Understanding the Printer Virus
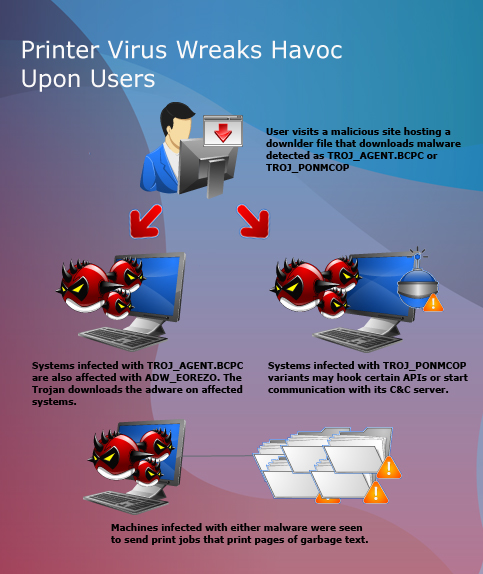
“Printer Virus” is a name collectively given to several malware that resulted in a number of reported infections seen to print out several lines of characters, like the one below:

The characters being printed out are actually lines of code that we believe to be of another malware intended to be executed by any of the following malware:
We speculate that there might be a bug that causes the malware to print the code instead of executing a file. However, this cannot be proven as of this writing.
How did I get infected?
Based on the analysis done, the following are two entry points used by this malware to get into a system:
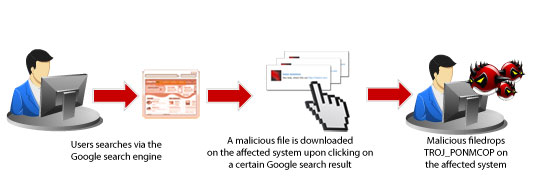
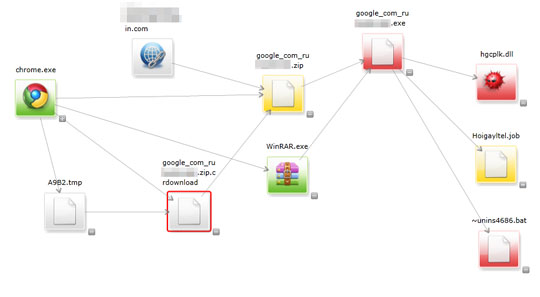
We've found some Google search results led to sites that download a file that drops TROJ_PONMCOP variants on an affected computer (see diagram above). This is similar to the diagram below, where the infection starts when a user, using Google Chrome as browser, accesses a malicious website. Once the malicious site is accessed, some files are downloaded on the system. These files execute and run on the system. In the diagram below, the executable file (google_com_ru{BLOCKED}.exe in the diagram) drops a .DLL file, which is detected as a TROJ_PONMCOP variant.
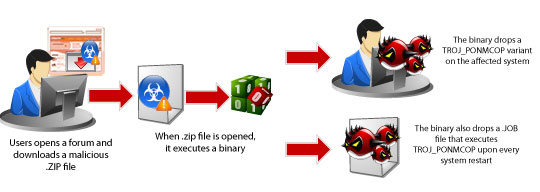
Another source of infection is via particular forums hosting a possibly malicious .ZIP file that when a user opens, executes a binary that drops TROJ_PONMCOP variants:
How do I know I’m infected?
Systems affected with TROJ_AGENT.BCPC connects to http://storage5.static.{BLOCKED}s.ru/i/12/0601/h_1338571059_9957469_b48b167953.jpeg, where it downloads ADW_EOREZO. Users might experience incessant pop-ups due to the presence of ADW_EOREZO on the system.
Also, the following components can be found in the infected machines:
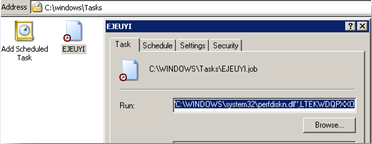
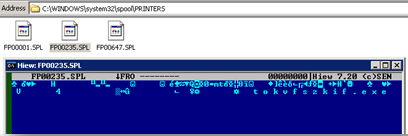
We have also noted that randomly-named binaries are found in the following locations:
- %System%\{random 10 letters}.exe
- %System%\SPOOL\PRINTERS\FP{5 numbers}.SPL - file that might be causing the printouts
- %System%\SPOOL\PRINTERS\{random file}.tmp
- Users\{user name}\Appdata\Roaming\{random file}.dll
- Documents and Settings\{user name}\Application Data\{random file}.dll
- %System%\{random file}.dll
- Program Files\{random folder}\{random file}.dll
- %Windows%\SysWOW64\{random file}.dll
What makes it difficult to analyze?
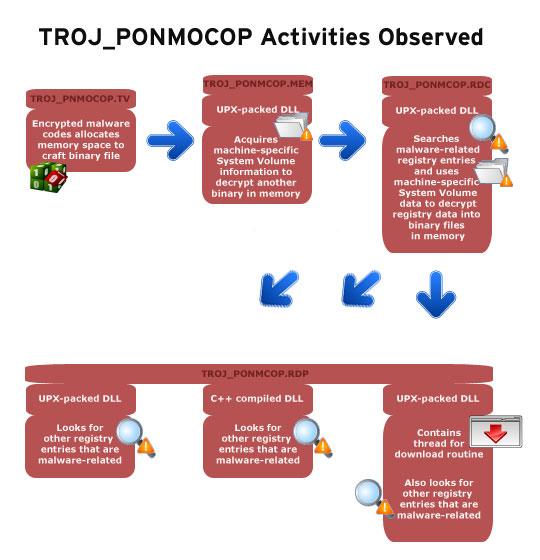
TROJ_PONMOCOP code contains an encrypted portion which is loaded and decrypted into memory. When decrypted, it will be a new binary file that is UPX-packed. After a successful decryption, it transfers the control to the newly-created binary. This newly created binary again contains encrypted code. Now to be able to decrypt this code, the malware gets the decryption keys from parameters found in the infected system i.e. ftCreationTime & ftLastAccessTime of %Windows%\system32 and System Volume Information folder, as well as the serial number of the hard drive. It then checks if decryption is successful. If the decrypted code is a valid binary file, it transfers the control to this another newly created binary. If not, then routine of the malware will not proceed. This simply means that the binary may be unique for each of infected system. Note that all these steps are done in memory, which means there is no dropped file. Routines of TROJ_PONMCOP is illustrated below:
Are Trend Micro users protected?
Yes, they are protected. All malware in this infection chain are actively detected and removed by Trend Micro products.