PE_SALITY and PE_VIRUX: Persistent File Infectors

PE_SALITY and PE_VIRUX are two of the most prevalent file infector families to date. Trend Micro engineers observed an increase in the number of PE_SALITY- and PE_VIRUX-infected systems in the Asia/Pacific region. In March 2010, they also observed a spike in the PE_SALITY and PE_VIRUX infection count in Latin America.
File infectors play a crucial role in spreading malware infections. Cybercriminals, however, no longer create file infectors to gain notoriety as in the past. They have instead taken to using file infectors as means to instigate malicious attacks. Although file infectors are not as popular as ZeuS, FAKEAV, and KOOBFACE variants, they remain persistent and continuously evolve in terms of malware technology.
How do these file infectors arrive on users' systems?
| PE_SALITY variants can arrive via removable drives and network shares. These may also be downloaded from malicious sites. A certain PE_SALITY variant exploited the Windows shortcut flaw (.LNK vulnerability) as an infection vector. | PE_VIRUX variants usually take advantage of vulnerabilities to infect users' systems. In fact, several .PDF exploits led to the download of PE_VIRUX variants. These may, however, also infect systems via drive-by downloads. Like PE_SALITY variants, these may also arrive via network shares and removable drives. |
How do these file infectors propagate?
| PE_SALITY
worm variant detected as WORM_SALITY.RL creates a malicious .LNK file that exploits the Windows shortcut flaw. Opening a shared folder triggers the exploit, which then executes WORM_SALITY.RL. It also propagates via file infection and by dropping an AUTORUN.INF file onto removable drives connected to an infected system. PE_SALITY variants infect .SCR and .EXE files. Accessing infected .SCR and .EXE files shared across a network thus eventually leads to malware infections. |
PE_VIRUX variants spread across removable drives and network shares. Like PE_SALITY variants, these also infect.EXE and .SCR files apart from .ASP, .HTM, and .PHP files. |
What happens when PE_SALITY and PE_VIRUX are executed on the users' systems?
| When executed, PE_SALITY variants infect all .EXE and .SCR files. These also access certain IRC servers via port 80. Once connected, these receive and execute commands, compromising infected systems’ security. These download other malicious files, depending on when the connection was established, onto the infected systems. This routine makes the systems vulnerable to other infections. Like PE_VIRUX variants, these also infect other malware that reside on the systems. The resulting malware blend then becomes more difficult to detect and consequently terminate. PE_SALITY variants also terminate antivirus-related processes. These also create registry entries to disable the Windows Firewall and Security plug-in, further increasing the systems' vulnerability to online threats. | A certain PE_VIRUX variant infects script files via the injection of a malicious iframe code, turning these into malware detected as HTML_IFRAME.NV. When executed, the script triggers the download of HTML_EXPLOIT, which leads to a series of malware infections. PE_VIRUX variants access IRC servers from which these receive malicious commands as well as other malicious URLs from which these download other malware. Although the downloaded malware may vary, these are usually FAKEAV variants. Like PE_SALITY variants, these also terminate security-related applications and disables the Windows Firewall Security plug-in. |
What types of infection do PE_SALITY and PE_VIRUX variants use to infect files?
| PE_SALITY infections are classified under the Entry Point Obscuring (EPO)-appending infection type, which occurs when a malware inserts its code at the end of those of their host files. | PE_VIRUX infections are classified under the EPO cavity-appending infection type. In this method, the malware does not modify its entry point. It instead inserts a JUMP or CALL statement that points to the malicious code after its entry point. |
How do these file infectors affect users?
File infectors, like any other information-stealing malware, have become a preferred cybercrime tool for generating profit. These spread through various means, thus infecting several systems and even networks. These also open infected systems and networks up to other malware infections and risks (e.g., information and identity theft) with their capability to access IRC servers.
Why are these file infectors noteworthy?
PE_SALITY and PE_VIRUX variants pose huge risks to home users and business organizations alike. Because these are capable of infecting other existing malware on target systems, PE_SALITY and PE_VIRUX variants become more difficult to detect and consequently remove, apart from exhibiting the infected malware's routines. These also spread via different means such as removable drives, network shares, exploits, and the Internet. User systems that access any file residing on an infected network thus also get infected.
Trend Micro monitors PE_SALITY and PE_VIRUX variants due to their malware technology, particularly their ability to terminate antivirus applications and the ways by which these spread across networks. Furthermore, these use multilayer encryption, making these harder to analyze.
Are Trend Micro product users protected from these file infectors?
Trend Micro products powered by the Trend Micro™ Smart Protection Network™ protect users from all known PE_SALITY and PE_VIRUX variants and their components. Web reputation technology blocks user access to related URLs to prevent the download of malicious components. Users are strongly advised to keep their systems up-to-date and to disable the AUTORUN features of their removable drives so these will not automatically execute malware.
Trend Micro OfficeScan 10 users are also urged to use the software's Self-Protection feature to prevent the execution of PE_SALITY and PE_VIRUX variants.
Here are instructions on how to reconfigure OfficeScan. To do this, follow the procedure below.
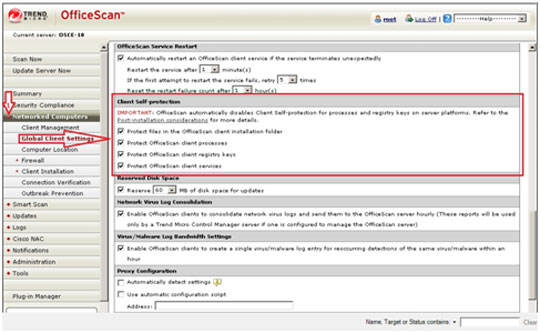
Enabling the OfficeScan 10 Self-protection feature:
- Open the OfficeScan 10 Web console.
- On the left panel, click Networked Computers to expand its list of contents.
- From these click Global Client Settings to open the user interface found on the right panel.
- On the right panel, locate Client Self-Protection and tick your preferred options off on the list to ensure and enable self-protection against malware that can disable the software.
- At the bottom of the right panel, click Save.
OfficeScan 10 users are also encouraged to enable the Behavioral Monitoring Module, which helps protect their systems from PE_SALITY infections. To do this, follow the procedure below:
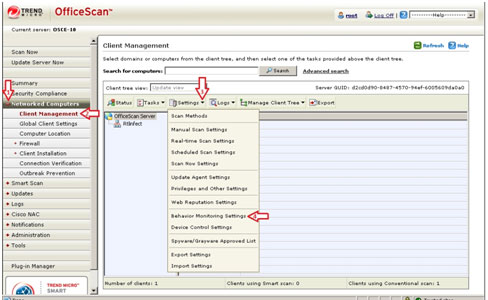
Enabling Behavioral Monitoring Module
- Open the OfficeScan 10 Web console.
- On the left panel, click Networked Computers to expand its list of contents.
- From these, click Client Management to open the user interface on the right panel.
- On the right panel, click Settings and choose Behavioral Monitoring Settings from the drop-down list. This will open a new window from which you can configure the software's behavioral monitoring settings.
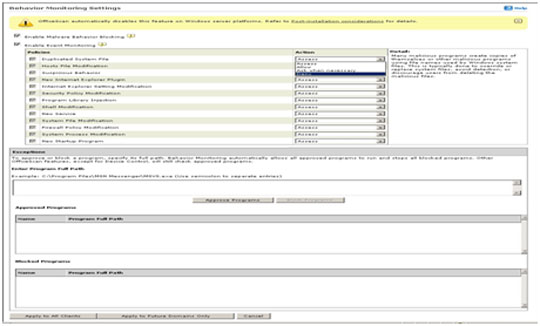
- Click Enable Malware Behavior Blocking.
- Click Enable Event Monitoring and set your policies and desired actions.
- At the bottom of the window, click Apply to All Clients.
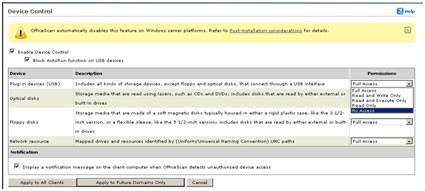
Enable OfficeScan 10's Device Access Control or (DAC) feature. To do this, follow the procedure below.
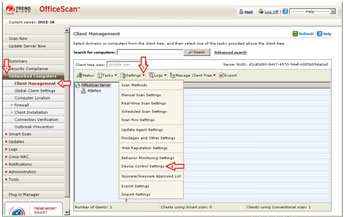
Enabling Device Access Control or DAC feature
- Open the OfficeScan 10 Web console.
- On the left panel, click Networked Computers to expand its list of contents.
- From these, click Client Management to open user interface on the right panel.
- On the right panel, click Settings and choose Device Control Settings from the drop-down list. This will open a new window from which you can configure the software's behavioral monitoring settings.
- Click Enable Device Control then Block Autorun function on USB devices after setting your desired permissions.
- At the bottom of the window, click Apply to All Clients.
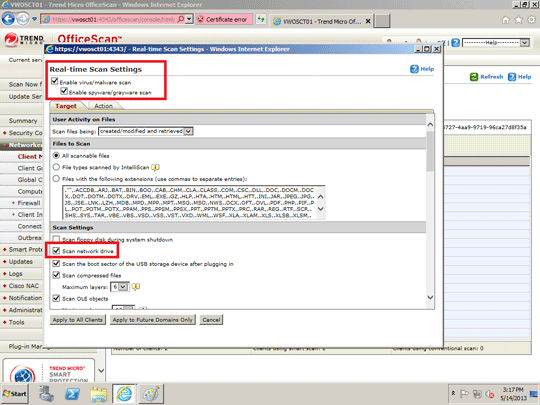
Enabling Scan Network Drive
- Open the OfficeScan 10 Web console.
- On the left panel, click Networked Computers to expand its list of contents.
- From these, click Client Management to open user interface on the right panel.
- On the right panel, click Settings and select Scan Settings then Real-Time Scan Settings.
- Click All scannable files and Scan network drive.
- At the bottom of the window, click Save.
In addition, users may download the fixtools for PE_SALITY and PE_VIRUX:
Expert Insights:
"PE_VIRUX and PE_SALITY variants are like living organisms that evolve over time to the extent when formulating a new cure or solution seems ridiculous. These file infectors open infected systems’ doors to other malware by shutting down installed antivirus applications, making their survival inevitable. Fortunately, Trend Micro products can prevent these prevalent threats from infecting systems and can resolve their effects via features like Behavioral monitoring (i.e., for attempts to infect systems), Device Access Control (i.e., for worms and other malware that spread via USB devices), and Self-Protection (i.e., for antivirus software termination)." --Francis Saguiguit, Threat Analyst
"PE_VIRUX and PE_SALITY variants remain persistent because these are pay-per-install (PPI) malware. The cybercriminals responsible for their creation are thus financially motivated to continuously improve their functionalities."--Jessa Dela Torre, Threat Response Engineer