Emerging Vulnerabilities: Glitches Go Mobile
Recent mobile vulnerabilities signal the growth and evolution of the mobile threat landscape. In our 2Q 2013 Security Roundup, we pointed out two new and sophisticated vulnerabilities in Android. In addition, the security industry has also unraveled security flaws in SIM cards the iPhone. Clearly, cybercriminals are now finding smarter ways to exploit mobile devices with these improved methods.
As mobile vulnerabilities continue to surface, patching issues also start to heat up. Software vendors tried to address these concerns by tweaking their vulnerability disclosure policies for quicker patch deployment. However, the bigger debate is not about how long it must take to fix and publish the glitches, but how vulnerabilities are disclosed to vendors and affected users.
What are mobile vulnerabilities?
These are security weaknesses found in mobile devices and operating systems. Mobile vulnerabilities may expose mobile devices to malware attacks and exploits.
What are exploits?
An exploit is a code crafted by attackers to take advantage of a vulnerability in software or devices. Exploit codes are typically assimilated with malware. Once exploit codes are successfully executed, the related malware drops a copy of itself into the vulnerable system and performs malicious activities that puts devices and stored data at risk.
In some cases, exploits may be used as a part of a multicomponent attack. Exploits can drop other malware that carry backdoors and spyware.
Which new mobile vulnerabilities should I be wary of?
Mobile users must take note of the following new bugs.
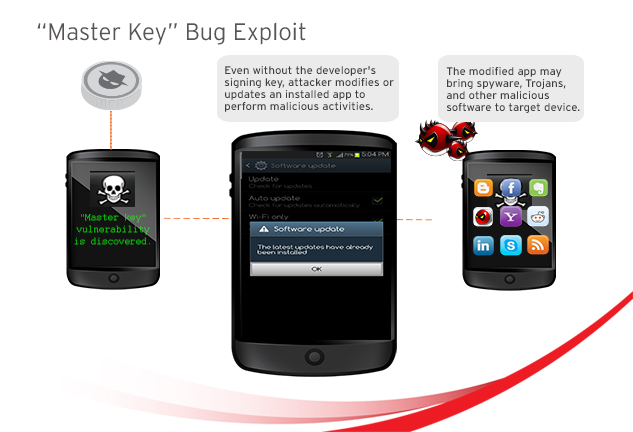
1. The Android “master key” vulnerability. Found in July 2013, this is the first exploitable flaw found in the kernel of nearly all Android-based devices.
The vulnerability allows installed apps to be modified and updated without the developer’s signing key. Therefore, the bug enables attackers to perform malicious mobile activities. These include replacing legitimate apps with malicious ones and applying malicious updates to online banking apps.
2. OBAD malware vulnerability. Similar to backdoors and rootkits, OBAD requests root and device administrator privileges to gain full control of infected Android-based devices. OBAD repeatedly shows pop-up notifications to convince users to grant these permissions. It also makes use of an obfuscation technique that makes detection and cleanup difficult.
3. The SIM card vulnerability. The source of this bug is the old encryption system used in most SIM cards. It allows attackers to generate a device error that reveals the 56-bit security key through a simple text message. This key can be used to trigger downloading malicious Java applets that can pave the way to several malicious routines. Among these routines are spreading text messages and location spying.
It’s important to note that this vulnerability isn’t dependent on the mobile operating system (OS); rather, it can affect different types of mobile OSs in different devices.
4. The iOS 6 security flaw. The fourth glitch shows that Apple devices aren’t immune to bugs. Researchers revealed that when connected to a fake charging station, the security flaw can grant complete access to an iPhone or iPad with an iOS 6 platform.Software vendors provide patches to repair detected vulnerabilities. But, it usually takes time for vendors to make a patch available after identifying a vulnerability. Cybercriminals take advantage of this window of exposure to exploit vulnerable mobile devices.
The existing Android update process below compounds this problem on patching as it further delays the deployment of software updates and patches:
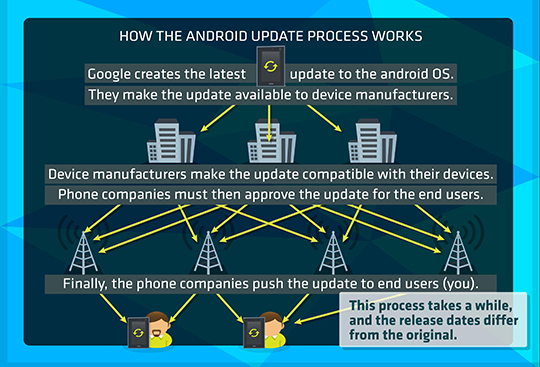
Figure 1. How the Android update process works
Before reaching users, patches are first given to manufacturers and service providers first to make it compatible to multiple platforms and devices.
What should I do to keep my mobile device safe from exploits?
Mobile vulnerabilities and bugs are fixed through patches or updates created by software vendors. It is recommended to immediately apply these patches once available.
However, not all Android phones receive the latest updates. In most cases, wireless carriers or mobile manufacturers decide on the updates they wish to deploy. Manufacturers oftentimes do not make the updates available. If your device is unable to receive these security updates, the device is considered “stale”. To keep a “stale” device safe, the best thing to do is to make sure that a trusted mobile security is installed. This won’t fix the bug, but it can help prevent an exploit.
There are other proactive measures to blocking exploits that target the abovementioned bugs. For the “master key” Android flaw, disable your device from installing apps from third-party app stores. This can be disabled in ‘Security’ found in the system settings of your Android device.
Trend Micro Mobile Security actively detects the OBAD malware to keep users safe from related exploits. This malware is also cleaned by our Hidden Device Admin Detector.
Lastly, the SIM card vulnerability can be dealt with in two ways. First, filter your text messages and immediately block suspicious texts from unknown numbers. Second, seek assistance from your phone provider. Ask if they offer in-network SMS filtering to help you detect malicious messages.
How do I know if my device has been exploited?
It depends on the known exploits that target the vulnerabilities mentioned above. For example, there are no active exploits related to the SIM card bug. But, if your device has Trojanized online banking apps from the abuse of the “master key” vulnerability, you will notice that one banking app file is smaller than usual. In the screenshot below the inserted malicious file is classes.dex with 205 KB:
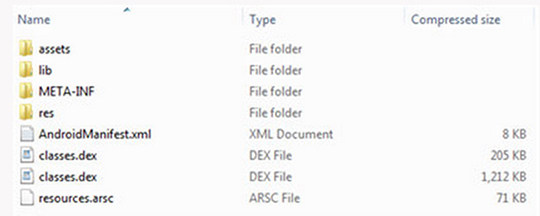
Figure 2. The inserted malicious file "classes.dex" has a smaller file size than the legitimate version
In addition, the OBAD malware have an active characteristic. It displays frequent pop-up messages when the device restarts. Pop-ups also appear when users press the back button and the home button.
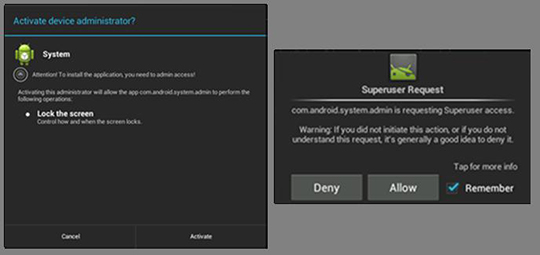
Figure 3. Activating device administrator allows the malware to run in stealth mode
You can also distinguish the malicious app from the mixed Android system apps under Apps Management. But, you won’t be able to uninstall it because it’s a device admin app.
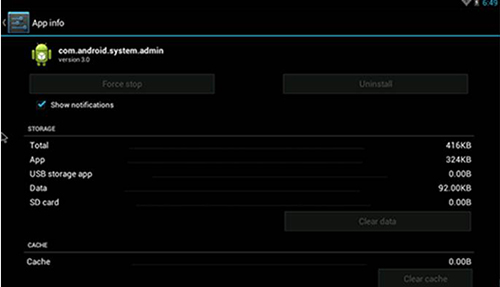
Figure 4. Malware’s app information
Determining whether your device is susceptible to attacks can be a daunting task. It’s best to follow the security measures recommended above to ensure that your device stays safe against threats.
Are Trend Micro users protected from these threats?
Yes.Trend Micro Mobile Security constantly updates user protection against emerging mobile threats. It also actively detects and cleans the OBAD malware to keep users safe from related exploits. Additionally, Trend Micro Mobile App Reputation Service detects apps that abuse the “master key” vulnerability.
EXPERT INSIGHTS
“The need for mobile users to keep their device secure from threats is now greater than ever, and is bound to even be more critical later on. Not only are new threats or infection points emerging; the known threats are also increasing, and improving at the same time. As reported in our recently released 2Q 2013 Security Roundup, the malicious and high-risk apps found affecting Android has reached 718,000 — showing an increase of 350,000 in just 6 months.
For now, the best course of action that users can take is to make sure that their device software is always updated. This step, along with installing a security software and downloading only from trusted sources should help minimize the risk of being affected by attacks.” – Gelo Abendan, technical communications specialist