Zero-Day Internet Explorer Exploit Downloads HYDRAQ
February 19, 2010
Background of the Attack
Trend Micro received several reports and inquiries surrounding a series of attacks that exploited an application vulnerability to download HYDRAQ variants onto infected computers. Awareness about the attacks that first manifested as targeted against individuals increased when the code used in them was made publicly available. These attacks exploited a vulnerability in all versions of Internet Explorer (IE), except IE 5.0. For patch information, users are advised to refer to this Microsoft Web page.
What happens in this attack?
Users either received spammed messages or other inbound online communication means that led them to various exploit-ridden URLs, which cybercriminals specifically designed to carry exploits in order to execute malicious code on visitors’ computers without their knowledge.
These exploits targeted a vulnerability in a widely used application for which there had been no security updates yet. (January 21 Update: Patch now available in this Microsoft Web page.) Once the exploit is triggered by visiting a malicious site, a backdoor file is downloaded onto users’ computers without their knowledge.
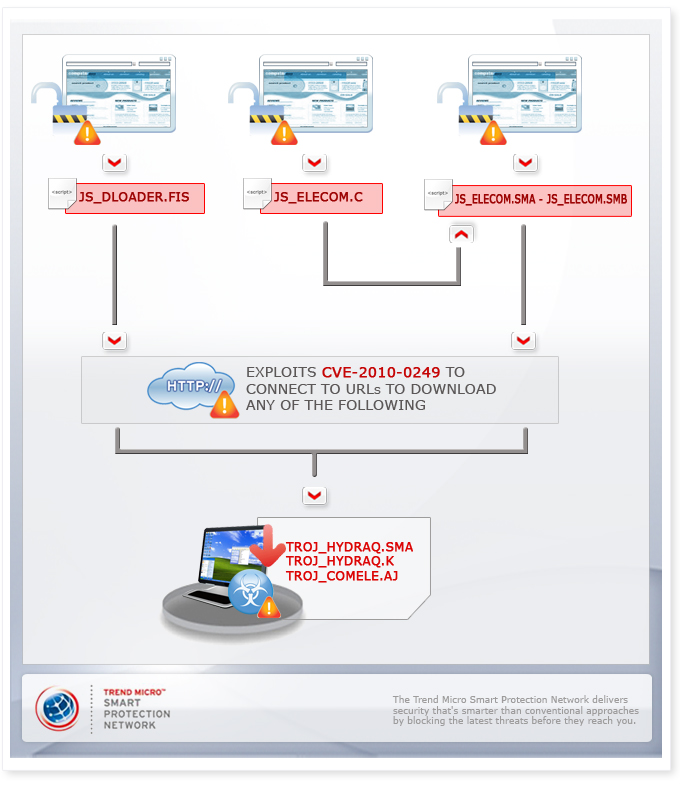
The diagram above illustrates the known versions related to this attack, each of which appeared one after another. The infection path using JS_DLOADER.FIS appeared first, followed by JS_ELECOM.C, and so forth. (January 21 Update: Subsequent exploit codes that appeared after JS_ELECOM.C are now detected by Trend Micro as the JS_ELECOM.SMA-JS_ELECOM.SMB tandem.) These exploit codes took advantage of the CVE-2010-0249 vulnerability to connect to remote URLs in order to download different HYDRAQ variants.
Why is this threat especially dangerous?
Systems affected by this threat are compromised in such a way that attackers who successfully exploit this vulnerability could take complete control of their systems (e.g., install programs; view, change, or delete data; or create new accounts with full user rights).
Am I at risk?
This attack is no longer targeted in nature. While its initial evolution was directed toward certain individuals, now that the code has been made accessible to everyone, cybercriminals can use them to instigate their own attacks. Therefore, if you have been affected by this attack and the browser you are currently using remains vulnerable, then your computer will perform the malicious routines of the Trojan payloads. These include connecting to several remote URLs, which may also host other malicious elements, and reassigning control of your computer to malicious attackers. A sample serving of the full range of malicious routines that can be performed on your computer can be found in the technical description of TROJ_HYDRAQ.SMA.
Is upgrading to the latest IE version enough to keep my computer from becoming infected?
No. The attack is continuously evolving. Performing the workaround provided by Microsoft is highly encouraged. However, enabling “Data Execution Prevention (DEP)” in IE versions where this is not enabled by default will only protect you from the publicly known exploits. There have already been reports of an exploit variant that can bypass IE’s DEP feature. (January 21 Update: Patch now available in this Microsoft Web page.)
So what can I do to protect my computer?
Apart from upgrading to the latest IE browser version, making sure that “DEP” is enabled, and using IE in protected mode (i.e., in Vista and Windows 7), you should also consider disabling your browser’s JavaScript feature. Trend Micro OfficeScan™ users with Intrusion Defense Firewall (IDF) plug-in are also protected from this attack if their systems are updated with IDF1003879 and 1003909 filters. Most importantly, however, you should update your IE browser by applying the patch mentioned here.
Trend Micro received several reports and inquiries surrounding a series of attacks that exploited an application vulnerability to download HYDRAQ variants onto infected computers. Awareness about the attacks that first manifested as targeted against individuals increased when the code used in them was made publicly available. These attacks exploited a vulnerability in all versions of Internet Explorer (IE), except IE 5.0. For patch information, users are advised to refer to this Microsoft Web page.
What happens in this attack?
Users either received spammed messages or other inbound online communication means that led them to various exploit-ridden URLs, which cybercriminals specifically designed to carry exploits in order to execute malicious code on visitors’ computers without their knowledge.
These exploits targeted a vulnerability in a widely used application for which there had been no security updates yet. (January 21 Update: Patch now available in this Microsoft Web page.) Once the exploit is triggered by visiting a malicious site, a backdoor file is downloaded onto users’ computers without their knowledge.
The diagram above illustrates the known versions related to this attack, each of which appeared one after another. The infection path using JS_DLOADER.FIS appeared first, followed by JS_ELECOM.C, and so forth. (January 21 Update: Subsequent exploit codes that appeared after JS_ELECOM.C are now detected by Trend Micro as the JS_ELECOM.SMA-JS_ELECOM.SMB tandem.) These exploit codes took advantage of the CVE-2010-0249 vulnerability to connect to remote URLs in order to download different HYDRAQ variants.
Why is this threat especially dangerous?
Systems affected by this threat are compromised in such a way that attackers who successfully exploit this vulnerability could take complete control of their systems (e.g., install programs; view, change, or delete data; or create new accounts with full user rights).
Am I at risk?
This attack is no longer targeted in nature. While its initial evolution was directed toward certain individuals, now that the code has been made accessible to everyone, cybercriminals can use them to instigate their own attacks. Therefore, if you have been affected by this attack and the browser you are currently using remains vulnerable, then your computer will perform the malicious routines of the Trojan payloads. These include connecting to several remote URLs, which may also host other malicious elements, and reassigning control of your computer to malicious attackers. A sample serving of the full range of malicious routines that can be performed on your computer can be found in the technical description of TROJ_HYDRAQ.SMA.
Is upgrading to the latest IE version enough to keep my computer from becoming infected?
No. The attack is continuously evolving. Performing the workaround provided by Microsoft is highly encouraged. However, enabling “Data Execution Prevention (DEP)” in IE versions where this is not enabled by default will only protect you from the publicly known exploits. There have already been reports of an exploit variant that can bypass IE’s DEP feature. (January 21 Update: Patch now available in this Microsoft Web page.)
So what can I do to protect my computer?
Apart from upgrading to the latest IE browser version, making sure that “DEP” is enabled, and using IE in protected mode (i.e., in Vista and Windows 7), you should also consider disabling your browser’s JavaScript feature. Trend Micro OfficeScan™ users with Intrusion Defense Firewall (IDF) plug-in are also protected from this attack if their systems are updated with IDF1003879 and 1003909 filters. Most importantly, however, you should update your IE browser by applying the patch mentioned here.