XPAJ: Back with a Vengeance
File infectors have recently seen a resurgence in the threat landscape. Prominent examples of file infectors are MUSTAN and QUERVAR. But another family of file infectors has once again made an appearance in the threat landscape.
XPAJ is a family of file infectors that was first seen in October 2009 and has resurfaced in October 2012. Since then, XPAJ variants have infected users’ systems in different countries including Australia, India, Japan, Italy, and the US. It has since spread to other countries in North America and Europe.
XPAJ variants are known to infect the master boot record (MBR) which makes malware removal difficult. XPAJ was also linked to click fraud incidents.
How does XPAJ get into my computer and what does it do?
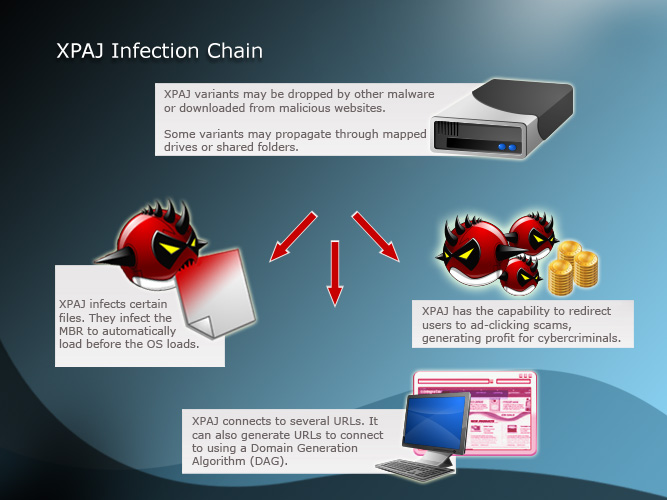
XPAJ enters users’ computers through different methods. XPAJ can be dropped by other malware or downloaded unknowingly through visiting malicious sites.
Once inside the system, XPAJ drops its encrypted mother file. XPAJ variants infect system files with the extensions .DLL, .EXE., .SCR, and .SYS. Aside from infecting these file types; XPAJ variants also infect the MBR. While other malware usually create registry entries to automatically load at system start-up, XPAJ variants infect the MBR which causes the malware to load before the operating system (OS). This makes removal of XPAJ malware even more difficult.
XPAJ also generates 197 URLs to connect to using a domain generation algorithm (DGA). This is done just case the malware cannot connect to the specific sites. The fact that XPAJ variants have URL-generating capabilities makes it difficult to block all related URLs.
Click fraud is another notorious routine by XPAJ. XPAJ redirects users to ad-clicking scams, which can generate profit for the cybercriminals.
Some XPAJ variants can spread via mapped drives or shared folders. This means that it is possible to infect other computers in the network with only one infected computer.
How does this affect my computer?
XPAJ variants infect executable files. Infected executable files often lead to malfunctioning computers, programs, applications, or even OSs. In the case of the file infector QUERVAR, affected users weren’t able to access Microsoft Excel and Word files.
It’s hard to detect and remove the XPAJ malware because it overwrites the MBR. This means that the malware will actually load before your OS does.
In addition, the click fraud routine of these malware makes users unwitting pawns in the cybercriminals’ money-making schemes.
How can I tell if my computer is infected with XPAJ?
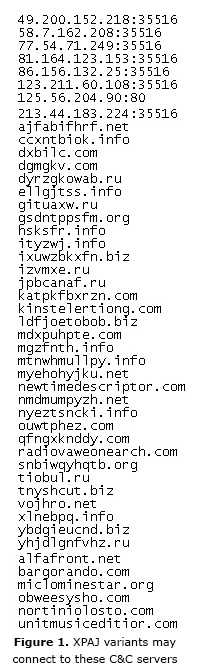
System administrators can check if XPAJ communicates with the command-and-control (C&C) servers listed below:
Users can check if certain files can be found in the Windows directory. As previously mentioned, XPAJ variants download a mother file and load it into the memory. Thus, a copy of the mother file can be found in the Windows folder using a random file name and extension. Typically, six to nine files are present.
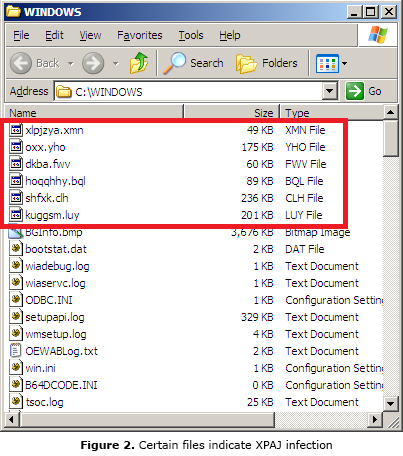
Computers are reinfected once these encrypted files exist again in the said folder with the same name and extension used before.
How do I remove these malware?
Trend Micro has created a tool named Trend Micro Rescue Disk to clean systems infected with the XPAJ variant, PE_XPAJ.C.
Trend Micro Rescue Disk is capable of doing the following:
- Clean infected MBR
- Clean files infected by the malware PE_XPAJ.C-1
- Delete files detected as Cryp_Xin14
Note that this tool uses a pattern designed only for PE_XPAJ.C-1 and Cryp_Xin14. Users may need to update their Trend Micro software with the latest pattern file if their computer is infected with other malware. Files that are not cleaned but detected by the Rescue Disk will be quarantined.
Trend Micro users should always make sure that they download the latest scan engine and patterns to keep their Trend Micro software up to date.
Users should also take note that PE_XPAJ.C can spread via mapped drives or shared folders. It is recommended that users disable their network shares immediately. They are also advised to block related malicious URLs and if possible, to add in the HOSTS file.