PE_BAMITAL.SME
Windows 2000, Windows XP, Windows Server 2003


Threat Type: File infector
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This file infector searches for files in %System%\dllcache and %System%. Once found, it infects the said files using Entry Point Obscuring (EPO) technique. Before proceeding with its payload, it first checks if it is being run by the local system, by checking if the SID starts with "S-1-5-18". It does not proceed if the SID is different.
If infection is successful, it attempts to access several randomly generated servers. It appends strings to the certain domain names.
This file infector arrives as a component bundled with malware/grayware packages. It may be unknowingly downloaded by a user while visiting malicious websites.
It modifies registry entries to enable its automatic execution at every system startup.
TECHNICAL DETAILS
Arrival Details
This file infector arrives as a component bundled with malware/grayware packages.
It may be unknowingly downloaded by a user while visiting malicious websites.
Installation
This file infector drops the following non-malicious files:
- %Windows%\expl.dat
- %System%\dllc.dat
- %System%\svch.dat
- %System%\winl.dat
(Note: %Windows% is the Windows folder, which is usually C:\Windows or C:\WINNT.. %System% is the Windows system folder, which is usually C:\Windows\System on Windows 98 and ME, C:\WINNT\System32 on Windows NT and 2000, or C:\Windows\System32 on Windows XP and Server 2003.)
It drops the following copies of itself into the affected system:
- %Application Data%\MicrosoftNT\winserver.exe
(Note: %Application Data% is the current user's Application Data folder, which is usually C:\Windows\Profiles\{user name}\Application Data on Windows 98 and ME, C:\WINNT\Profiles\{user name}\Application Data on Windows NT, and C:\Documents and Settings\{user name}\Local Settings\Application Data on Windows 2000, XP, and Server 2003.)
It creates the following folders:
- %Application Data%\MicrosoftNT
(Note: %Application Data% is the current user's Application Data folder, which is usually C:\Windows\Profiles\{user name}\Application Data on Windows 98 and ME, C:\WINNT\Profiles\{user name}\Application Data on Windows NT, and C:\Documents and Settings\{user name}\Local Settings\Application Data on Windows 2000, XP, and Server 2003.)
It adds the following mutexes to ensure that only one of its copies runs at any one time:
- 11expl22
- 11svch22
Autostart Technique
This file infector modifies the following registry entries to ensure it automatic execution at every system startup:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Explorer\
User Shell Folders
Startup = %Application Data%\MicrosoftNT
(Note: The default value data of the said registry entry is %User Startup%.)
Other System Modifications
This file infector adds the following registry entries as part of its installation routine:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows NT\CurrentVersion\Temp
Uses32 = {hex values}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows NT\CurrentVersion\Temp
TimeGetWork = {dword value}
Other Details
This file infector connects to the following URL(s) to check for an Internet connection:
- google.com
NOTES:
This file infector searches for the following files in %System%\dllcache and %System%:
- explorer.exe
- svchost.exe
- winlogon.exe
Once found, it infects the said files using Entry Point Obscuring (EPO) technique.
Before proceeding with its payload, the malware first checks if it is being run by the local system, by checking if the SID starts with "S-1-5-18". It does not proceed if the SID is different.
If infection is successful, it attempts to access several randomly generated servers:
- {15randomchars}.co.cc
- {15randomchars}.cz.cc
- {15randomchars}.info
- {15randomchars}.in
It appends the following strings to the above-mentioned domain names:
- /m.{BLOCKED}id={id}&pr={value}&os={value_os}&id={processor_info}&ver={value_ver}&ver={value_ver}
SOLUTION
Step 1
For Windows ME and XP users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 3
Restore a file/s that has/have been corrupted/modified by this malware/grayware
To restore system files:
• For Windows 2000:
- Insert your Windows 2000 Installation CD in your CD-ROM drive.
- Click Start>Run.
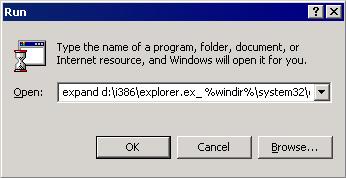
- In the Open text box, type the following then click OK:
expand D:\i386\{file to restore}.ex_ %windir%\system32\{file to restore}.exe
• For Windows XP and Windows Server 2003:
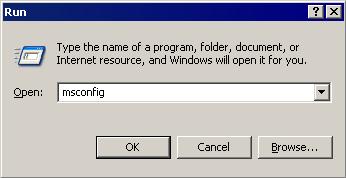
- Click Start>Run.
- In the Open text box, type the following then click OK:
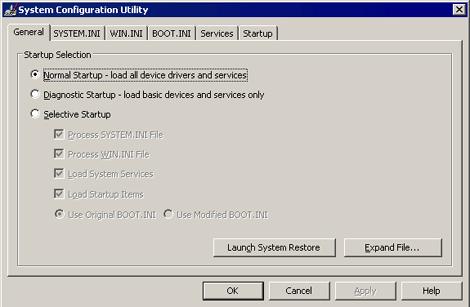
MSCONFIG - Make sure that the option Normal startup - load all device drivers and services option is selected.
- Click the Expand button.
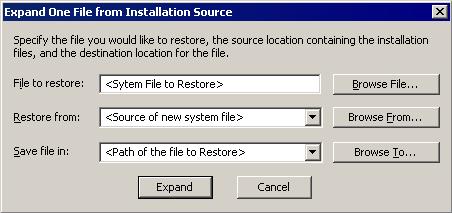
- In the dialog box that appears, type the following:
- File to restore contains the path and file name of the file you wish to restore.
- Restore from contains the path to the Windows CAB files. This path may vary from machine to machine. It may be in a local drive, in a network drive, or in a CD-ROM. In the local drive, it is usually in C:\WINDOWS\OPTIONS\INSTALL.
- Save file in contains the path of the file you wish to restore (Do not include the file name).
- Click the Expand button.
• For Windows Vista and Windows 7:
- Insert your Windows Installation CD or the USB flash drive then restart your computer.
- When prompted, press any key to boot from the CD or the USB drive.
- Choose your language settings then click Next.
- Click Repair your computer.
- Select the OS you want to repair then click Next.
- On the System Recovery Options menu, click Startup Repair. At this point, Windows automatically begins restoring modified/deleted system file/s.
Step 4
Restore this modified registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer"s registry.
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
- From: Startup = %Application Data%\MicrosoftNT
To: Startup = %User Startup%
- From: Startup = %Application Data%\MicrosoftNT
Step 5
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer"s registry.
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Temp
- Uses32 = {hex values}
- Uses32 = {hex values}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Temp
- TimeGetWork = {dword value}
- TimeGetWork = {dword value}
Step 6
Search and delete these files
Step 7
Search and delete this folder
Step 8
Scan your computer with your Trend Micro product to clean files detected as PE_BAMITAL.SME If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
NOTES:
RECOMMENDATIONS:
- This malware is detected and removed by the latest Trend Micro anti-malware engine and pattern. Always keep pattern files and engines up-to-date. To know more about updating your Trend Micro product’s pattern, please refer to the following Trend Micro support page:
Note: The steps apply for specific products indicated in the page. - To actively detect and protect your machine, enable real-time scanning of your Trend Micro anti-malware product. Refer to the following Trend Micro support page to know more about enabling real-time scanning in your Trend Micro product:
- Enable firewall to protect against threats.
- Monitor network connections for any suspicious connection or connectivity.
- Avoid downloading software cracks and/or pirated applications.
- Be aware of social engineering attacks to be safe.
Did this description help? Tell us how we did.


