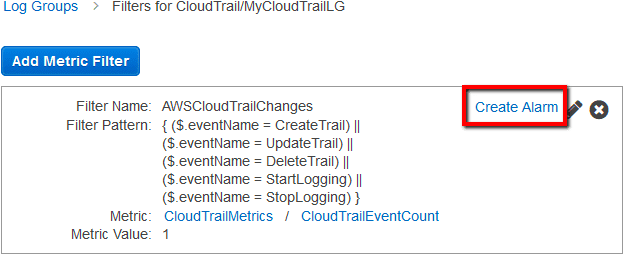 .
.  to trigger the alarm every time a change is made in the AWS CloudTrail configuration.
to trigger the alarm every time a change is made in the AWS CloudTrail configuration. .
.