How to Keep Attackers at Bay
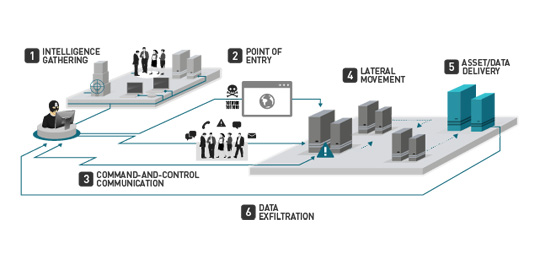
Malicious threat actors, particularly those engaged in targeted attacks, use several tools and routines to circumvent traditional protection. They do this to gain access to an organization’s infrastructure. With this access, these attackers aim to acquire confidential data or higher user privileges, enabling them to cruise within the corporate’s network with ease.
Below are some notable attacks in the past:
- Operation Payback. A campaign targeting financial firms such as PayPal, Visa, and Mastercard, which refused to process certain donations. The attack was in the form of a DDoS attack, which lead to these sites to be inaccessible for hours.
- OpGoldenDawn. A campaign that targeted Greece’s Ministry of Foreign Affairs and the Organization for Security and Co-operation in Europe (OSCE) that resulted to attackers leaking 3,700 documents from the company.
- Several organizations were targeted by a campaign that serves as retaliation for the closing of the then popular site Pirate Bay.
Despite these, there are available security measures that can help organizations combat such threats before it escalates.
What do these attackers need from my company?
There are several reasons why attackers target certain entities. These reasons range from political motivations to straight up data theft. However, the common denominator in this attack is to gather sensitive information for example, login credentials that can be used to access online banking accounts or extort users with.
Company database is another set of information that attackers can sell to other cybercriminals. Compromised systems within the organizations can also be used as part of an attacker's botnet.
These attacks are typically considered long-term and attackers intent to persistently access the organization's network.
How can organizations protect themselves from these attacks?
Segmentation
As corporate networks become more complex, the more need to break it down into as logical segments. A segment is basically a collection of systems, servers, printers and other devices that can access one another. These segments must be separated by firewall that can control and monitor network traffic. In a corporate setting, they can be considered check points. Without such, attackers can easily access the entire corporate infrastucture. Network segmentation also act as filter, in particular to employees who are not authorized to access certain data.
Networks can be broken down by using logical categories, such as segmenting by function, location or security level. Each segment must be as secure as possible.
Log Analysis
Logging (and analyzing logs) is critical in determining if organizations are being attacked. This provides insights as to what areas the attackers infiltrated and what data they are looking for. Dedicated analysts, who are well-versed with the daily network traffic activities, can help detect an attack early enough and may even thwart it before it's full operational. If not detected early, the data can be used by analysts to help recreate attackers activities.
Below are information that organizations should log:
- Records of internal mapping to physical machines
- Web proxy and Domain Name System (DNS) requests
- User access e.g. physical, Remote Desktop Protocol (RDP), virtual private network (VPN), and others
- External and internal network traffic (must be within legal bounds)
- Packet captures (pcap) or at least, network flows
- Emails with full headers and attachments
- Firewall drop rules
These data can be harnessed by technologies like the security information and event management (SIEM) and security event manager (SEM), which can determine the state and activity of corporate environments in real time.
User Accounts and Workstations
Often taken for granted, organizations must strictly implement policy pertaining to user's access to company resources. It is common for employees to have their own accounts and workstations. However, these accounts must have restricted access to minimize impact of attacks. Organizations must require implement a strict password creation policy and if possible, a two-factor authentication method.
What is penetration testing and how can it help?
Penetration testing is a method to evaulate system and network security. In such a test, an authorized agent (penetration team) simulates an attack on a system or network, either internally or externally. The intent is to determine and analyze potential software vulnerabilities or other operational weaknesses that can be abused by attackers.
This is also an opportunity for IT security and monitoring staff to gain real-life experience. To make it successful, organizations should provide considerable leeway to the penetration team. However, they can impose certain limits and must discuss this with them.
Are Trend Micro users protected from this threat?
Trend Micro protects users from this threat via Deep Discovery, which monitor and detect suspicious network activities within the organization’s infrastructure. Deep Security, on the other hand, is another layer of protection against exploits and vulnerabilities. Trend Micro Smart Protection Network provides protection against suspicious email messages, blocks access to known dubious domains, and detects malware if found in the system.