Gumblar Steals More Credentials
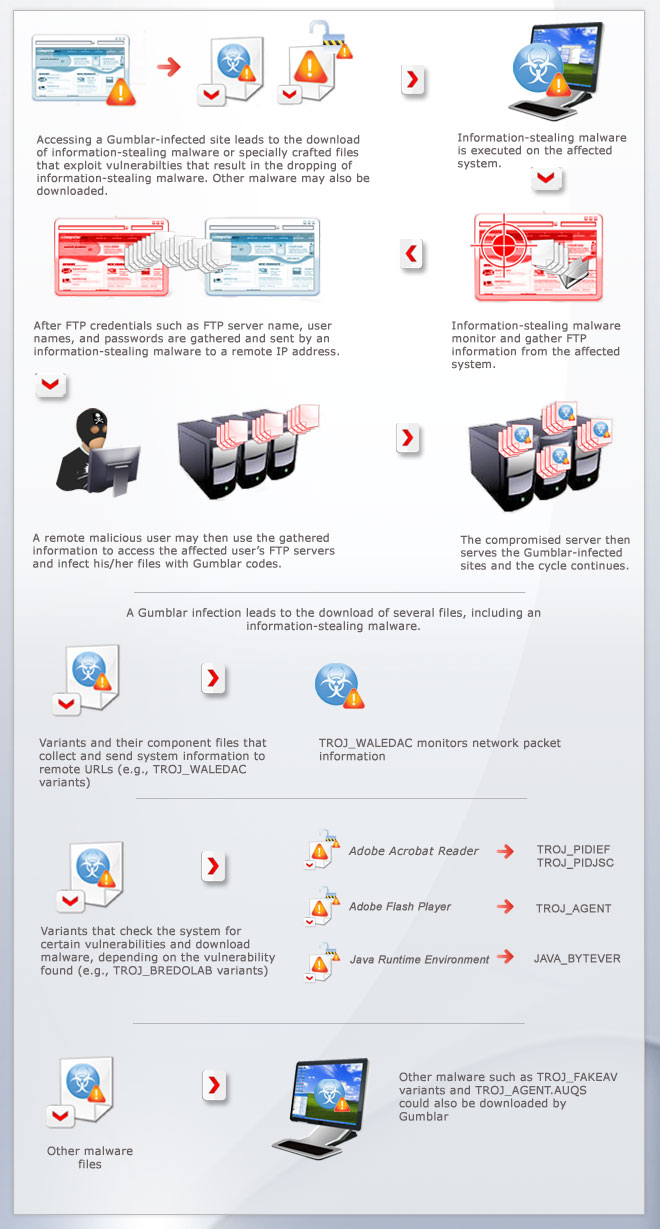
How does this threat get into users' systems?
A Gumblar-related attack arrives when a user accesses a compromised site embedded with malicious code. These sites redirect the user to malicious websites where the malicious code is hosted.
A new Gumblar attack has been given the name "Gumblar.8080," which originated from a URL redirector.
How does this threat affect users?
As the Gumblar script is an information stealer, users are directly affected when the script monitors and gathers FTP information from affected systems. The downloaded malicious files can be classified into variants and component files that collect system information and send these to remote URLs, variants that check systems for vulnerabilities, and variants that download other malware as final payloads.
How does this threat protect itself from detection and removal?
A major factor in Gumblar's stealth is that it uses file obfuscation to hide its malicious routines. This makes analysis harder because of hard-to-read codes. This also prevents anti-malware products from easily detecting the malware.
Due to obfuscation, the codes may differ but still result in the same malicious output. The JavaScript has also been modified to create a polymorphic code in order to avoid easy detection. This ability to dynamically generate and obfuscate codes has made Gumblar difficult to remove.
What is the driving force behind this threat?
The remote malicious user is able to access the FTP server using the stolen credentials. If the stolen credentials have administrative rights, the malicious user may infect the files in the FTP with malicious codes by downloading them, injecting Gumblar code into them, and reuploading them to the server. This way, the server will become a host to Gumblar-infected files.
How can users protect themselves from this attack?
Gumblar has been very difficult to remove due to its constant evolution. Though protection against Gumblar should be done by Web masters, users are advised to ensure that their systems are up-to-date with the latest system patches. This is a must since Gumblar leverages known vulnerabilities. Security software should likewise be installed and frequently updated to minimize the possibility of attack.
Trend Micro products use various aspects of the Smart Protection Network™ to protect systems against Gumblar infections. Gumblar-related domains are blocked by the Web reputation service while files infected by Gumblar may be cleaned with the help of file reputation service.