KOOBFACE Targets Social Networking Sites
KOOBFACE is considered a revolutionary threat as it is the first malware family that have a successful and continuous run propagating in social networking sites. It was initially found to spread on Facebook, but later on was discovered in other social networking sites like Twitter, MySpace and others. It is also considered unique among other malware because as most cram their components on one malicious file, KOOBFACE divides its capabilities into various components that work together to form the KOOBFACE infection.
Trend Micro has reported several incidents involving this threat in its blog entries:
KOOBFACE IP Taken Down, Gang Transfers Hosting to China
KOOBFACE Makes a Comeback
New KOOBFACE Component Imitates Facebook User
Christmas-Themed KOOBFACE Campaign Seen
KOOBFACE Abuses Google Reader
Pick Your Poison: KOOBFACE or FAKEAV
To read more about this threat, Trend Micro has also created extensive analysis in the following papers:
Web 2.0 Botnet: KOOBFACE Revisited
The Real Face of KOOBFACE: The Largest Web 2.0 Botnet Explained
The Heart of KOOBFACE: C&C and Social Network Propagation
Show Me the Money! The Monetization of KOOBFACE
How do users get this Web threat?
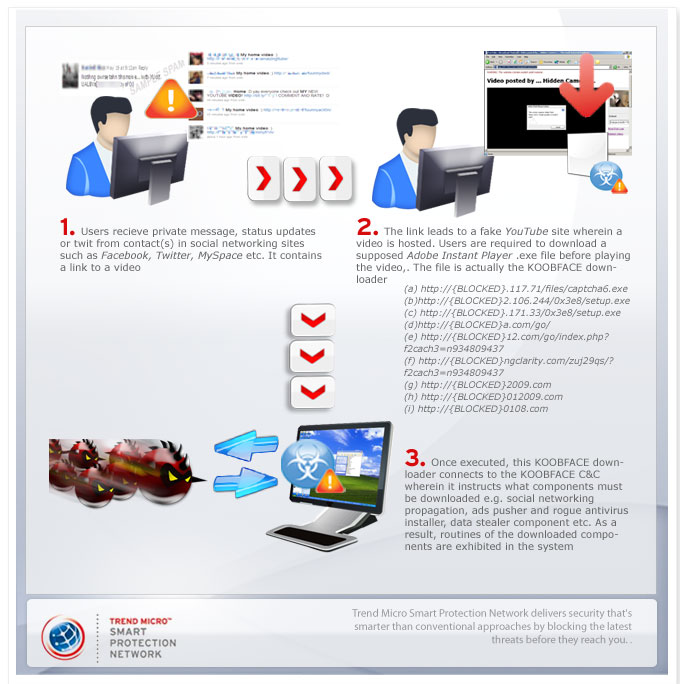
KOOBFACE attack usually arrives as a private message, status updates, or a tweet (Twitter) from a users contact or friend. It contains catchy messages to entice users to read them. These messages usually contain a link that leads to a site (usually a fake YouTube site) wherein a video is hosted. Users who attempt to play this video are then prompted to install an executable file, usually a fake Adobe Instant Player. In reality, this .EXE file is a downloader of the KOOBFACE components.
What happens once the threat gets inside computers/networks?
Once the downloader is executed in the system, it downloads other components of the KOOBFACE. This downloader serves different functions, such as 1.) determining what social network the affected user is a member of, 2.) connecting to the KOOBFACE command and control (C&C) and 3.) downloading the KOOBFACE components the C&C instructs it to (download).
How are users affected by this threat?
KOOBFACE has different components that can adversely affect users in different ways. Its social network propagation components are responsible to spreading the spam messages to the affected user’s contacts in social networking sites. It can also function as a server component, making the infected system an unwitting Web server, making it part of the KOOBFACE botnet.
KOOBFACE instructs its C&C to download rouge antivirus program from specific sites. Furthermore, its data stealer component steals important information such as Windows digital product IDs, Internet profiles, email credentials, FTP credentials, and IM application credentials. It can also intercept search queries to Google, Yahoo, MSN, Ask, or Live and redirect users to dubious search portals via Web Search Hijacker. Users who may try to access legitimate sites may also be redirected to phishing sites via KOOBFACE Rogue DNS Changers component.
What is the driving force for this threat?
Infected systems becomes a part of the KOOBFACE botnet operations, including propagating the said variant to the users’ contacts in social networking sites.
KOOBFACE generates profit for its perpetrators with the downloading of the fake antivirus programs. By showing fake scanning results and its subsequent alarming message prompt, it persuades users to purchase the spoofed software. Perpetrators of this threat also generate income via Click fraud, information stealing, and online dating.
What is different in this attack?
The KOOBFACE C&C, by checking on the social network cookies found, determines what additional components the KOOBFACE downloader needs to download. If the affected user has Facebook, MySpace, and Twitter accounts, the KOOBFACE downloader reports the presence of these cookies to the KOOBFACE C&C. It then instructs the KOOBFACE downloader to download the social network propagation KOOBFACE components responsible for sending out messages in the specific site.
Why does this threat persist?
Aside from its popularity with users, social networking sites have also become an important tool for enterprises and small and medium businesses (SMB) to drive their businesses. Naturally, cybercriminals would want to take advantage of that. Unfortunately, it has also become a lucrative enterprise for its perpetrators.
Those people behind this are also up-to date with the latest security measures done by social networking sites and security experts alike. This enables them to create variants resilient of these security efforts.
Are Trend Micro users protected from this threat?
Trend Micro customers are protected from this threat via its Smart Protection Network by securing its users from different components of the attack. Spam messages related to this attacked are blocked, even before it reaches users’ s inboxes via its Mail Reputation services. Related links are also blocked via its Web reputation services while KOOBFACE variants are also detected and deleted via its File Reputation Services.
What can users do to prevent this threat from entering computers?
Users must avoid clickng on links provided in dubious messages. Since these messages come from users' contacts in the social networking site, it is best to verify its legitimacy directly with the specific contact. Users must also avoid downloading executable from dubious Web sites.
Non-Trend Micro users can also use free tools like Housecall to detect and delete possible KOOBFACE variants. Social networking sites such as Facebook and Twitter have been aggresively users about this attack.