Staying Safe from Disaster Relief Scams
March 15, 2011
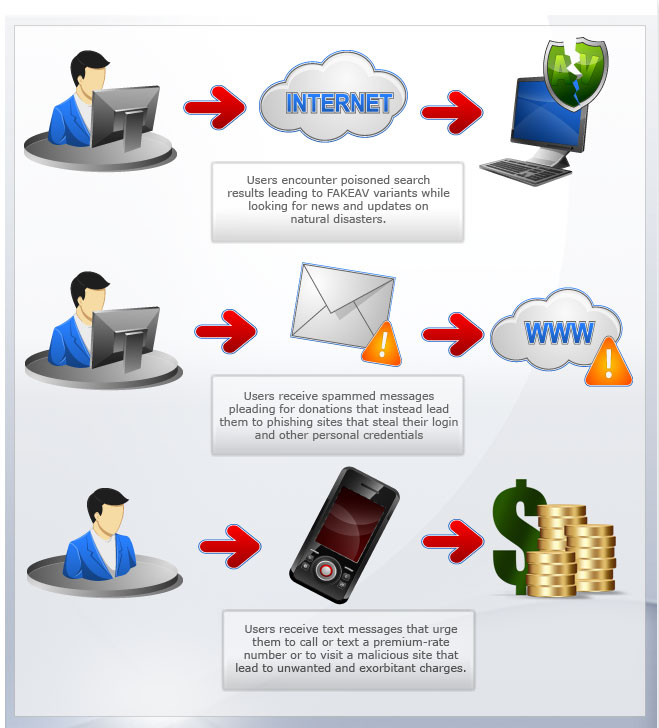
As the world scrambles for more information on natural disasters that hit certain parts of the globe, cybercriminals are quicker on the draw. It only takes a few hours before disaster-related Web threats find their way to the Internet and, eventually, to users’ systems.
How do these threats arrive on users’ systems?
Disaster-related threats arrive via the Internet or, in some cases, via text messages. Initial attacks leverage news reports to attract users in search of more information on disasters. Cybercriminals employ poisoned search results to lead users to rogue antivirus or FAKEAV download pages.
Apart from downloading FAKEAV, users may also become victims of fake donation scams, phishing attacks, hoaxes, and spammed and text messages taking advantage of a natural calamity.
What immediate threat can users encounter?
Right after a major natural disaster strikes, Internet users may immediately encounter poisoned results. Using popular keywords to poison search engine results, cybercriminals easily spread FAKEAV to unknowing albeit curious users.
What other threats may take advantage of such events?
Unfortunately, disaster relief scams do not stop at just FAKEAV downloads. Hours after a major natural calamity hits, users may also encounter the following as seen during the recent disasters in Japan:
- Fraudulent donation sites: Cybercriminals may change their keywords to appeal to users who are looking for opportunities to help. Malicious sites posing as fake donation sites are not uncommon and should be expected whenever disasters occur. Cybercriminals even go as far as creating multiple parked domains that they can readily use for phishing attacks and other malicious activities.
- News hoaxes: Hoaxes can be used as bait or can cause fear and unnecessary panic among curious users. False rumors about radiation effects on other countries following the nuclear power plant problem in Japan, for instance, circulated online. Similarly, bogus reports concerning the deaths of two popular Japanese cartoon character creators also caught the world’s attention. Apart from spreading lies, hoaxes can also be used in blackhat search engine optimization (SEO) attacks.
- Spammed messages appeal to users: Apart from Web-based threats, disaster-related attacks may also arrive via spam. Leveraging human curiosity and the instinct to give, these scams typically arrive as heart-wrenching appeals for help. At the end, however, the scams point users to dubious sites instead of to those of legitimate organizations. As even legitimate organizations have been spoofed and hacked in the past, users need to be extra careful. In addition to scams, chain-letter-type spammed messages have also been seen in the past. Users who end up falling into cybercriminals’ traps may inadvertently contribute to spreading spam by forwarding email messages to their contacts.
- SMS scams: Unfortunately, scammers do not limit themselves to online resources. To further their schemes, they have also been known to send text messages enticing good souls to send money to an account or to reply to a premium-rate number. Text messages and even phone calls made to landline numbers have previously been used in phishing tactics as well. It goes without saying that cybercriminals will stop at nothing to achieve their goals.
How do these threats affect users?
As with most of today’s cybercrime attacks, the primary end goal of disaster-related threats is to generate profit. Even during times or natural disasters, attackers find every opportunity to lure in those who want to extend their help.
In FAKEAV attacks, scareware tactics are used to convince users that their systems have been infected and that they need to pay a specified amount to get rid of the malware. Fake donation sites and other scams prey on users who merely want to help, benefiting from their generosity in the process.
Sadly, in some attacks, users are not only conned into losing money. They may also become victims of information theft, as in cases of phishing and FAKEAV attacks. Their systems may also be compromised due to malware infection. The bottom line is that users who are simply looking for more information or for opportunities to help only end up at the losing end of the bargain.
Are Trend Micro product users protected from these threats?
Yes, the Trend Micro™ Smart Protection Network™ email reputation technology prevents spammed messages from reaching users’ inboxes. Web reputation technology blocks access to malicious sites that host malware and serve spam. File reputation technology likewise prevents the execution of and deletes all known malicious files from users’ systems.
What can users do to prevent these threats from affecting their systems?
Best Practices for the Web
- Instead of using search engines to find relevant news reports, it is better to directly access reliable news sites.
- When using search engines, read the overview of a result to check if it makes sense. Malicious results typically have random words mixed up with the keywords in the overview, which usually do not result in sensible descriptions.
- Directly type in URLs into the Web browser’s address bar to avoid clicking poisoned links that crop up in search engines. However, make sure that you correctly type in the URLs to avoid malicious pages that use typosquatting techniques.
- Do not click unverified links, especially if these contain random characters. Always double-check the complete URL of shortened links before clicking them. To be sure, you can verify a site’s legitimacy with the help of the Trend Micro Site Safety Center.
- If you want to make a donation, it is best to directly go to trusted organizations’ official sites.
- Install a good URL-filtering program such as Web Protection Add-On that can be integrated into browsers.
Best Practices for Email
- Immediately delete suspicious-looking email messages, particularly those that come from unknown senders.
- Do not send money or provide personal information to unverified senders.
- Do not forward chain-letter-type messages to your contacts.
- Avoid downloading file attachments or clicking links embedded in spammed or suspicious-looking email messages.
- Install a security software that immediately deletes spammed messages from your inboxes and that verifies the legitimacy of the sites you visit.
Expert Insights
"... we’ve previously documented instances of attacks that leveraged natural disasters such as Hurricane Katrina in 2005, Hurricane Gustav in 2008, Chinese Sichuan earthquake in 2008, the latest attack used the Haiti earthquake in 2010. Users should remember to choose trustworthy organizations when it comes to handing over their donations."
Noriyaki Hayashi, Senior threat researcher
"Blackhat SEO attacks leading to rogue antivirus downloads is still very common. We recommend that our readers get the latest news from trusted media outlets to prevent becoming victims of blackhat SEO attacks." Norman Ingal, Threat response engineer